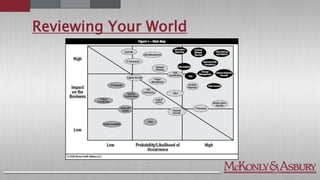
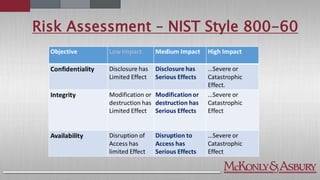
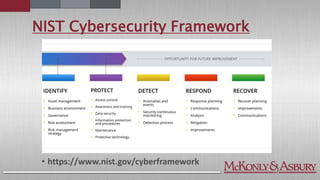
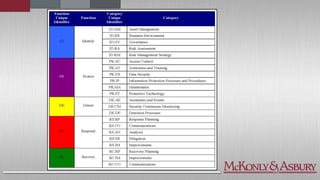
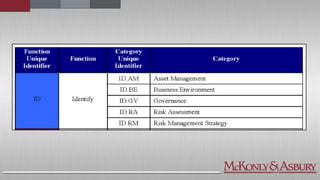
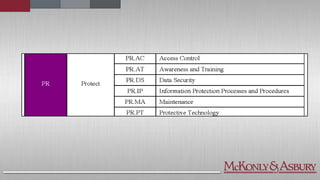
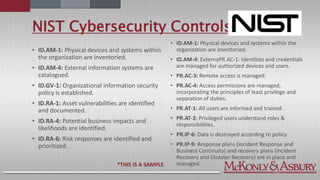
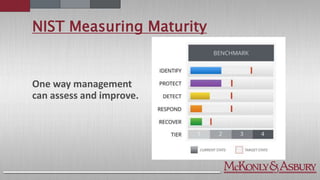
The document discusses the importance of cybersecurity frameworks in organizations, focusing on their benefits and drawbacks, as well as best practices for effective implementation. It highlights the necessity of conducting security risk assessments, understanding various types of cybercrime, and emphasizes the integration of structured frameworks like the NIST Cybersecurity Framework for better risk management. Additionally, it provides insights on developing successful employee relationships and the importance of communication and continuous improvement in mitigating fraud and risk.