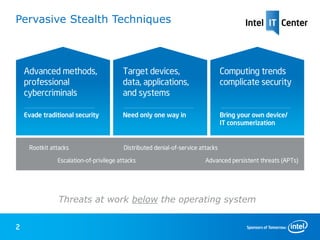
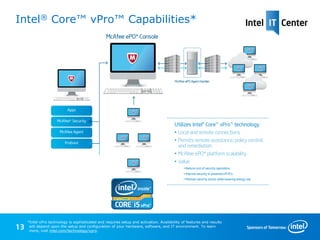
1) Next-generation endpoint security solutions from Intel and McAfee use hardware-assisted security beyond the operating system to detect and remove advanced, hidden threats like rootkits in real time.
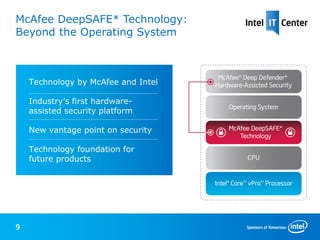
2) McAfee Deep Defender utilizes Intel Core vPro processors and DeepSAFE technology to provide kernel-level monitoring and block stealthy attacks that evade traditional OS-based security.
3) McAfee ePO Deep Command enhances security management by leveraging Intel Core vPro capabilities to remotely control powered-off endpoints, perform remediation, and easily manage mobile PCs.