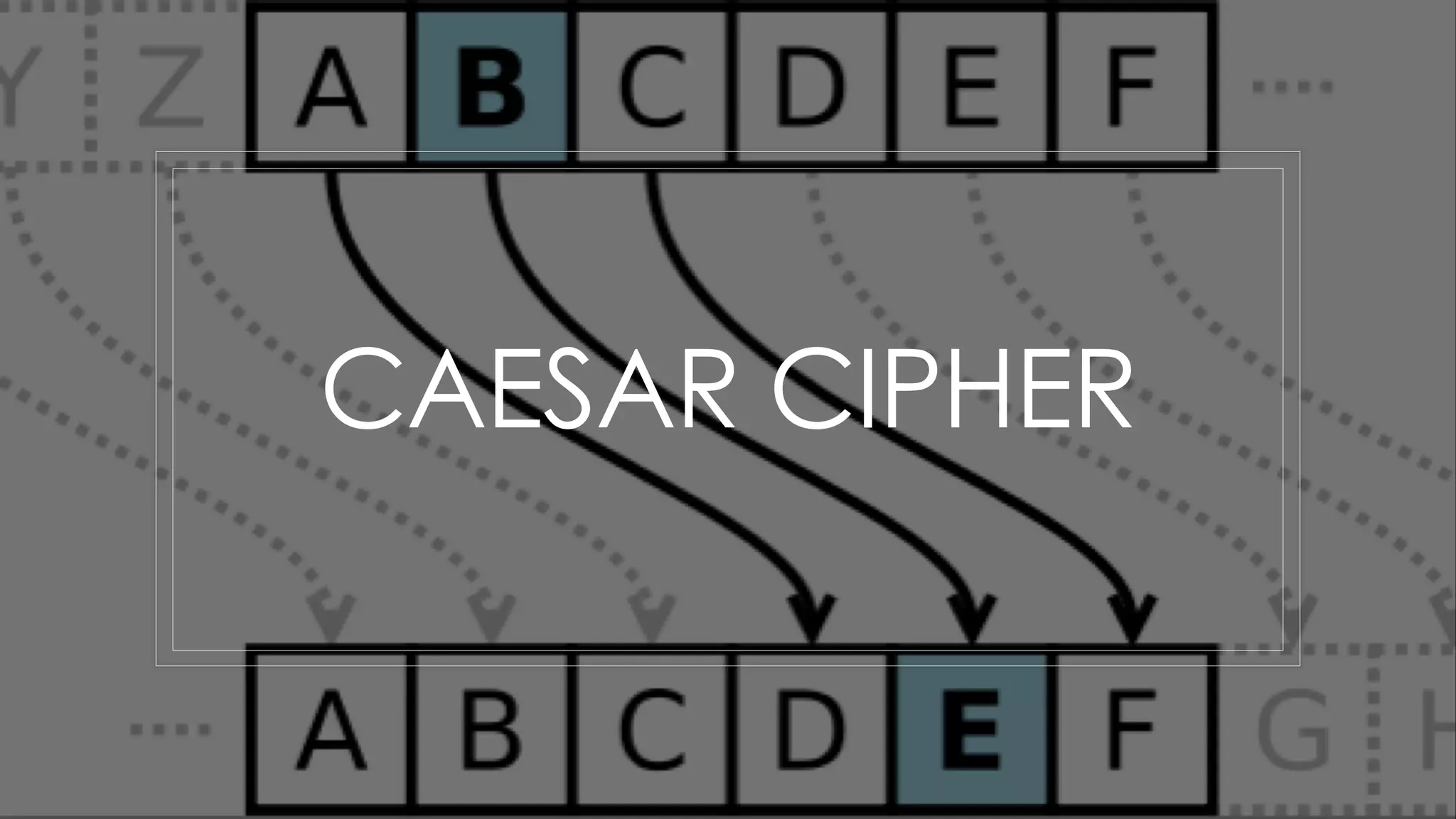
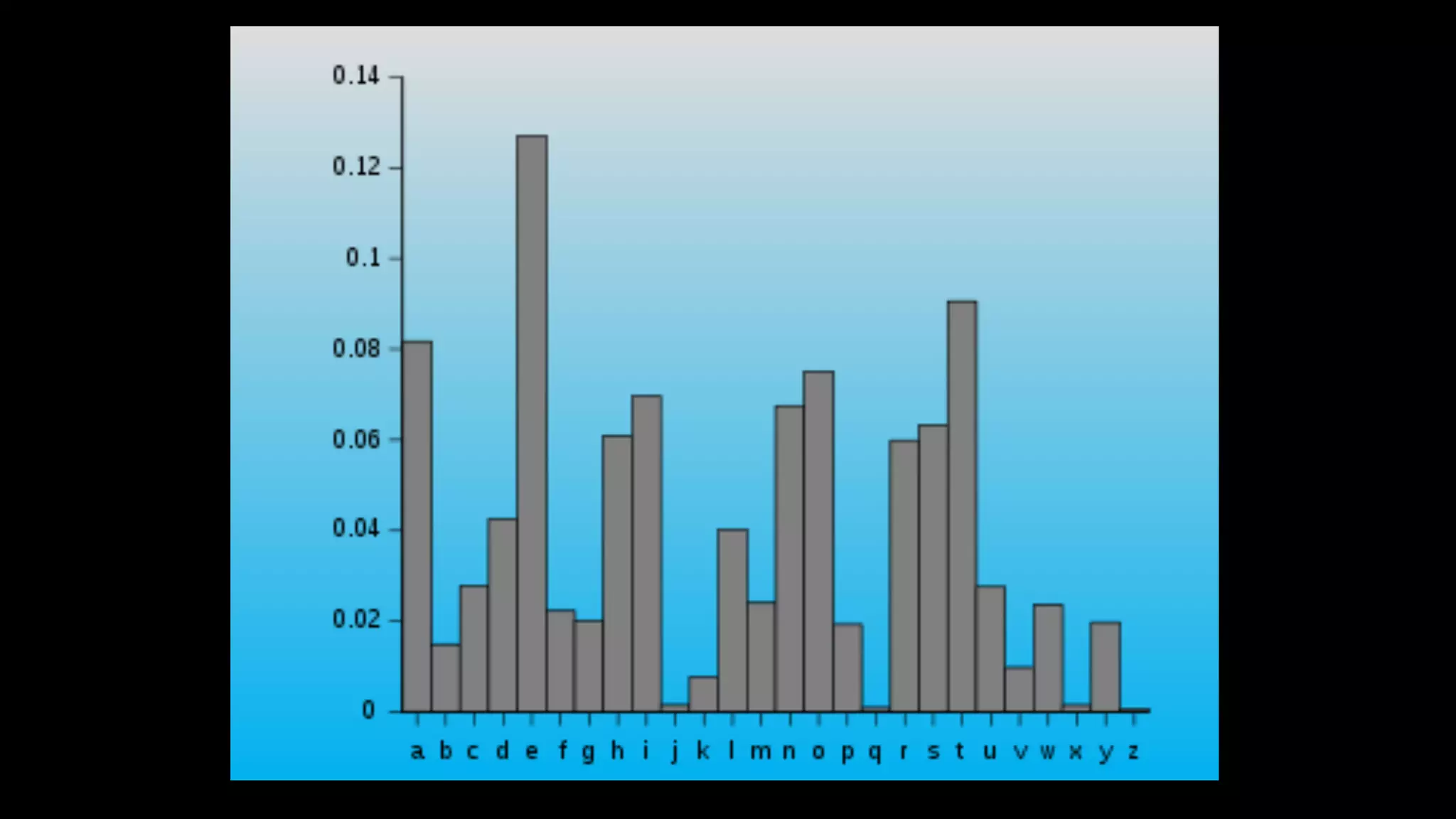
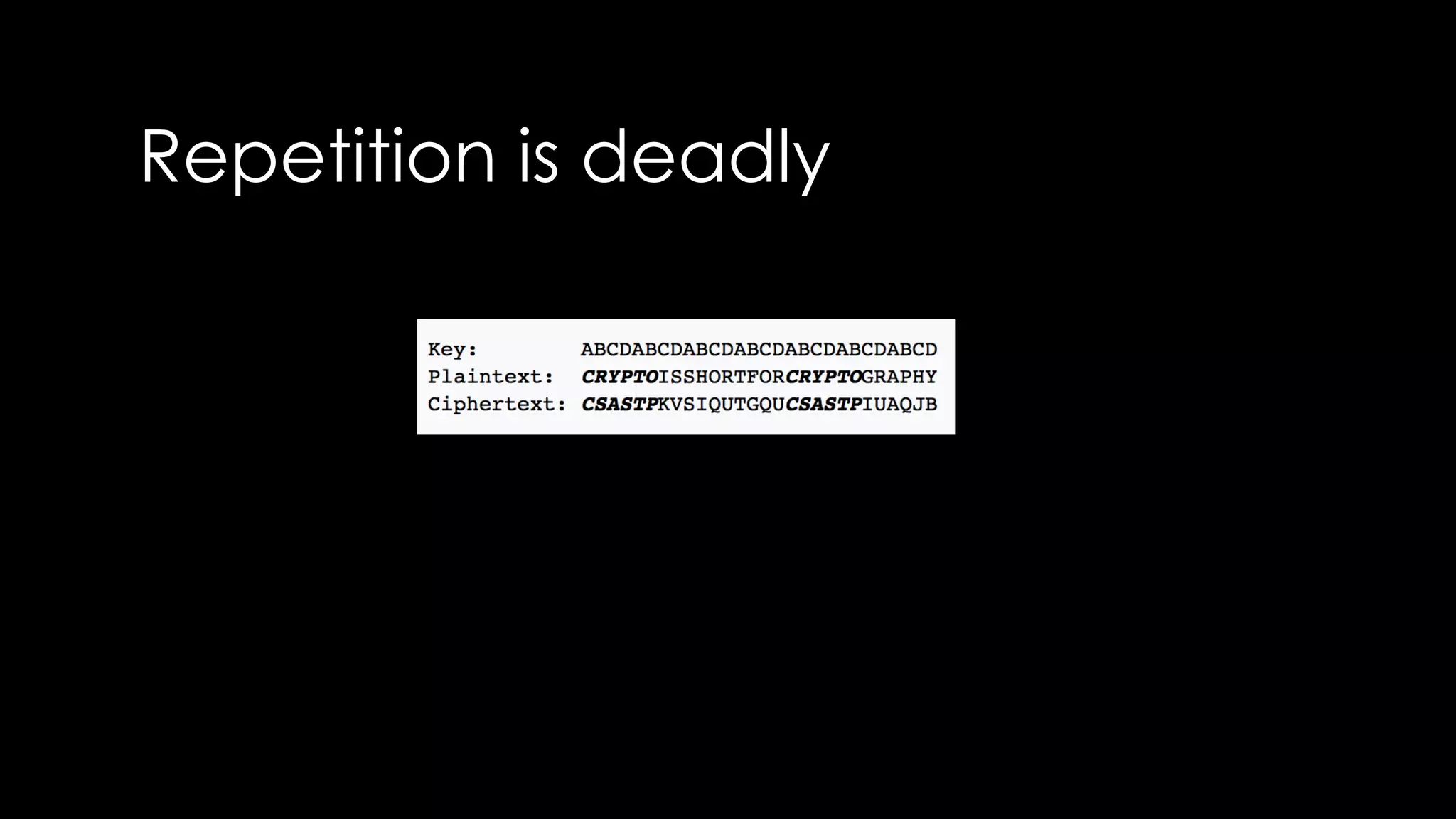
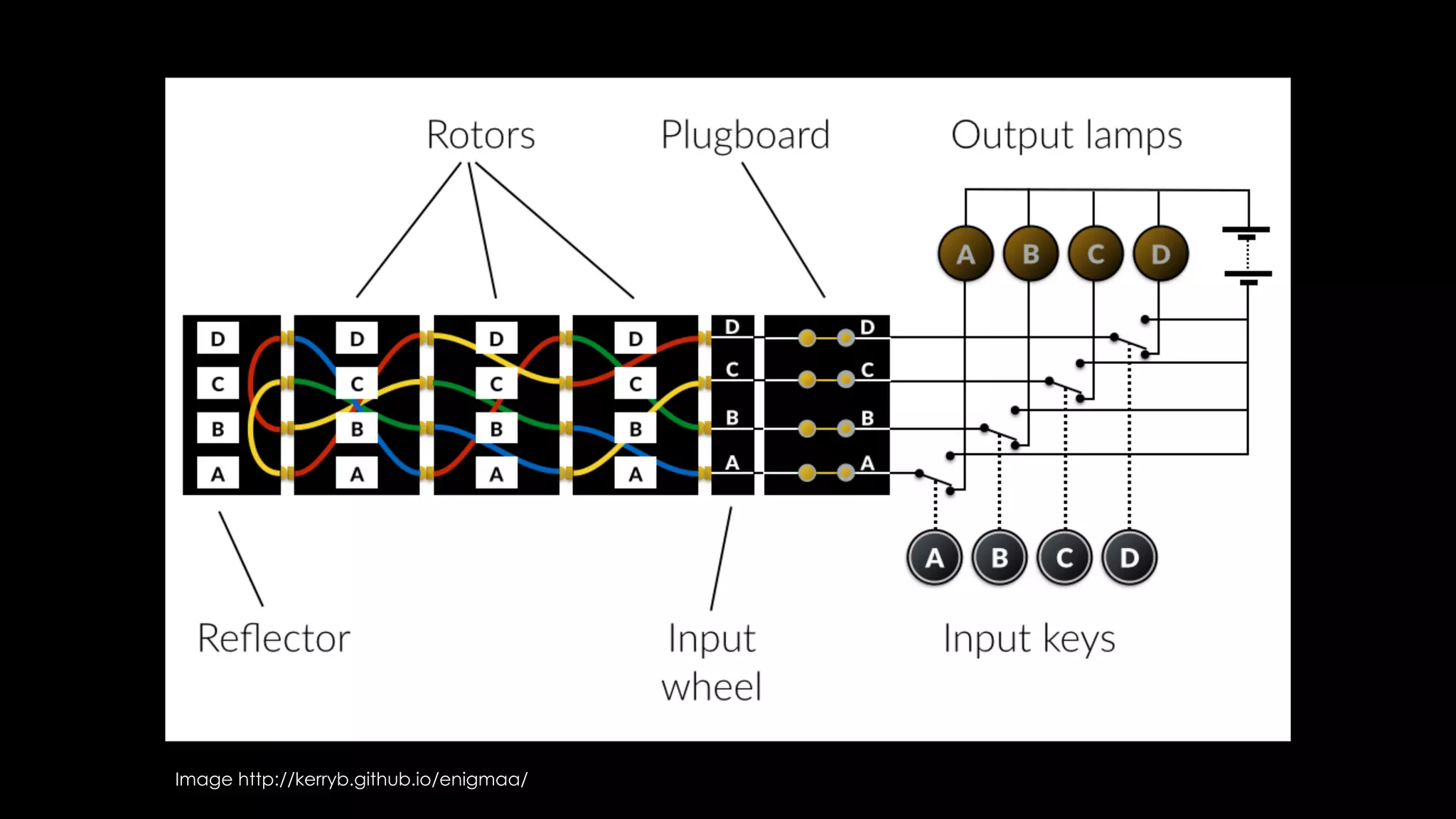
