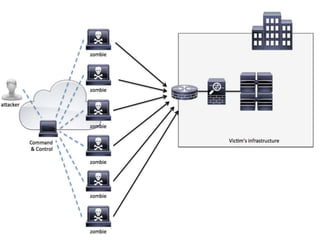
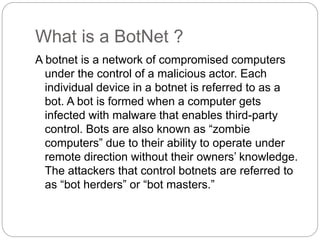
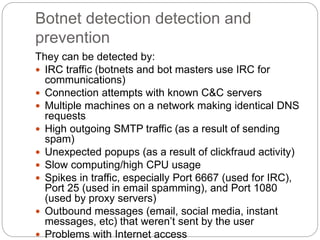
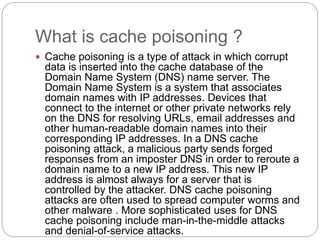
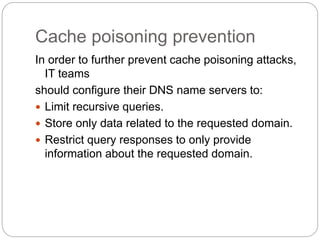
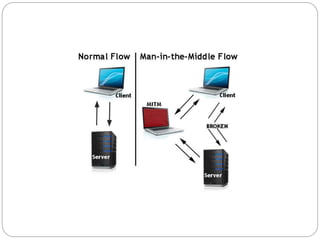
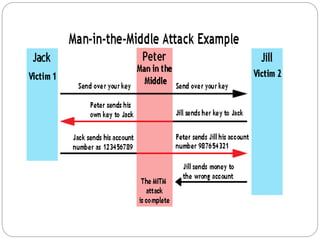
The document discusses several types of cyber attacks and threats including ARP spoofing, botnets, cache poisoning, computer worms, keyloggers, malware, man-in-the-middle attacks, rootkits, and spoofing attacks. It provides definitions and examples of each threat as well as methods of detection and prevention. ARP spoofing, botnets, and cache poisoning are network-based attacks while keyloggers and rootkits are installed locally. Man-in-the-middle attacks exploit real-time communications. Detection requires antivirus software, monitoring of running processes and startup programs, and analyzing file system logs and network traffic. Comprehensive prevention relies on encryption, firewalls, and avoiding insecure network configurations.