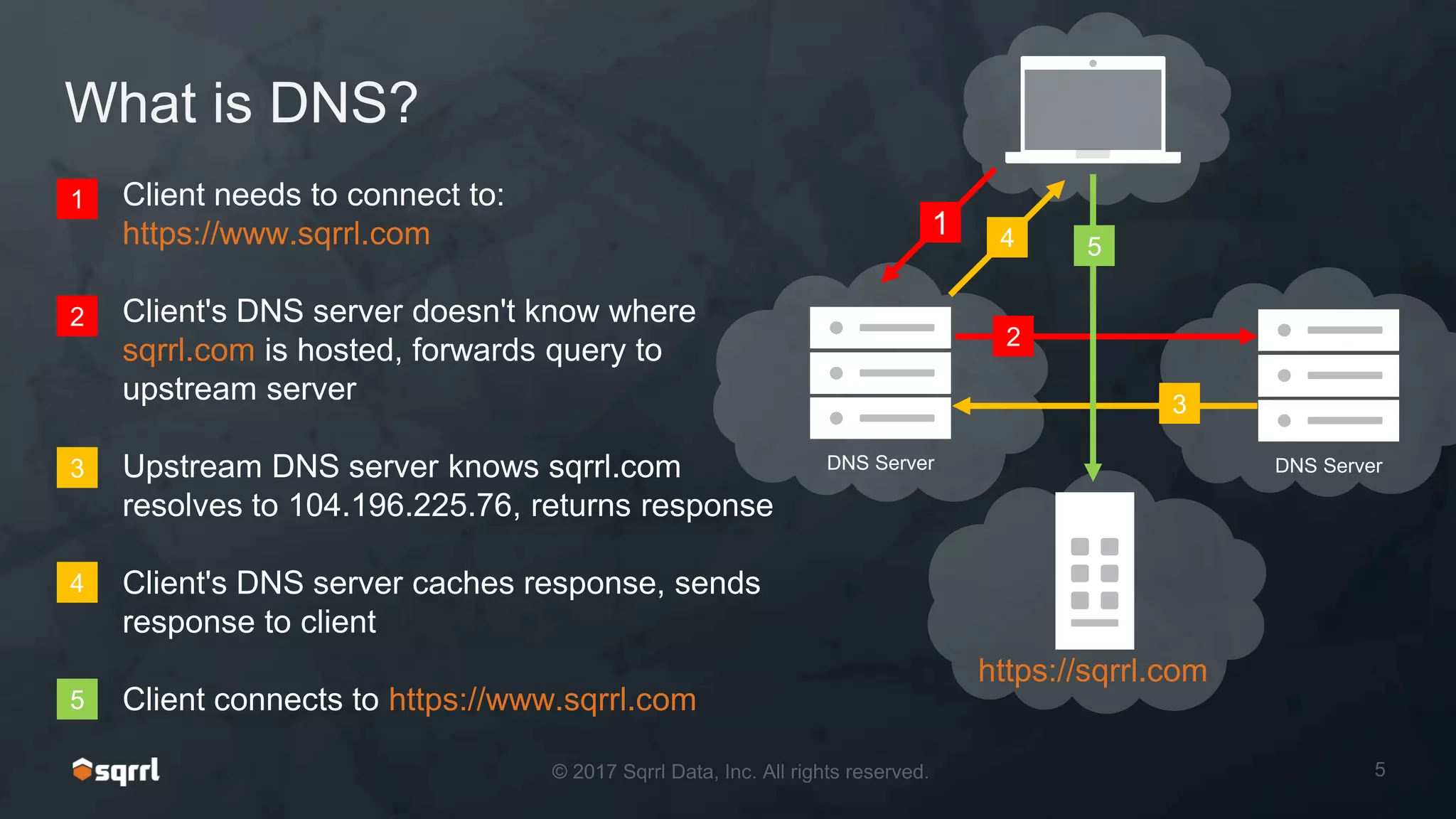
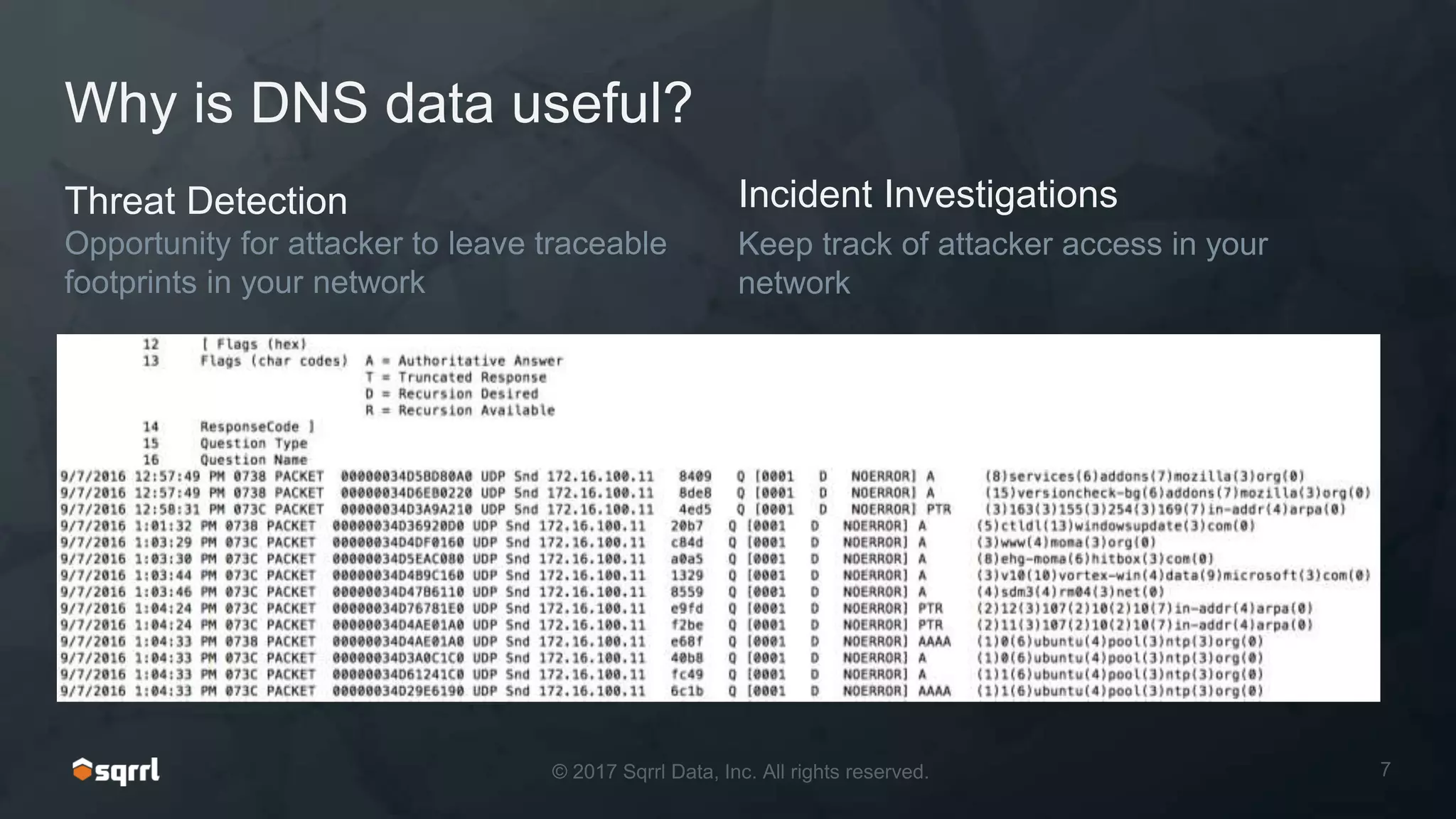
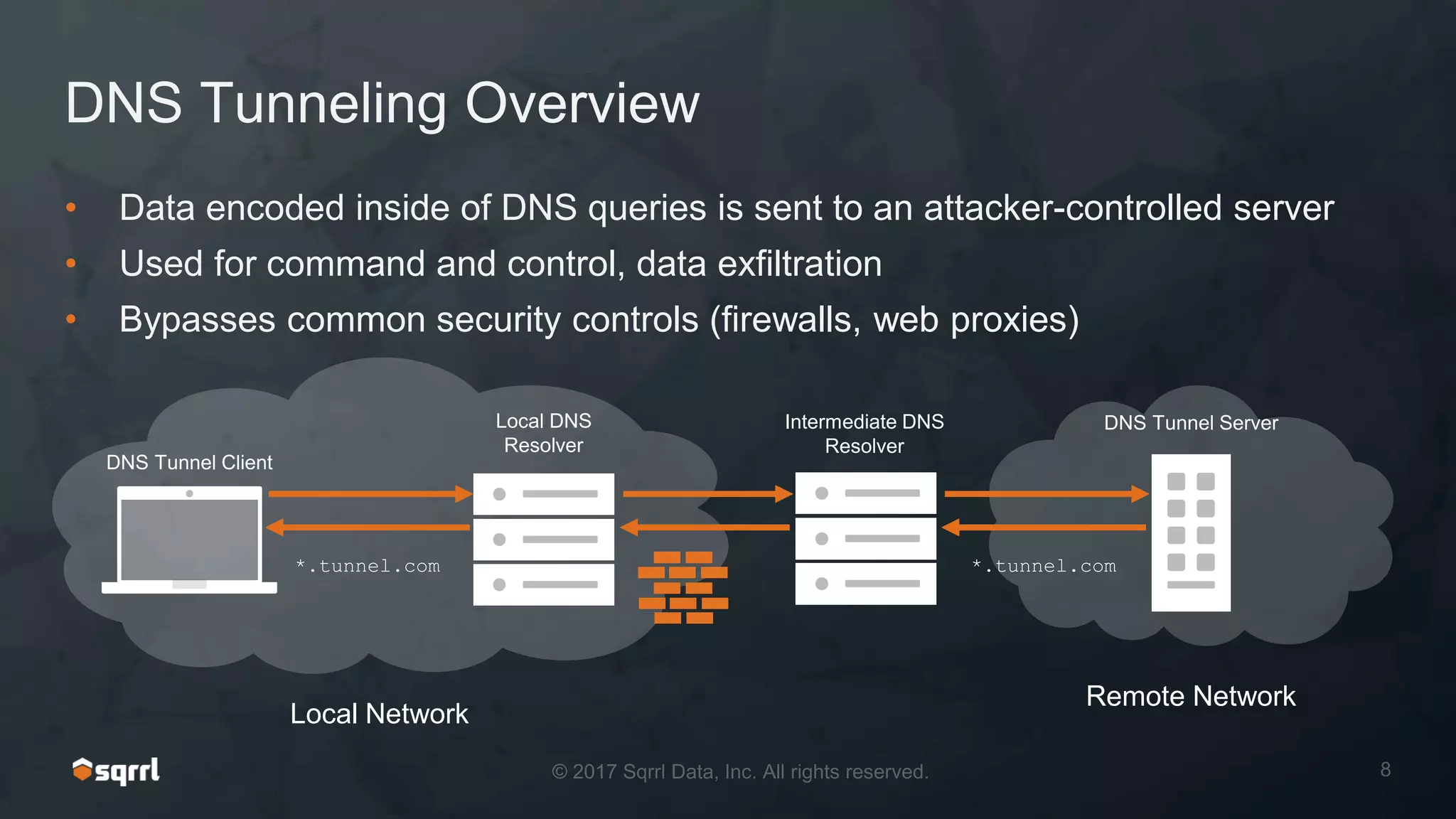
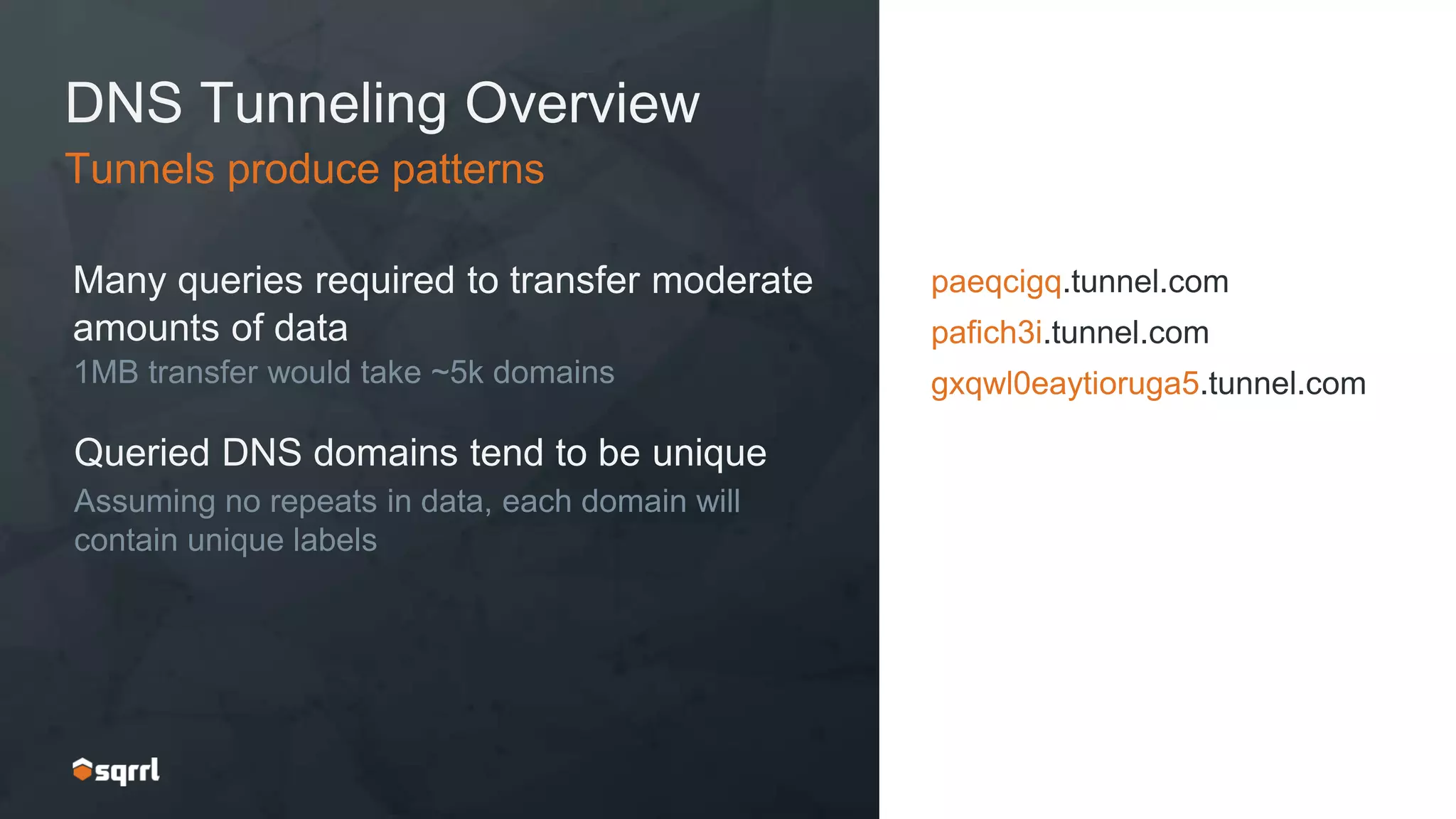
