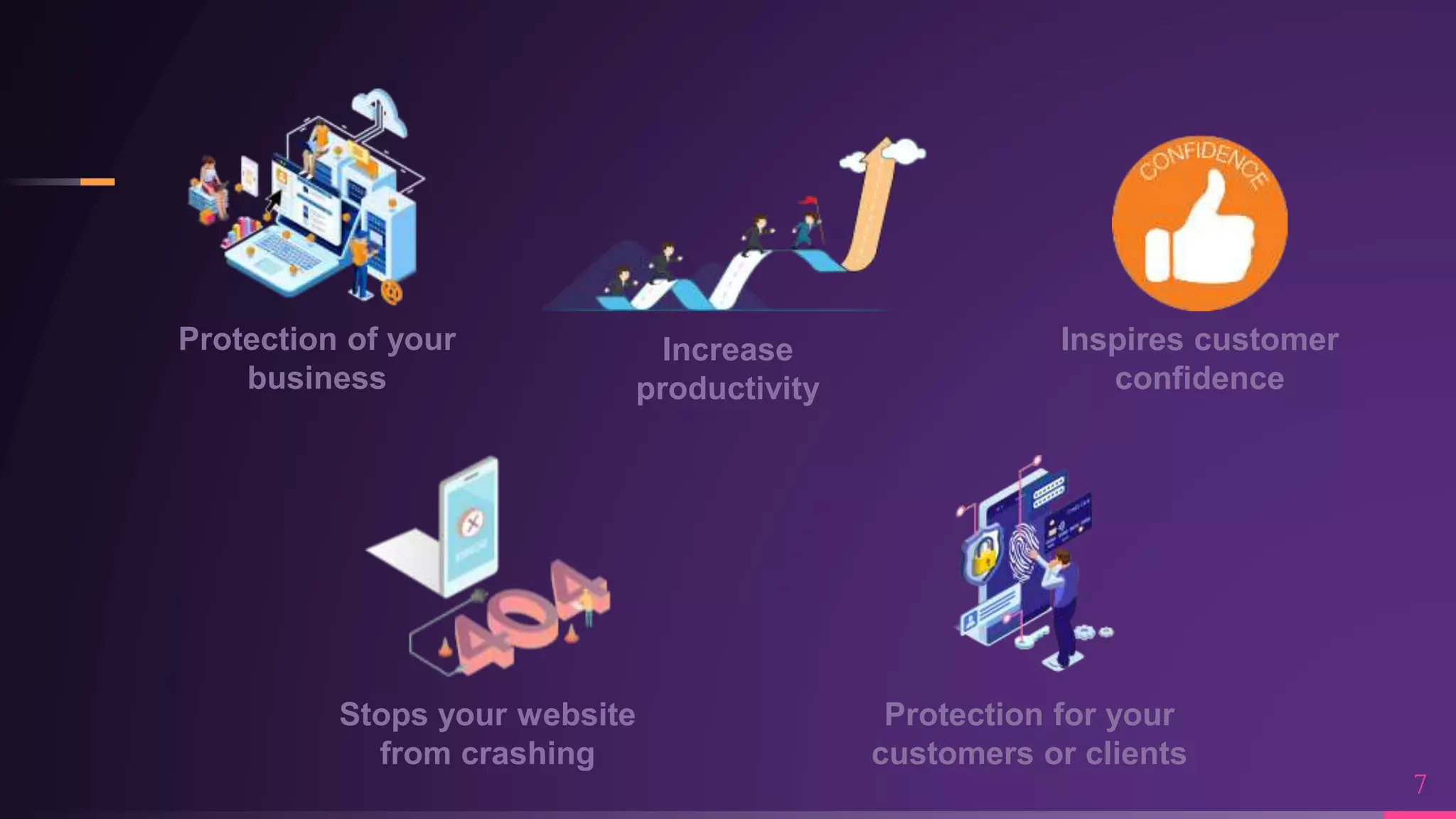
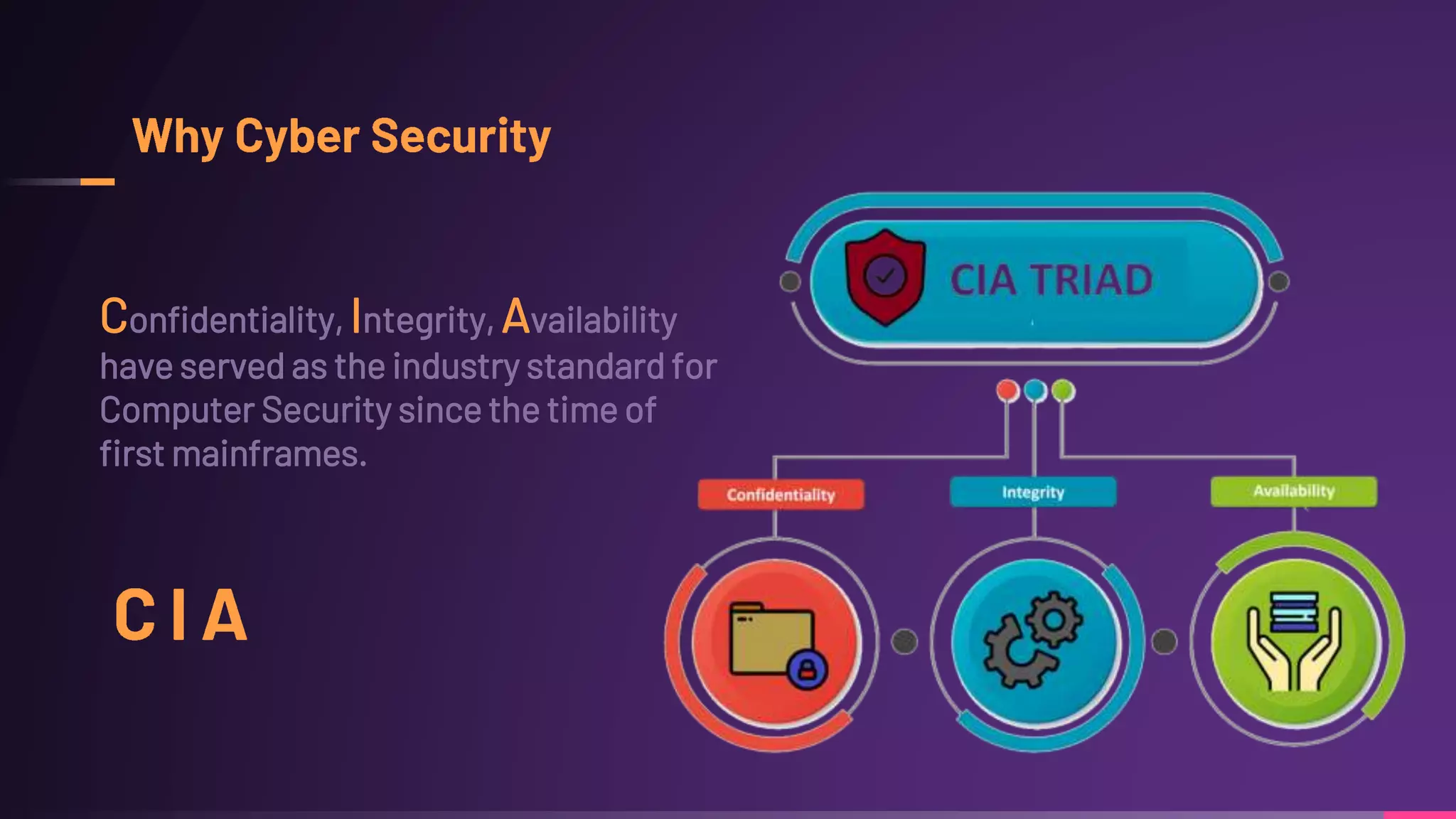
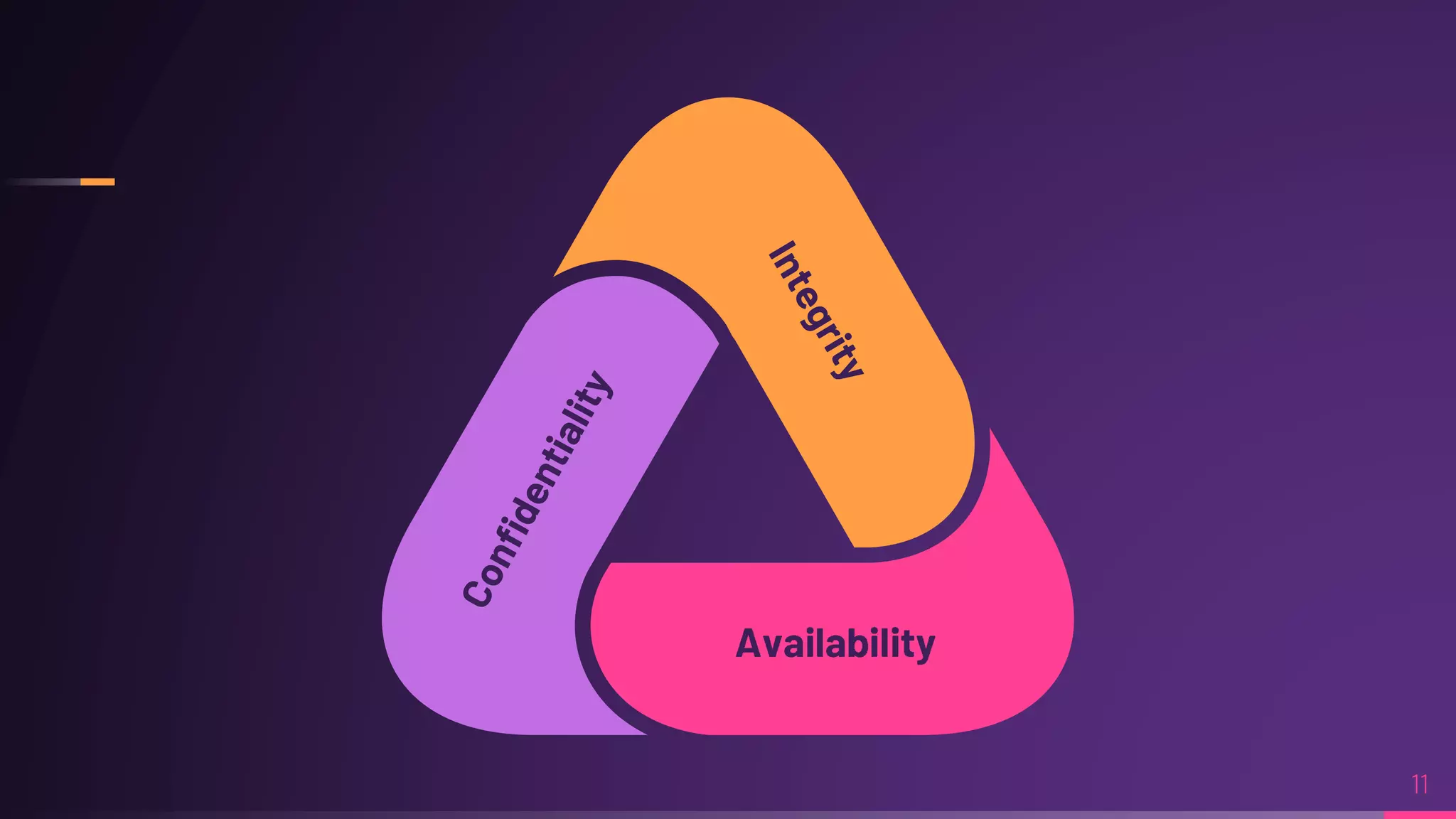
