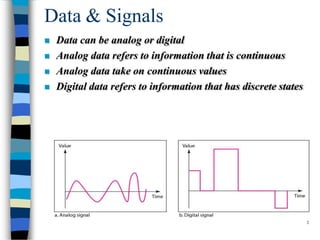
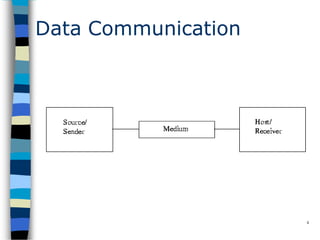
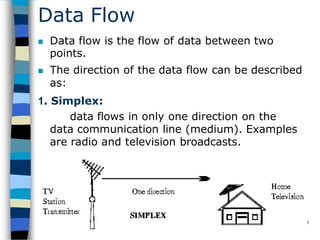
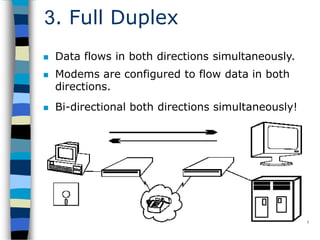
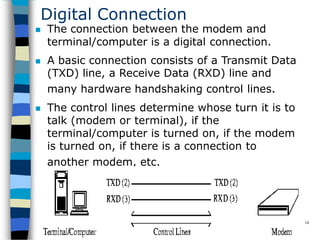
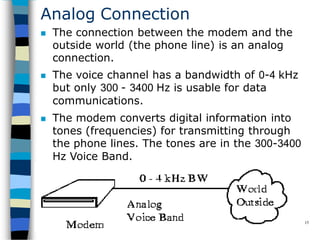
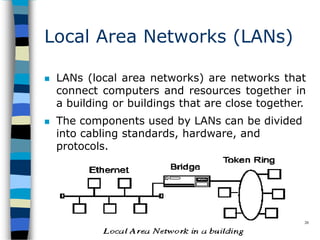
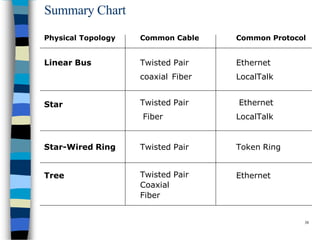
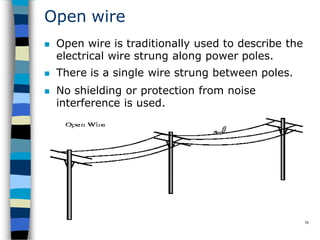
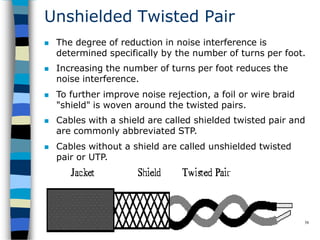
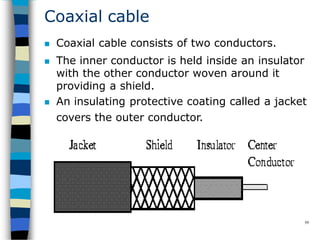
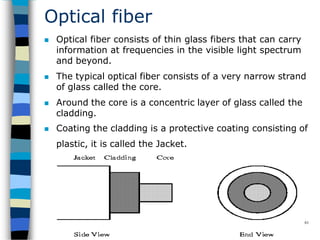
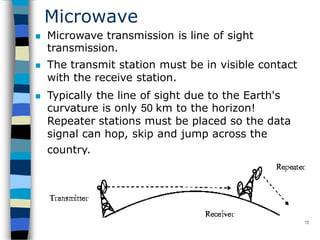
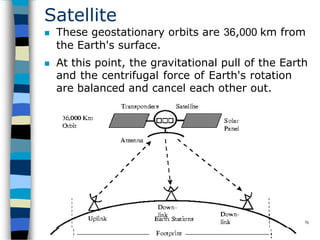
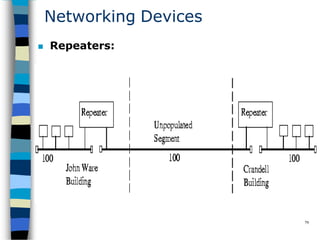
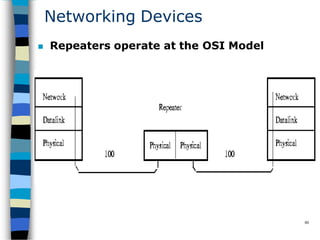
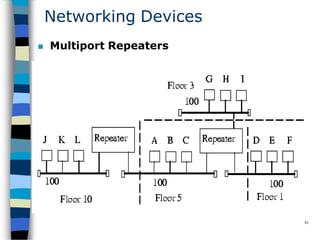
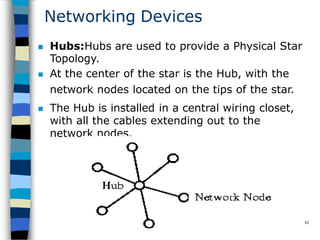
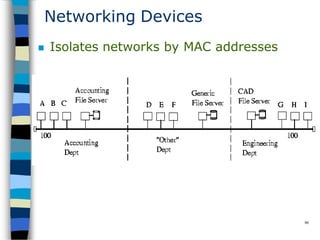
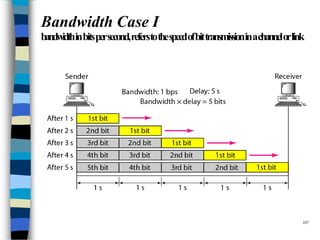
Data communication and networking involves the transfer of data between a source and receiver. There are different types of data (analog and digital) and various methods for data to flow (simplex, half-duplex, and full-duplex). Modems allow computers to transmit digital data over analog networks like telephone lines by modulating and demodulating signals. Common network topologies include bus, star, ring and tree configurations using different transmission media like twisted pair, coaxial or fiber optic cabling. The OSI model defines a framework for network communication using seven stacked layers.