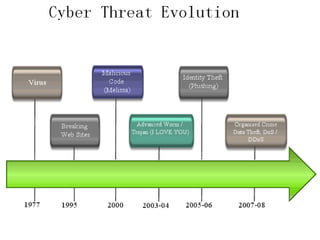
Cyber crime involves using computers and the internet to steal identities or data. The document discusses the history and types of cyber crimes such as hacking, denial of service attacks, and software piracy. It provides statistics on common cyber attacks and safety tips for preventing cyber crimes like using antivirus software and firewalls. The conclusion reflects on how technology can be destructive if not used responsibly.