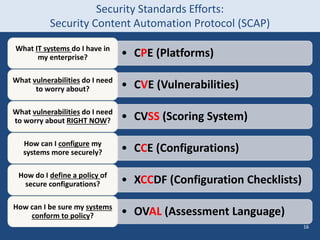
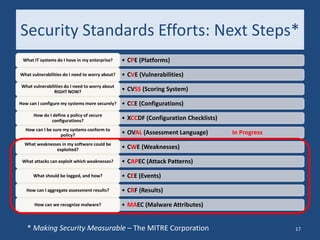
The document discusses the history and future of cyber security. It covers how the internet has changed security, current cyber threats facing the nation, and recommendations from a cyber security commission. The author advocates for near-term actions like updating procurement practices and the FISMA framework, as well as longer-term initiatives to fundamentally change security approaches and business models through standards like SCAP and new workforce development. The overall message is that cyber security must be treated as a high priority through cooperative public-private efforts.