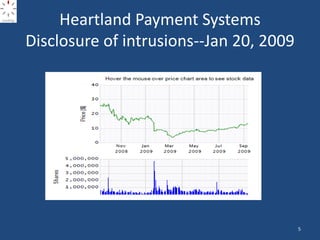
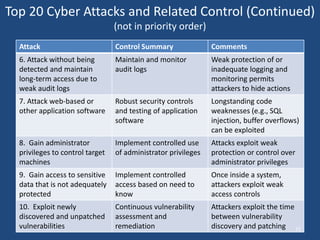
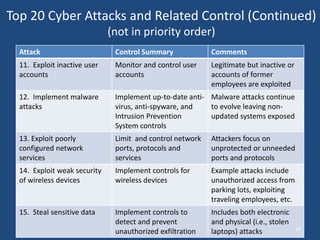
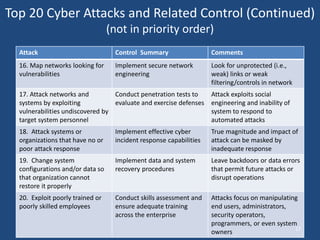
The document discusses the critical state of cyber security, emphasizing it as a national security crisis exacerbated by increasing threats and vulnerabilities. It recommends immediate actions, such as appointing a cybersecurity official and enhancing public-private partnerships, while also outlining longer-term goals for improved security practices and infrastructure. The importance of a robust cyber defense strategy and the transformation of the software industry to ensure security and resilience are highlighted.