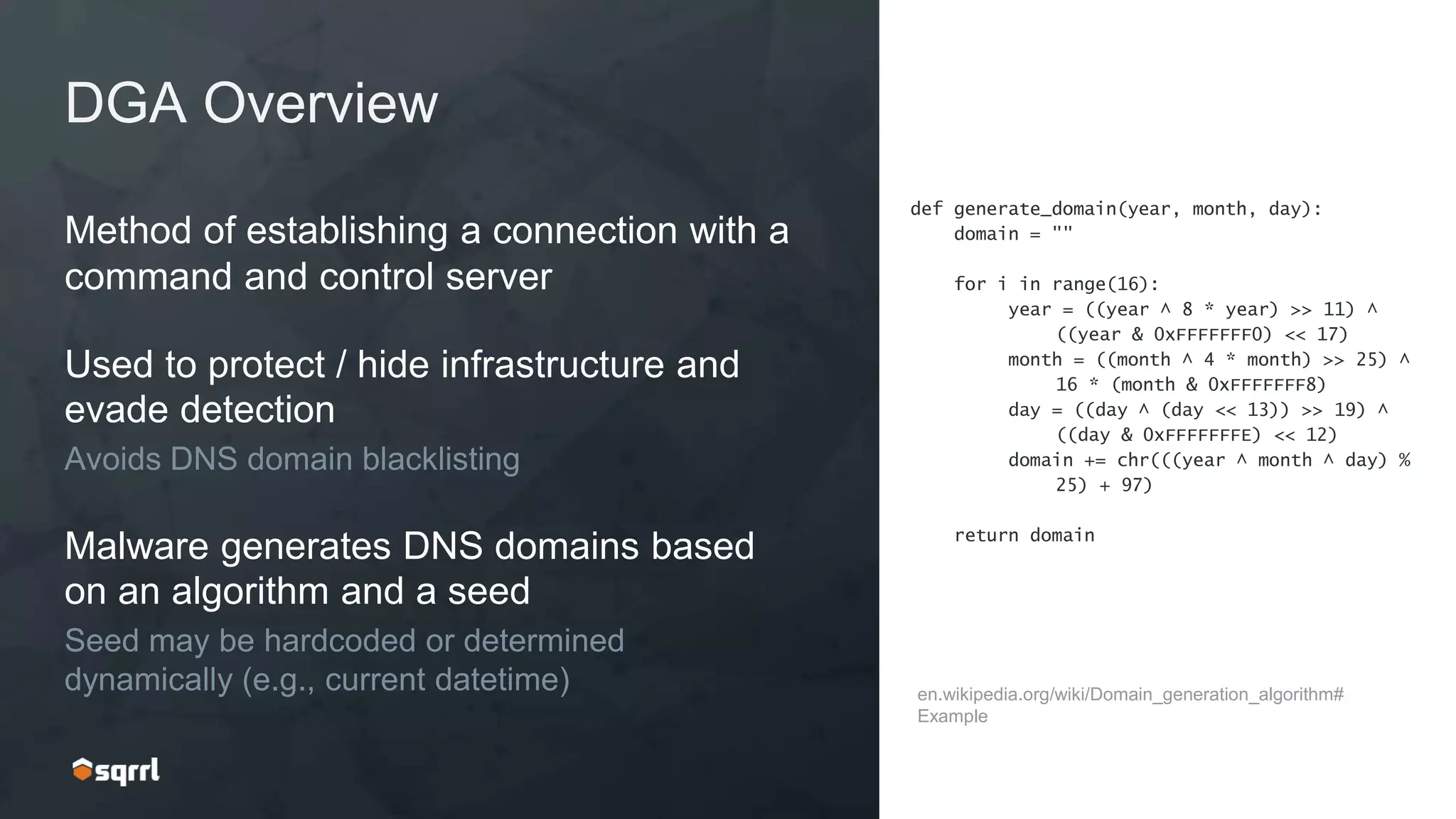
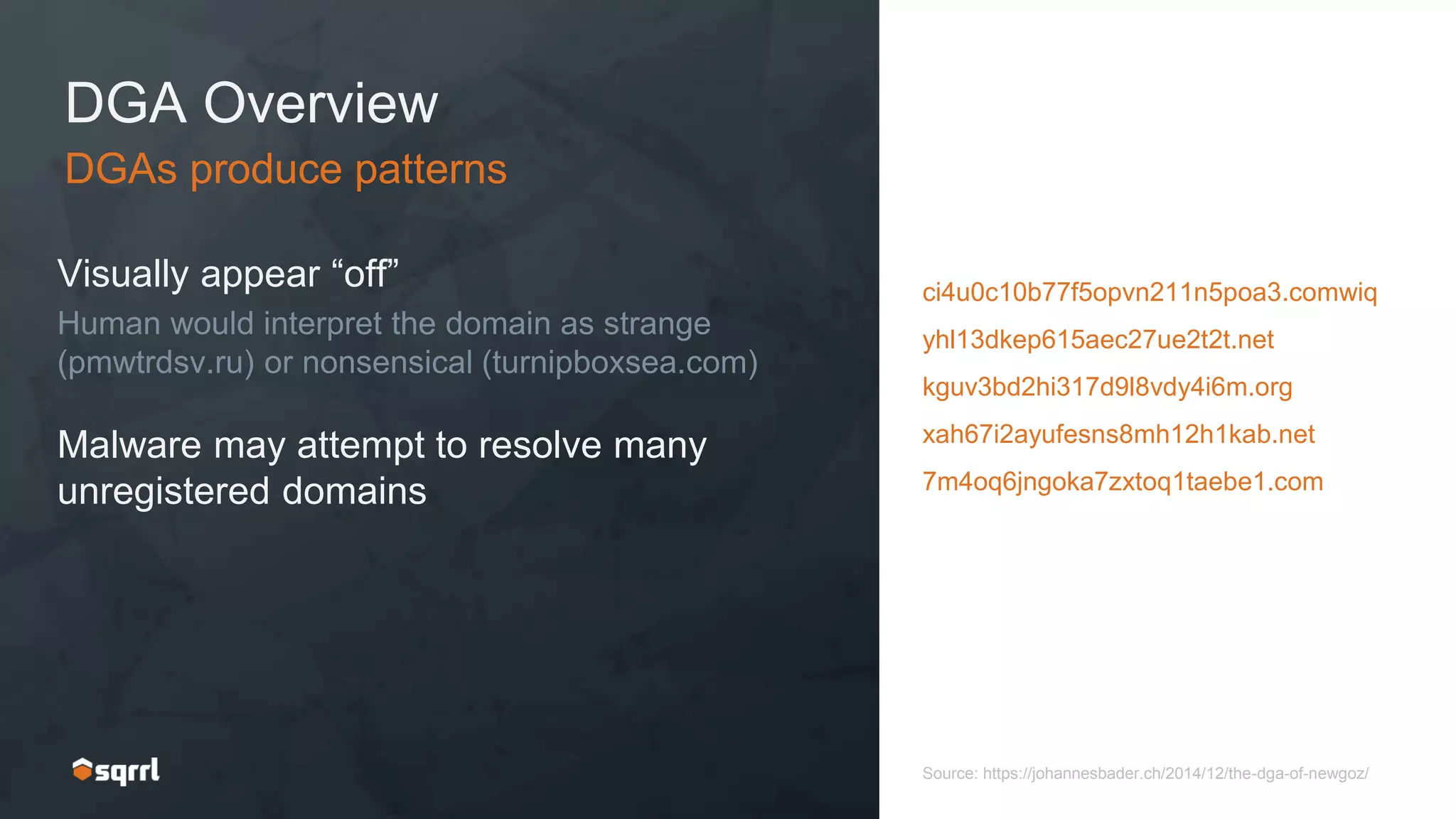
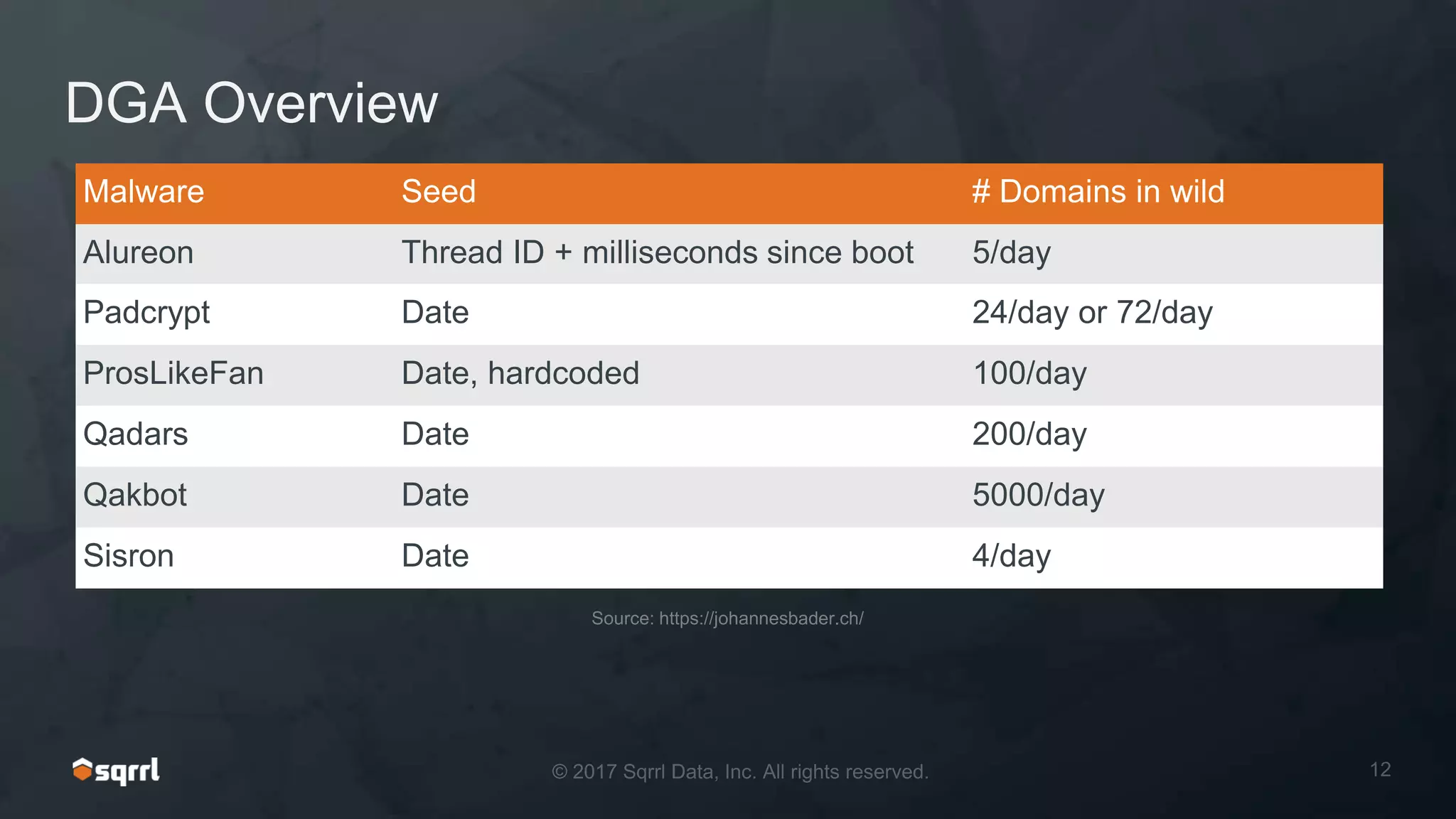
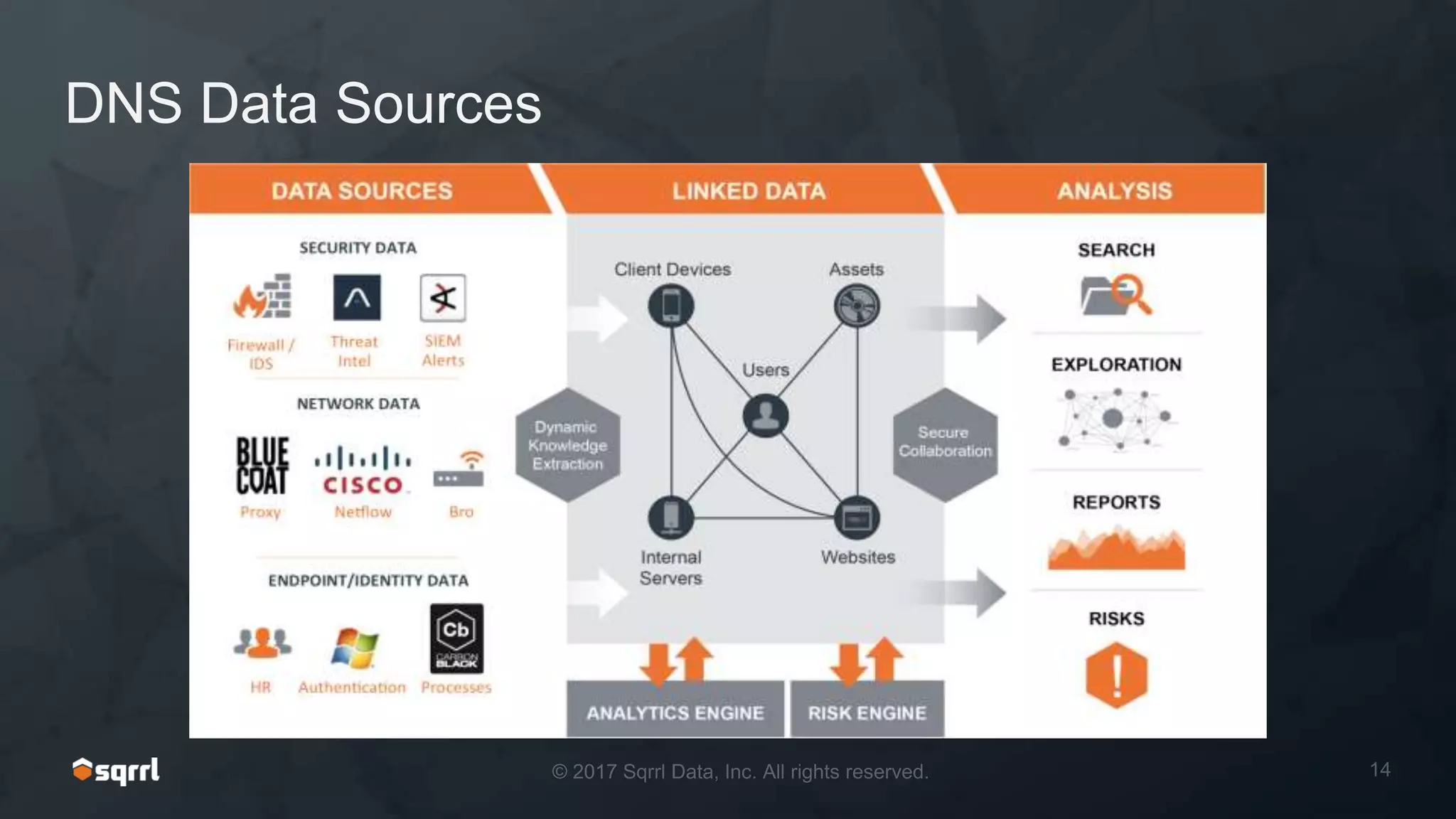
