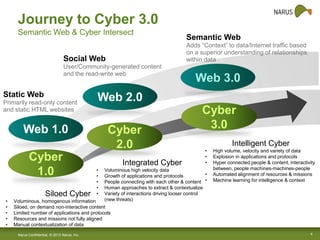
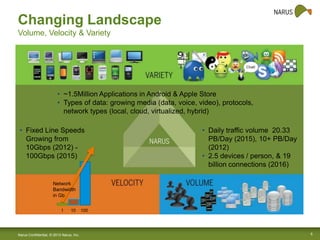
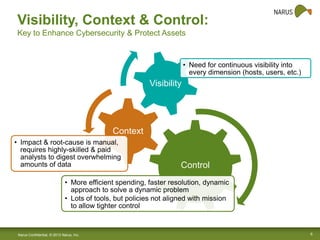
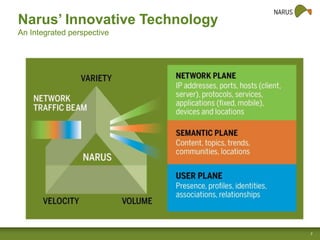
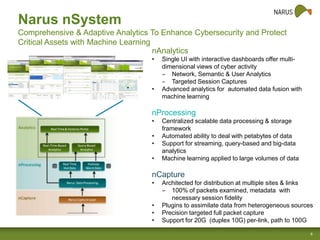
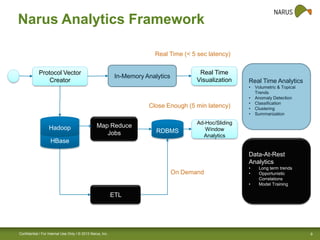
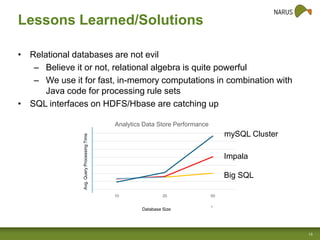
Narus provides cybersecurity analytics and solutions to help customers gain visibility into their network traffic and security threats. Their technology fuses network, semantic, and user data to provide comprehensive security insights. Key challenges include increasing data volumes and diversity of network deployments. Narus addresses these with an integrated analytics platform that uses machine learning to extract metadata and detect anomalies in real-time and over long periods of stored data. Their hybrid approach leverages both Hadoop/Hbase and relational databases for scalable analytics and business intelligence.