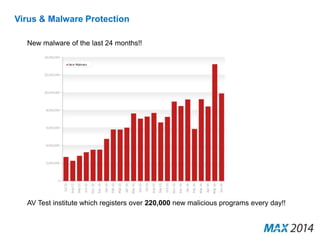
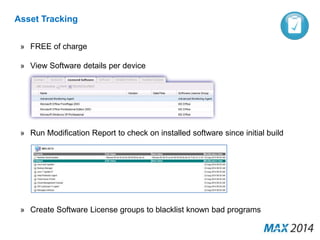
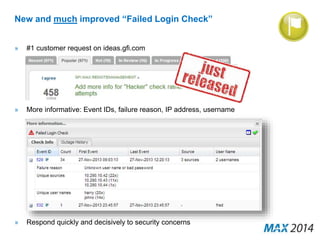
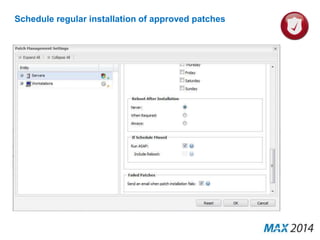
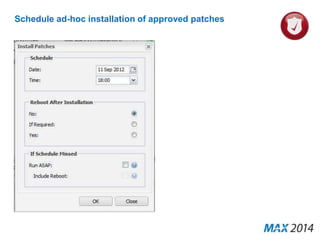
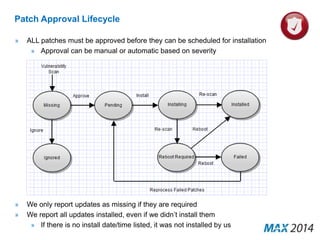
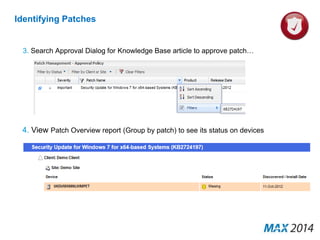
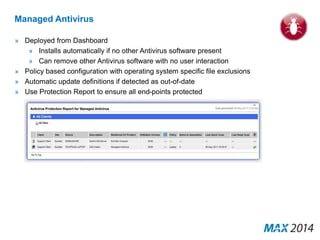
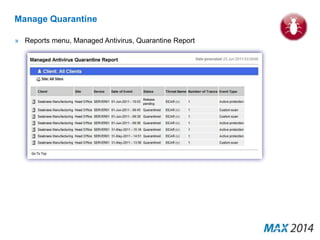
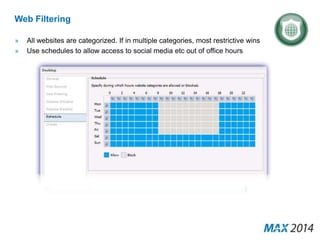
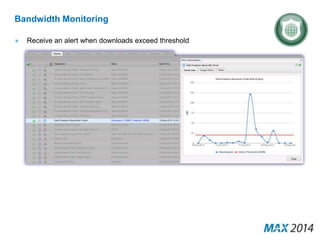
The document emphasizes the critical importance of cybersecurity, illustrating the severity of cyber attacks through historical case studies and highlighting the financial impact on organizations. It outlines a multi-layer approach to security, detailing key mitigation strategies, software patch management, and proactive measures for data protection, including managed antivirus and web security. Additionally, it discusses the projected growth of the managed security services market and the increasing reliance of organizations on external security services due to skill shortages.