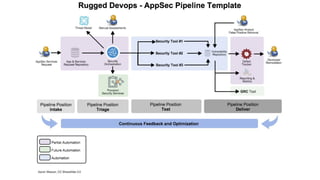
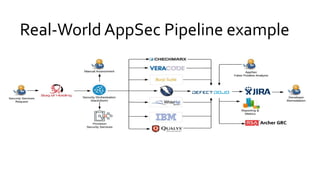
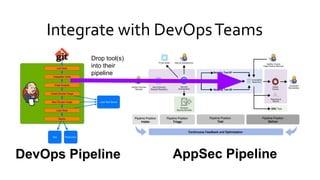
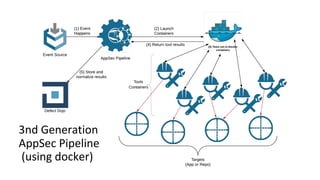
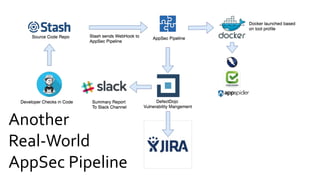
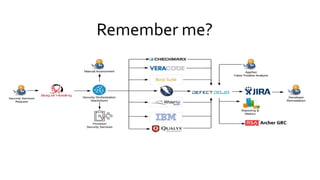
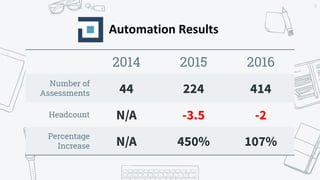
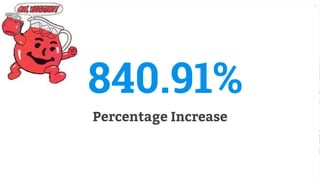
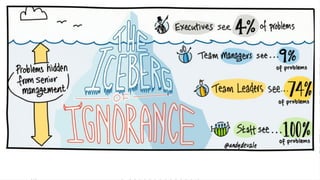
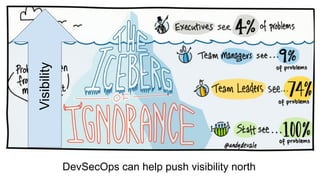
This document discusses the fundamentals and evolution of DevSecOps. It begins by introducing the author and their background. It then outlines key DevSecOps concepts like reducing complexity, managing dependencies, shared understanding, enabling default security controls, fully utilizing frameworks, embracing cloud-native principles, codifying processes, treating servers as cattle, and automating workflows. The document also discusses the importance of DefectDojo and generating AppSec pipelines to integrate security testing into development pipelines in order to scale efforts and increase visibility, consistency, and flow. It emphasizes automating non-human tasks to optimize security personnel.