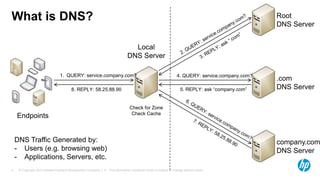
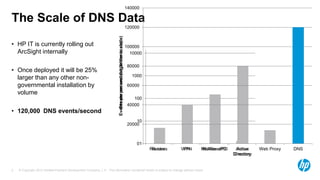
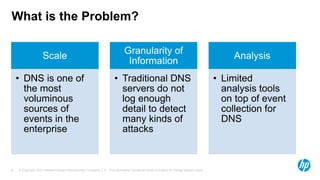
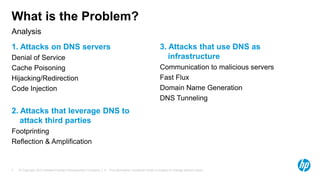
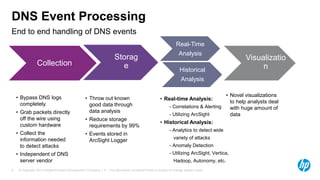
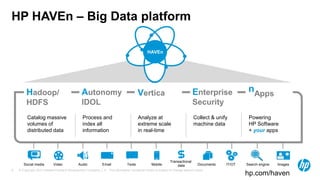
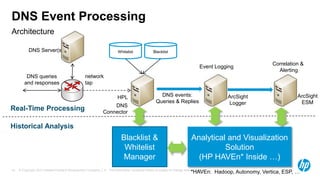
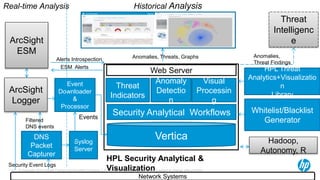
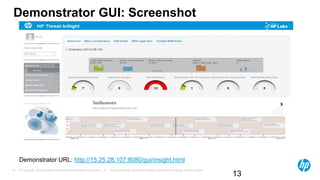
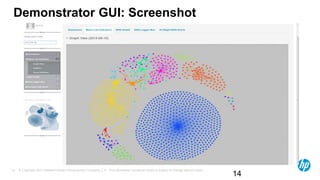
The document discusses the challenges and methodologies for analyzing DNS data as a significant source of security events in enterprises. It outlines the limitations of traditional DNS servers and presents a solution involving real-time and historical analysis using HP's big data platform, which includes various technologies such as Hadoop and ArcSight. The document also highlights the competitive landscape in the security market, noting the capabilities of HP's competitors in network packet capture and advanced analytics.