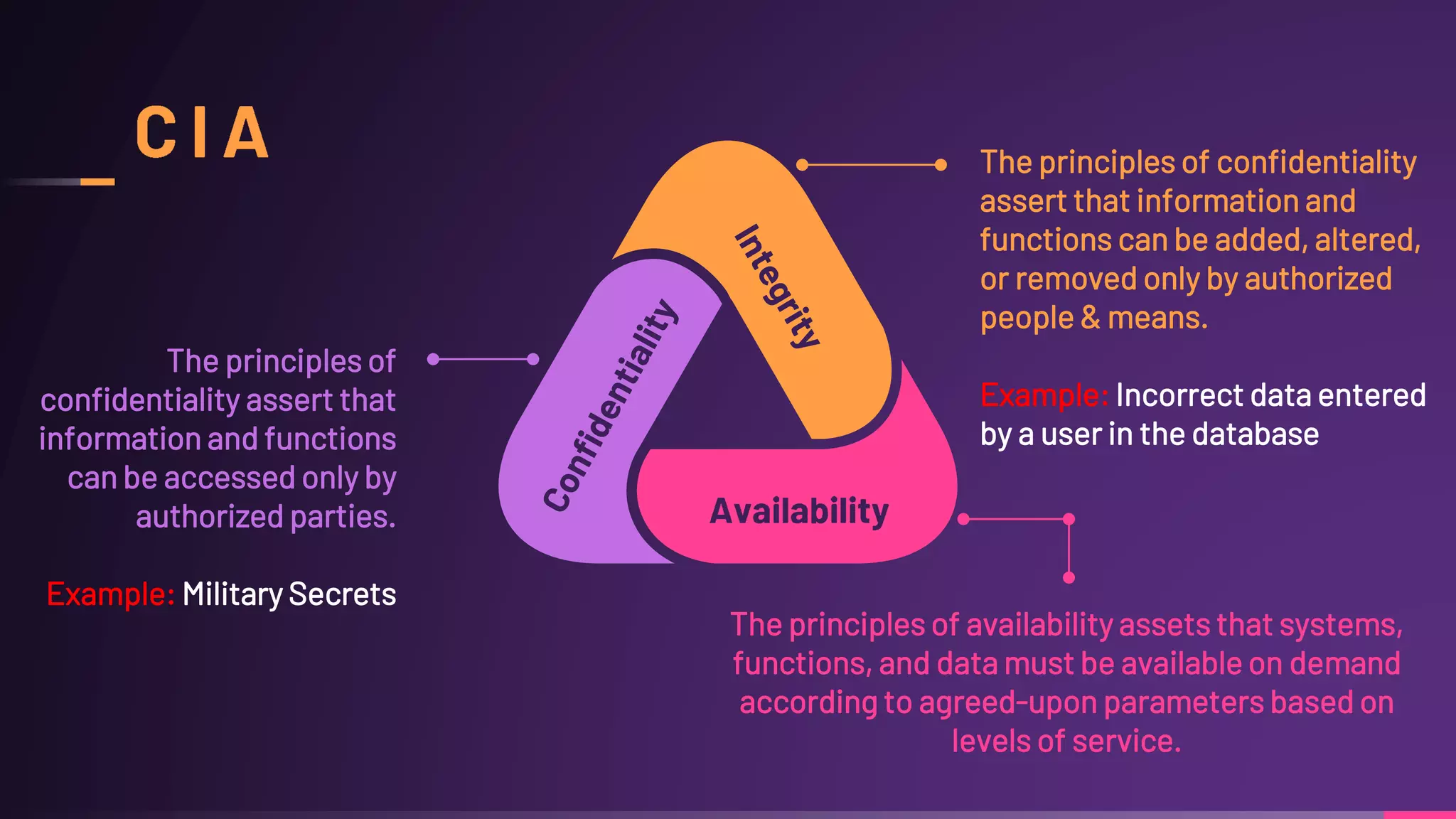
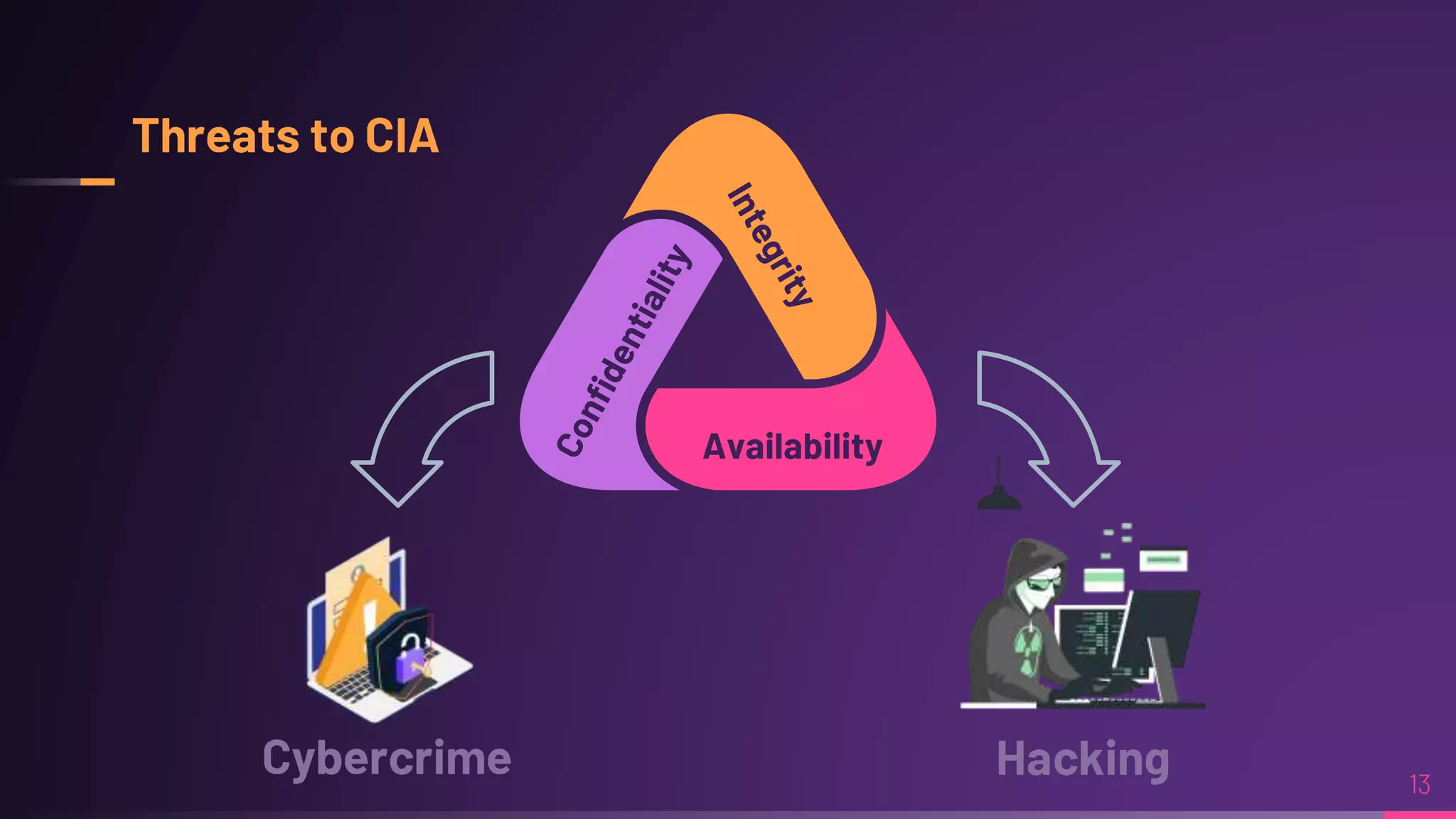
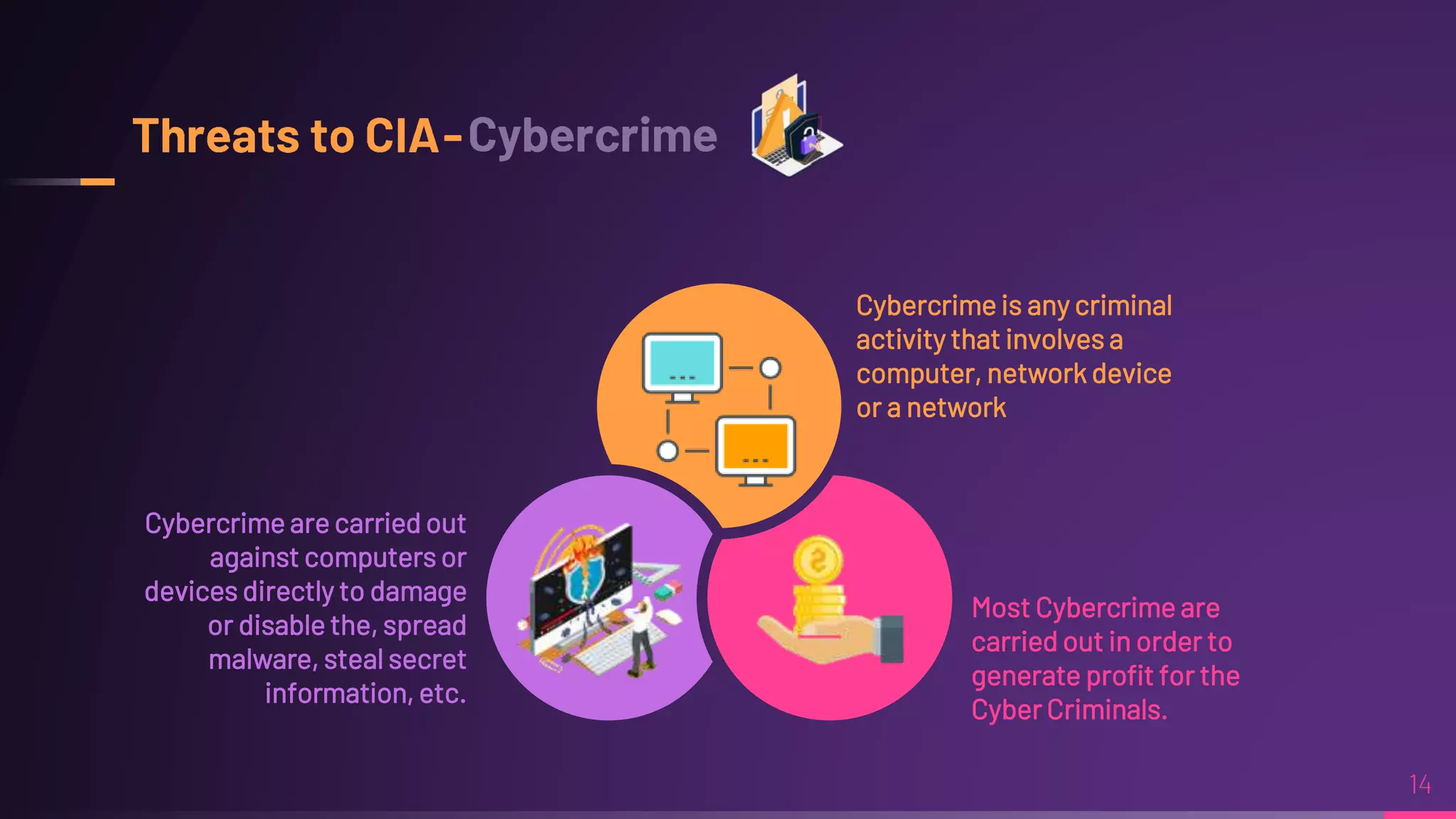
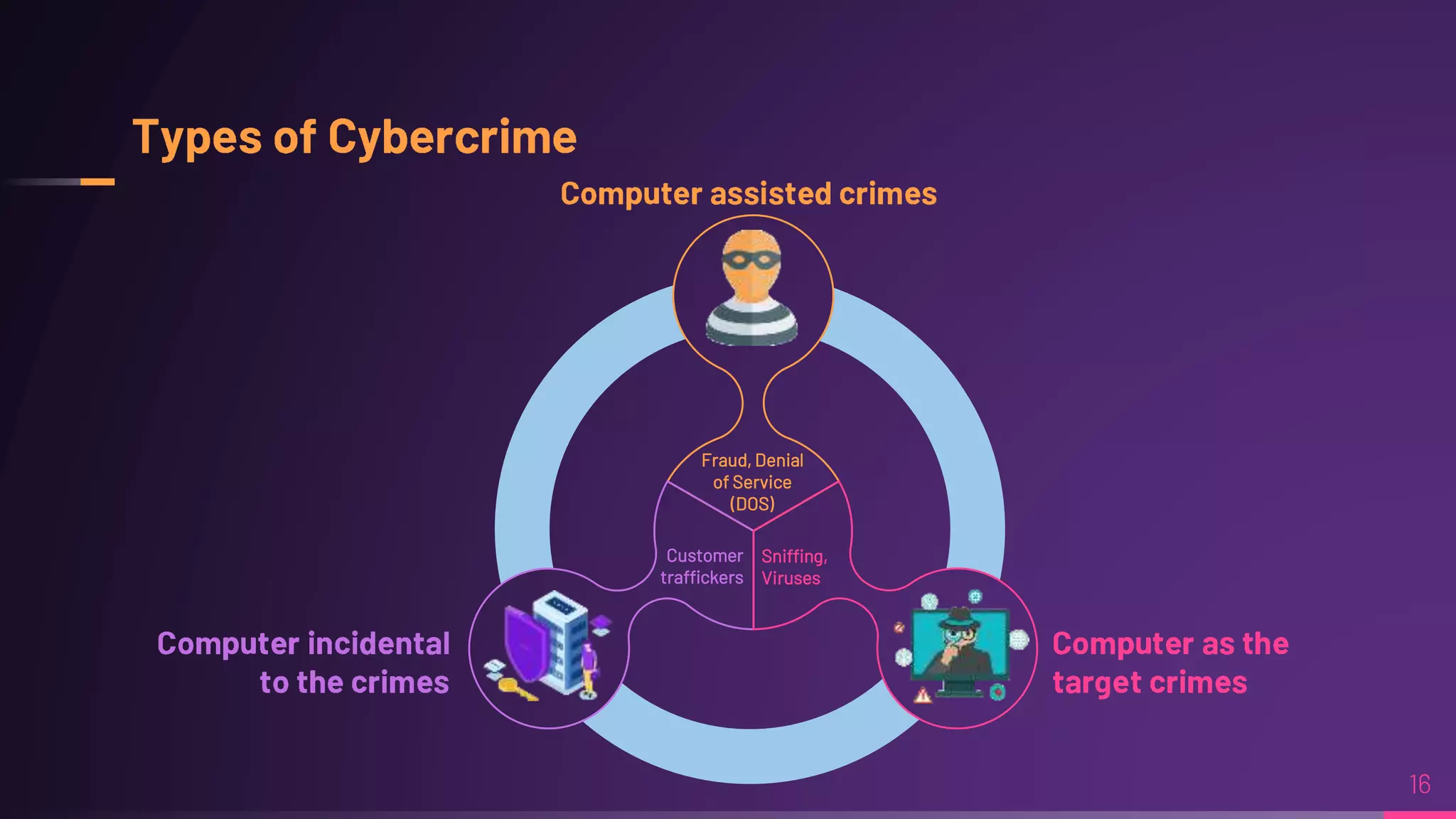
