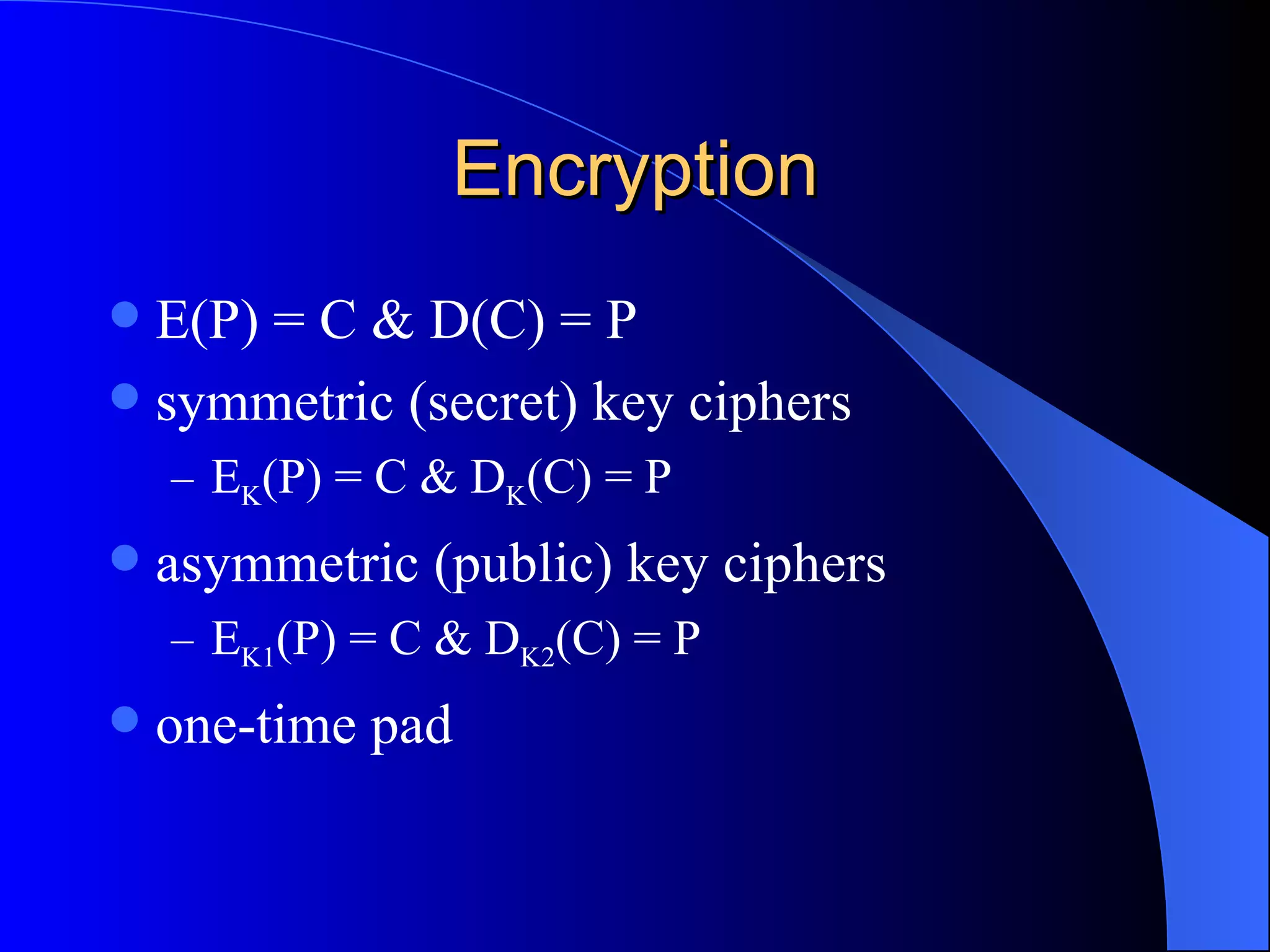
