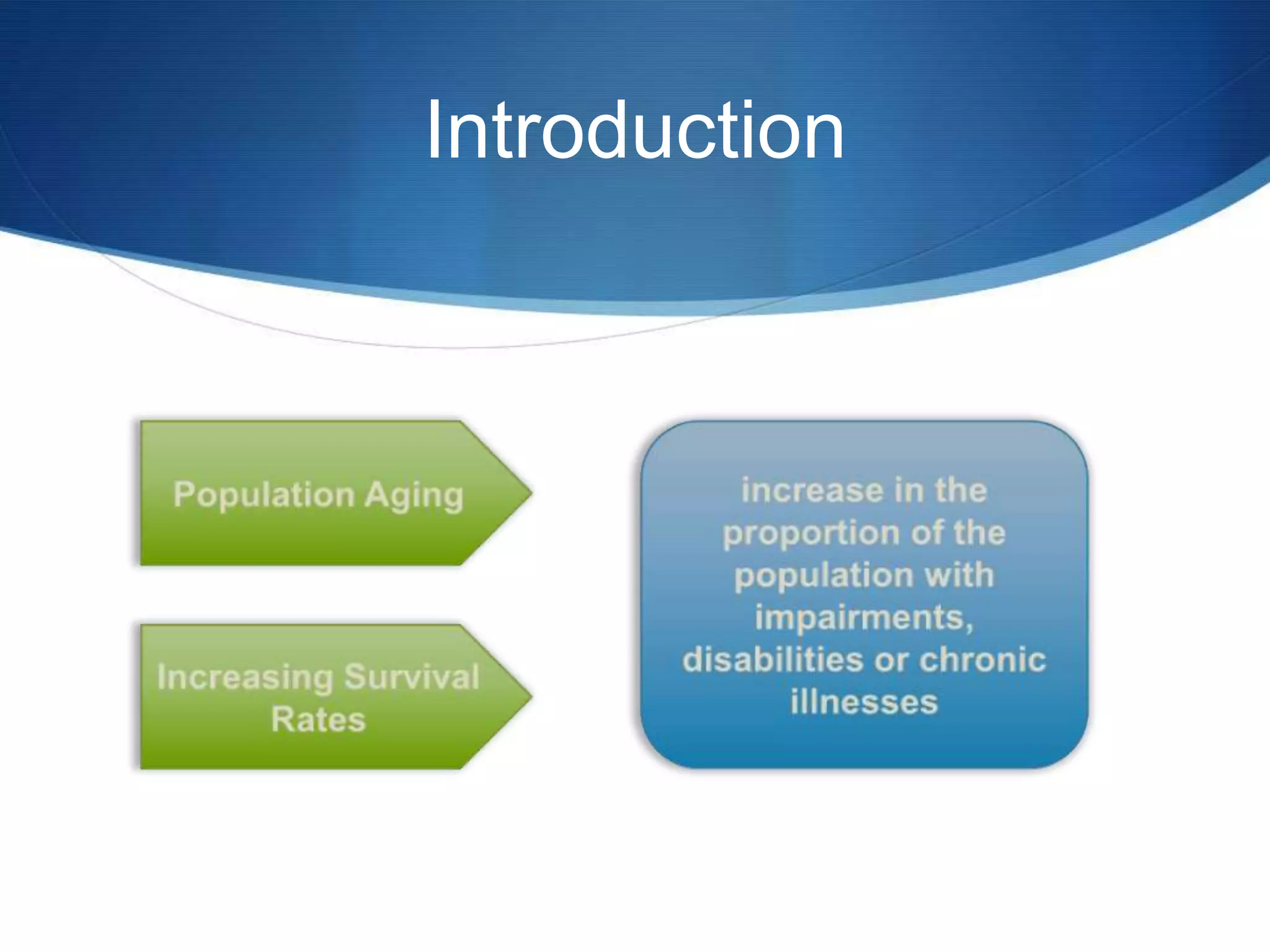
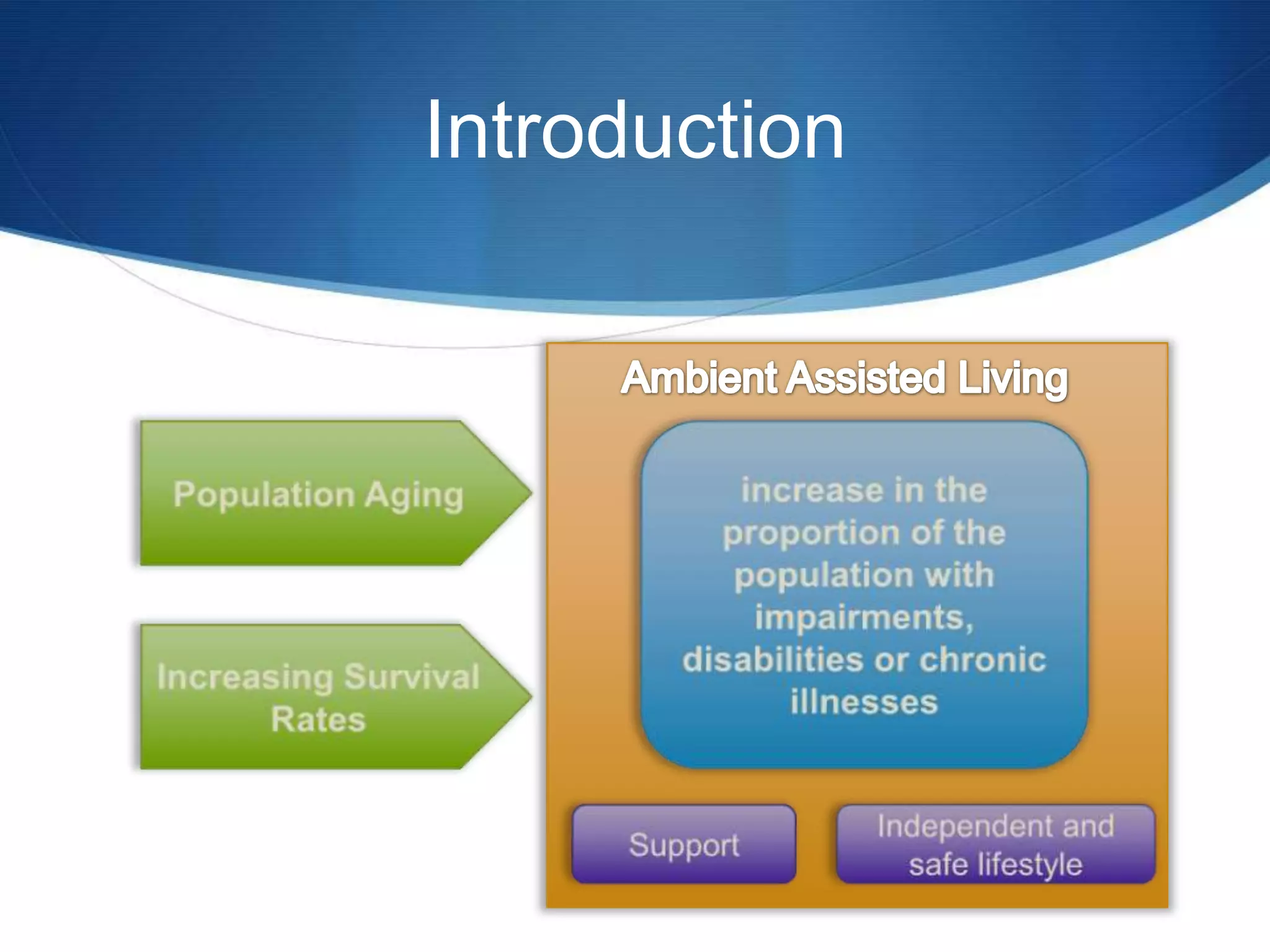
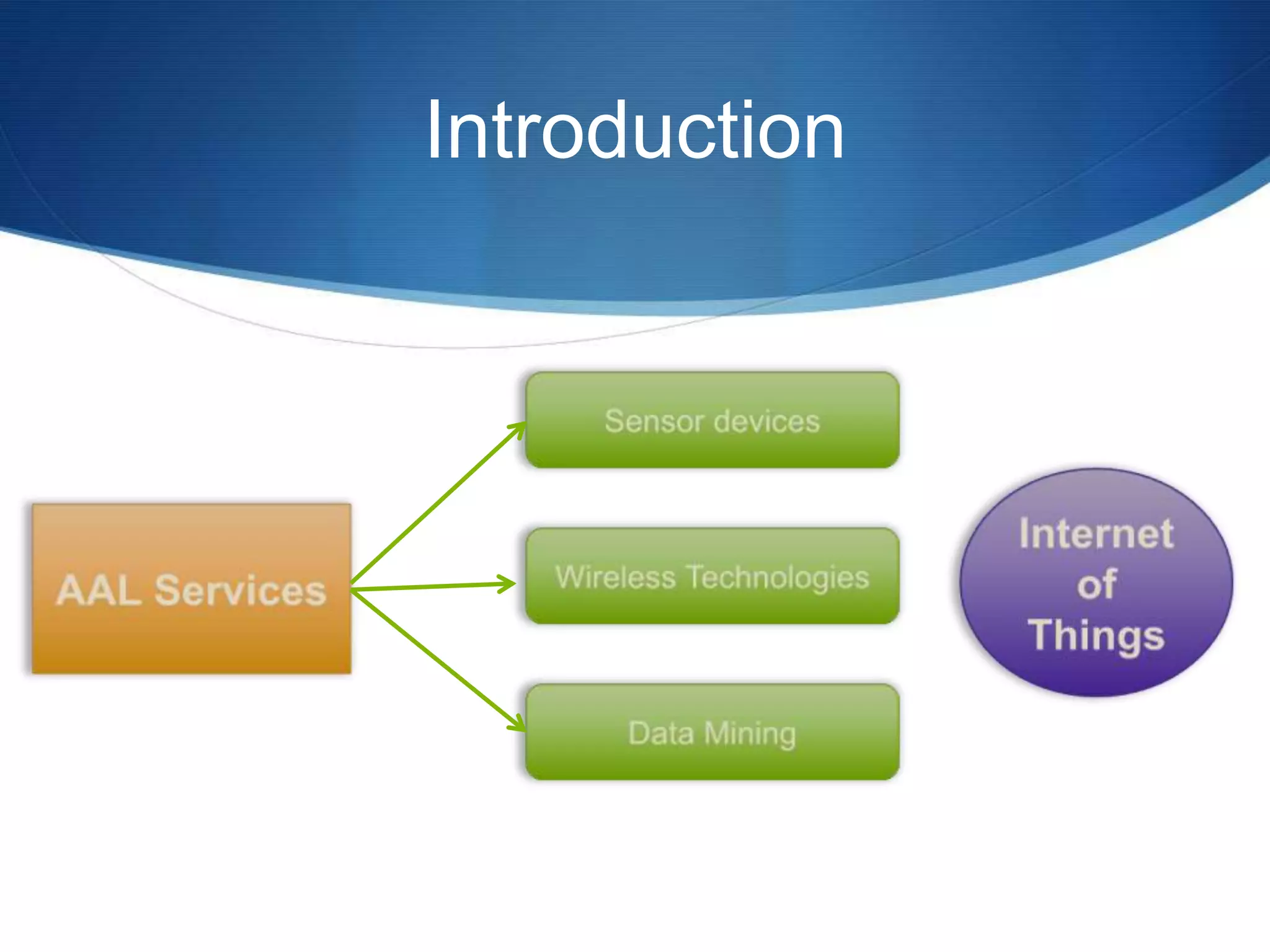
