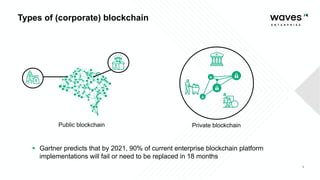
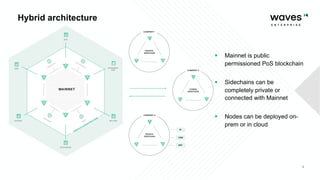
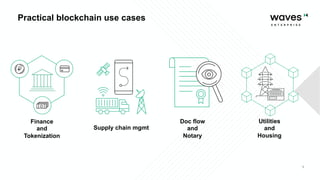
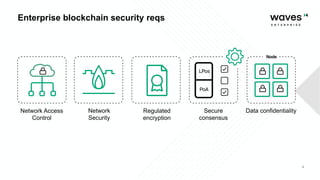
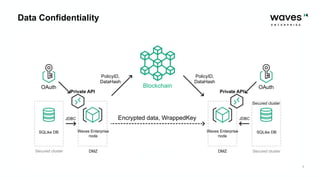
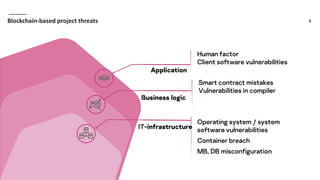
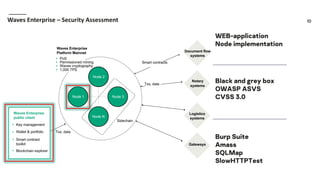
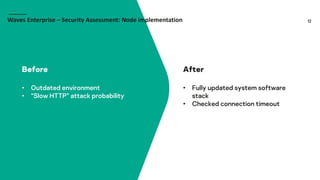
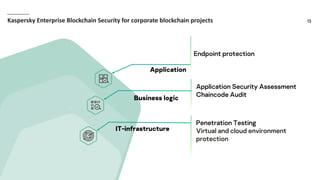
Waves Enterprise offers a hybrid blockchain platform aimed at scalable digital infrastructure, combining rapid deployment and a full suite of services including consulting and support. The document highlights the importance of application security assessments in detecting vulnerabilities early in the development process to avoid significant costs and disruptions. It also discusses various blockchain security requirements and threats, including human factors and software vulnerabilities.