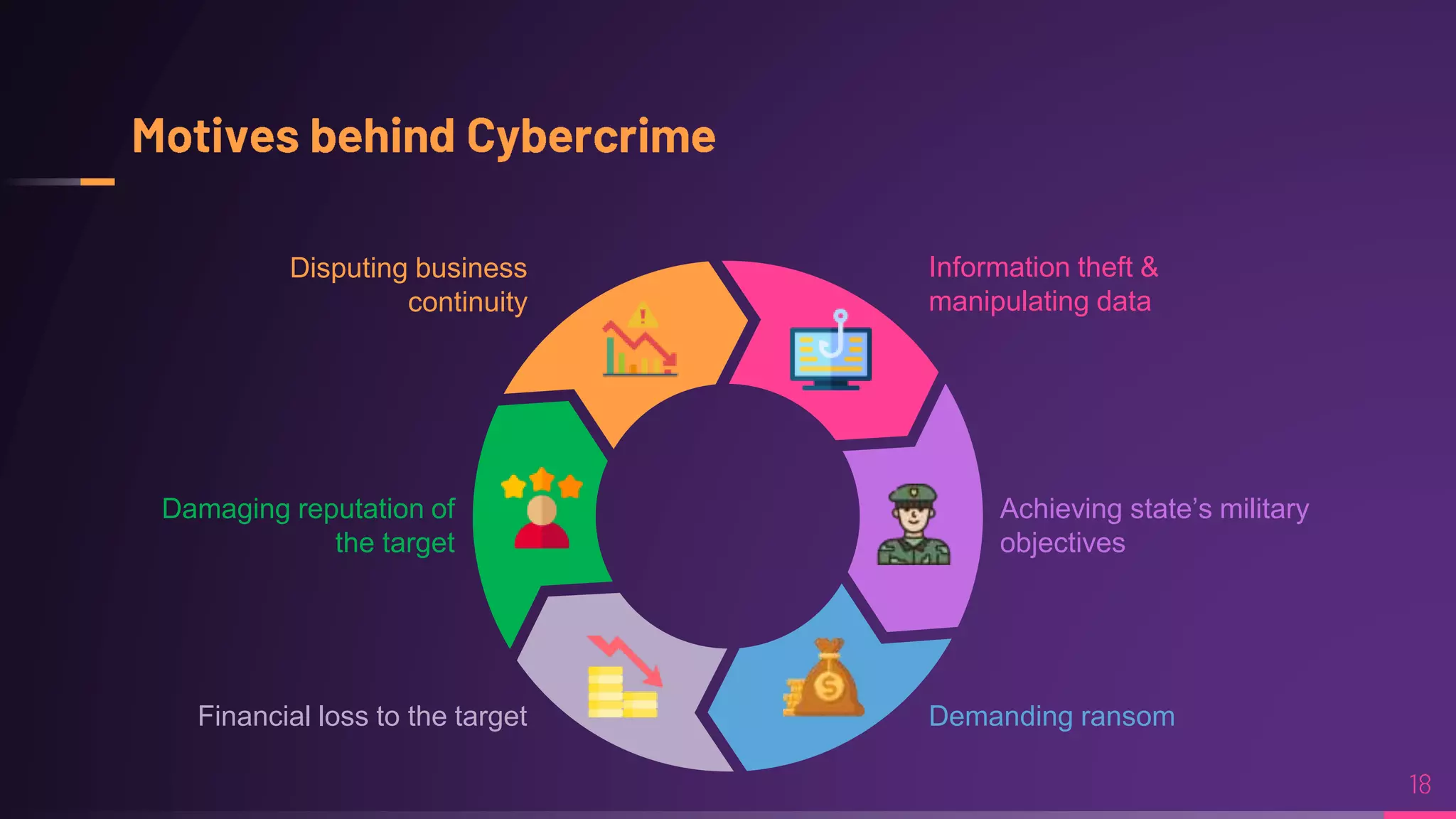
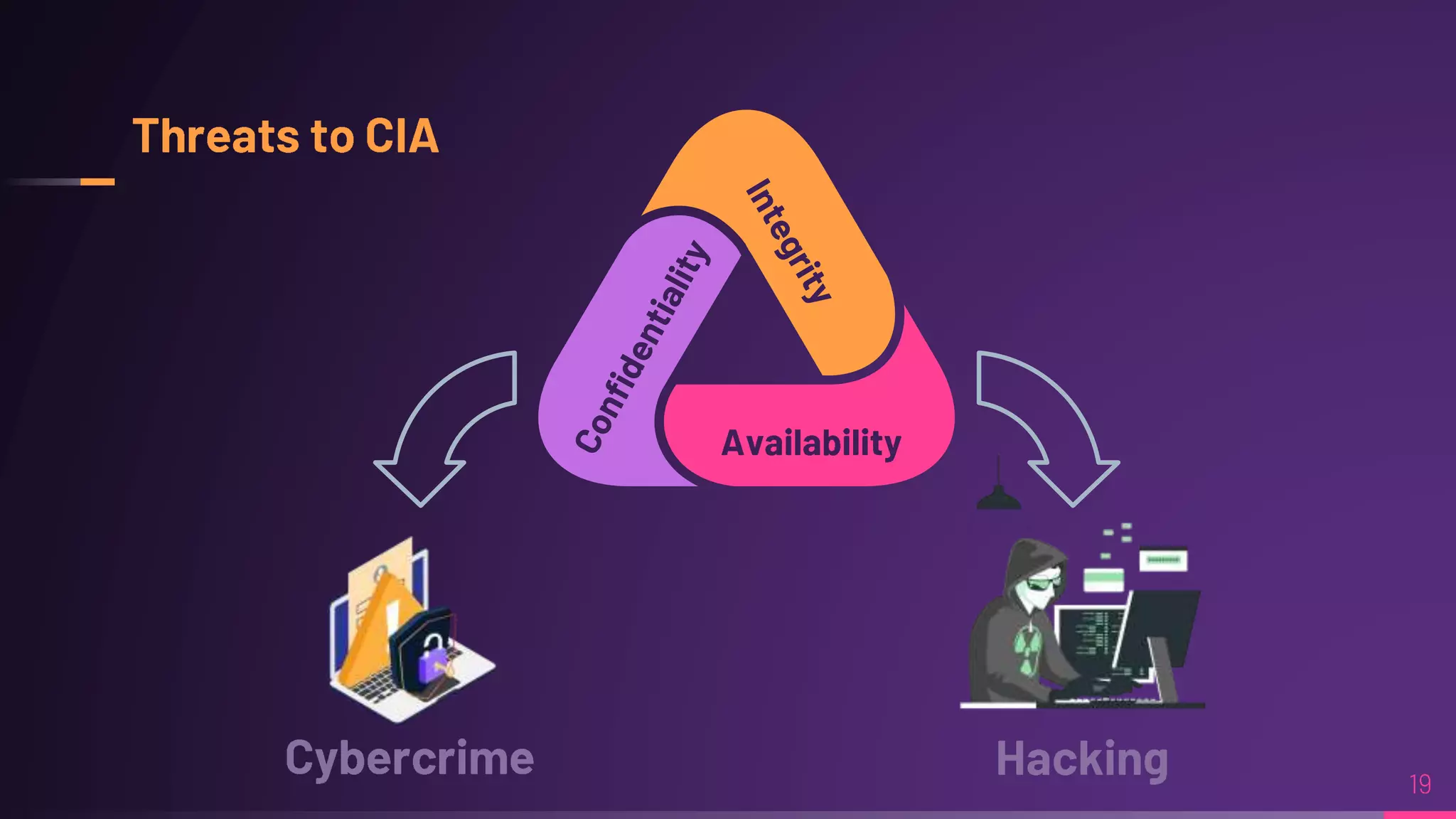
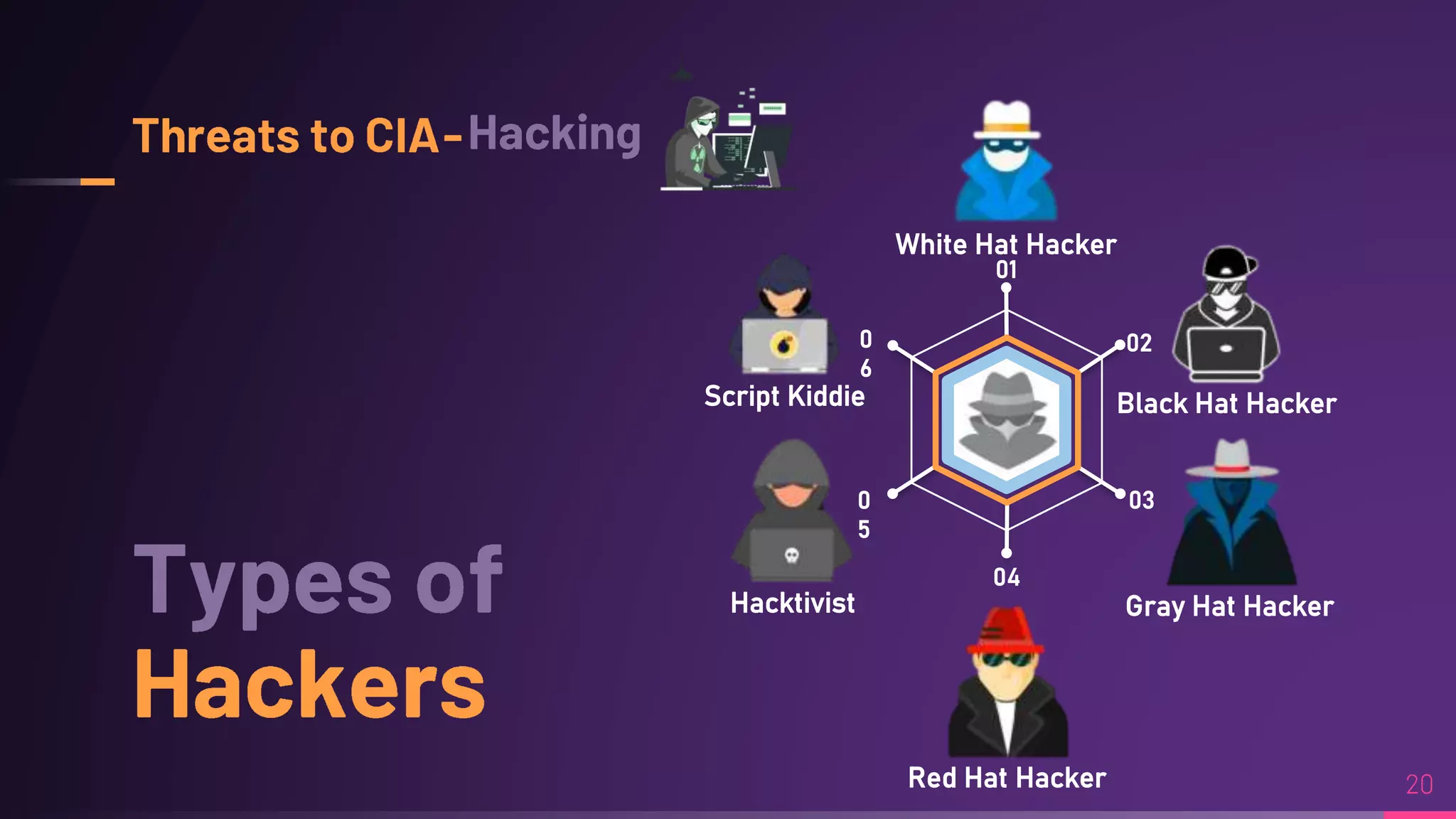
