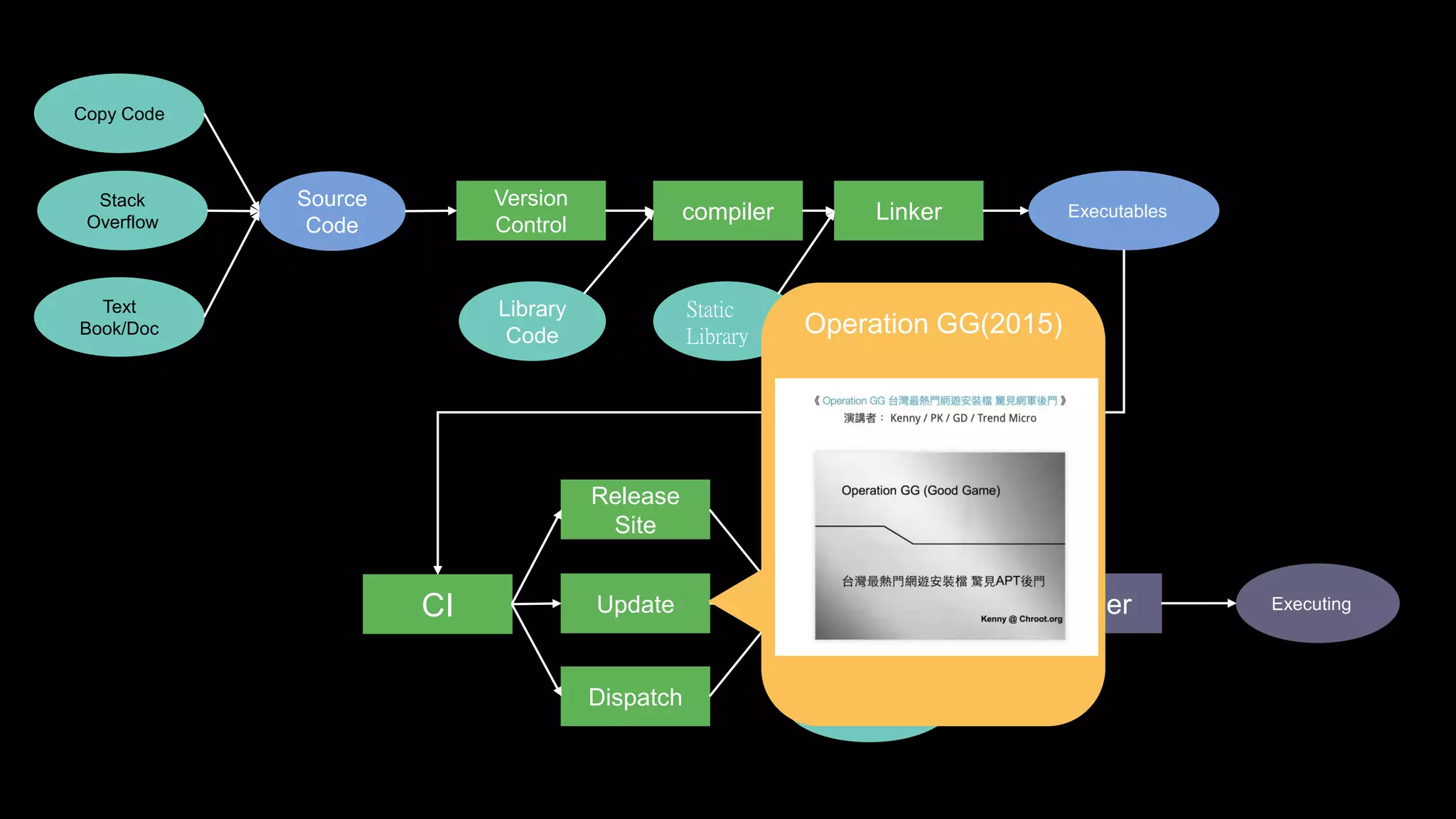
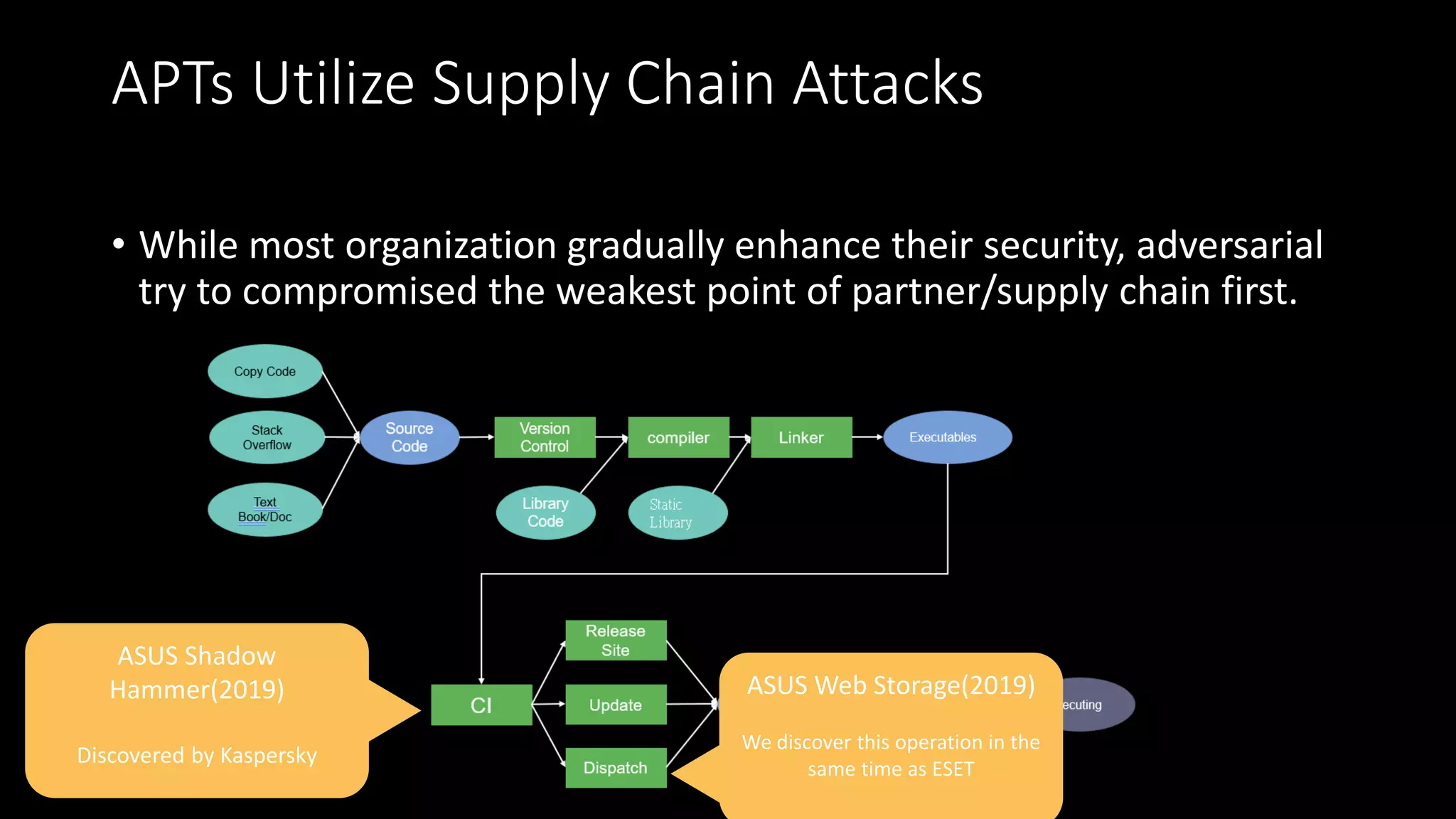
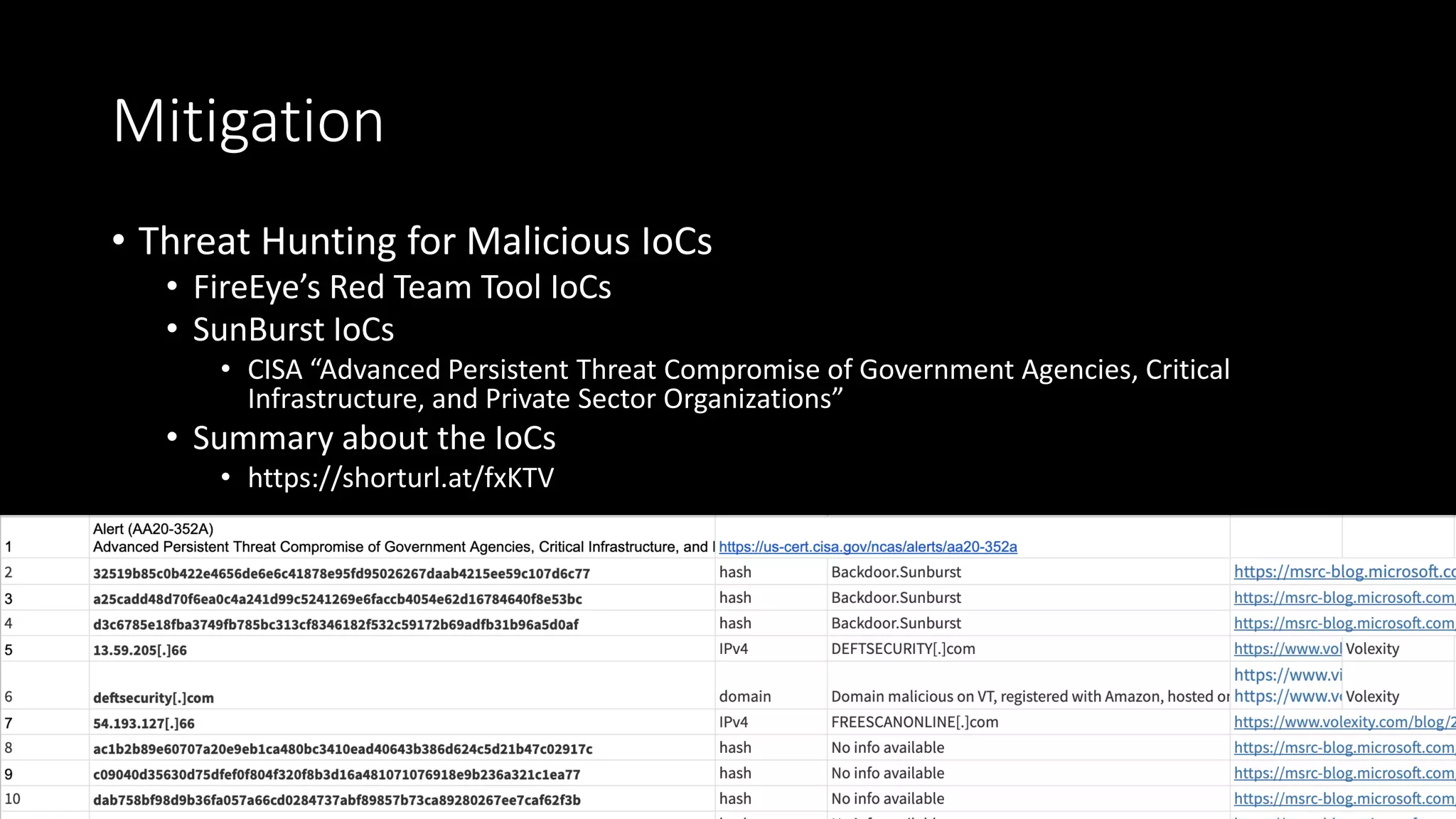
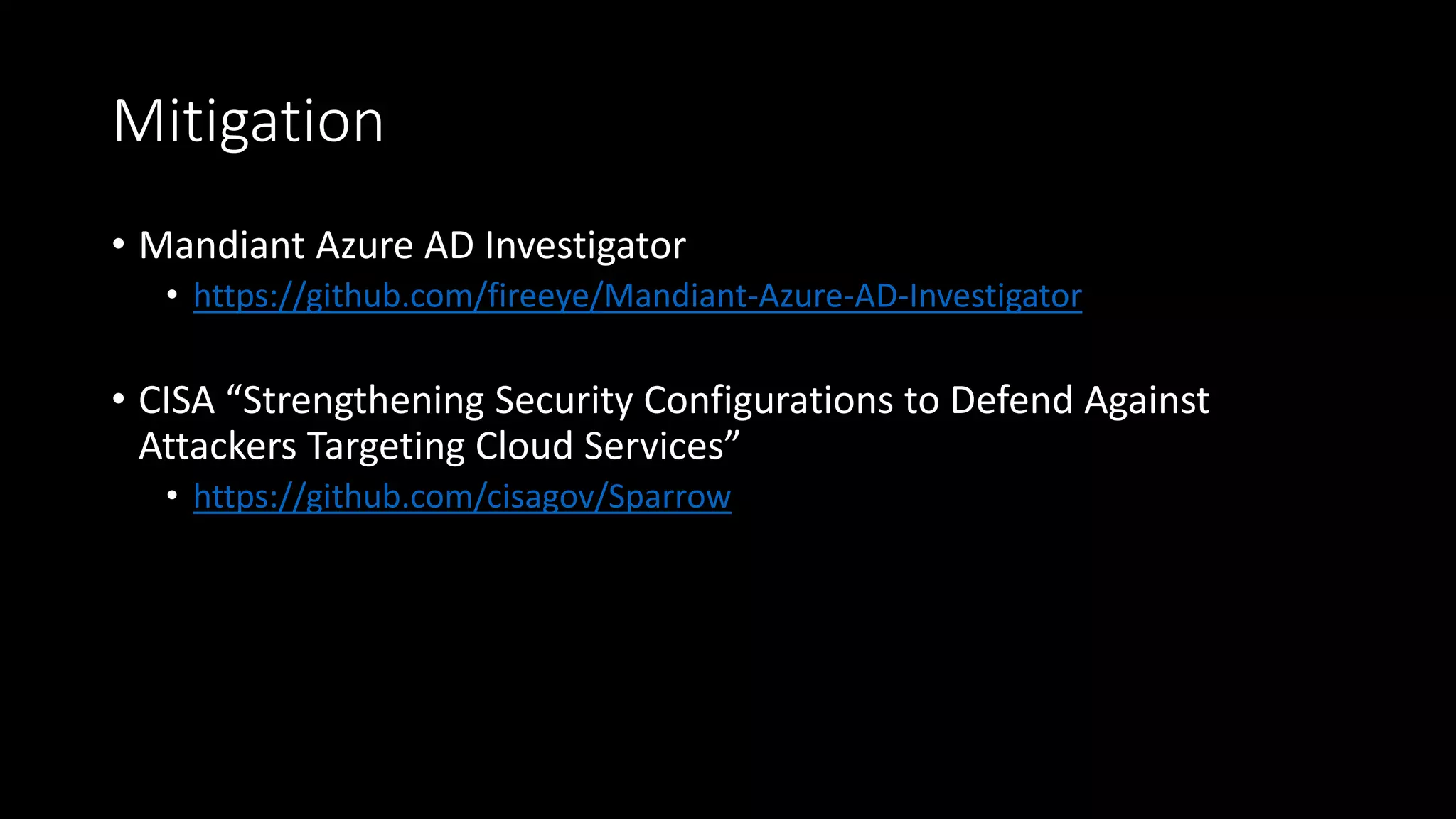
