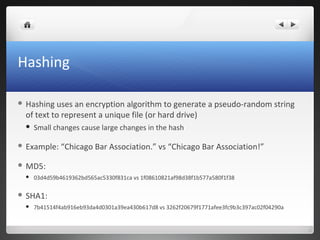
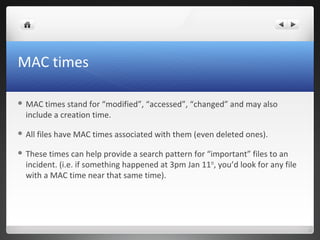
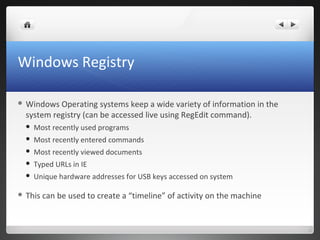
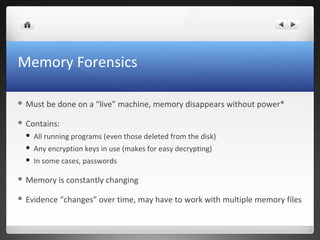
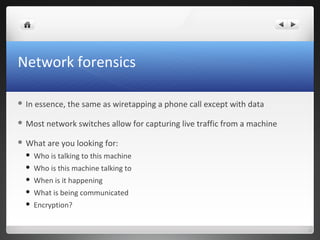
The seminar covers various aspects of cybercrime and computer forensics, including types of computer crime, legal issues, and the importance of chain of custody in evidence collection. Key topics include the differences between incident response and forensics, data acquisition methods, as well as tools like hashing for ensuring data integrity. Additionally, the seminar emphasizes the complexity of evidence collection from hard drives, memory, networks, and other digital sources.




![E-mail headers
Return-path: <kthompson@davismcgrath.com>
Envelope-to: jcb@bambenekconsulting.com
Delivery-date: Tue, 15 Mar 2011 12:13:56 -0500
Received: from mailhost.davismcgrath.com ([12.233.219.123])
by thebox.pentex-net.com with esmtp (Exim 4.69)
(envelope-from <kthompson@davismcgrath.com>)
id 1PzXoi-0000mf-Fw
for jcb@bambenekconsulting.com; Tue, 15 Mar 2011 12:13:56 -0500
Received: from DM48WXP (unverified [192.168.3.69]) by mailhost.davismcgrath.com
(Rockliffe SMTPRA 9.3.1) with ESMTP id <B0002606529@mailhost.davismcgrath.com> for <jcb@bambenekconsulting.com>;
Tue, 15 Mar 2011 12:16:42 -0500
From: "Kevin A. Thompson" <kthompson@davismcgrath.com>
To: <jcb@bambenekconsulting.com>
References: <201033962-1299187478-cardhu_decombobulator_blackberry.rim.net-1091018849-@bda678.bisx.prod.on.blackberry> <051601cbd9e9$bd0fae80$372f0b80$@com>
<e71cae025b2bd4be5a4422d9f71c3322.squirrel@bambenekconsulting.com>
In-Reply-To: <e71cae025b2bd4be5a4422d9f71c3322.squirrel@bambenekconsulting.com>
Subject: RE: CBA - CLE/Seminar?
Date: Tue, 15 Mar 2011 12:16:39 -0500
Message-ID: <020b01cbe334$bf146320$3d3d2960$@com>
MIME-Version: 1.0
Content-Type: text/plain;
charset="US-ASCII"
Content-Transfer-Encoding: 7bit
X-Mailer: Microsoft Office Outlook 12.0
Thread-Index: AcvhtQ/DNjyl3vl3Rr+AKt9z5zMFkwBf6MAA
Content-Language: en-us](https://image.slidesharecdn.com/cba-forensics-130816144213-phpapp01/85/Cybercrime-and-Computer-Forensics-Seminar-Chicago-Bar-Association-CLE-May-25-2011-20-320.jpg)