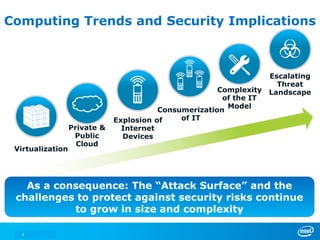
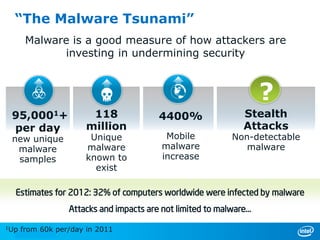
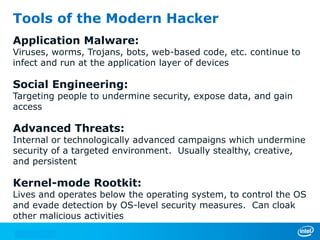
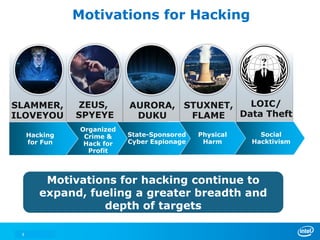
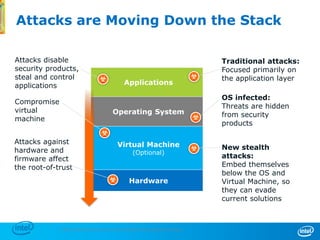
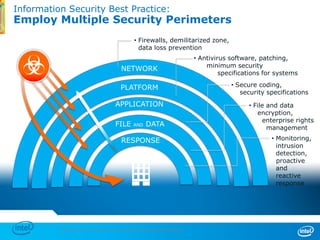
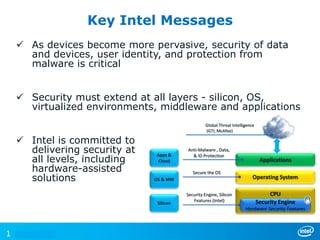
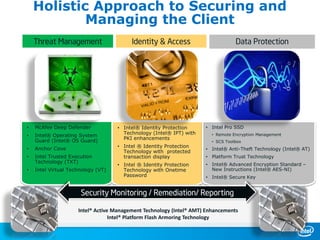
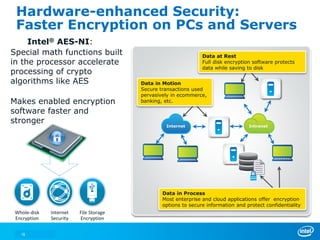
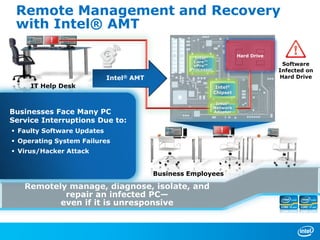
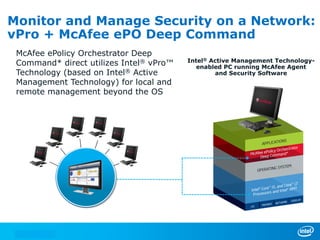
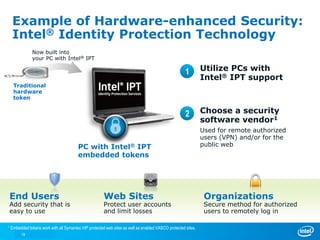
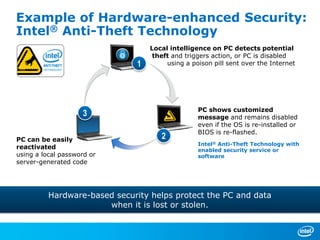
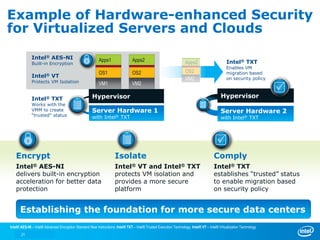
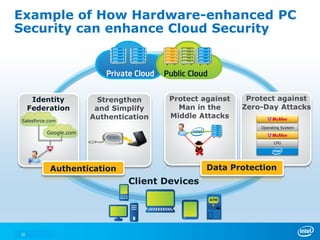
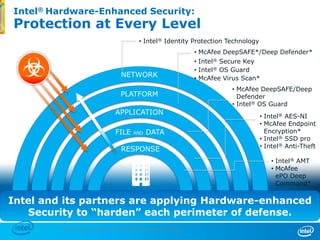
The document discusses cyber security trends, solutions from Intel and McAfee, and opportunities for hardware-enhanced security. It notes that the threat landscape and attack surfaces are growing in complexity. Intel and McAfee aim to deliver security at all levels including the silicon, operating system, virtualized environments, and applications. Examples are given of how hardware features can accelerate encryption and provide more robust protection for devices, servers, and cloud environments against viruses, malware, and advanced threats.