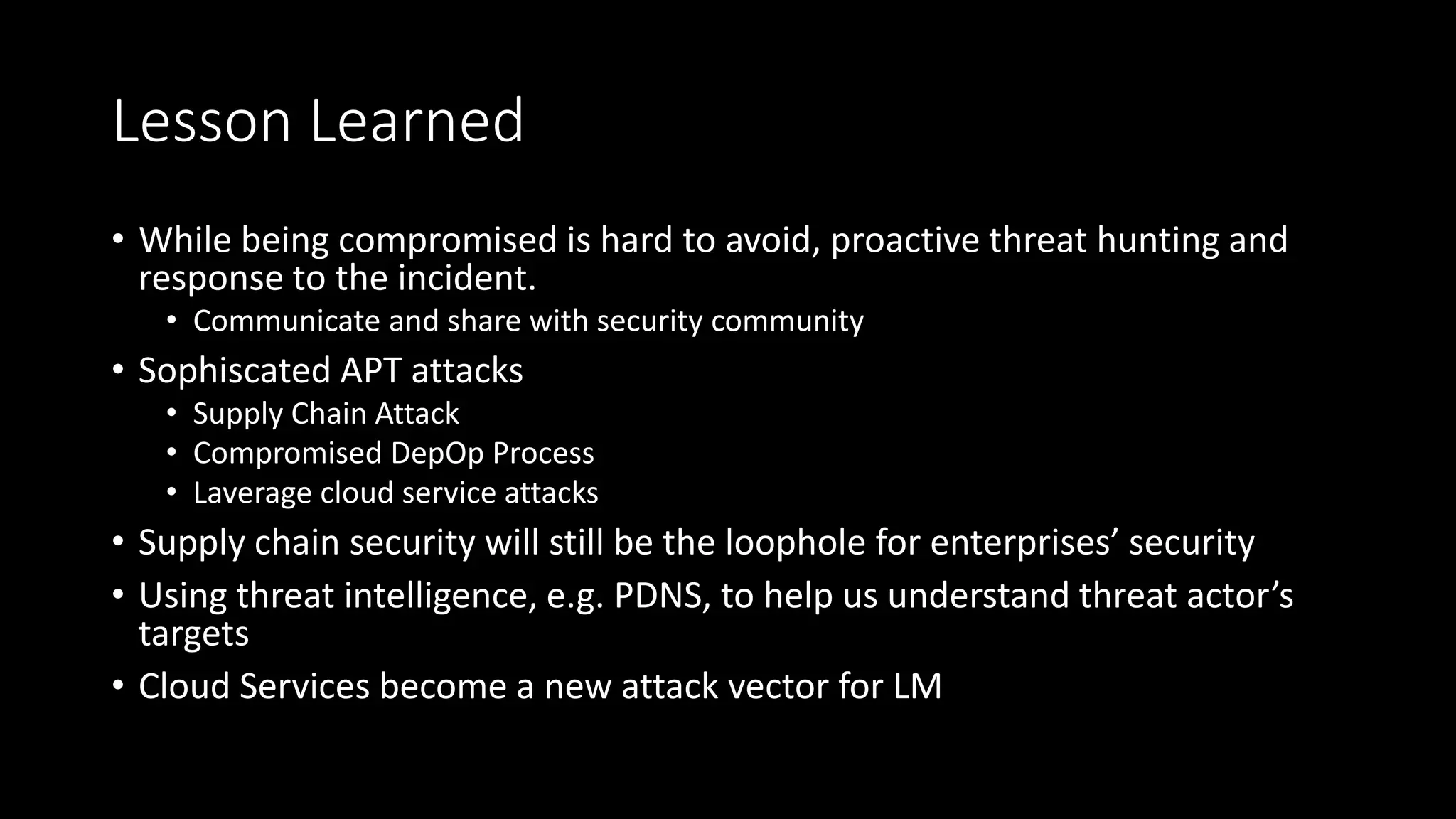
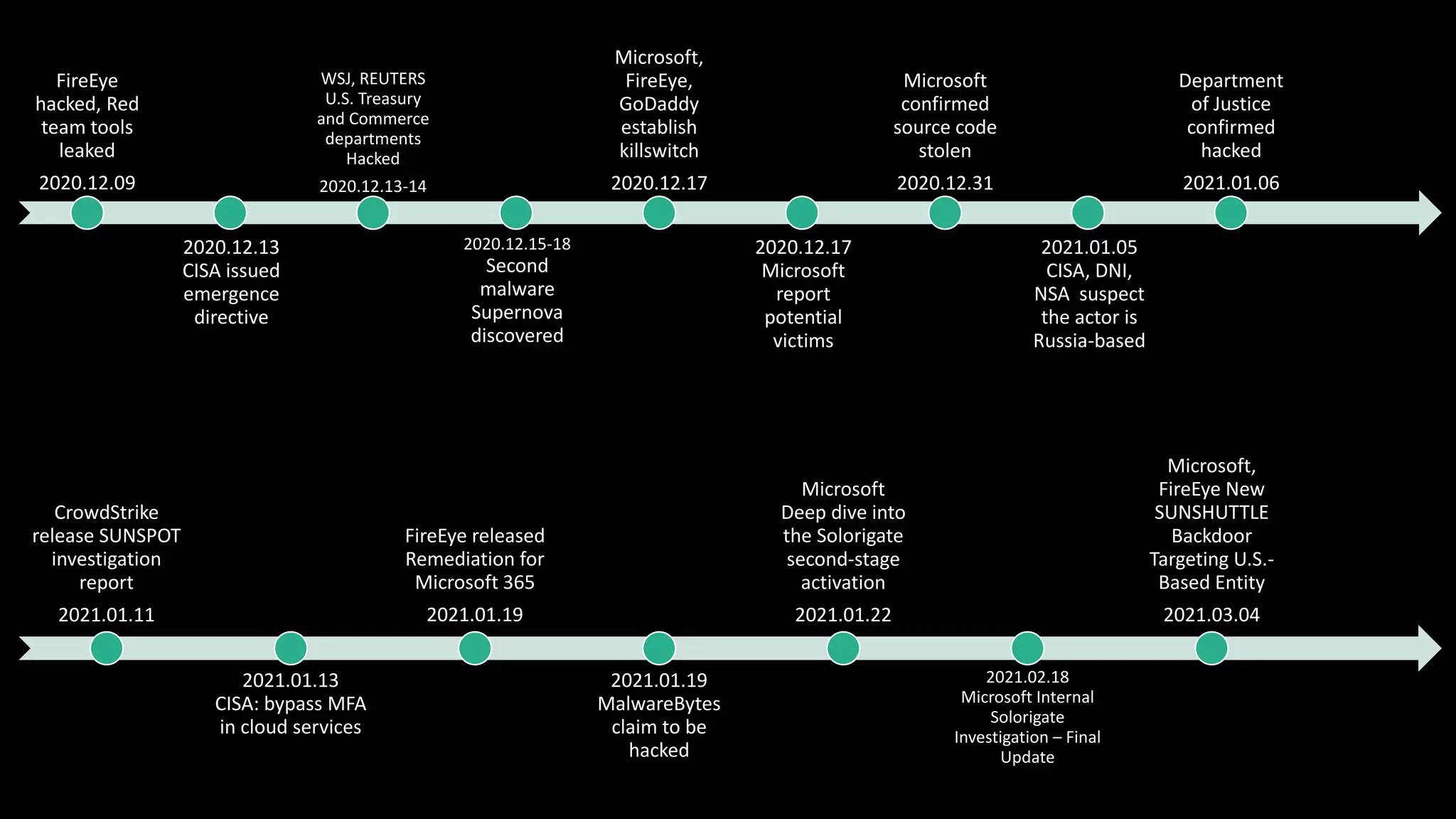
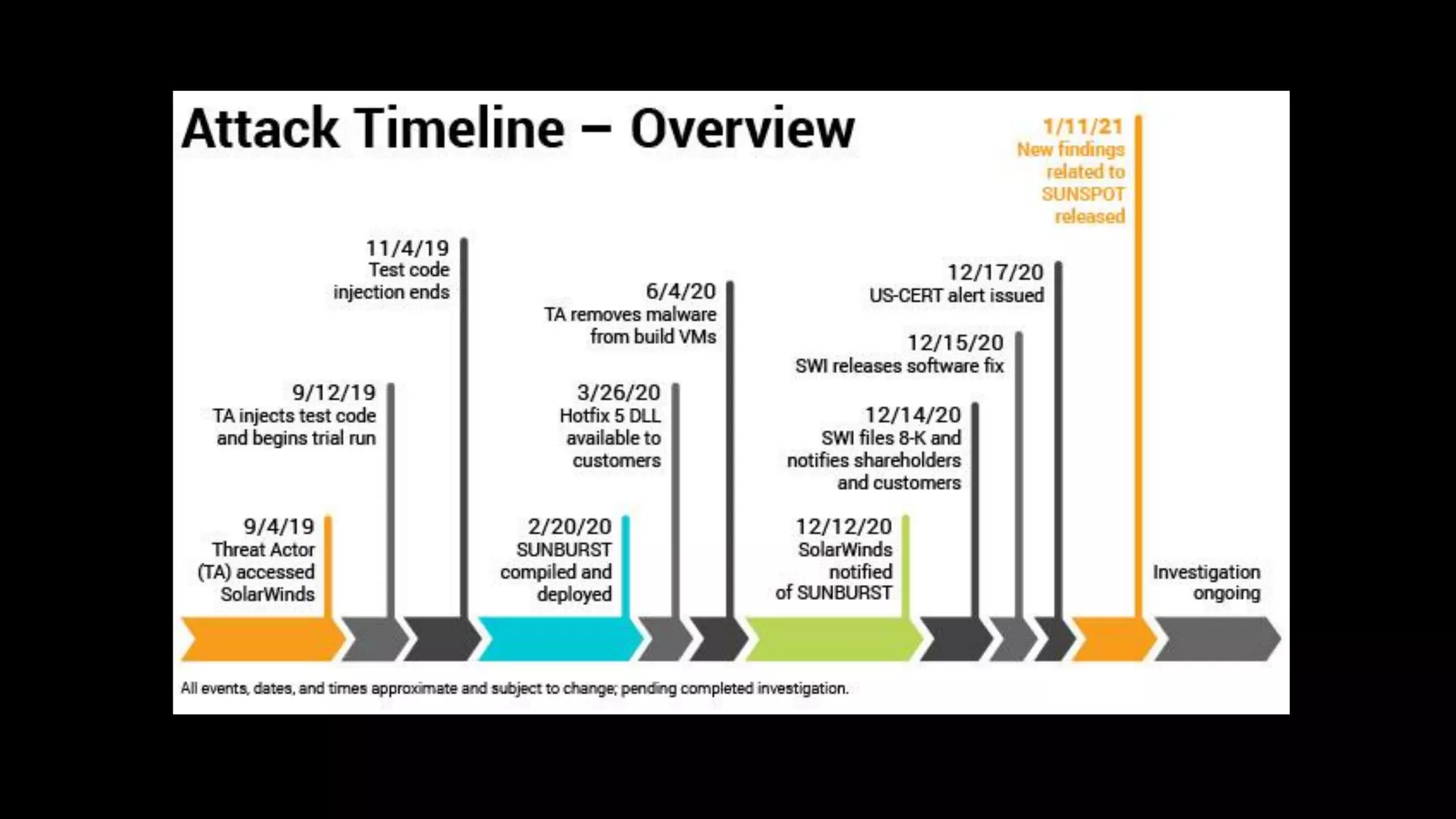
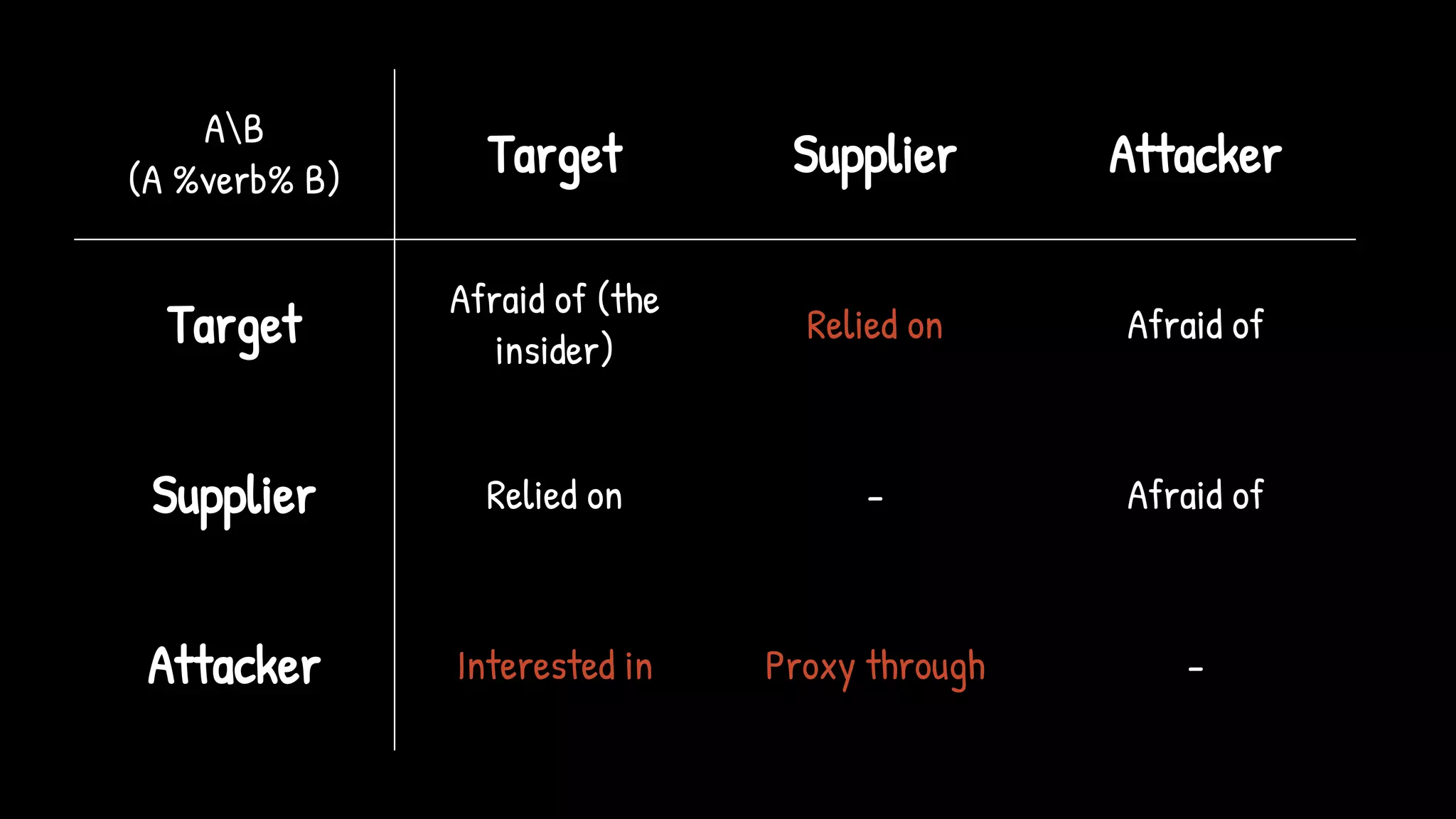