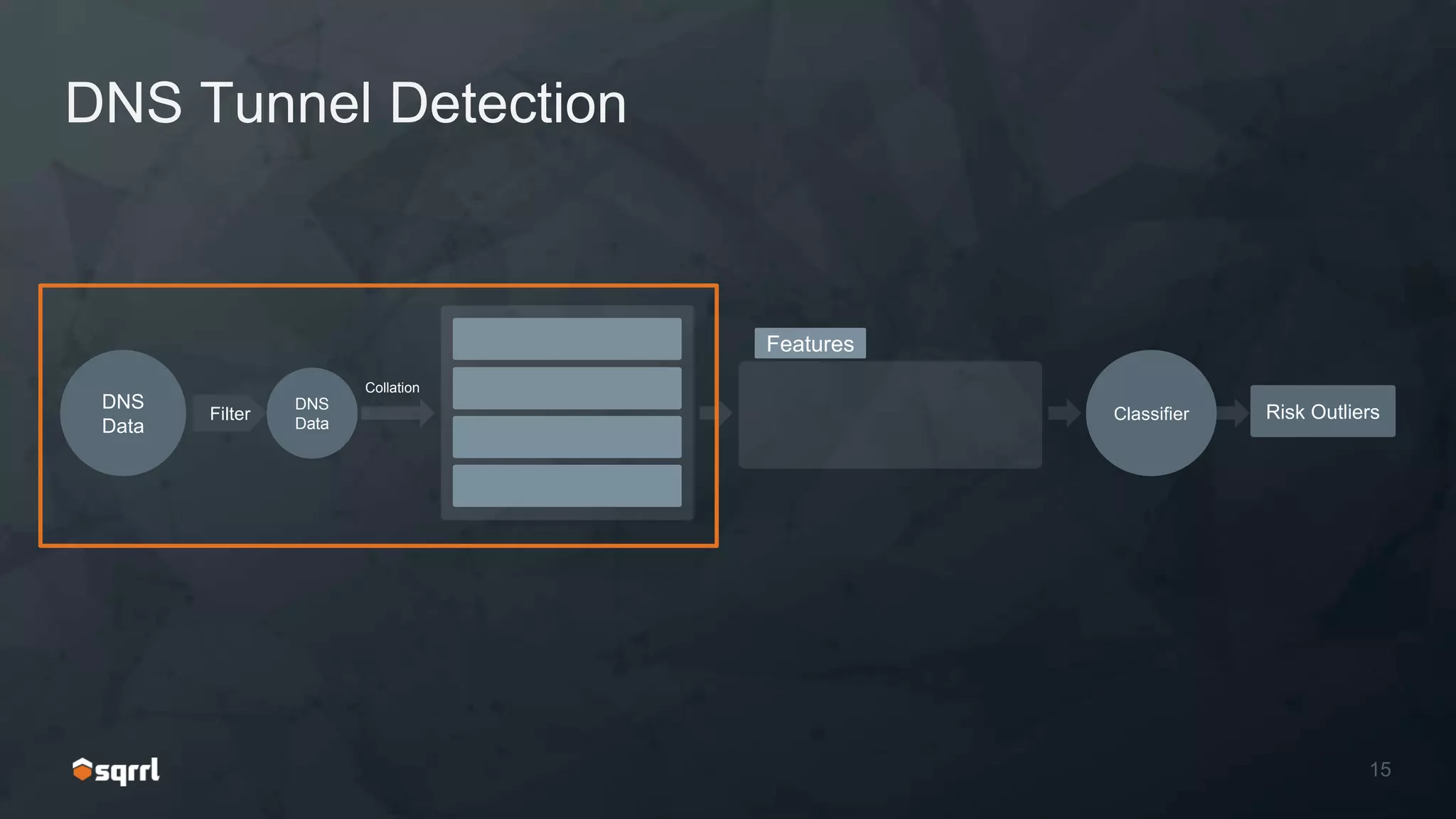
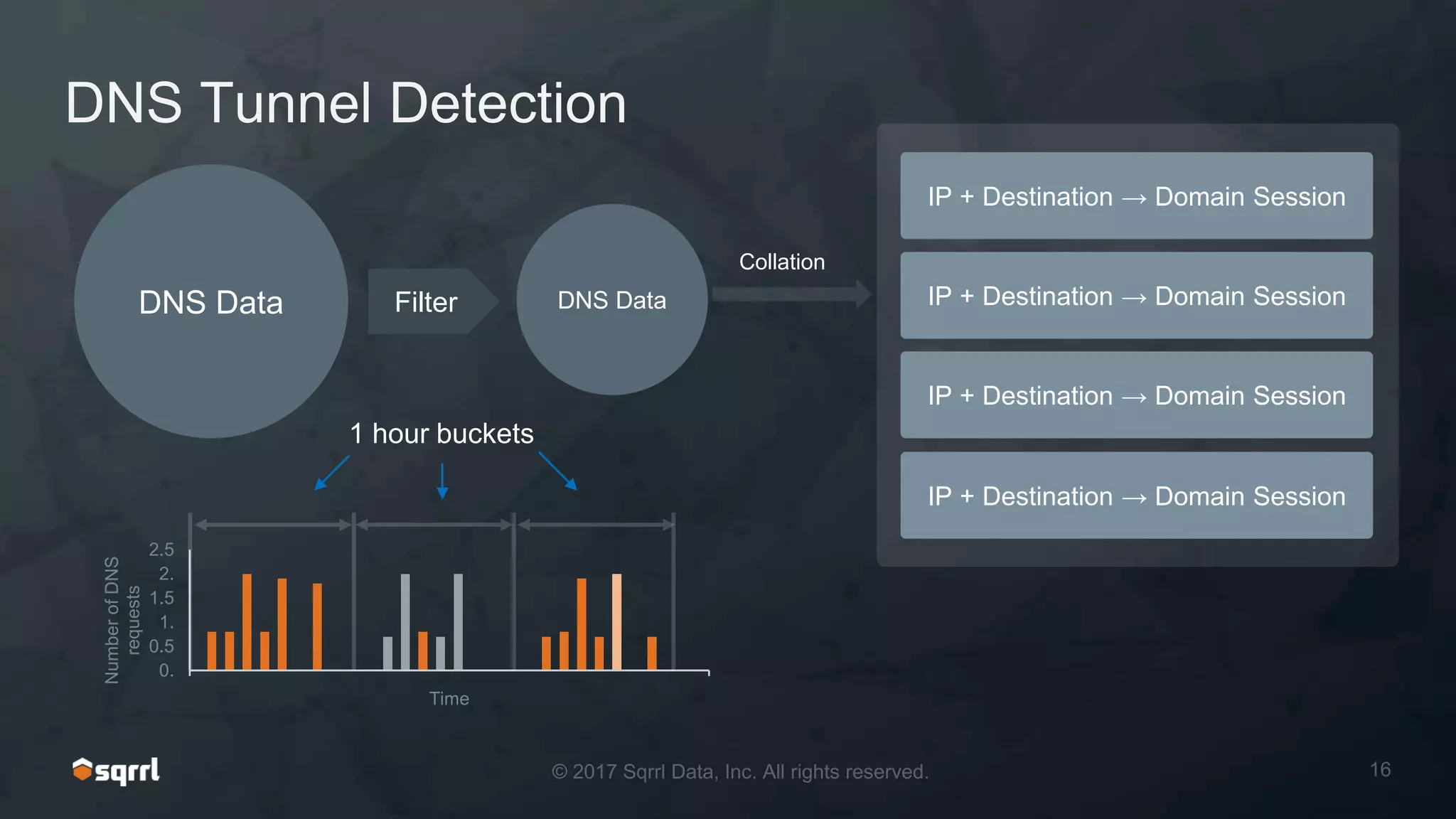
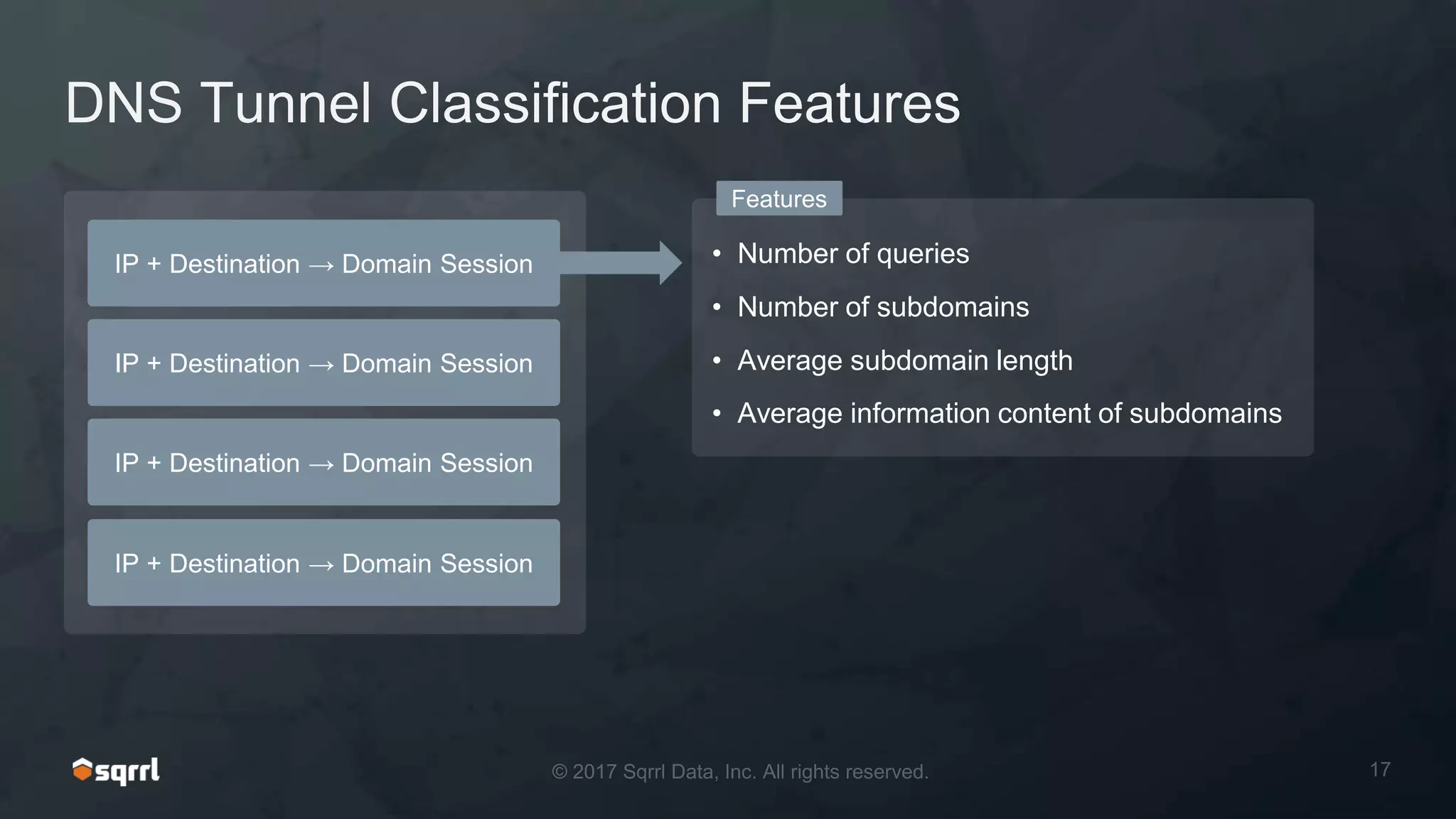
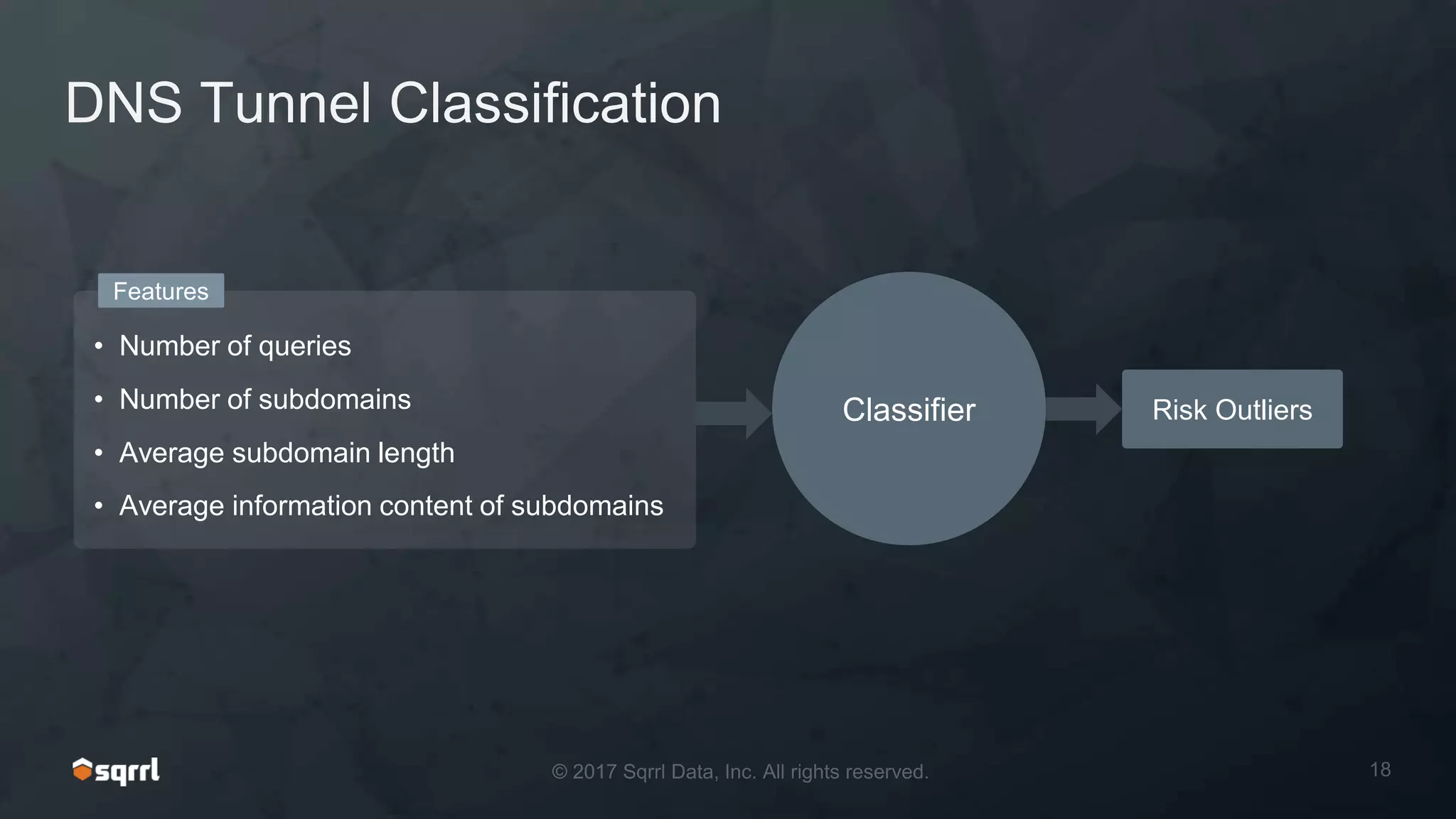
