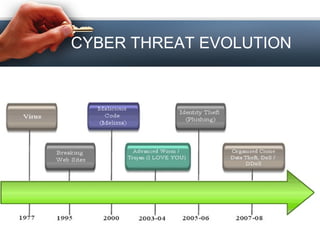
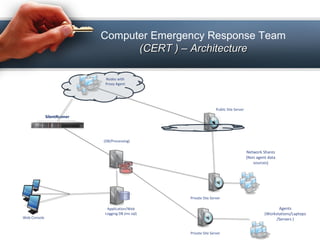
This document discusses cyber crime and security. It defines cyber crime as illegal activity committed on the internet. It then covers various topics related to cyber crime such as definitions, history, categories and types of cyber crimes including hacking, denial of service attacks and computer vandalism. The document also discusses cyber security and provides safety tips to prevent cyber crime such as using antivirus software and firewalls. It notes that technology alone is not destructive and depends on how people use it.