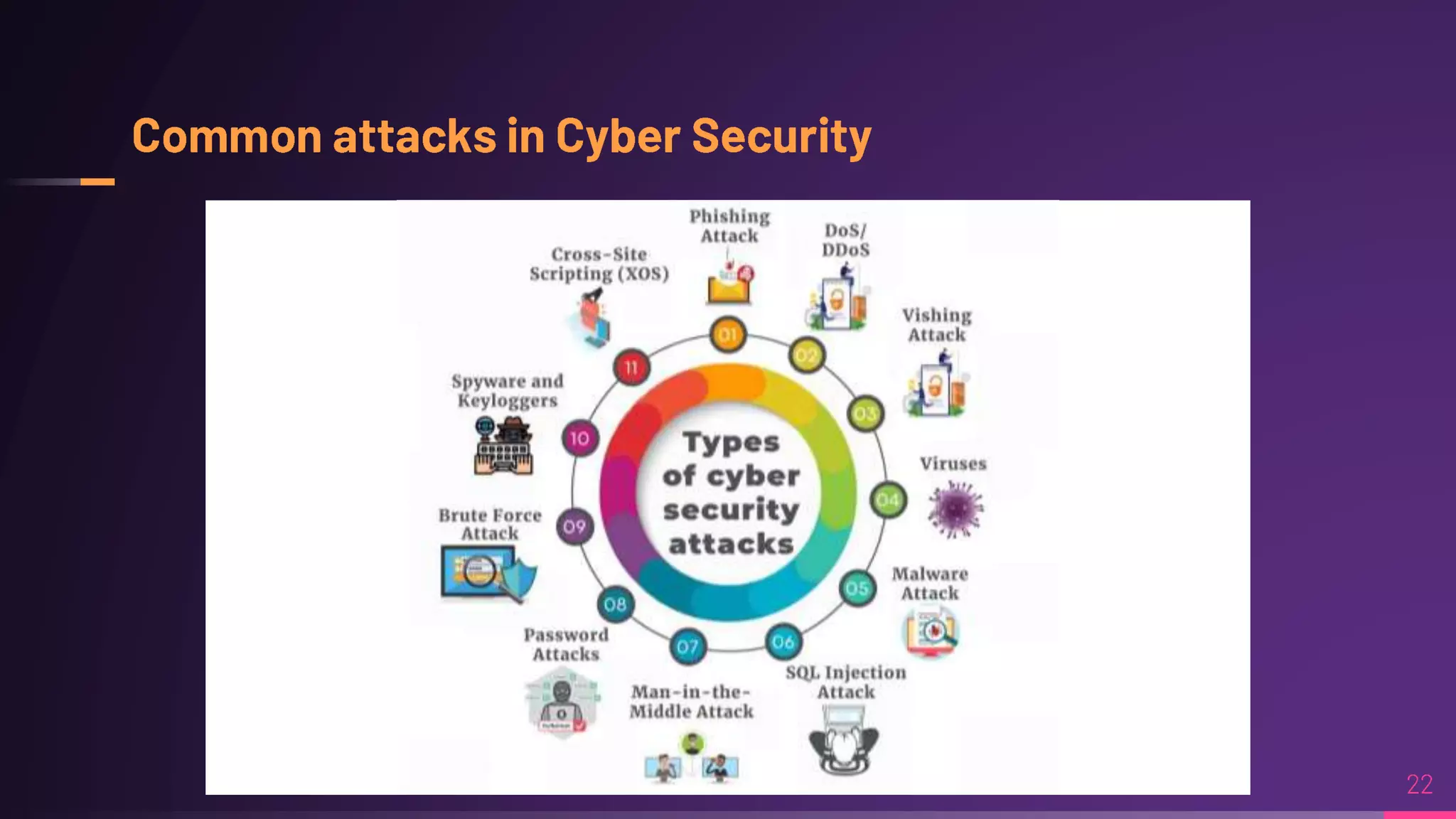
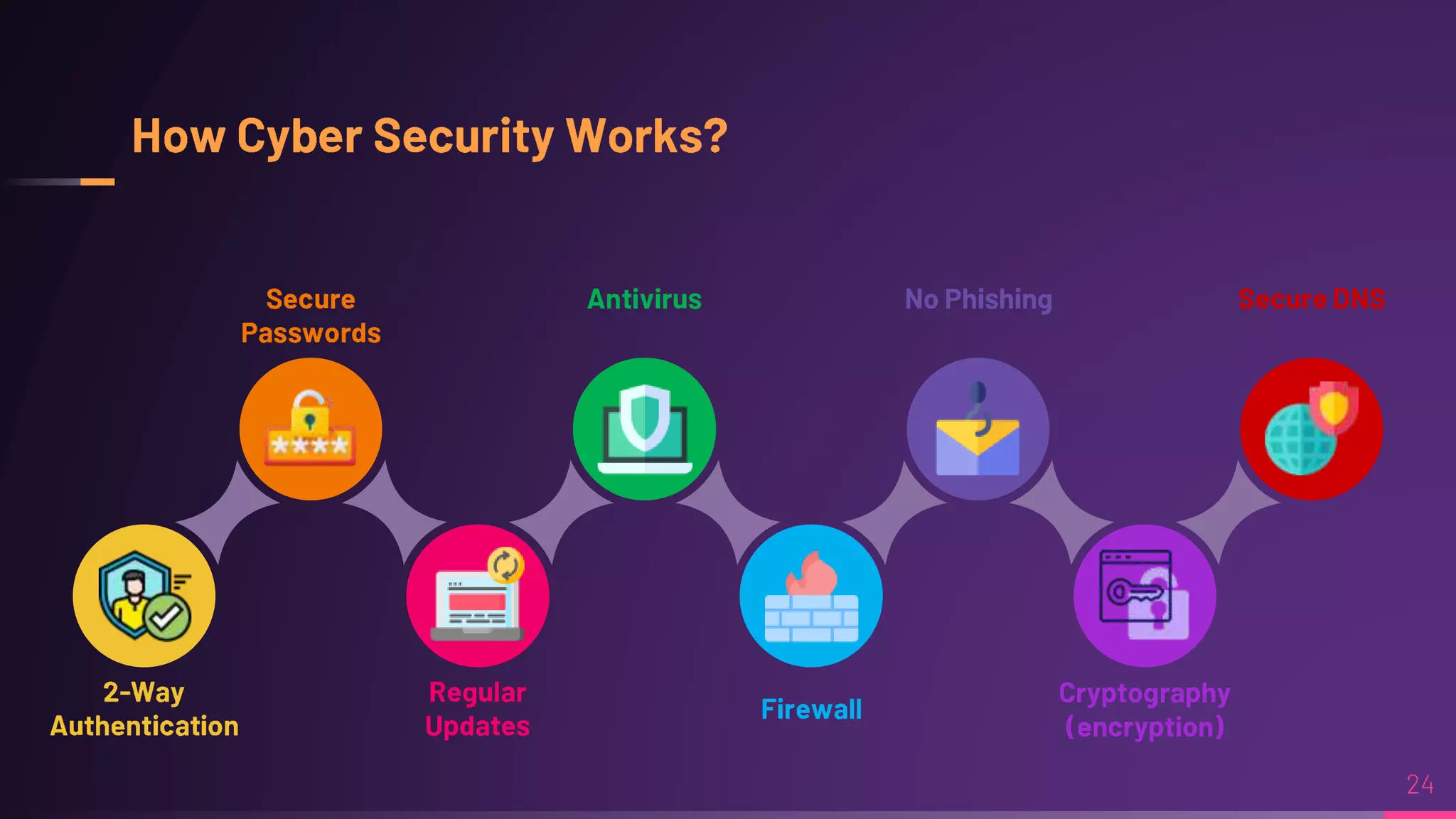
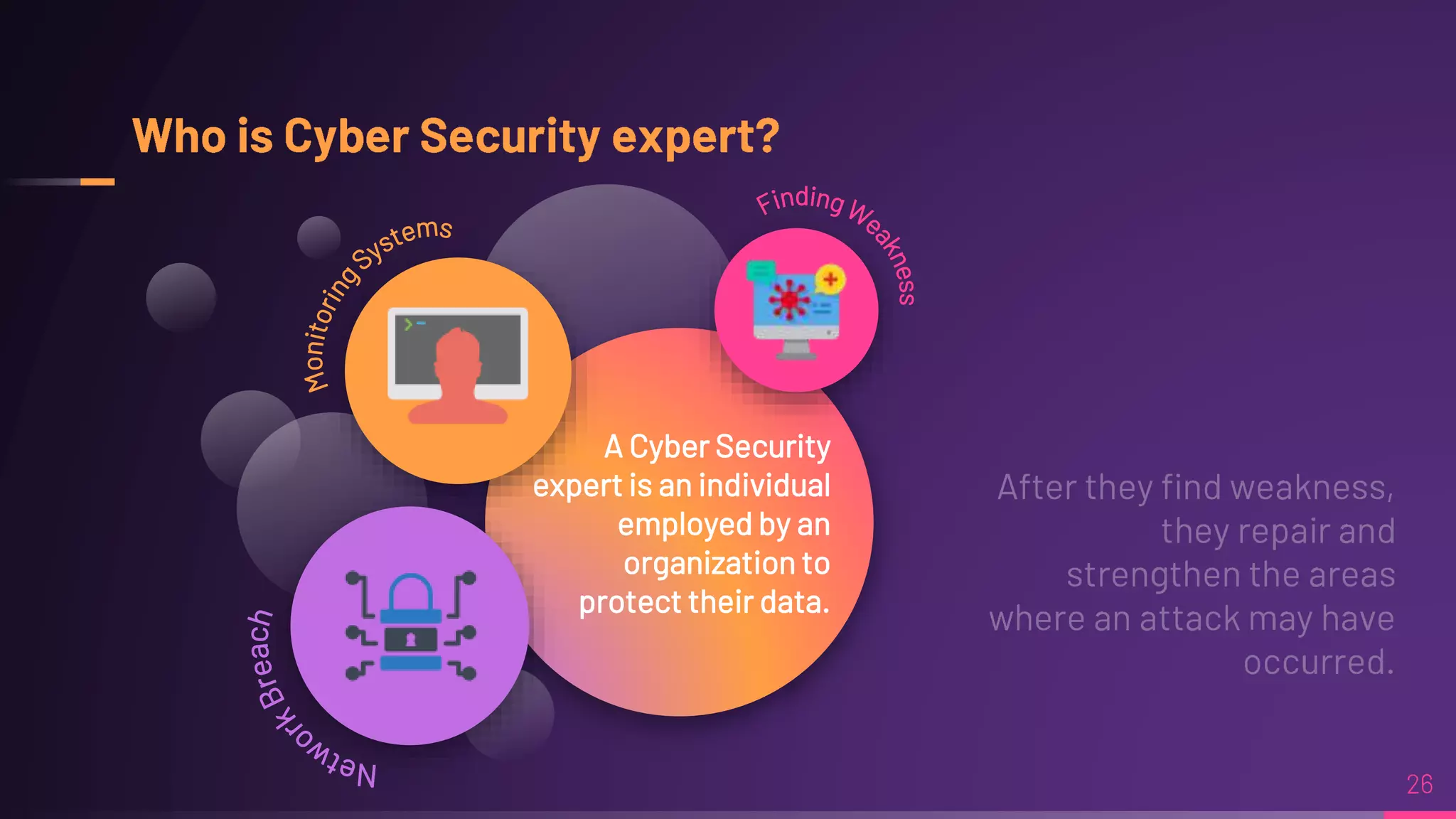