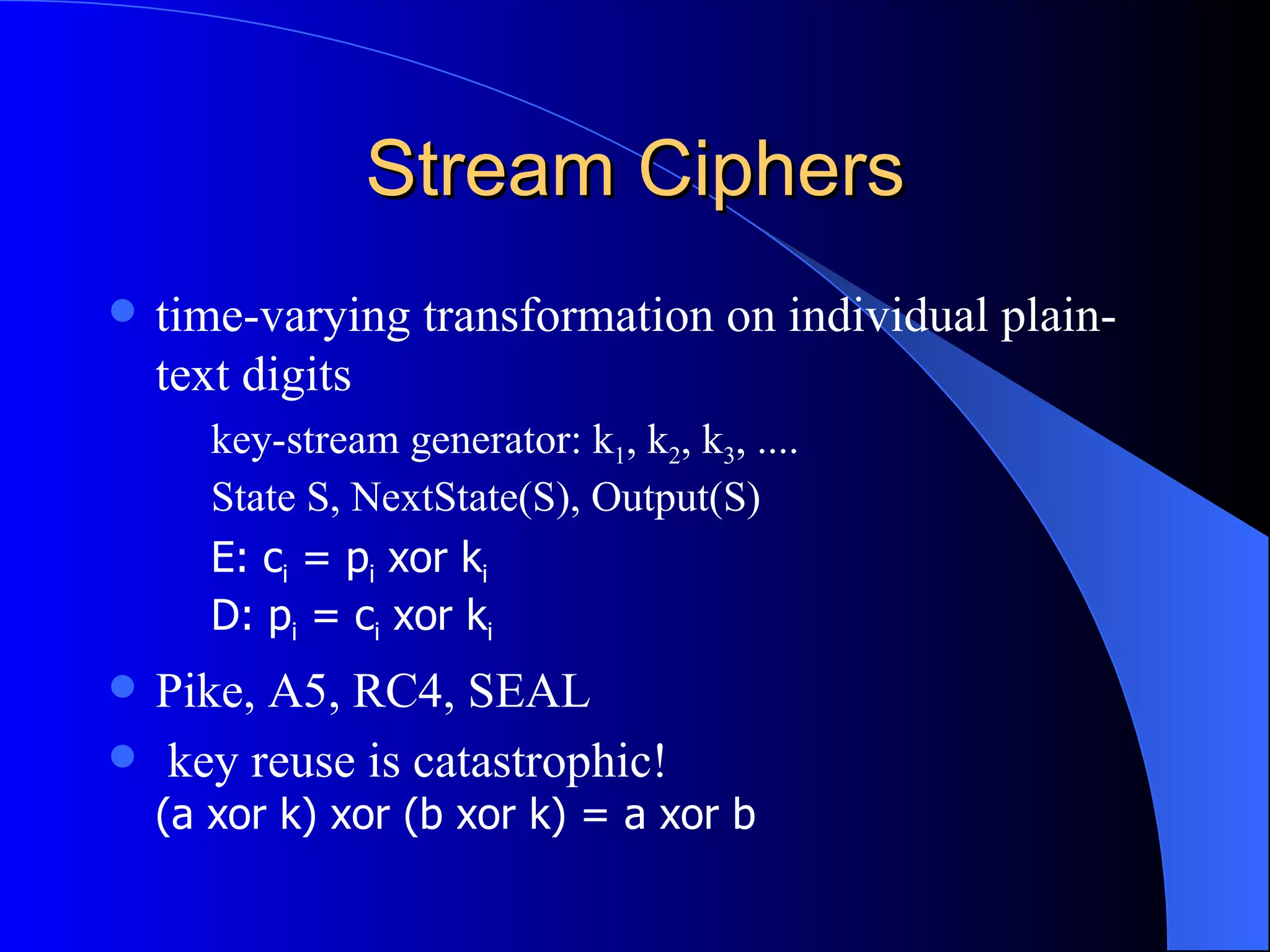
