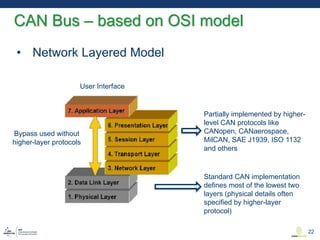
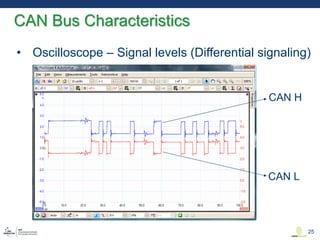
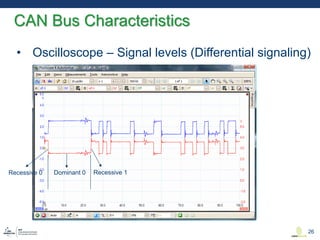
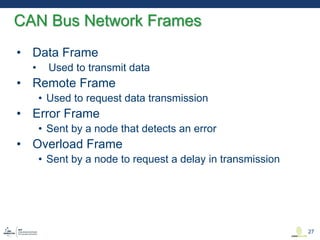
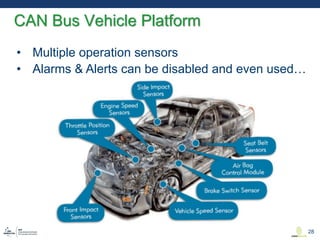
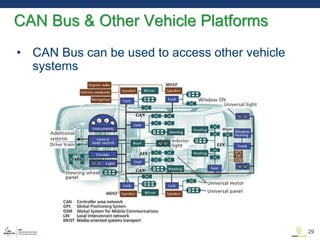
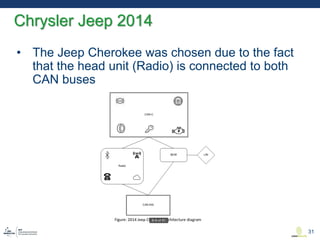
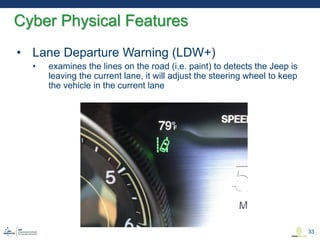
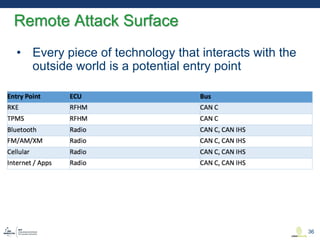
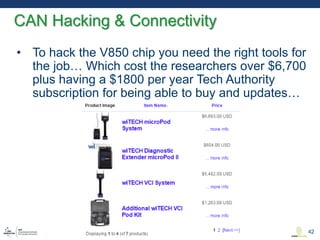
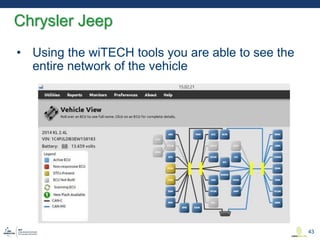
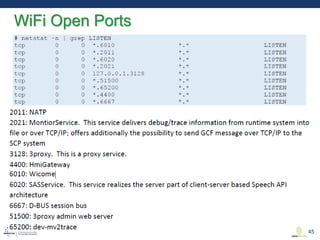
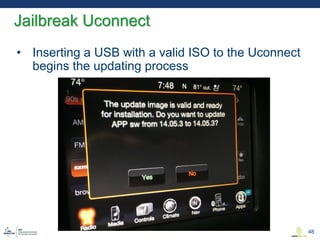
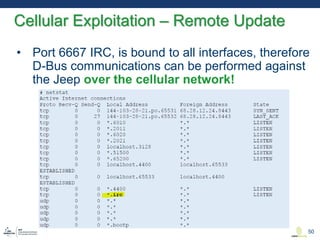
This document discusses various aspects of cyber security in transportation, focusing on vulnerabilities within aviation, public transport, and connected vehicles. Specific incidents of cyber attacks are highlighted, including the LOT Polish Airlines disruption and hacks affecting United Airlines and Chrysler Jeep systems. The overall emphasis is on the need for comprehensive protection and awareness of both internal and external threats in transportation systems.