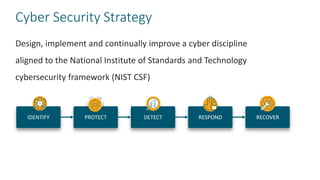
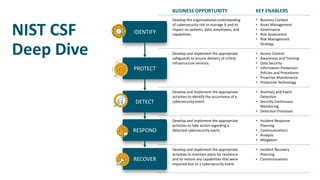
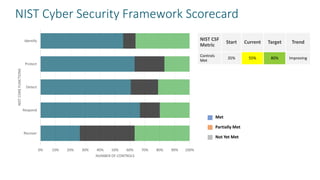
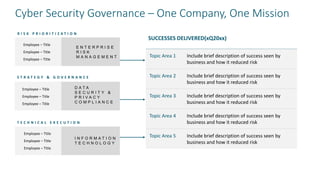
The document provides guidelines for slides on cyber security topics. It includes sections on framing cyber security using the NIST framework, doing a deep dive on the NIST CSF, populating a NIST scorecard, mapping security stakeholders and describing successes, presenting operational metrics from security technologies and the security team, and including a risk metric dashboard. The agenda covers cyber security strategy, the NIST CSF scorecard, governance, operational metrics on defense, and a risk matrix dashboard.