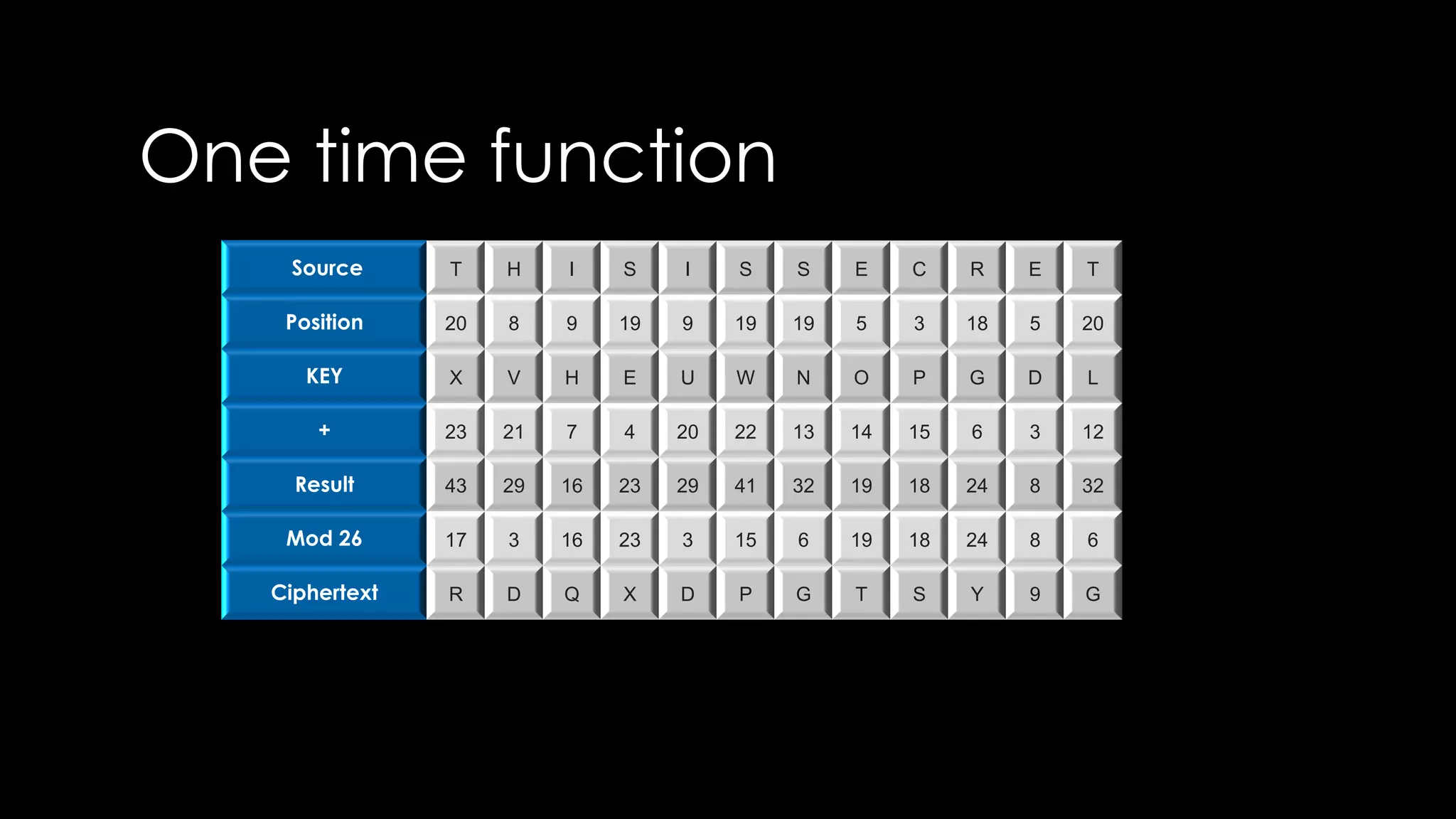
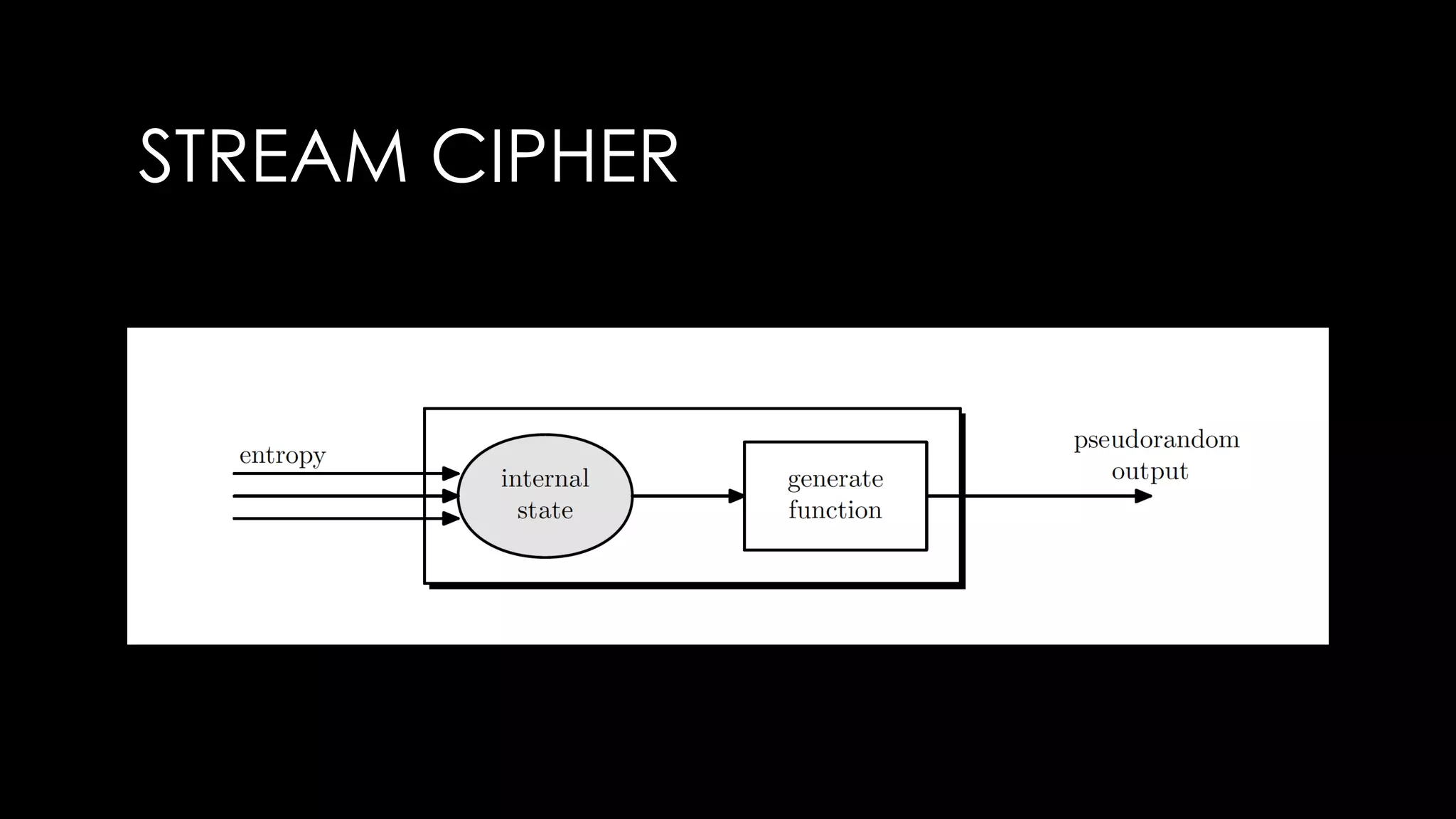
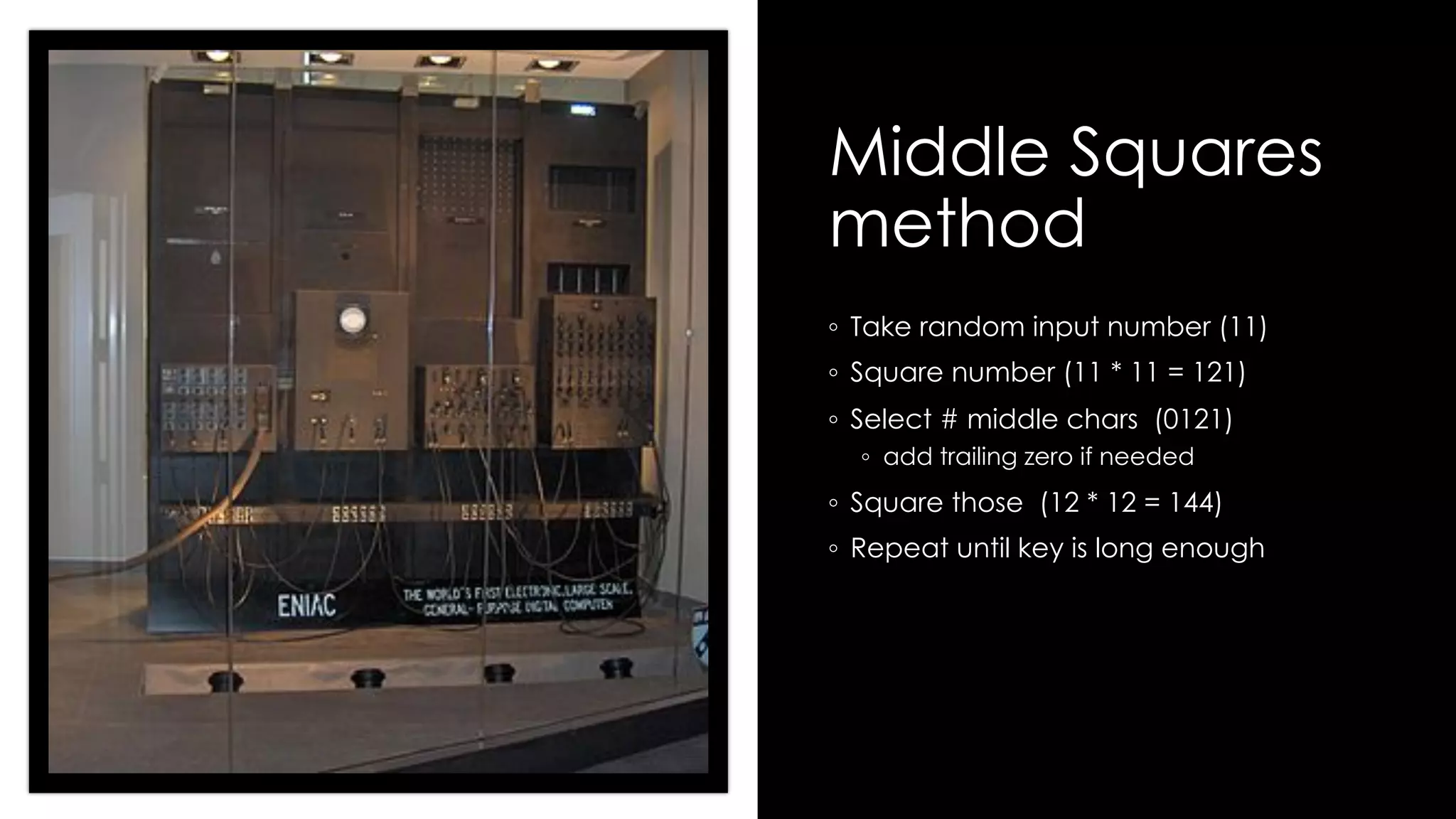
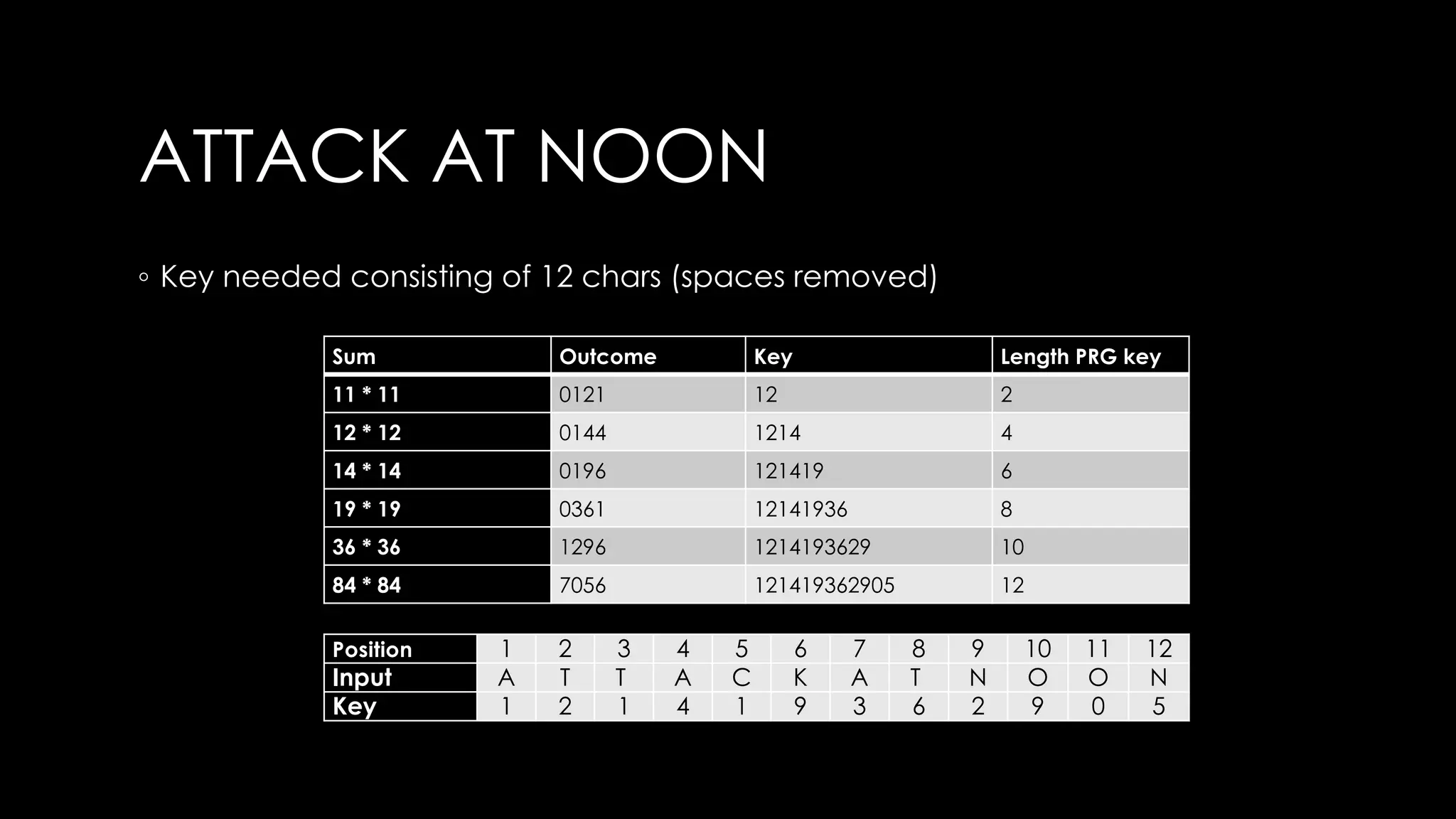