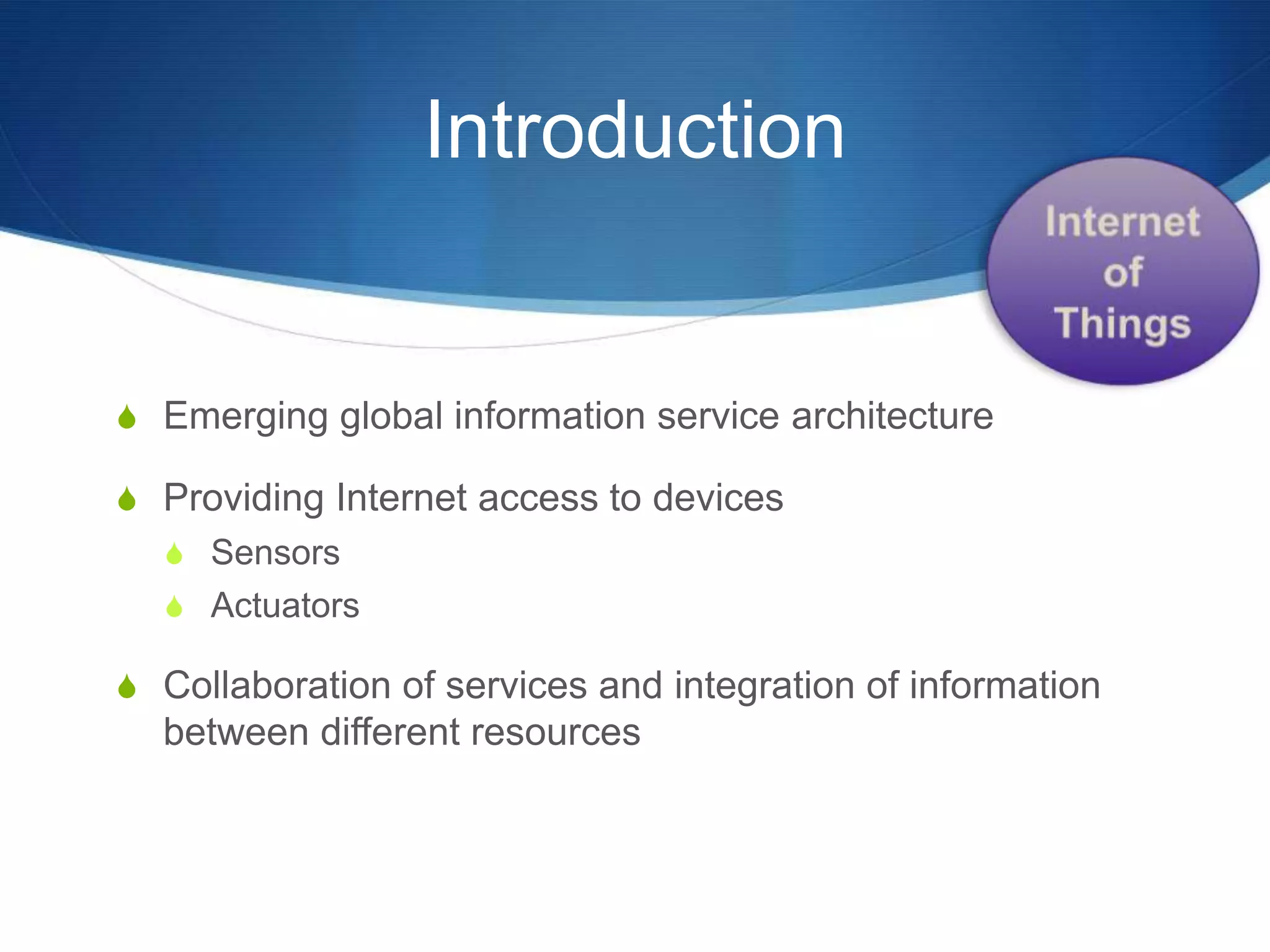
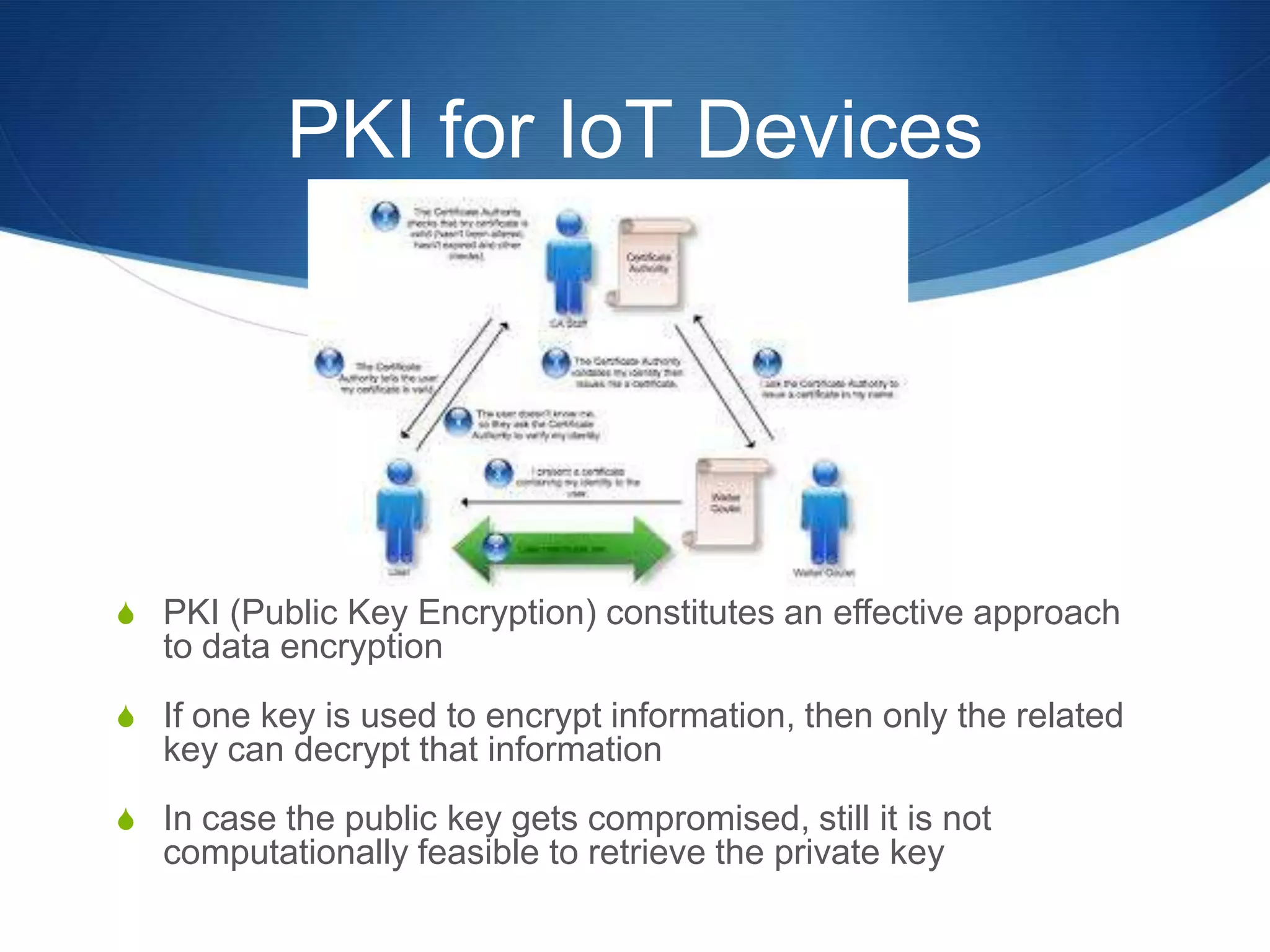
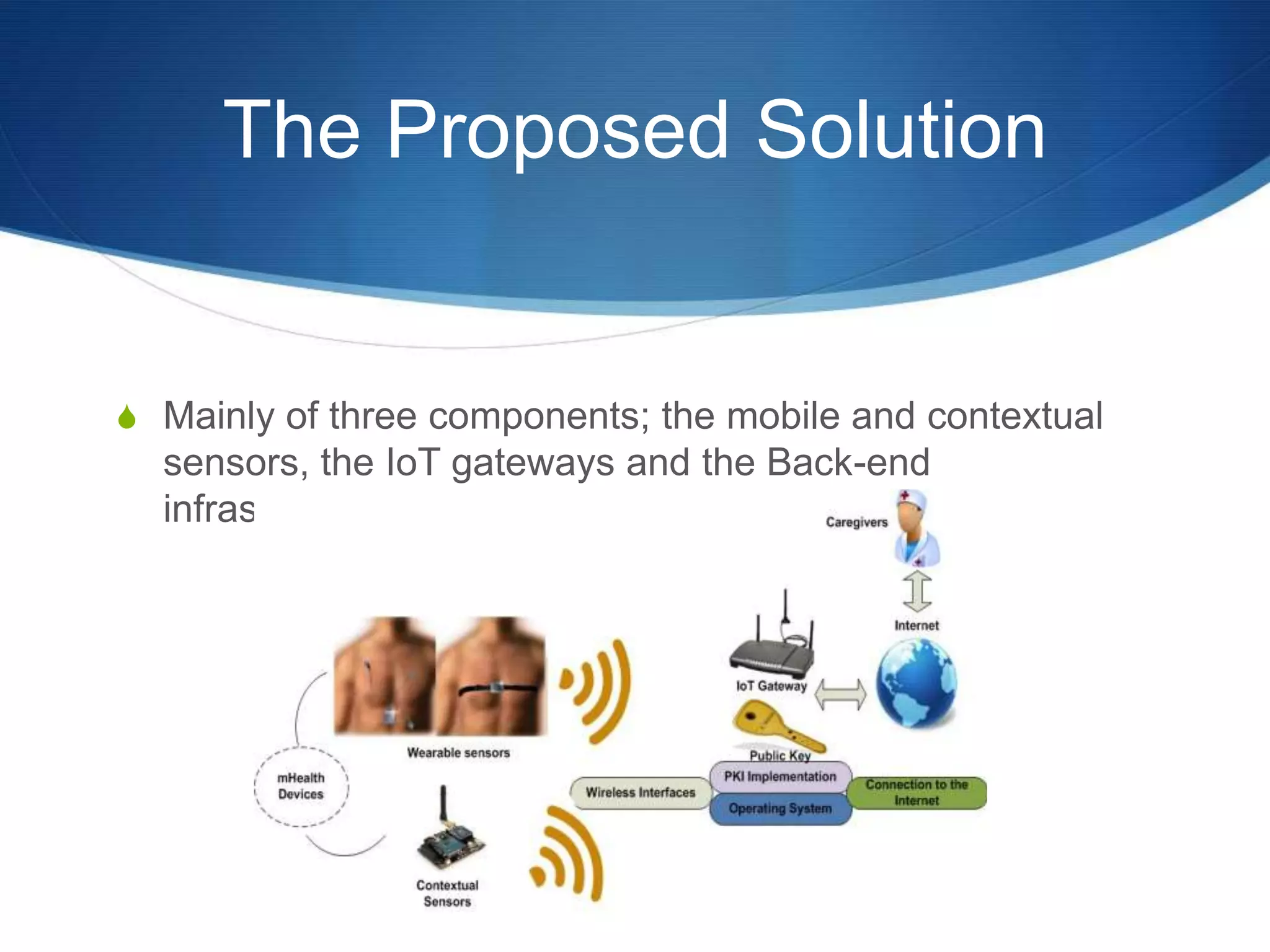