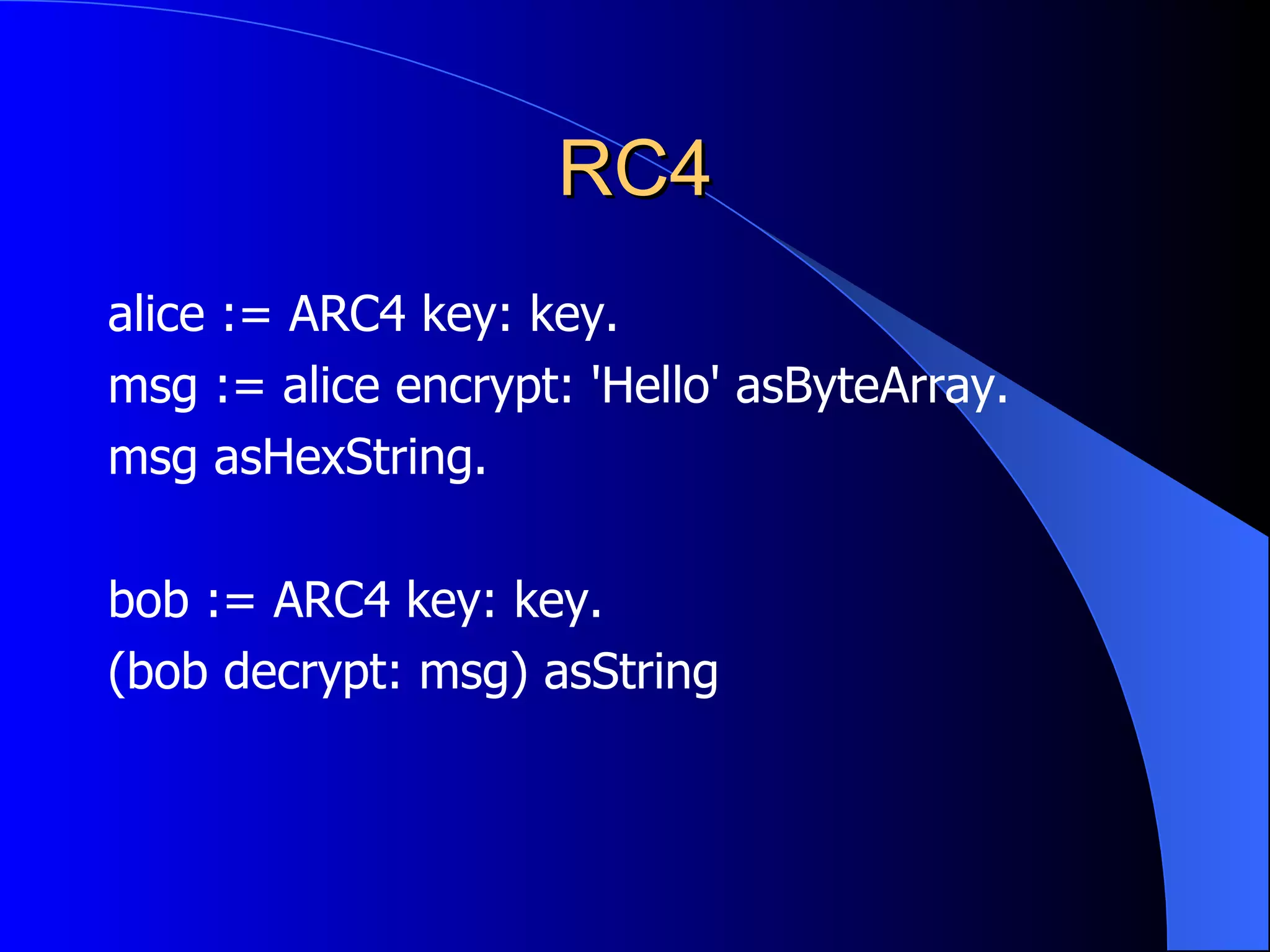