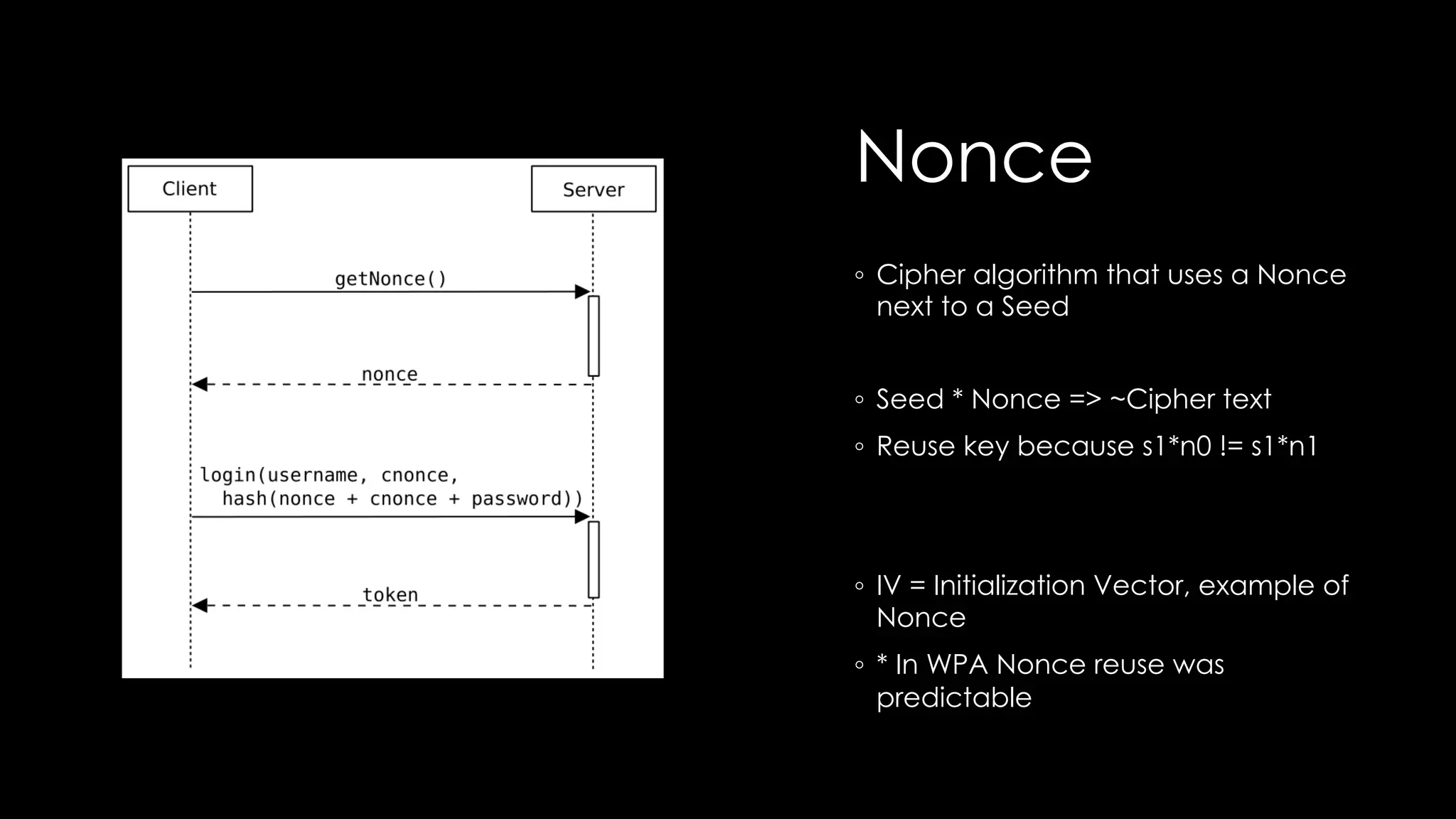
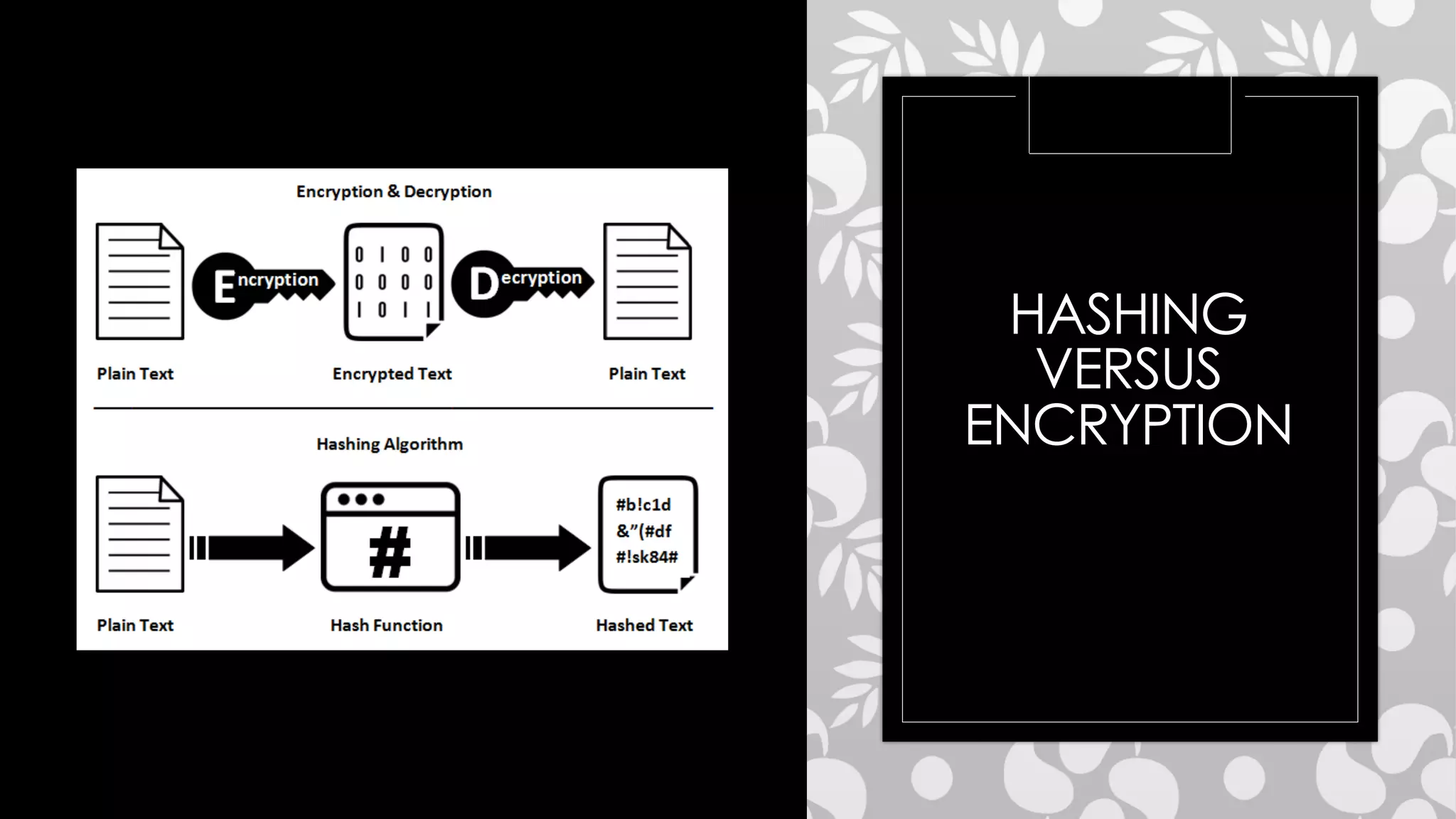
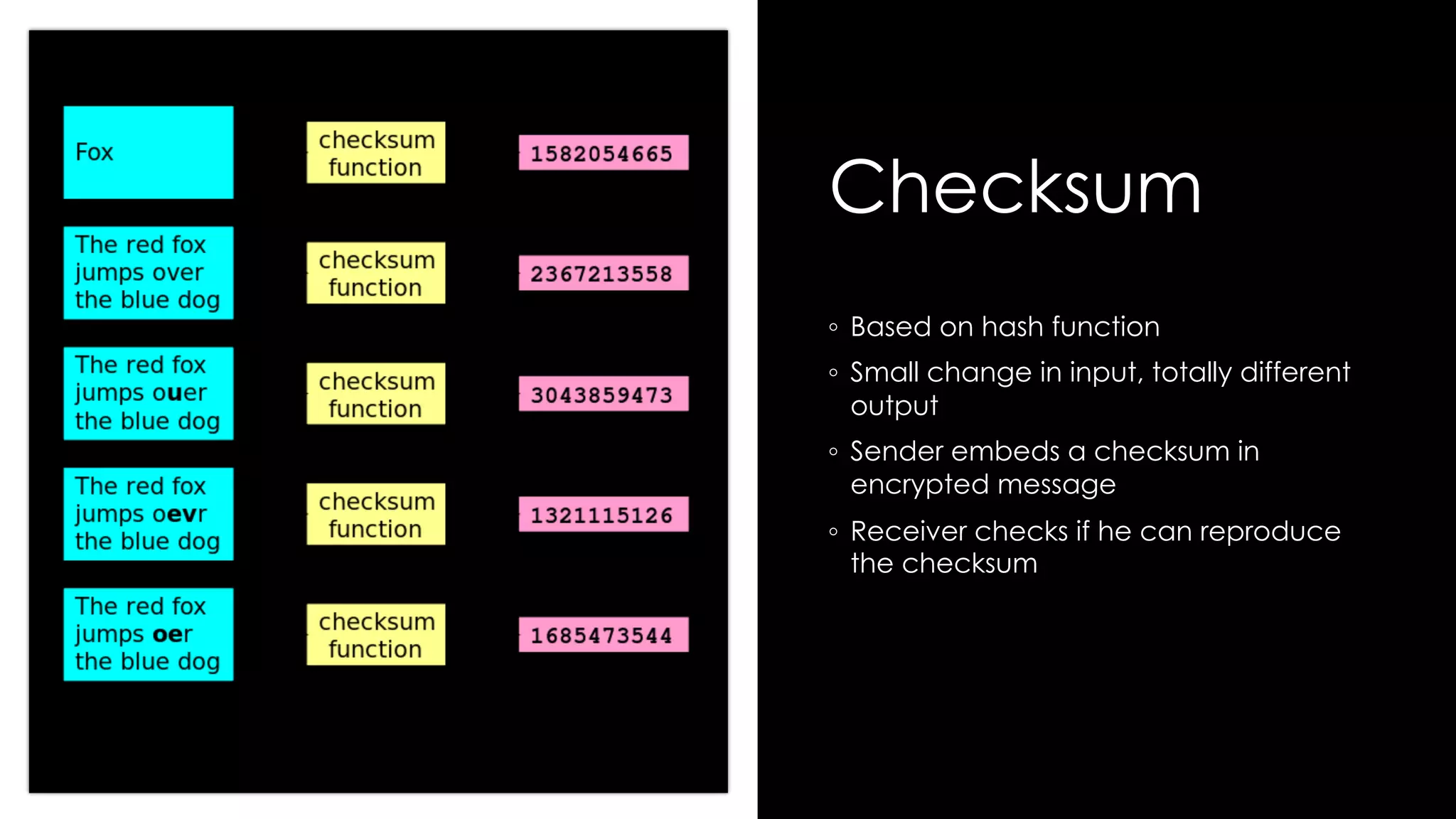
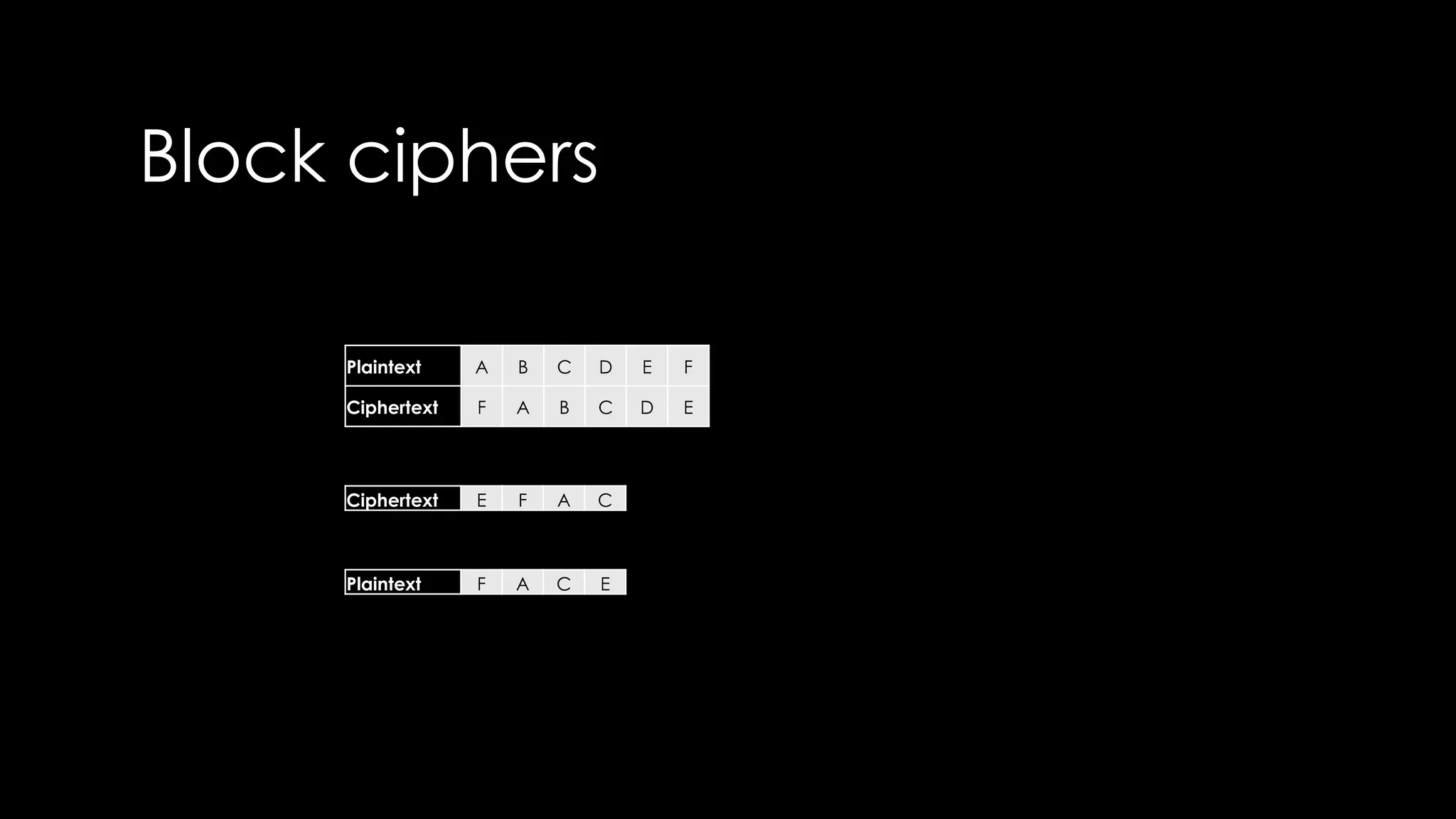
