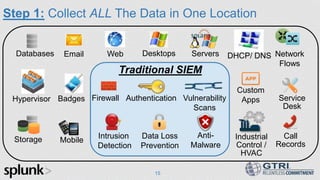
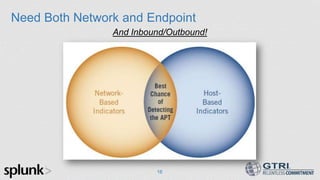
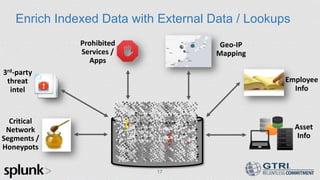
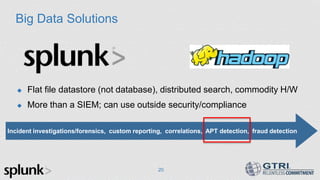
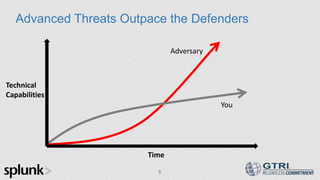
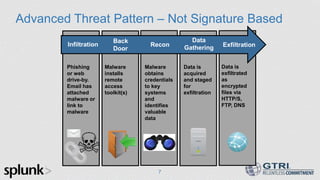
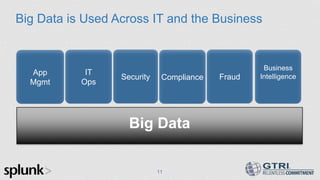
The document discusses the use of big data in cybersecurity to address advanced threats that traditional security methods struggle to detect. It emphasizes the importance of collecting and analyzing large datasets to identify anomalies indicative of security breaches and offers a three-step approach to enhance threat detection and remediation. The presentation showcases Splunk's capabilities in machine data analytics and highlights the need for skilled practitioners to leverage big data effectively.










![Big Data Analytics
14
Security for Business Innovation
Council report, “When
Advanced Persistent Threats
Go Mainstream,”
Chuck Hollis
VP – CTO, EMC Corporation
“The core of the most effective [advanced threat]
response appears to be a new breed of security
analytics that help quickly detect anomalous
patterns -- basically power tools in the hands of a
new and important sub-category of data scientists:
the security analytics expert..”
“[Security teams need] an analytical engine to sift
through massive amounts of real-time and
historical data at high speeds to develop trending
on user and system activity and reveal anomalies
that indicate compromise.”
14](https://image.slidesharecdn.com/using-big-data-to-counteract-advanced-threats-140521161152-phpapp01/85/Using-Big-Data-to-Counteract-Advanced-Threats-14-320.jpg)