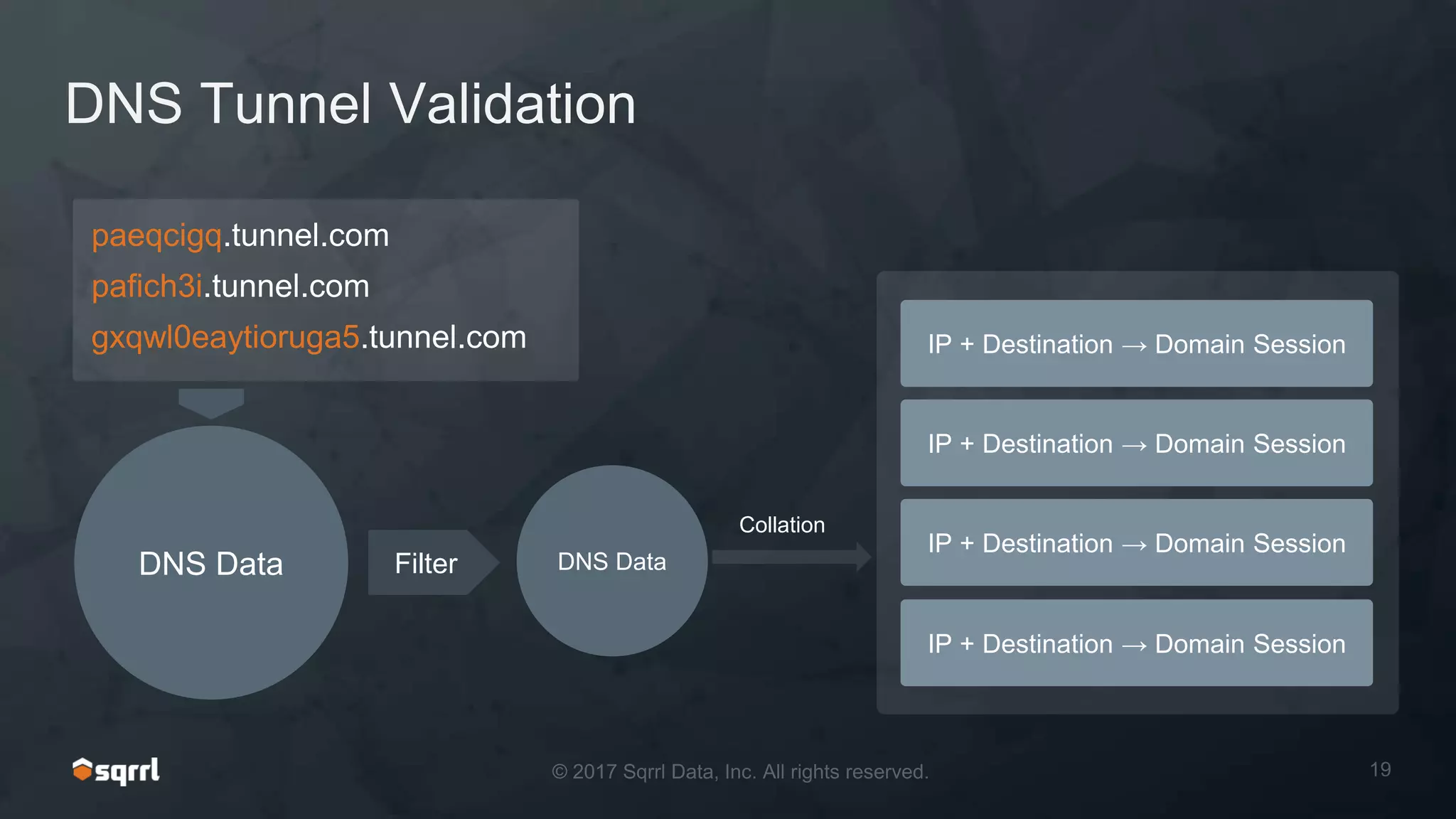
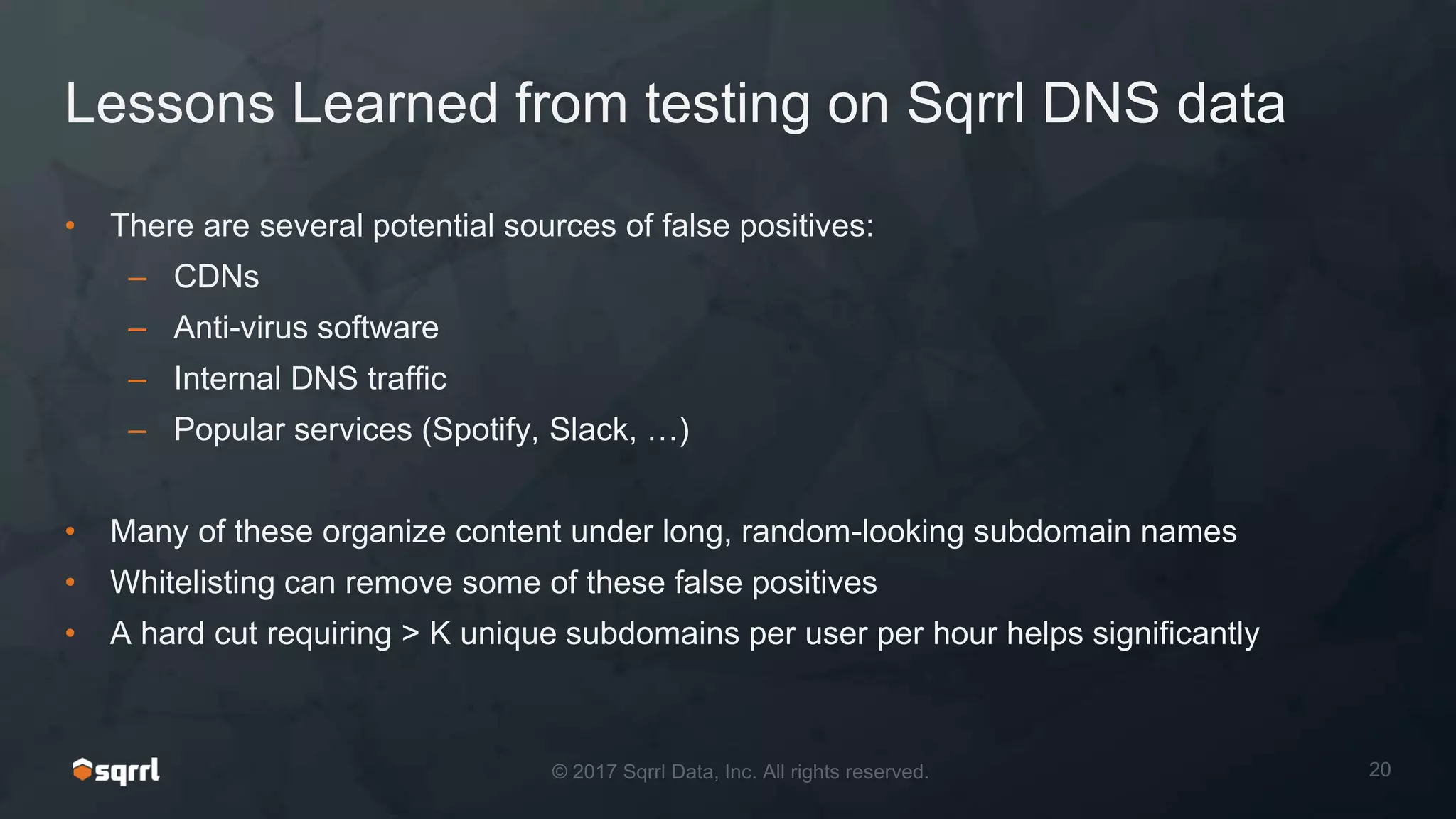
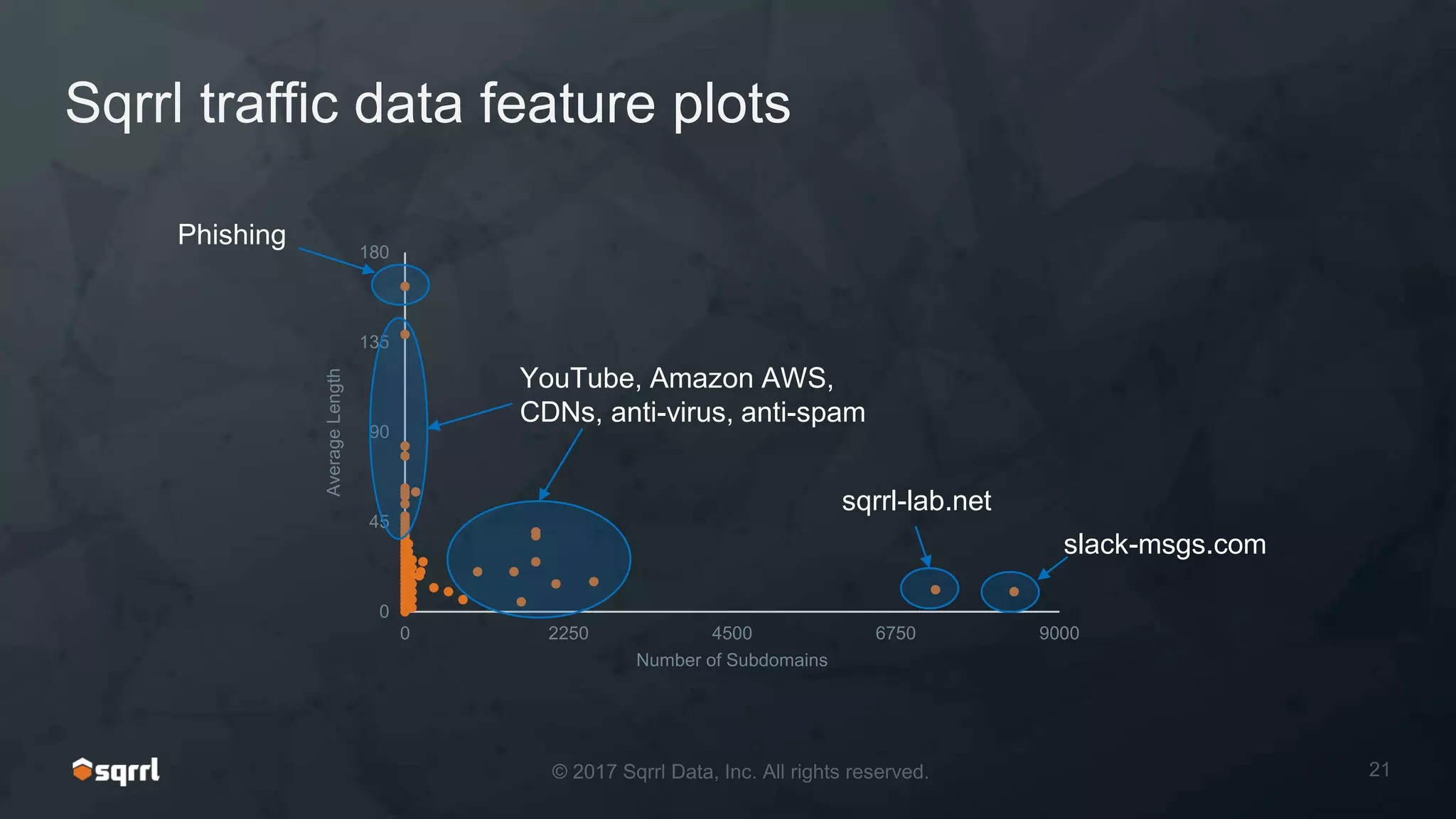
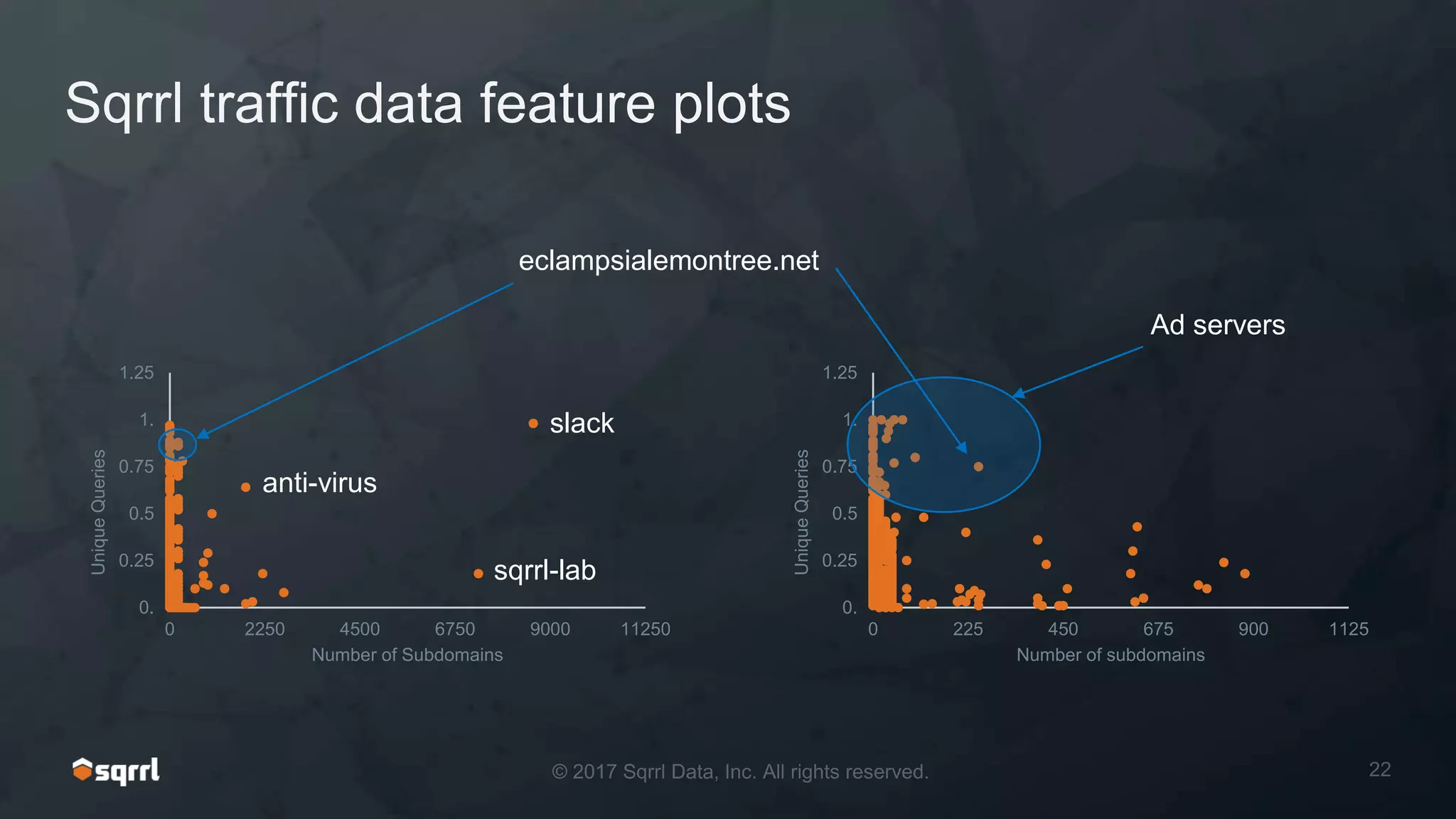