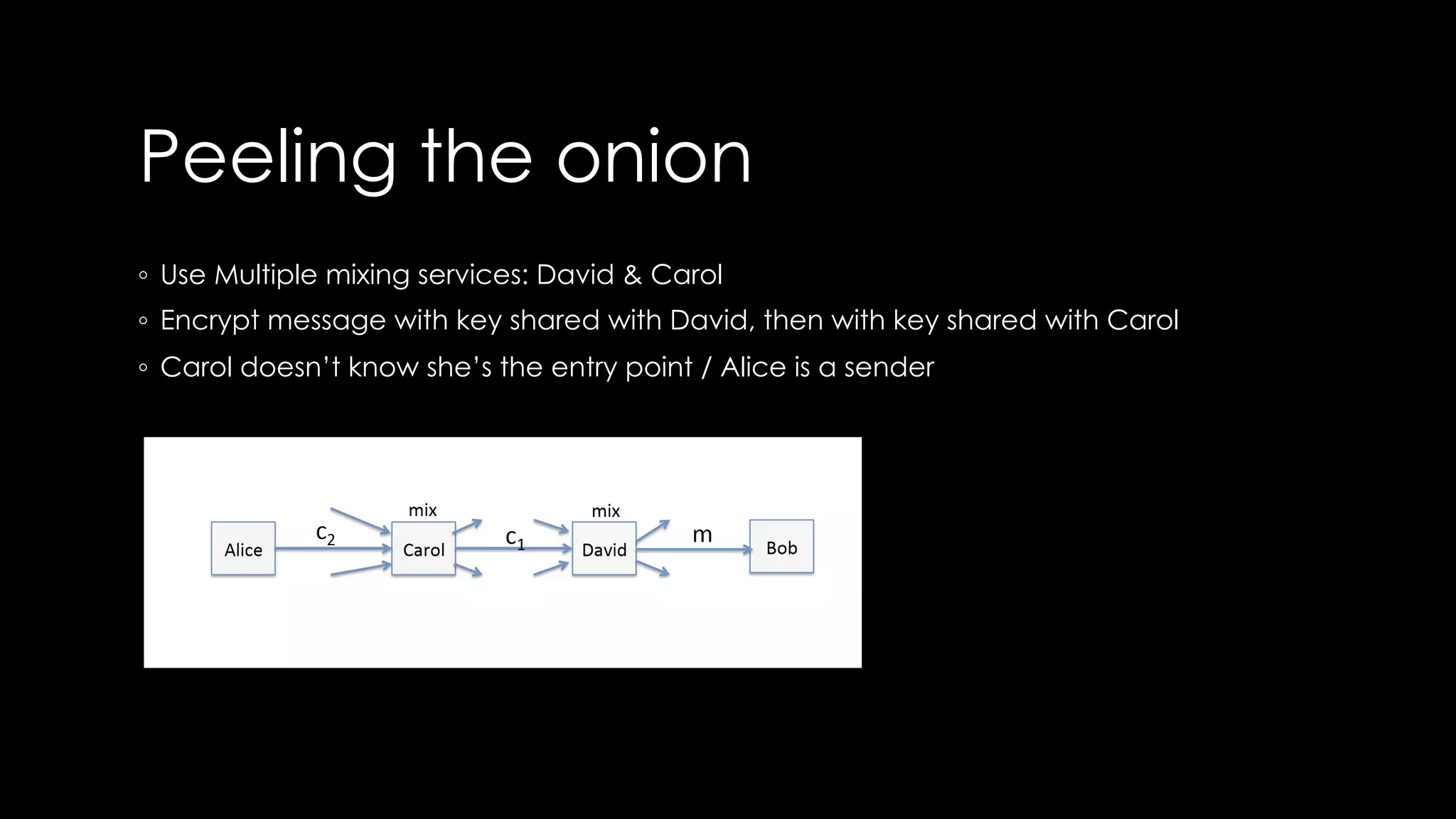
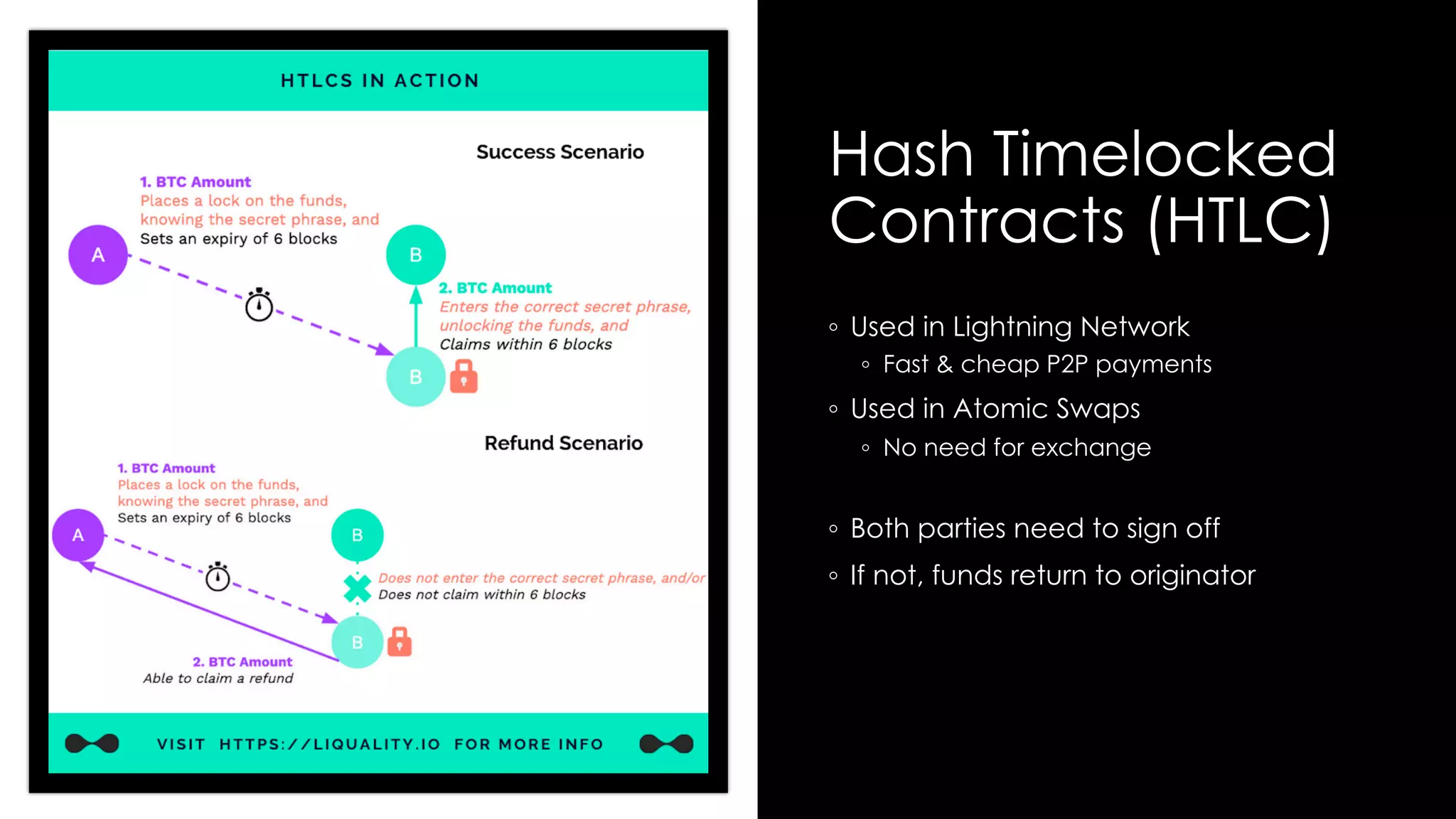
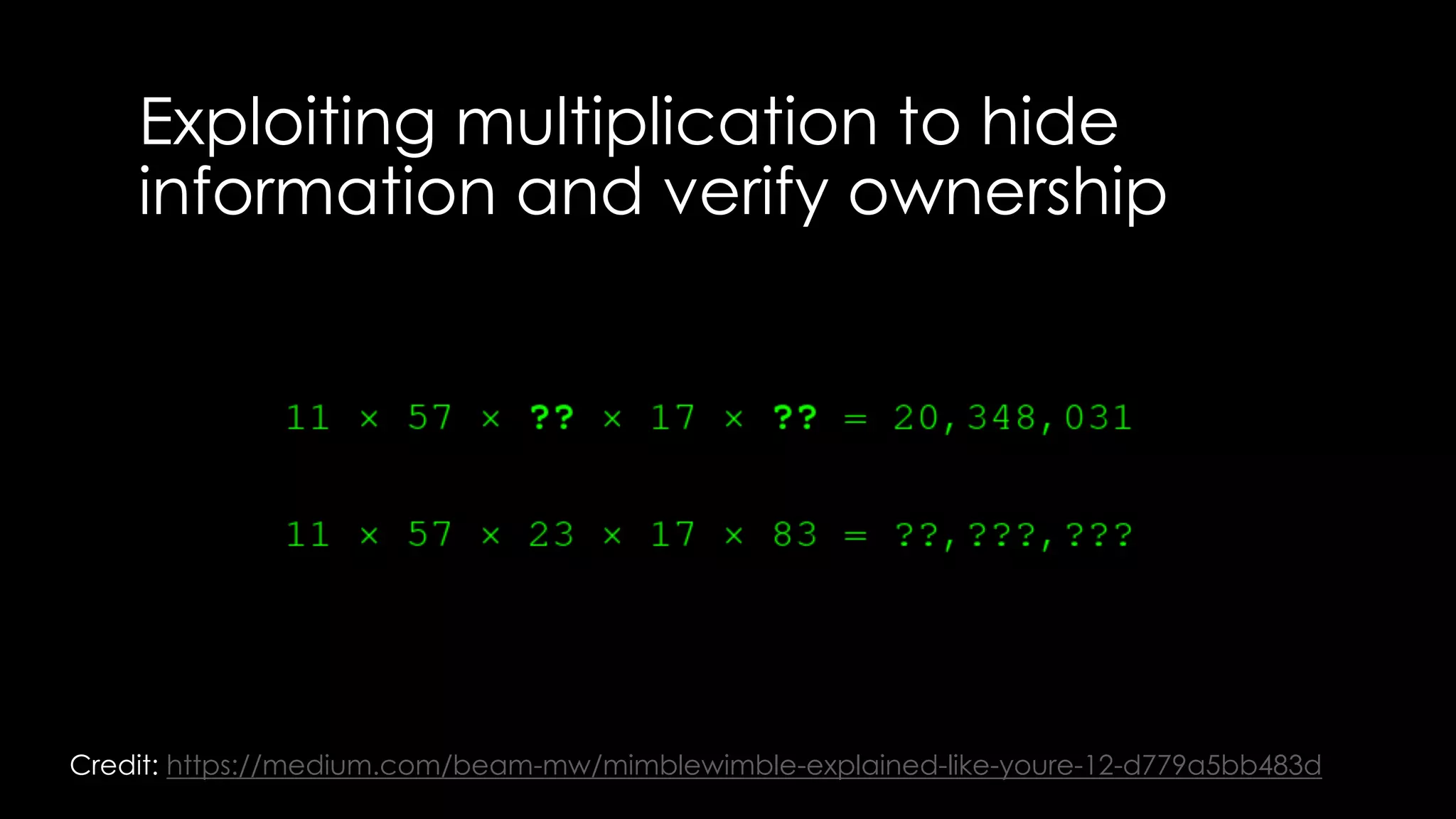
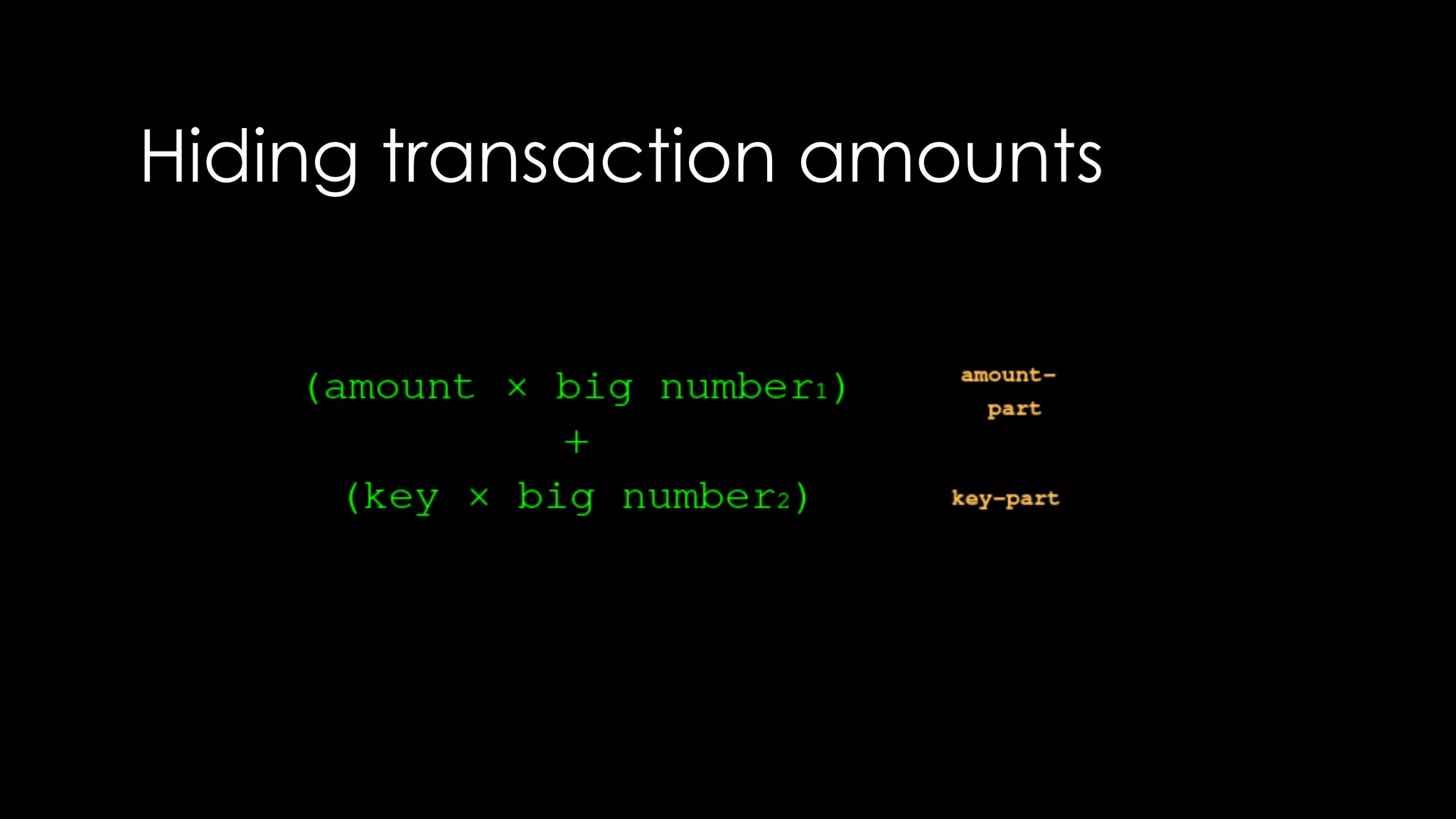