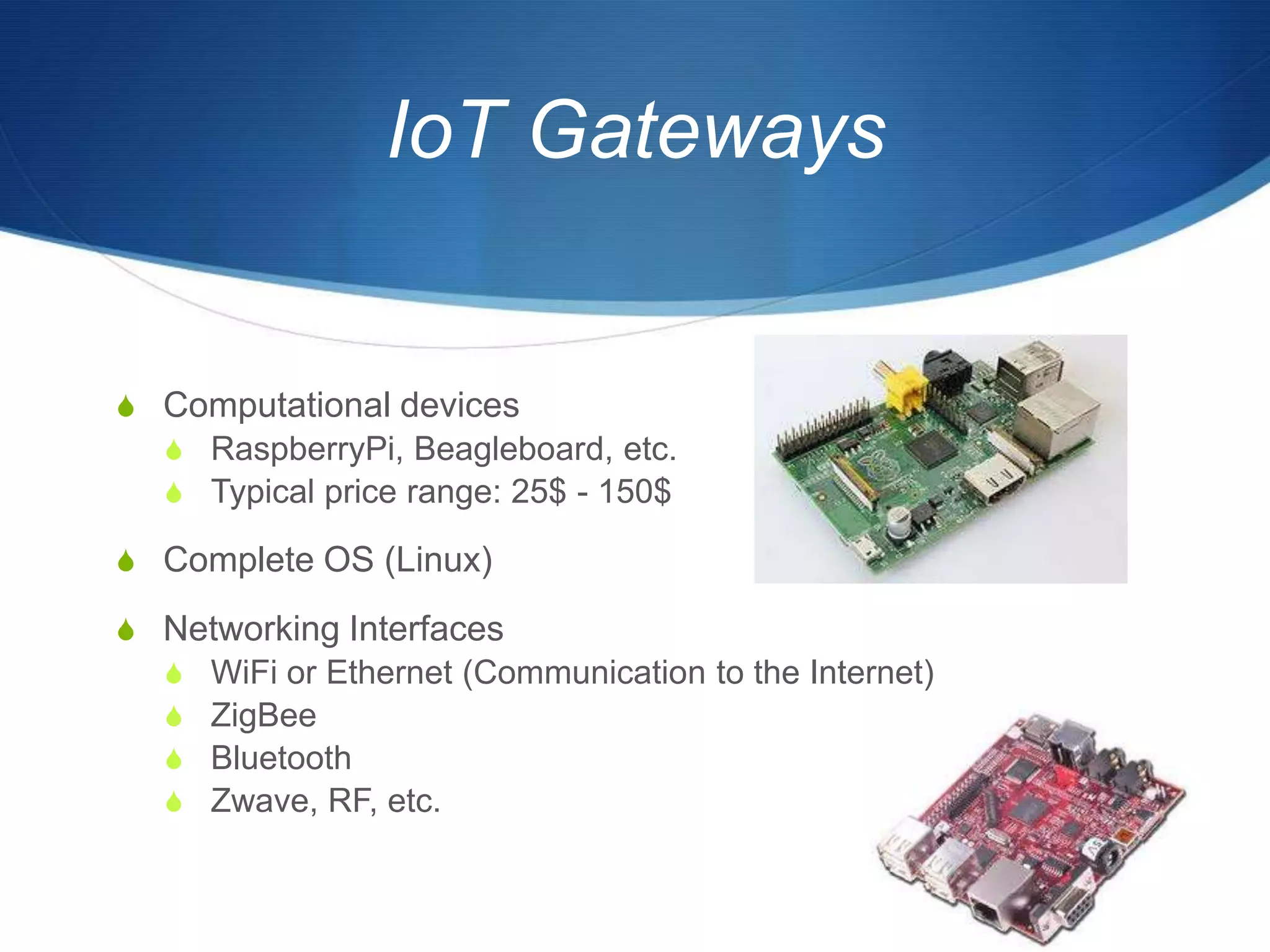
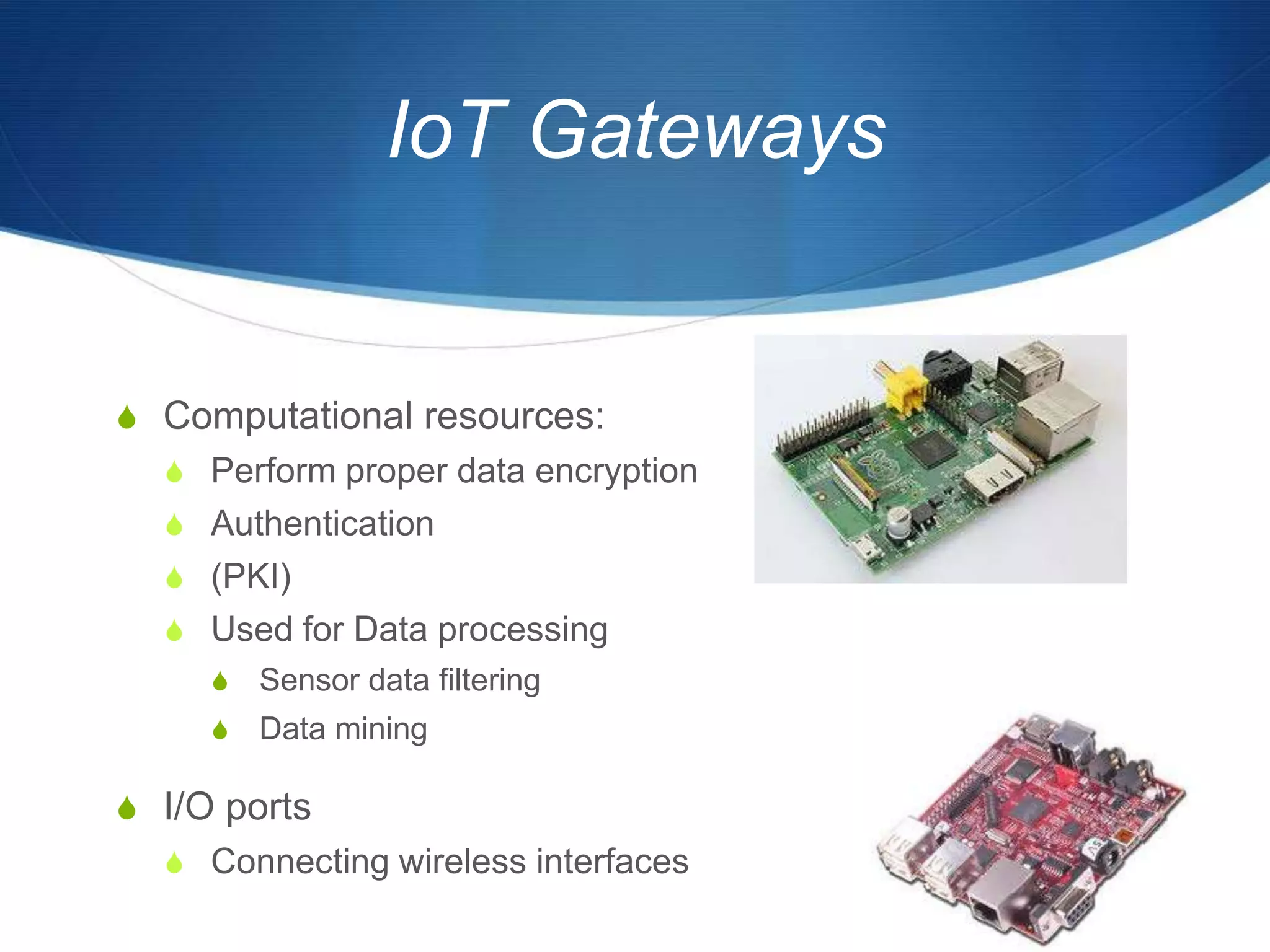
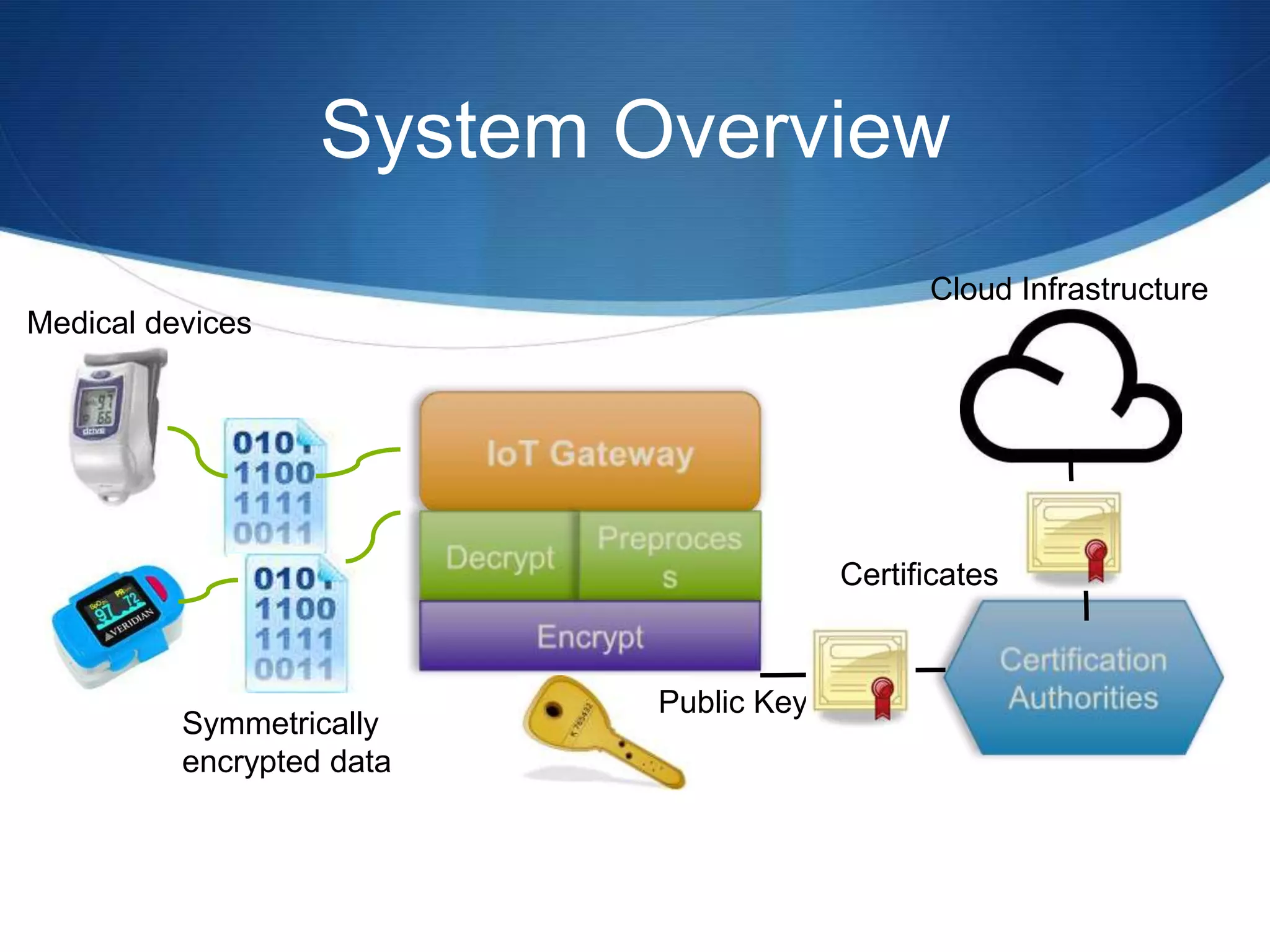