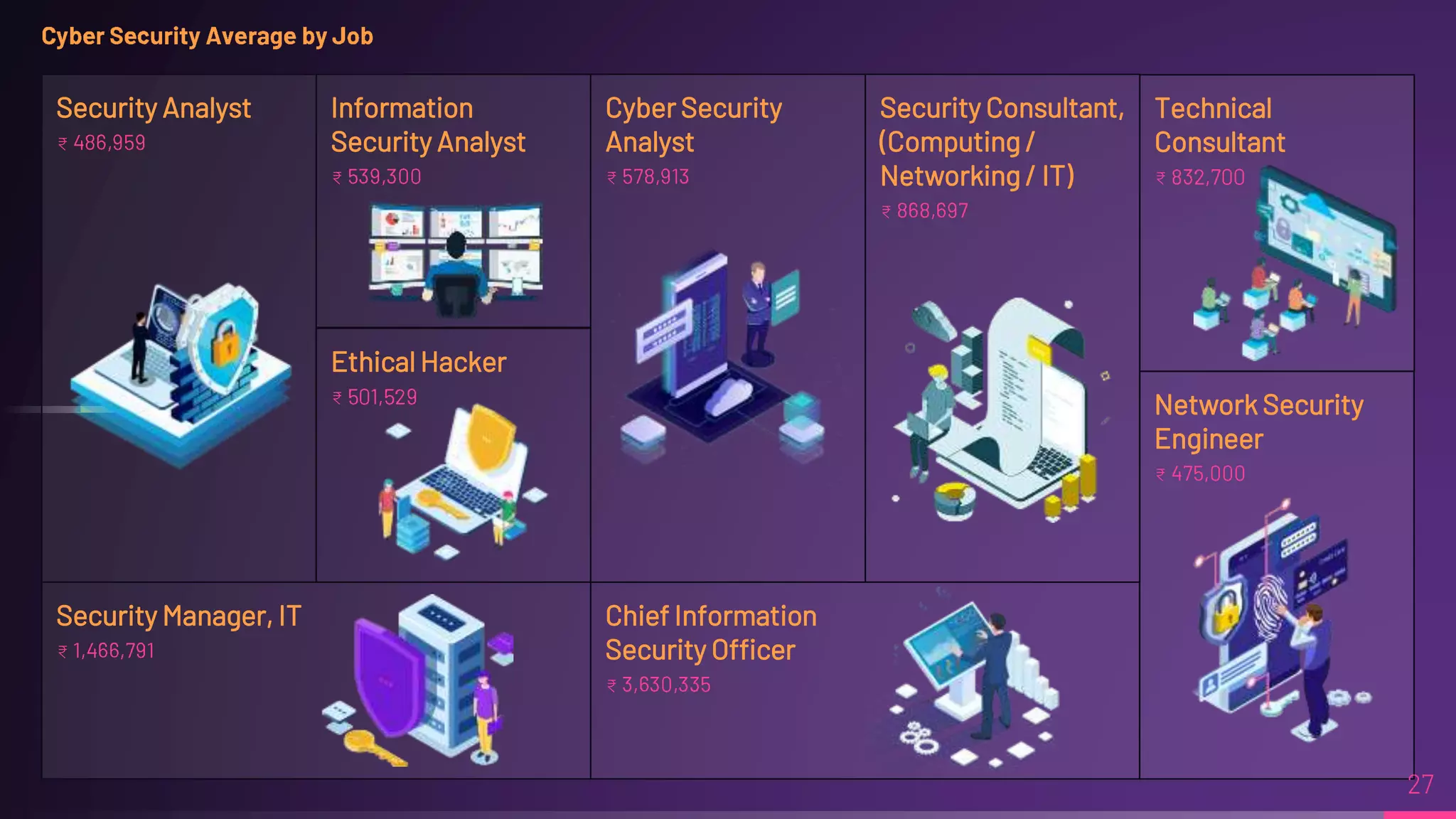
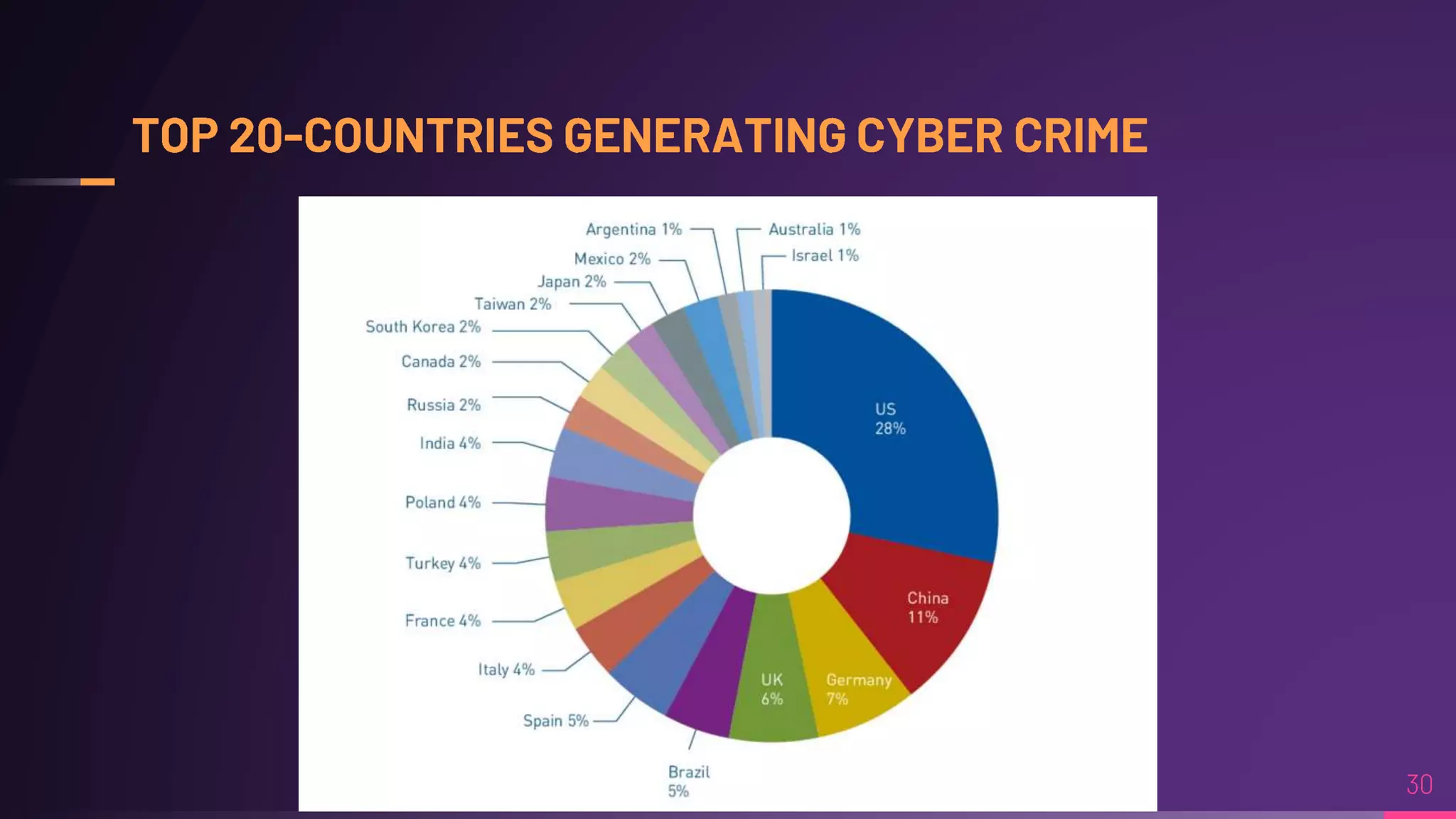
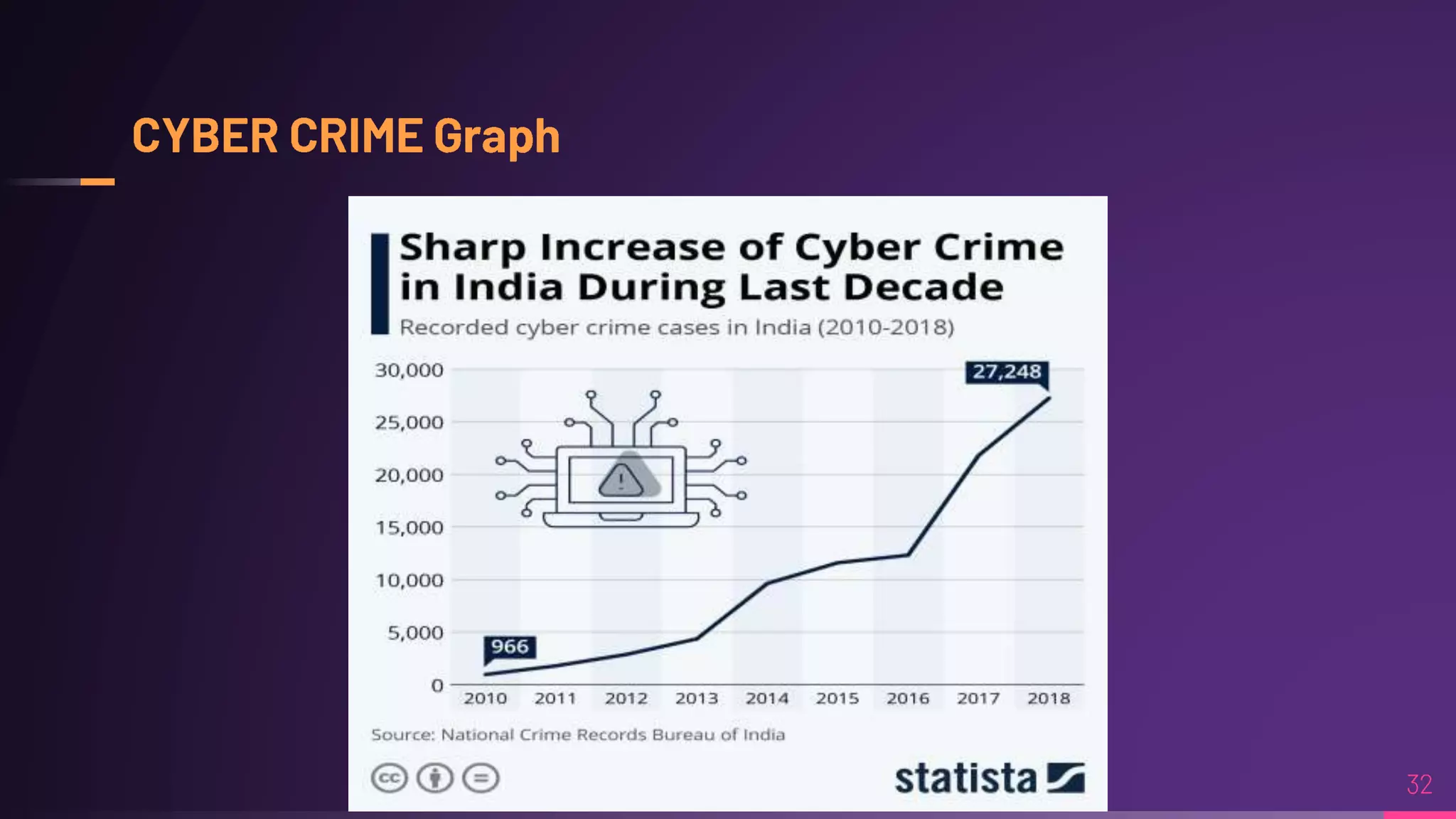
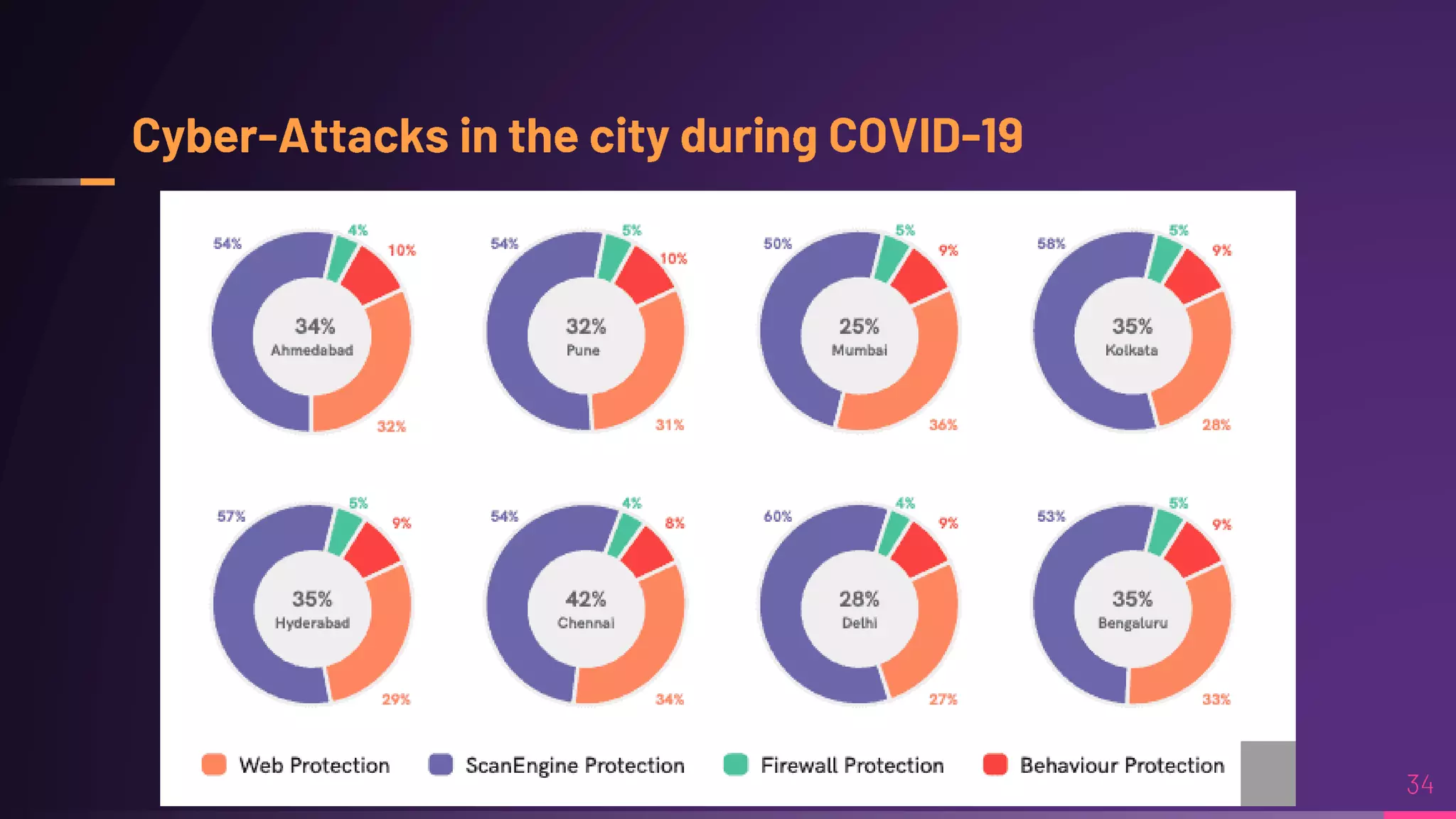
Debraj Karmakar is pursuing a B.Tech in Computer Science and Engineering and discusses the importance of cybersecurity in protecting networks and devices. Key principles include confidentiality, integrity, and availability, which safeguard against cybercrime and unauthorized access. The document also outlines various roles within cybersecurity, including ethical hackers and security analysts.