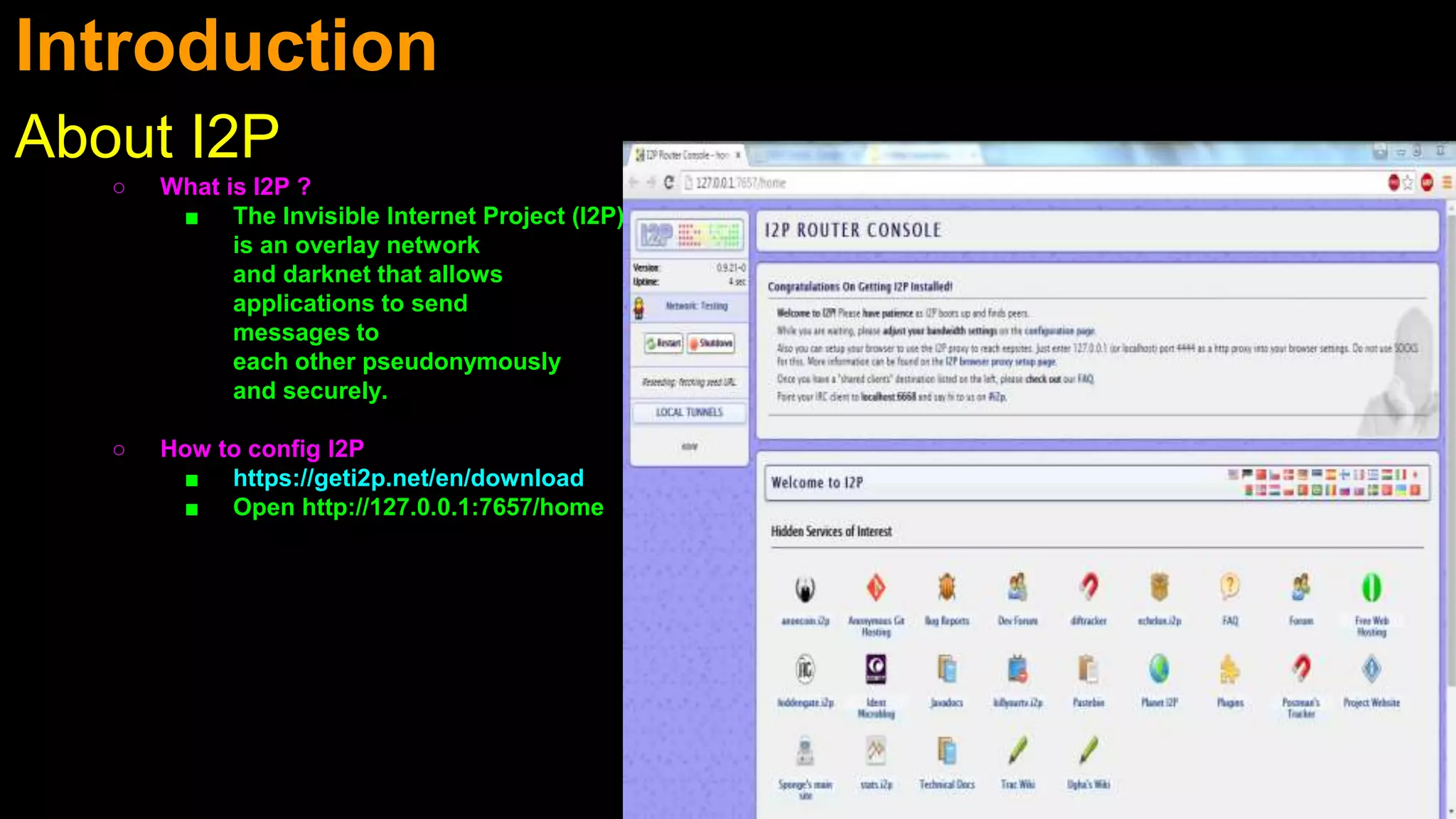
The document discusses the different layers of the internet, including the clearweb which is accessible via search engines, the dark web which search engines don't index, and the deep web which requires special software like Tor or I2P to access. It provides an overview of Tor and I2P anonymity networks, and how to configure them to access the deep web through URLs ending in .onion rather than standard top-level domains. The document also gives an example of a hidden wiki URL that can only be accessed through the Tor browser, not a regular browser.