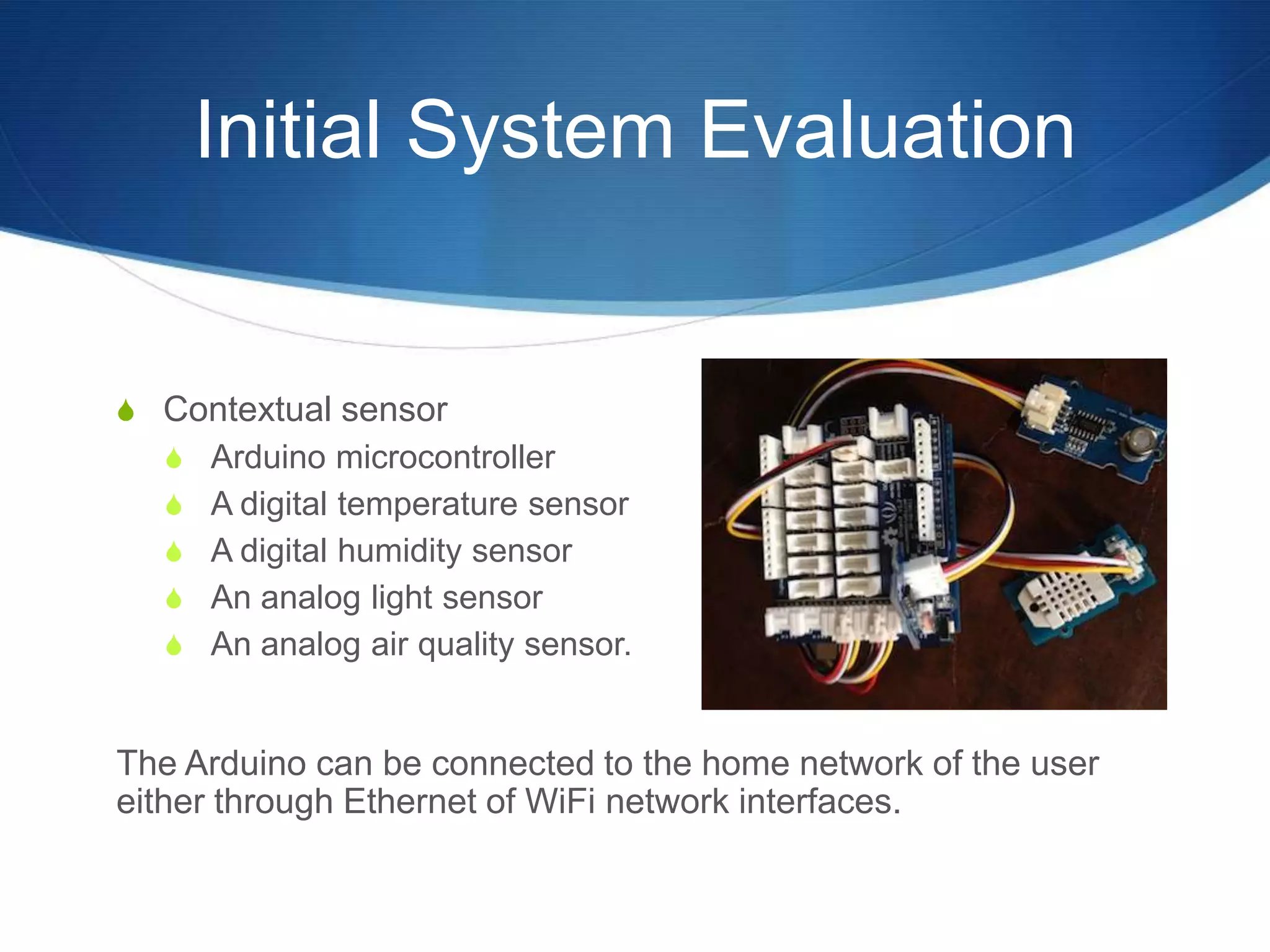
The document discusses a prototype cloud-based system that employs PKI encryption for data protection in IoT m-health devices, facilitating secure transmission and authentication of sensor data. It addresses challenges in healthcare related to security, interoperability, and data management, proposing IoT gateways to enhance computational resources and facilitate key management. Initial evaluations indicate that while the encryption process introduces some overhead, it remains acceptable for mobile health applications.