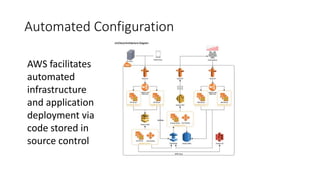
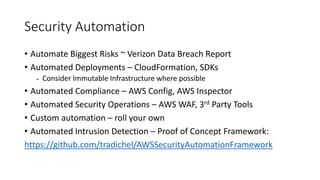
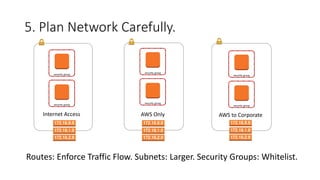
This document discusses AWS security best practices for enterprises. It recommends following AWS security policies and IAM best practices, automating security configurations through tools like CloudFormation, and architecting networks carefully with security groups and subnets. Automating security operations, compliance checks, and incident response is emphasized to manage risks and unknown threats. The document also warns against simply migrating on-premises systems to AWS without redesigning for the cloud.