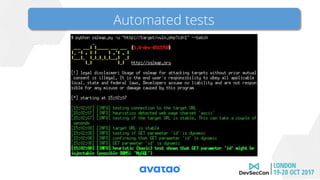
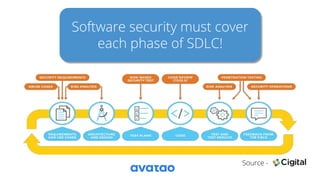
This document promotes secure software development practices and advertises an upcoming security conference. It discusses the speaker's background in security research and hacking competitions. It then outlines some common security issues like weak passwords, SQL injection, and open redirects. To demonstrate secure development, it proposes a hands-on exercise of attacking, fixing, and rewriting the codebase of a sample legacy online spaceflight booking application. The document emphasizes the importance of considering security throughout the entire software development lifecycle from design to deployment. It invites the reader to join the security conference conversation.


















![Vulnerability - Evil REs stuck on crafted inputs.
– (a+)+
–([a-zA-Z]+)*
–(a|aa)+
–(a|a?)+
–(.*a){x} | for x > 10
Feaure - Registration (email RE in Spring)
Source - OWASP
Regular Expression DoS](https://image.slidesharecdn.com/devsecconlondon2017-gaborpek-171030080535/85/DevSecCon-London-2017-Hands-on-secure-software-development-from-design-to-deployment-by-Gabor-Pek-27-320.jpg)