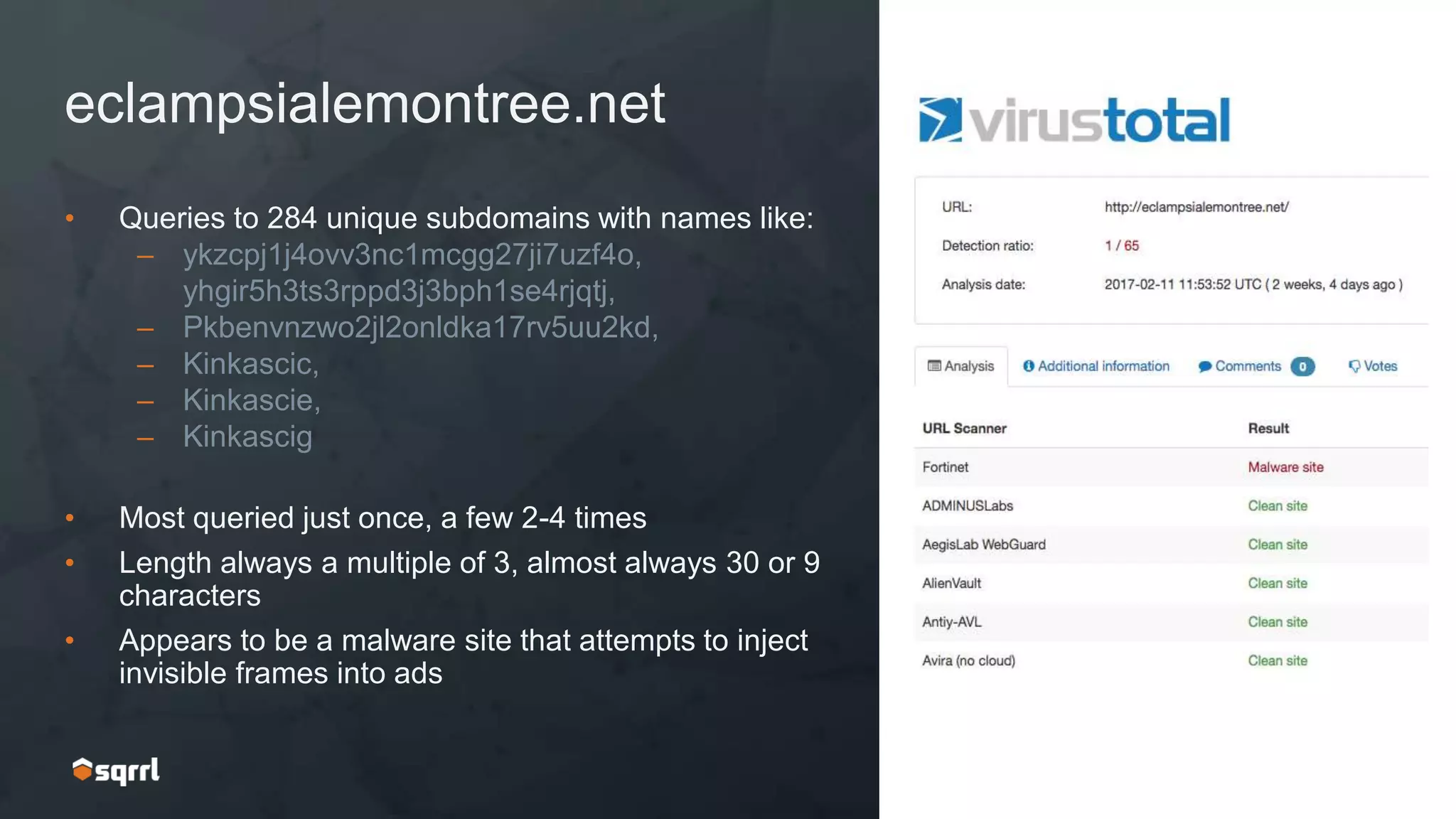
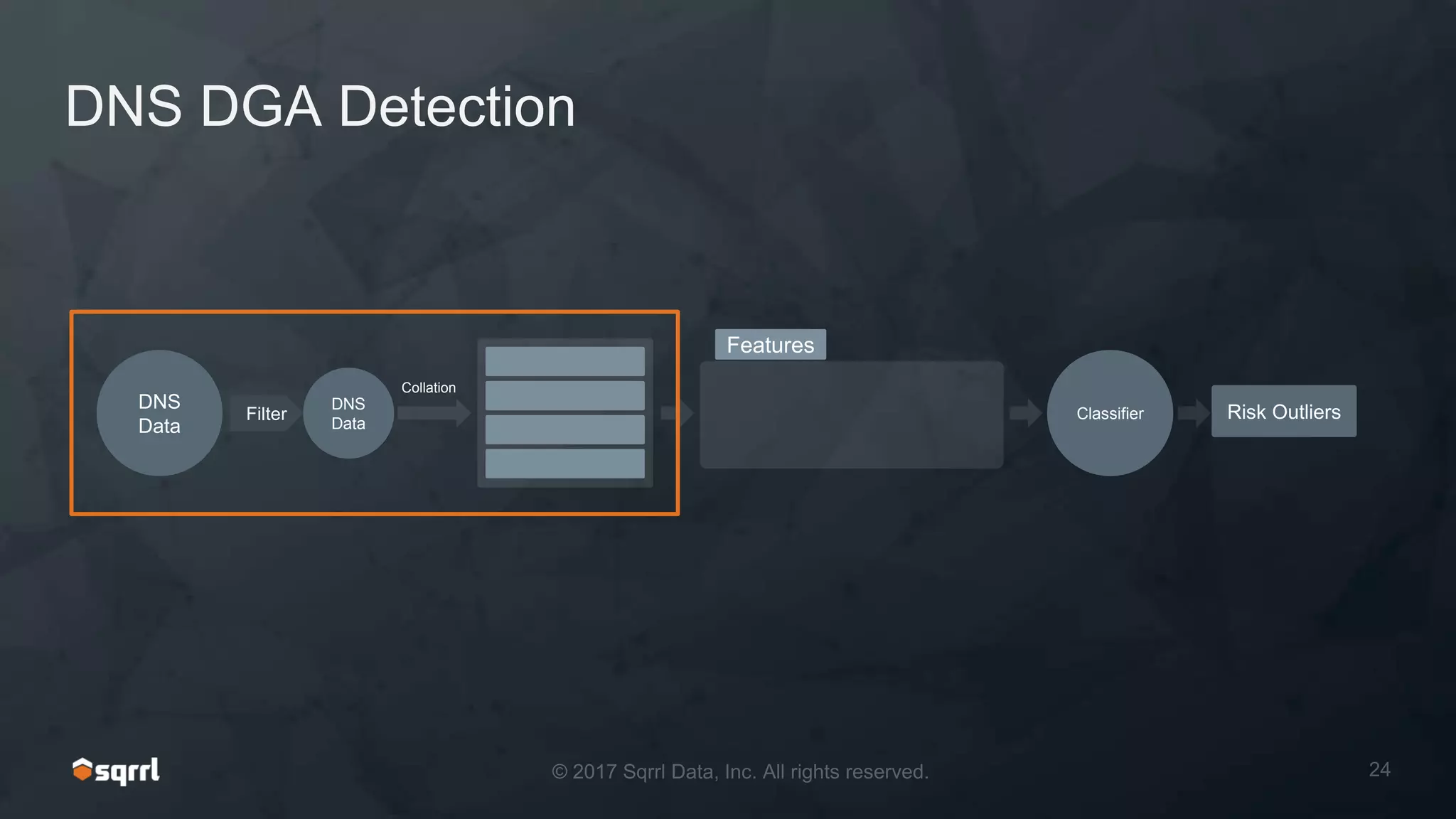
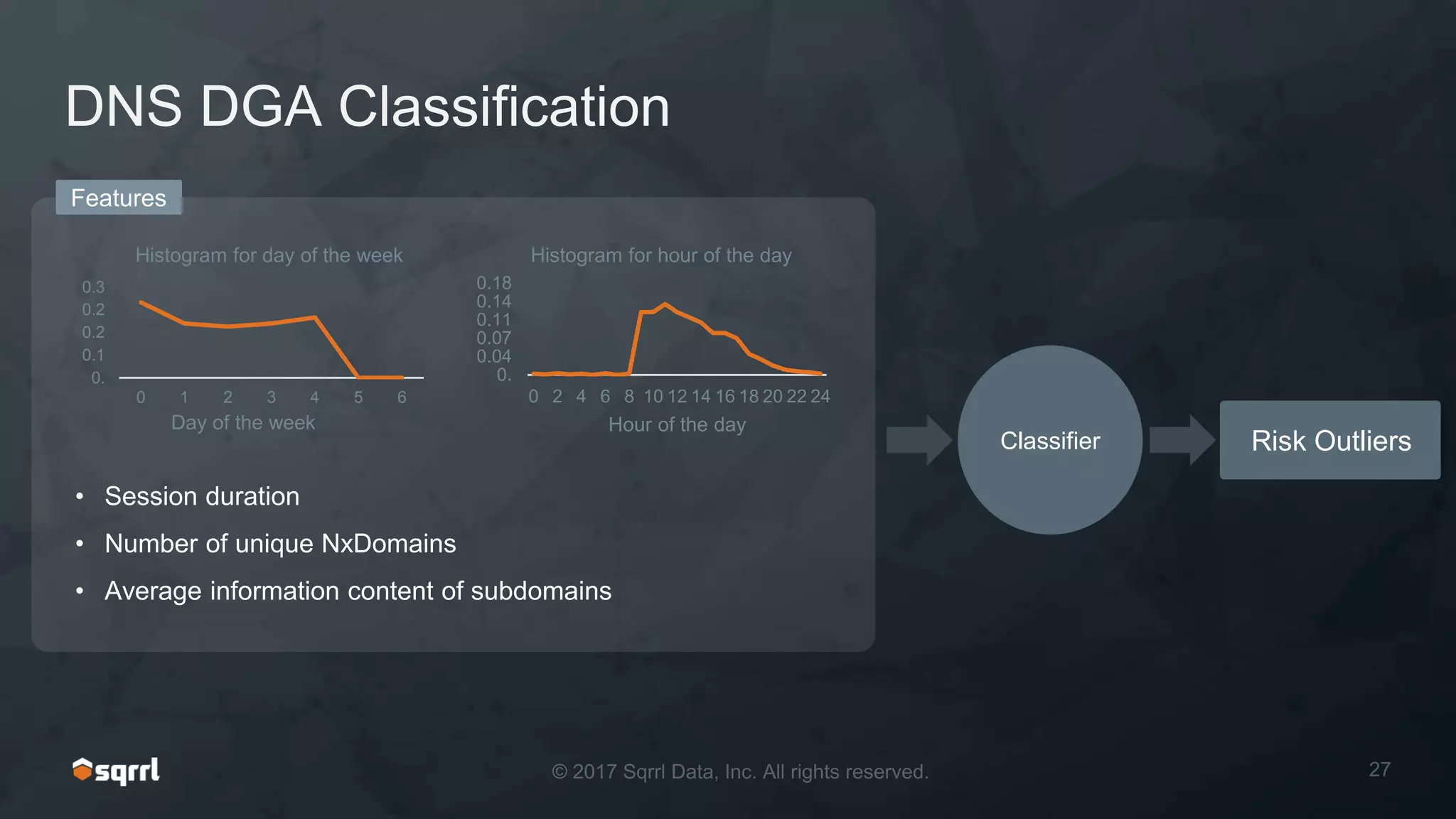
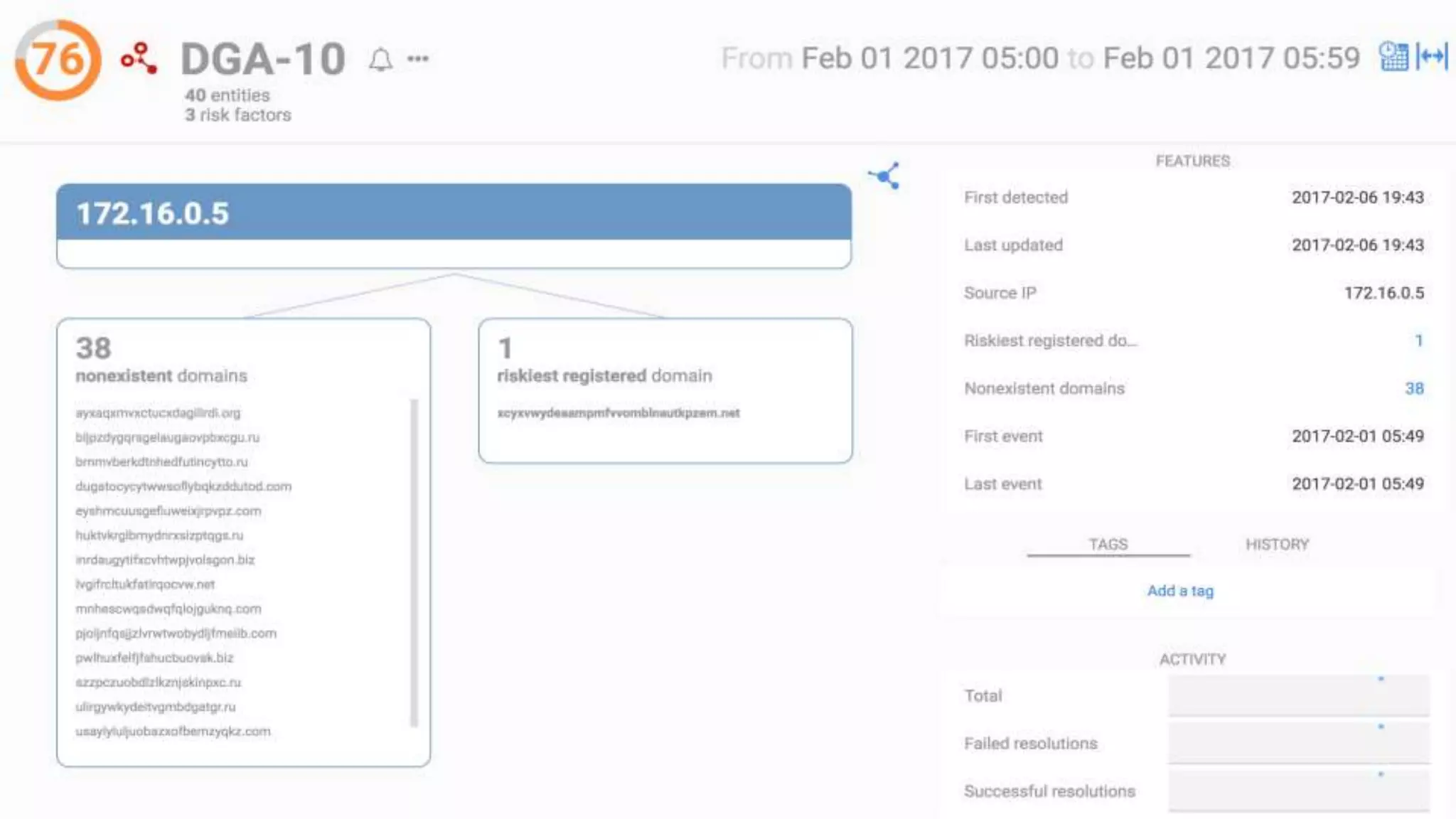