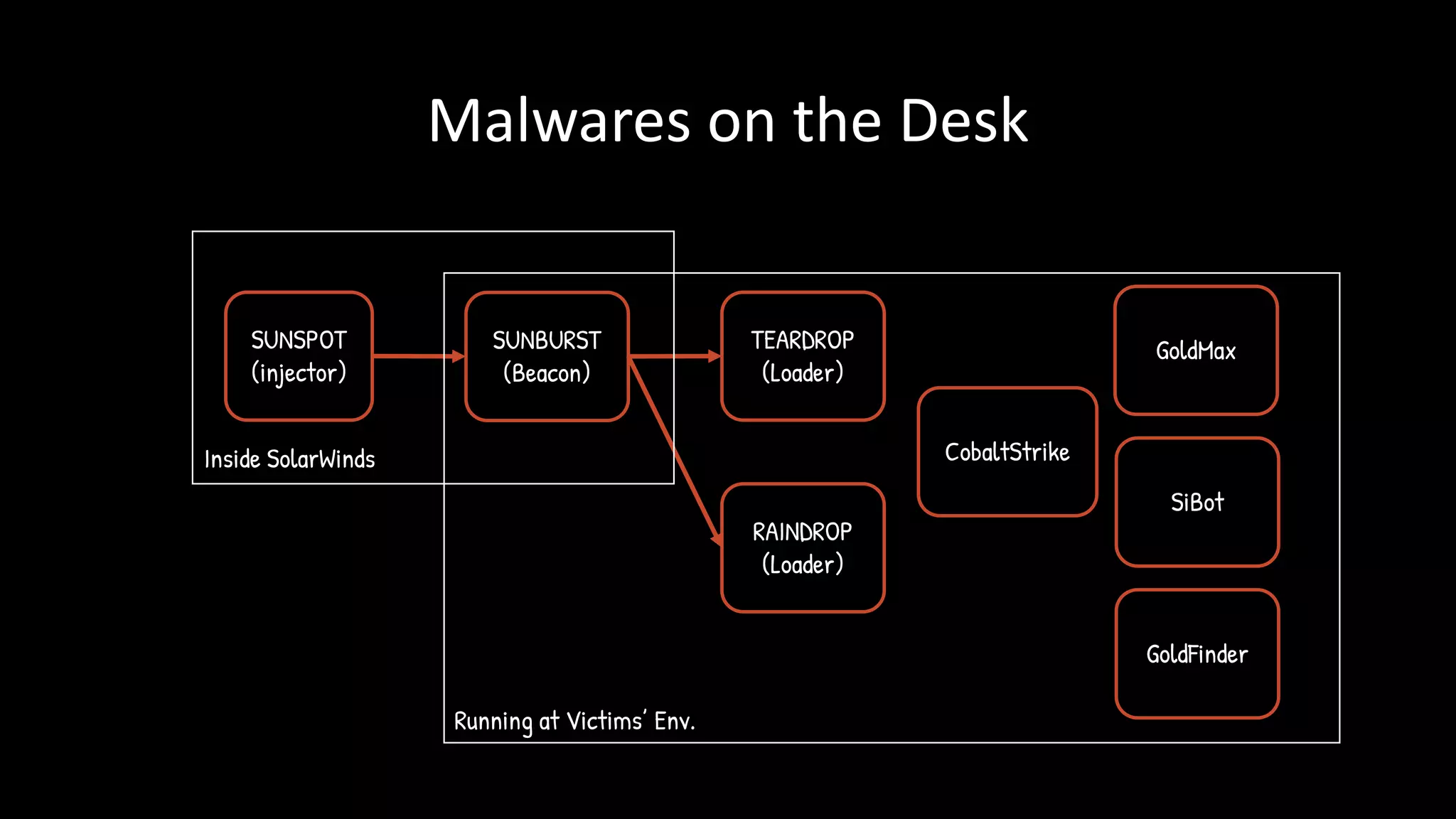
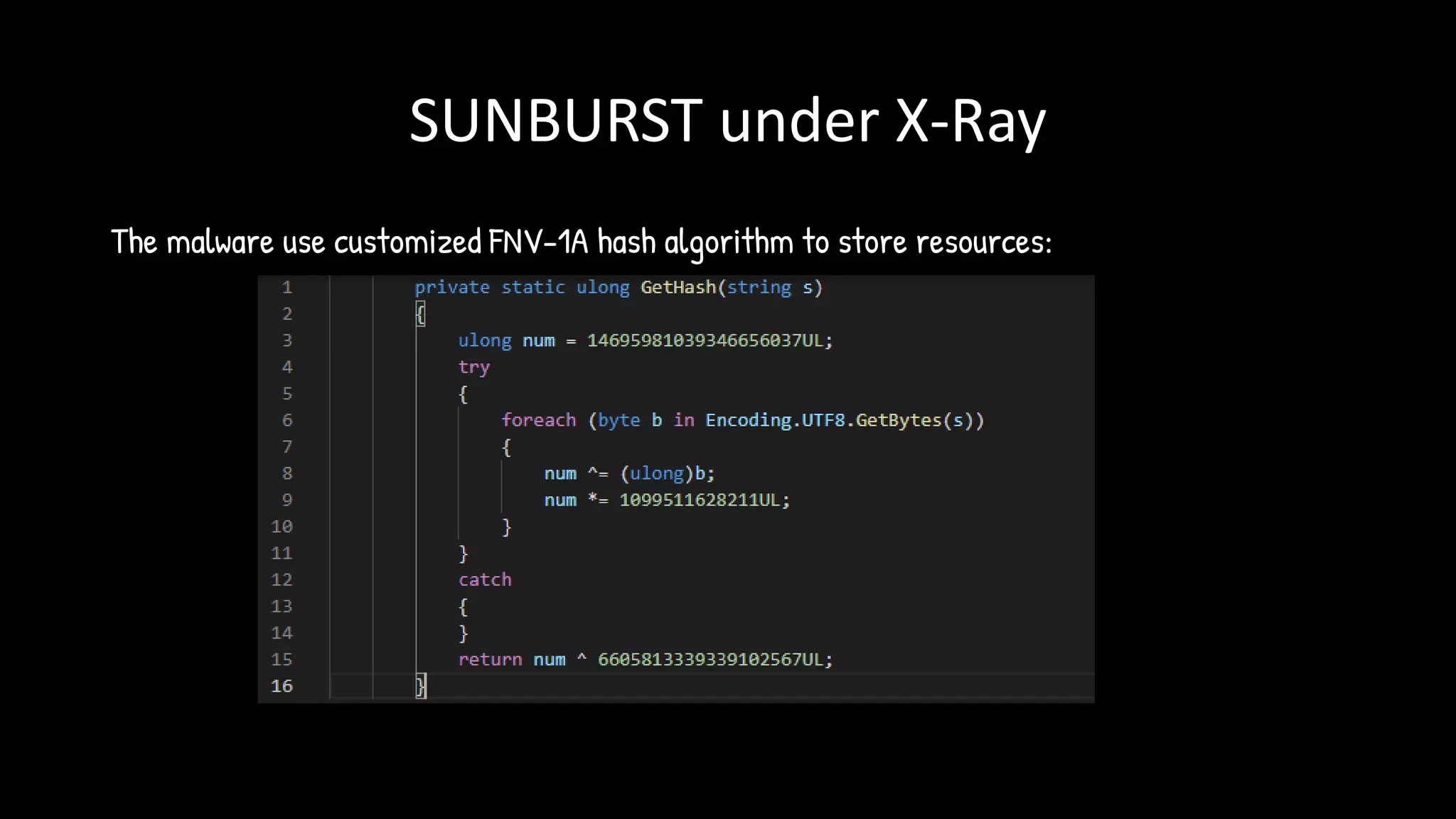
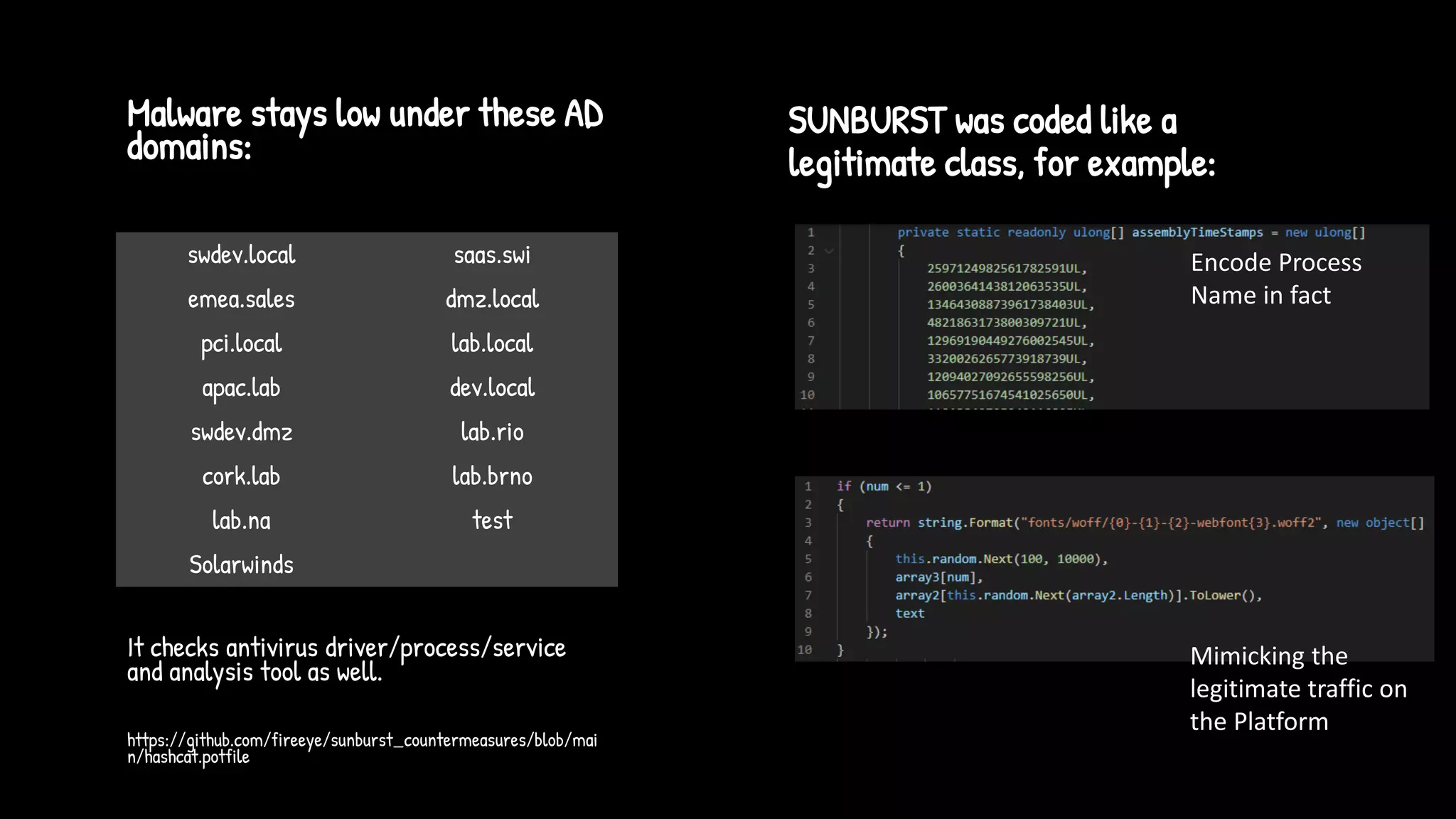
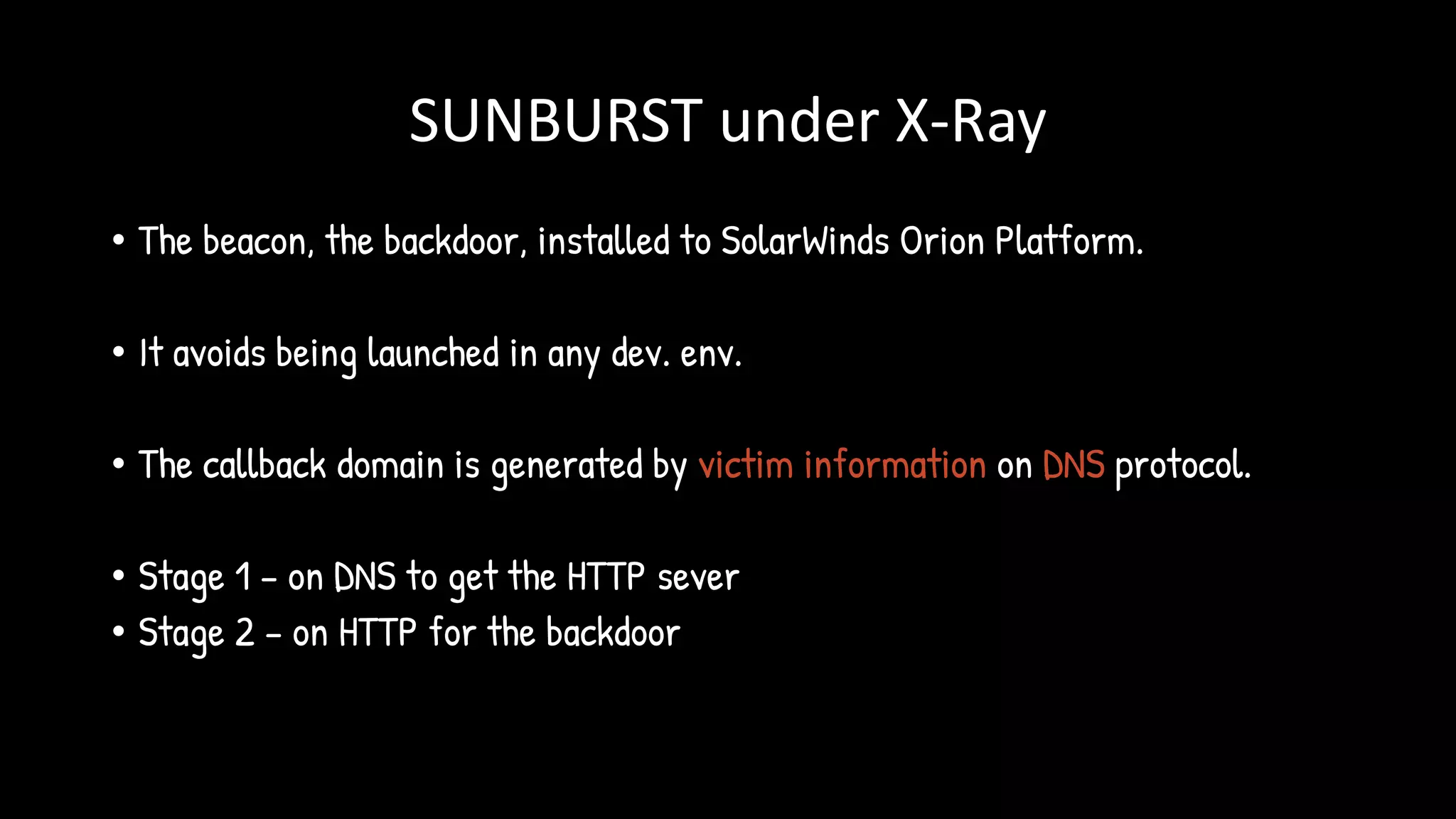
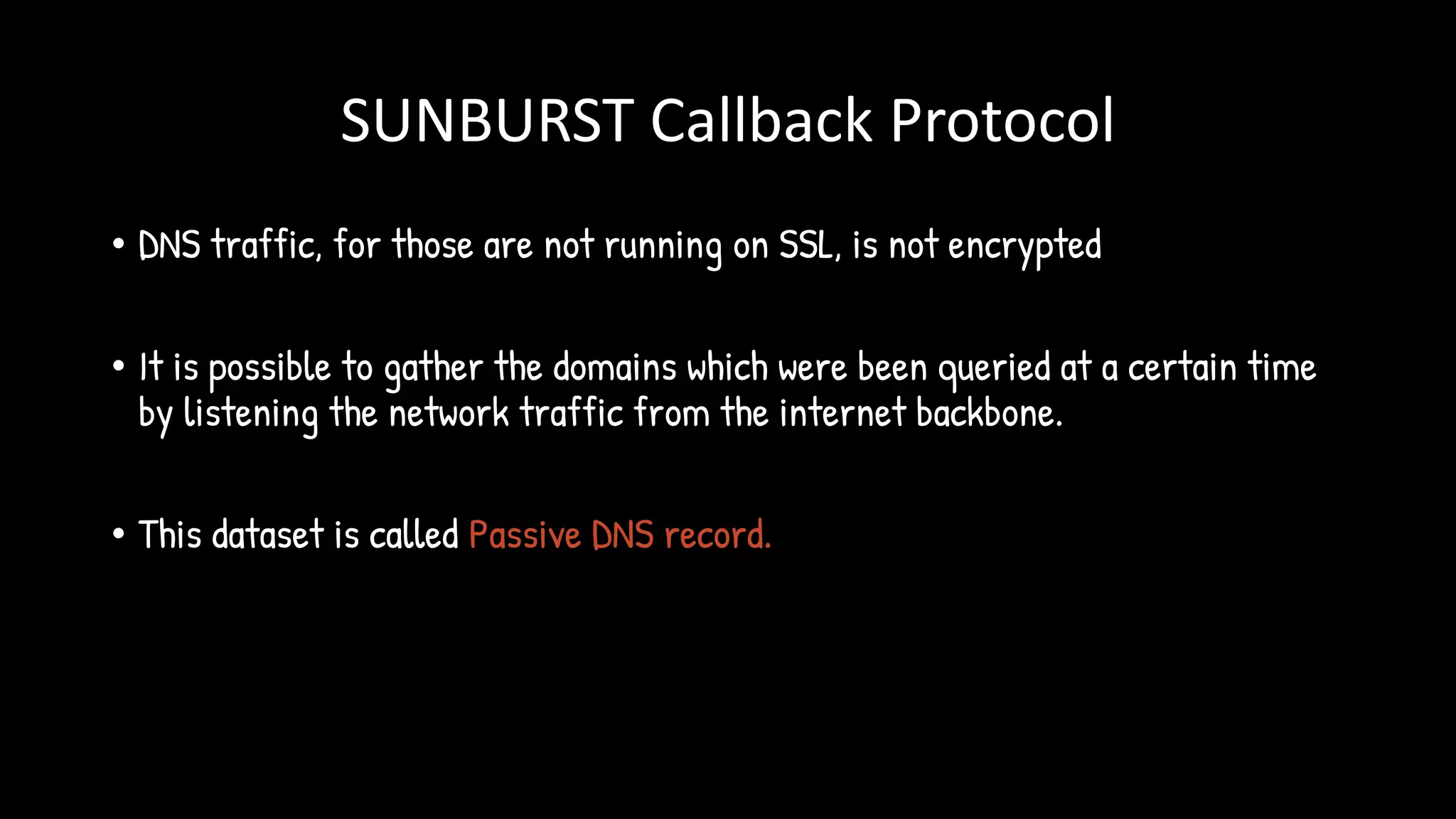
The document discusses the SolarWinds supply chain attack, detailing its impact, methodologies, and the importance of threat intelligence in identifying and mitigating such threats. It outlines the sophisticated nature of the malware used, specific incidents related to the attack, and the lessons learned regarding supply chain security vulnerabilities. The presentation also emphasizes proactive threat hunting and the collaboration within the security community to respond to advanced persistent threats.








