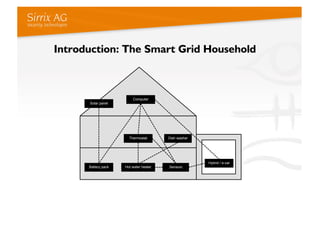
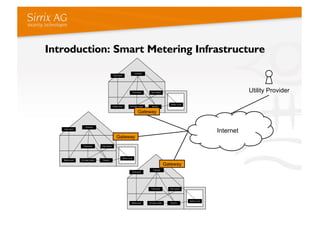
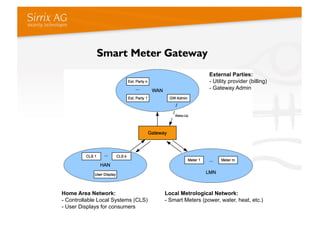
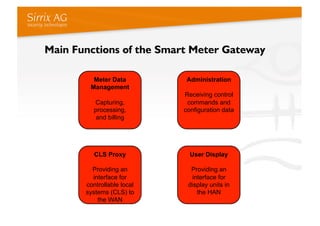
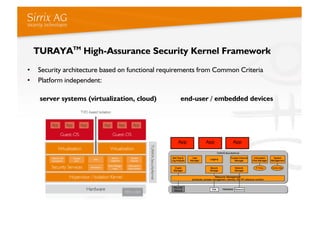
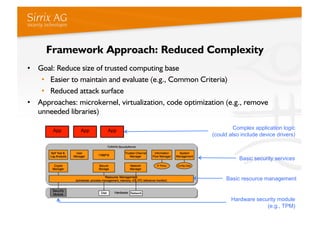
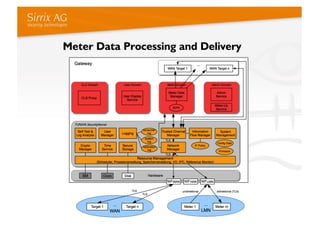
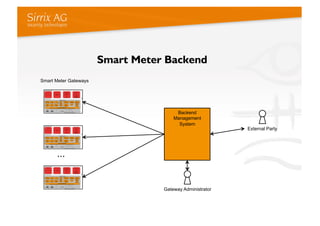
The document discusses applying a security kernel framework to smart meter gateways. It notes privacy and security are critical issues for smart metering given data from homes is communicated over the internet. The EU has directives requiring smart meters be installed in most homes by 2020 and specifying security and privacy protections. The talk describes security requirements for smart meter gateways set by German standards, and issues with existing approaches not meeting them. It then introduces the TURAYA security kernel framework as a way to address these issues and simplify developing secure smart meter gateways.