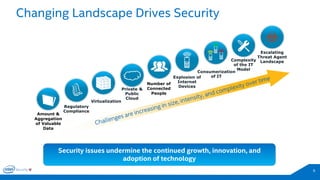
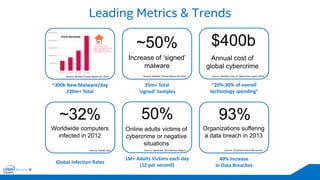
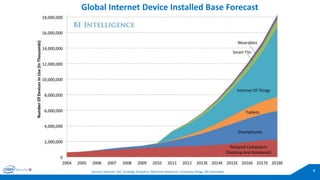
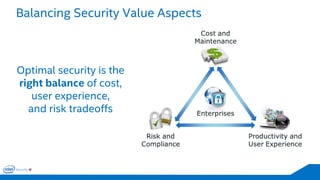
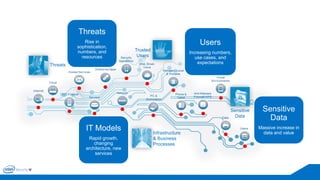
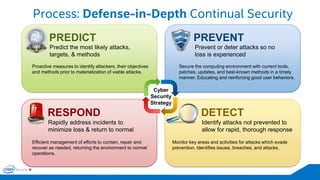
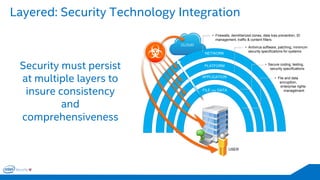
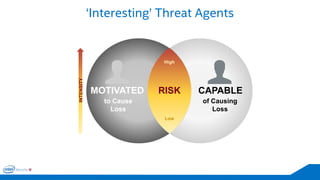
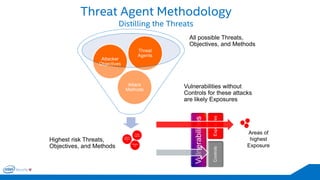
The document discusses the critical importance of leadership in managing cybersecurity risks, emphasizing that without effective leadership, organizations face crises rather than proactive security management. It highlights the increasing sophistication and number of cyber threats, the significant costs associated with cybercrime, and the necessity for a layered security strategy that integrates various technologies and practices. Ultimately, it calls for a collective approach to security, urging organizations to understand their threats and contribute to their own defense to avoid becoming easy targets.