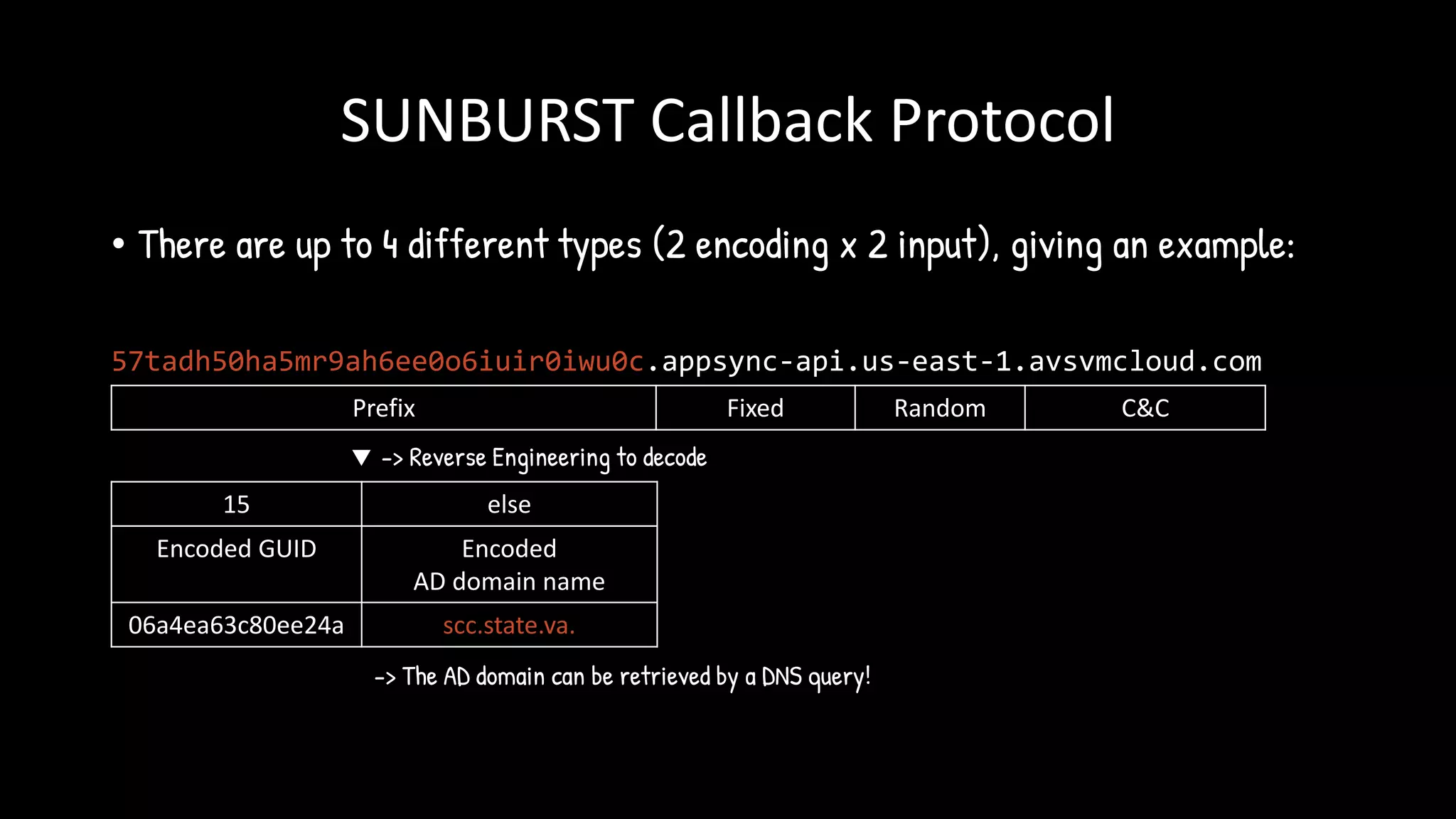
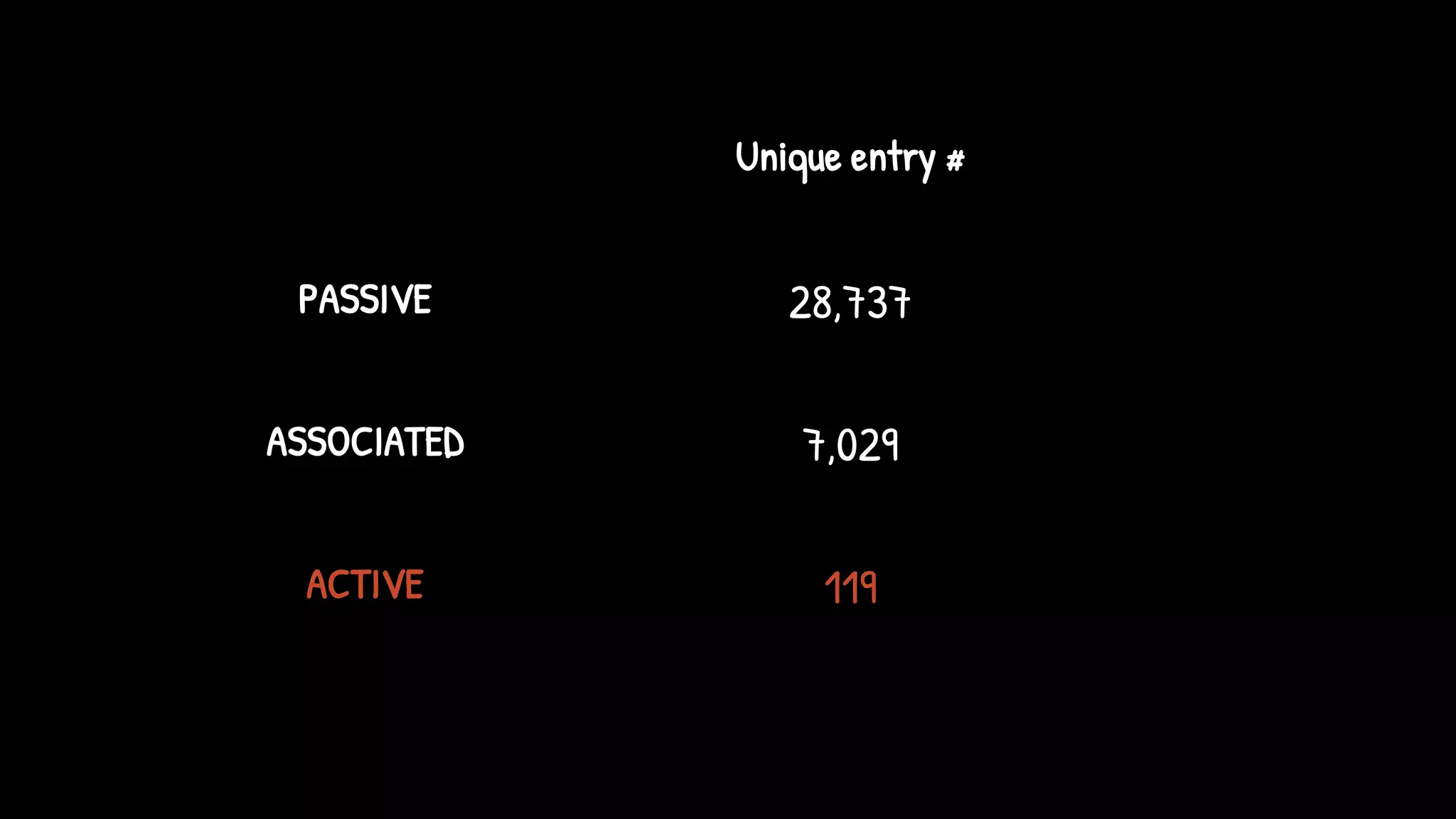
![ASSOCIATED
[T+AVs]
TRUNCATED
Backdoor stopped
PASSIVE
[domain[:15],
domain[15:]]
Potential Target,
Response magic A record
Not interesting
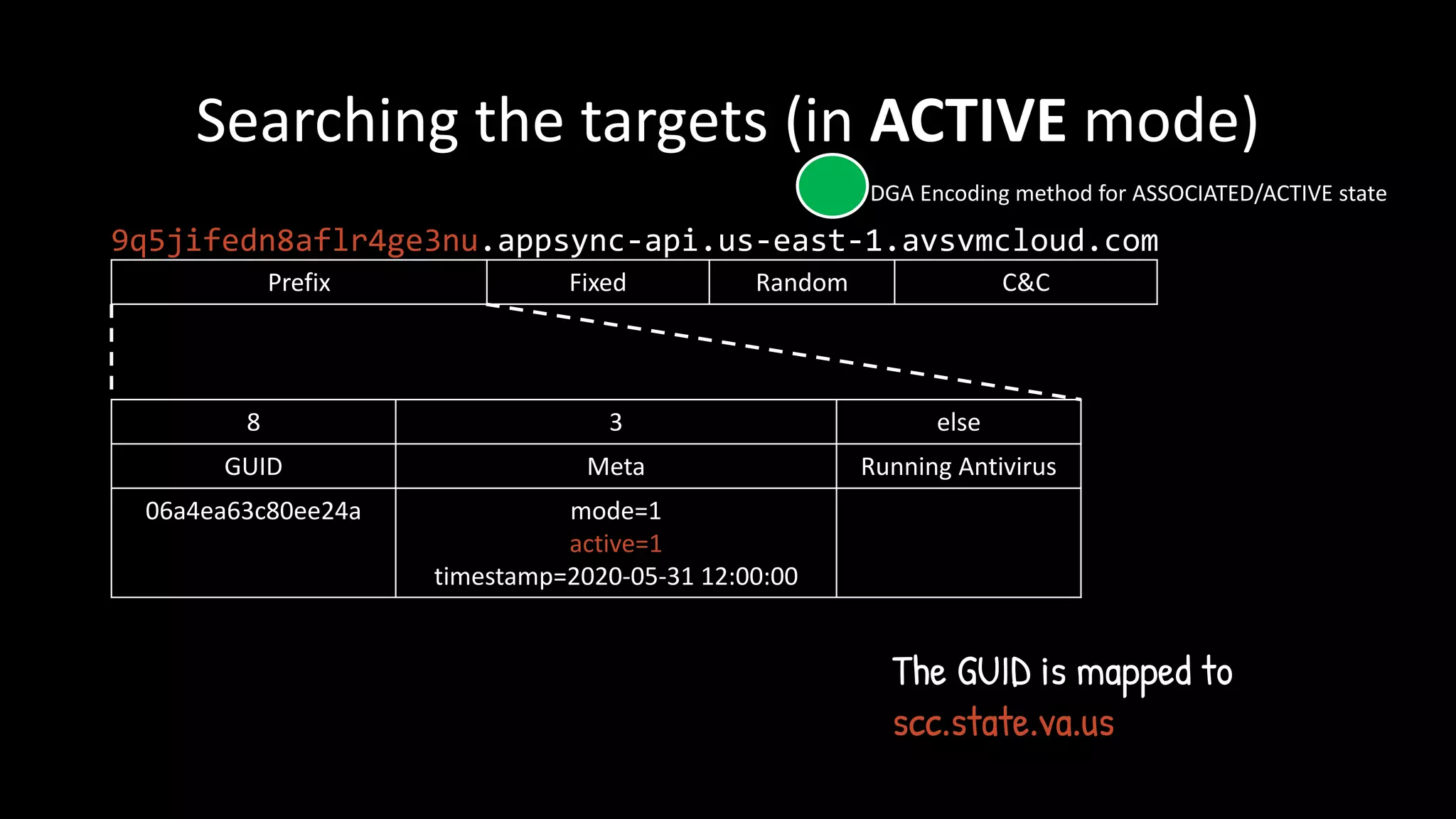
ACTIVE
Backdoor on HTTP
[T+AVs + Active bit]
Select Target,
Response HTTP C&C server at CNAME
DGA Encoding method for PASSIVE state
