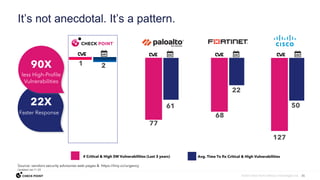
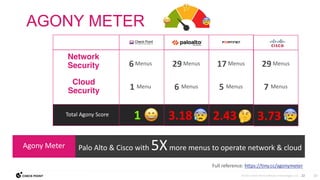
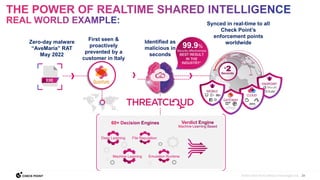
The document discusses the need for comprehensive, collaborative, and consolidated cybersecurity and argues that second best security will result in a breach. It notes that while all vendors claim to have the best security, only Check Point delivers real-time prevention across all attack vectors from code to cloud through its 3Cs approach. Check Point's threat prevention is powered by its threat intelligence cloud, ThreatCloud, which collects big data from over 2 billion daily inspections to identify emerging threats.















![17
©2023 Check Point Software Technologies Ltd.
NOT ALL VENDORS PROVIDE
REAL-TIME PREVENTION
“SHUT DOWN THE NETWORK”?!
[Protected] Distribution or modification is subject to approval 17](https://image.slidesharecdn.com/cpx23moti2ndbestsecwillgetubreachedv11-230130205144-b9d679c7/85/CPX23_Moti_2nd_best_sec_will_get_u_breached_v11-pdf-17-320.jpg)


![20
©2023 Check Point Software Technologies Ltd.
[Internal Use] for Check Point employees
INFINITY
CONSOLIDATION. ONE PORTAL TO MANAGE ALL PRODUCTS](https://image.slidesharecdn.com/cpx23moti2ndbestsecwillgetubreachedv11-230130205144-b9d679c7/85/CPX23_Moti_2nd_best_sec_will_get_u_breached_v11-pdf-20-320.jpg)
![21
©2023 Check Point Software Technologies Ltd.
[Internal Use] for Check Point employees
CHECK POINT INFINITY
ONE PORTAL TO MANAGE ALL PRODUCTS
VS](https://image.slidesharecdn.com/cpx23moti2ndbestsecwillgetubreachedv11-230130205144-b9d679c7/85/CPX23_Moti_2nd_best_sec_will_get_u_breached_v11-pdf-21-320.jpg)





![28
©2023 Check Point Software Technologies Ltd.
AI is all about your data
[Internal Use] for Check Point employees
2,000,000,000
Websites and files inspected
Counted
DAILY!
20,000,000
Potential IoT devices
1,500,000
Newly installed mobile apps
73,000,000
Full content emails
1,000,000
Online web forms
2,000,000
Malicious indicators
Big data threat intelligence:
30,000,000
File emulations](https://image.slidesharecdn.com/cpx23moti2ndbestsecwillgetubreachedv11-230130205144-b9d679c7/85/CPX23_Moti_2nd_best_sec_will_get_u_breached_v11-pdf-28-320.jpg)

![31
©2023 Check Point Software Technologies Ltd.
Validated by 3rd party (Miercom):
THE BEST PROTECTION AND VALUE TO OUR CUSTOMERS
[Protected] Distribution or modification is subject to approval 31
99.7%
99.7%](https://image.slidesharecdn.com/cpx23moti2ndbestsecwillgetubreachedv11-230130205144-b9d679c7/85/CPX23_Moti_2nd_best_sec_will_get_u_breached_v11-pdf-31-320.jpg)

![33
©2023 Check Point Software Technologies Ltd.
[Restricted] ONLY for designated groups and individuals](https://image.slidesharecdn.com/cpx23moti2ndbestsecwillgetubreachedv11-230130205144-b9d679c7/85/CPX23_Moti_2nd_best_sec_will_get_u_breached_v11-pdf-33-320.jpg)