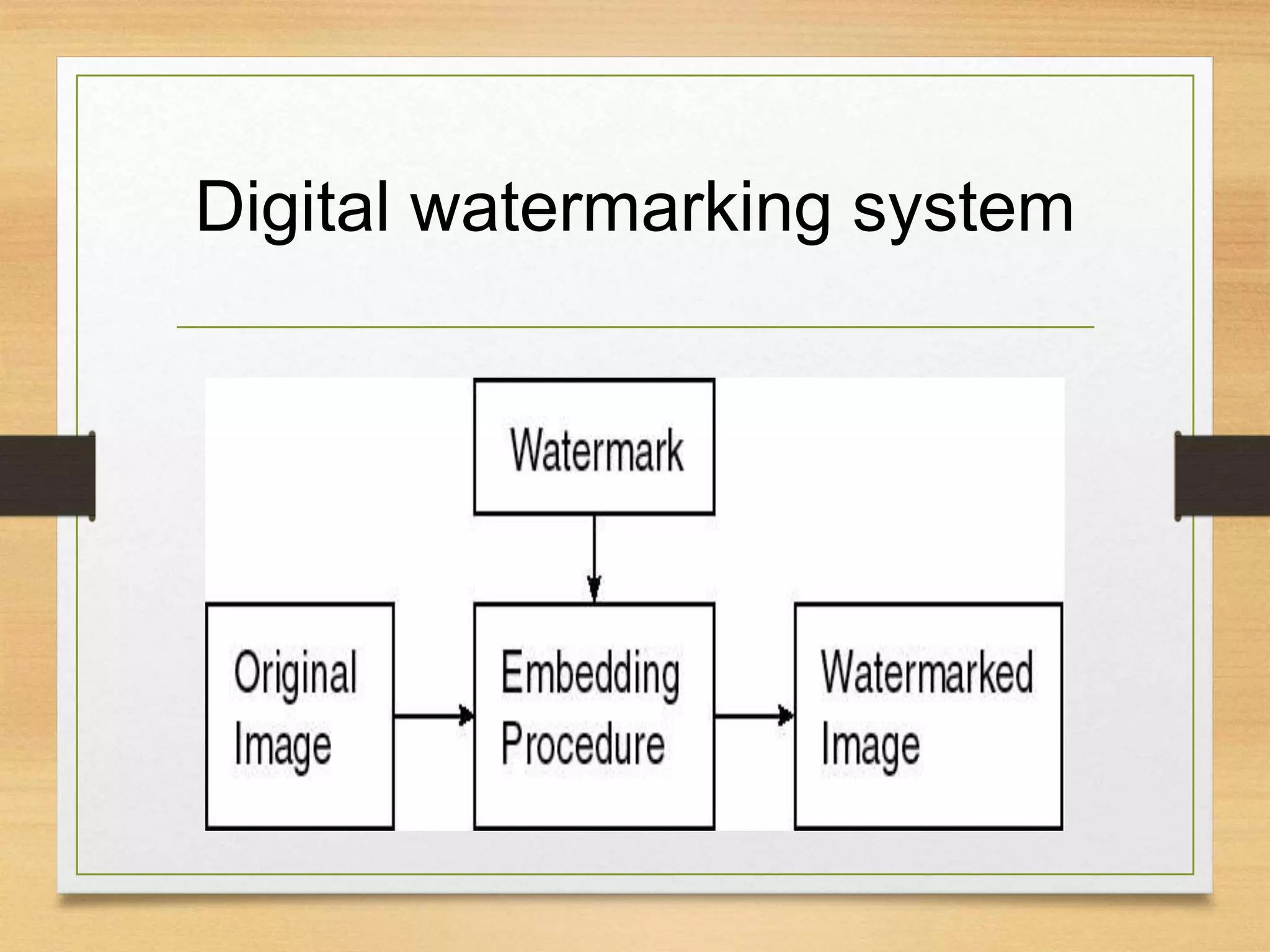
This document discusses digital watermarking techniques for security applications. Digital watermarking involves embedding a secret watermark into digital media like images, video and audio. This allows for authentication of data and copyright protection. There are two main types of watermarking - spatial domain, which embeds watermarks by modifying pixel values, and frequency domain, which represents the image in transform coefficients and embeds watermarks there. Digital watermarking has applications like copyright protection, medical records, and privacy controls of images. Common attacks aim to remove or interfere with watermarks through operations like noise insertion, compression, or attempts to extract the watermark without authorization.