DGA Encoding method for ASSOCIATED/ACTIVE state](https://image.slidesharecdn.com/hitconfreetalkfinal-210317042326/75/HITCON-FreeTalk-2021-SolarWinds-19-2048.jpg)
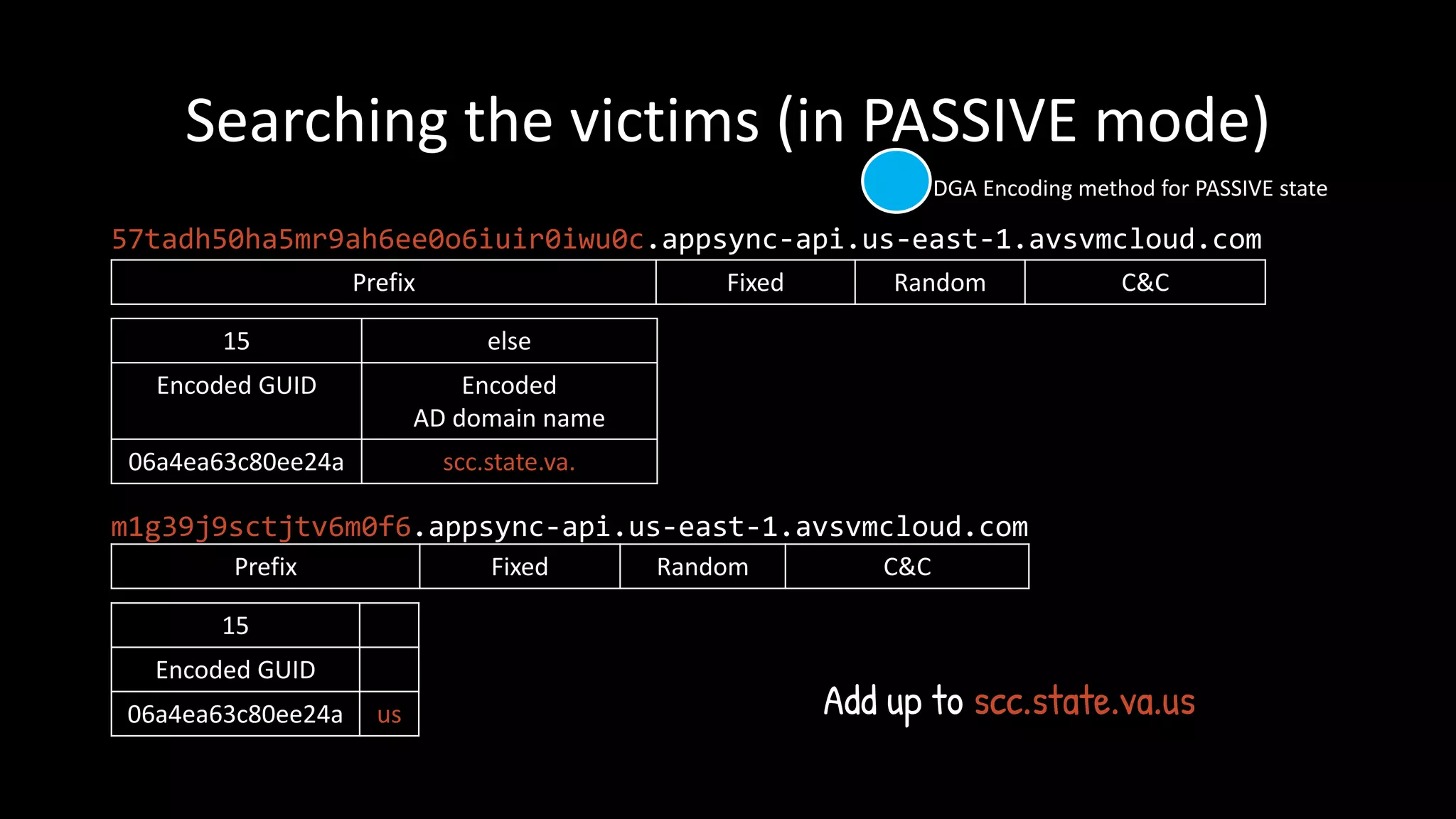
![ASSOCIATED
[T+AVs]
TRUNCATED
Backdoor stopped
ACTIVE
Backdoor on HTTP
[T+AVs + Active bit]
Select Target,
Response HTTP C&C server at CNAME
DGA Encoding method for PASSIVE state
DGA Encoding method for ASSOCIATED/ACTIVE state](https://image.slidesharecdn.com/hitconfreetalkfinal-210317042326/75/HITCON-FreeTalk-2021-SolarWinds-22-2048.jpg)