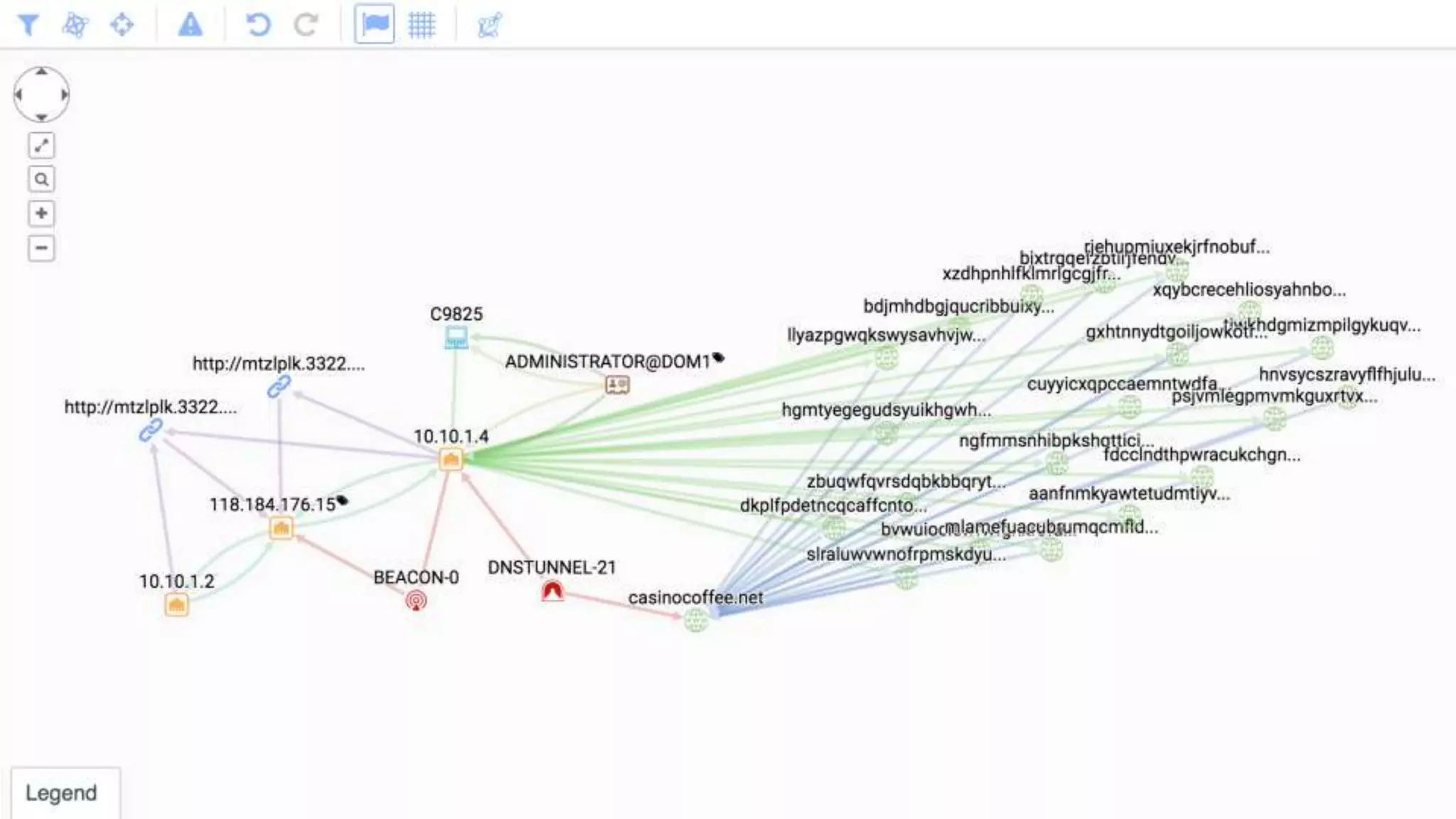
The document discusses techniques for leveraging DNS data to investigate and detect attacker activities such as tunneling and domain generation algorithms (DGA). It outlines how attackers utilize DNS for command and control, data exfiltration, and evading detection, while also presenting various data science methods to identify these threats. A focus is placed on the potential for false positives in detection and recommends strategies for refining detection methodologies.