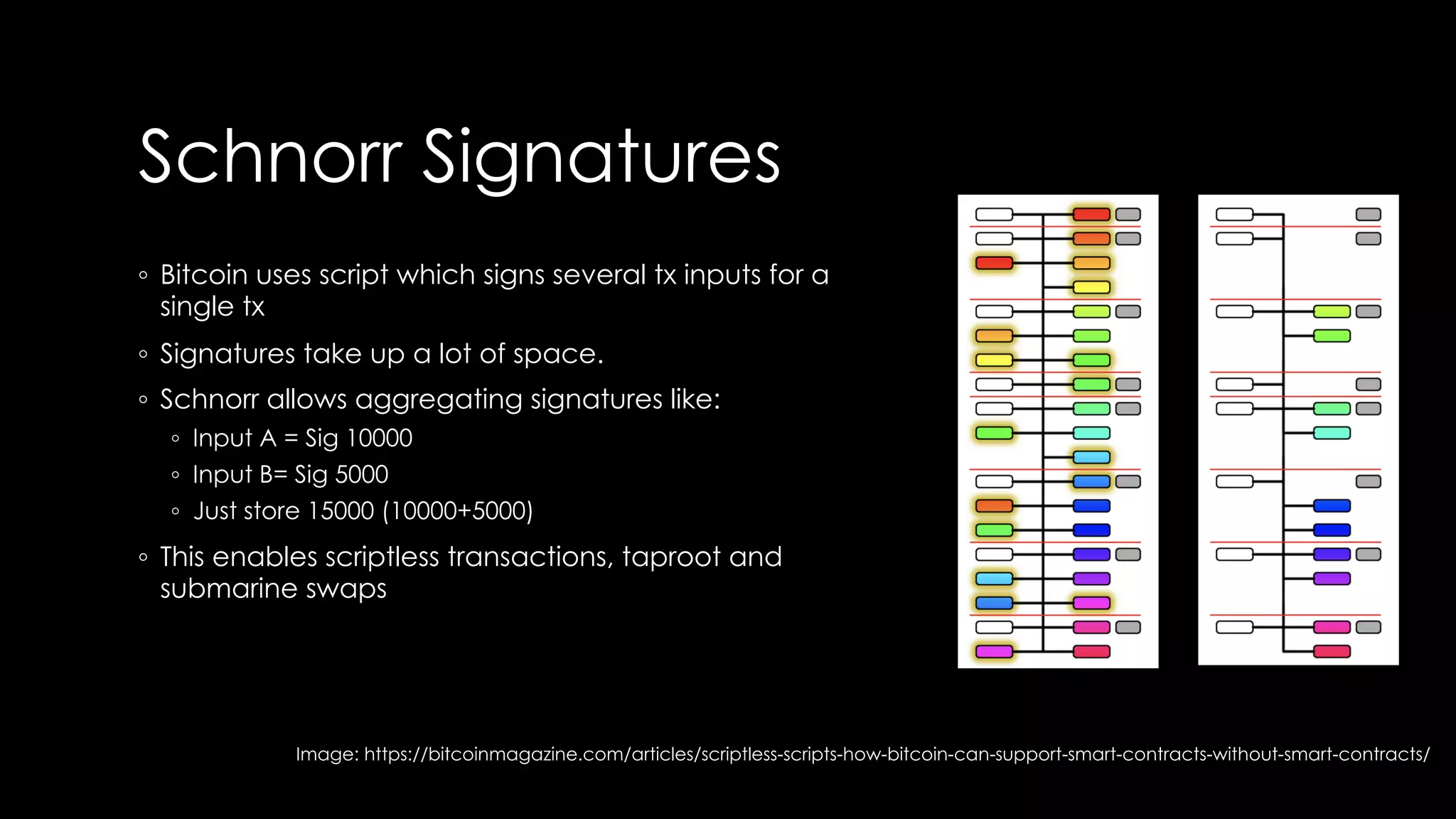
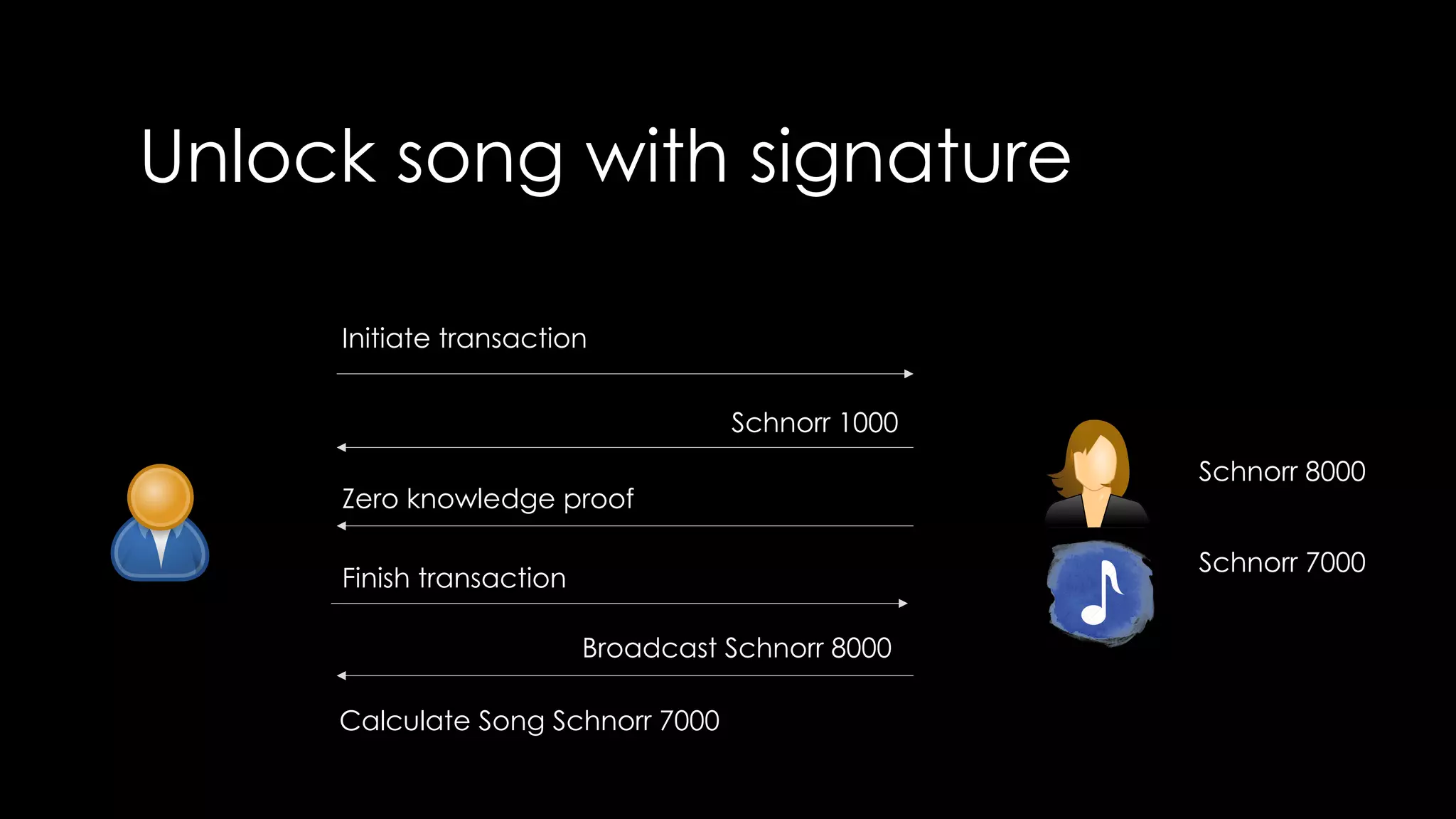
Roy Wasse presented an overview of cryptography concepts including classical ciphers like the Caesar cipher and Vigenère cipher. Modern symmetric ciphers use pseudorandom number generators with nonces to prevent key reuse. Asymmetric encryption allows public/private key pairs. Quantum computing may break current algorithms like RSA and ECC. Anonymity can be achieved using mixing services and onion routing. Zero-knowledge proofs allow verification without revealing information. New developments like Schnorr signatures and Mimblewimble aim to improve scalability and privacy in cryptocurrencies.