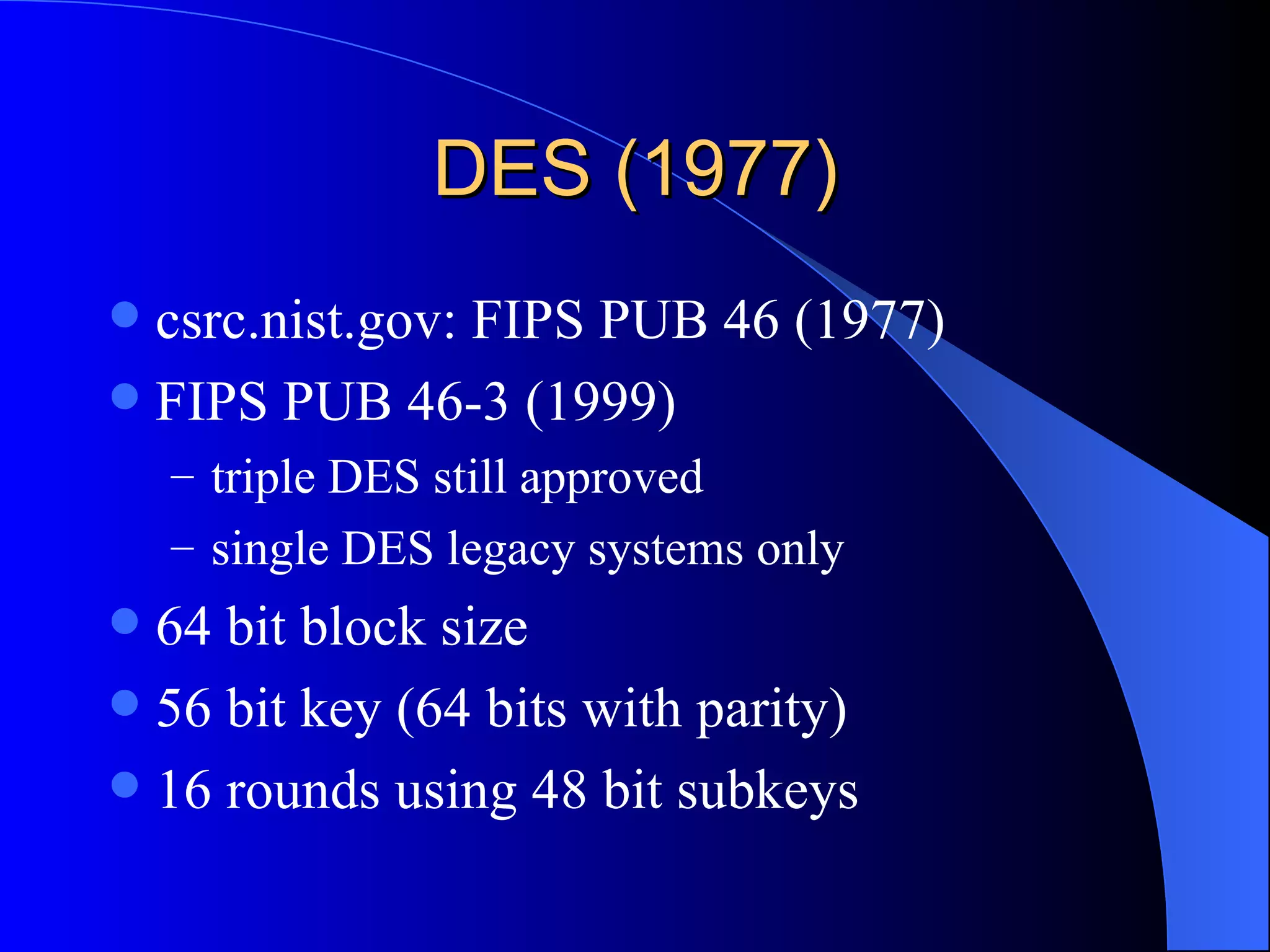
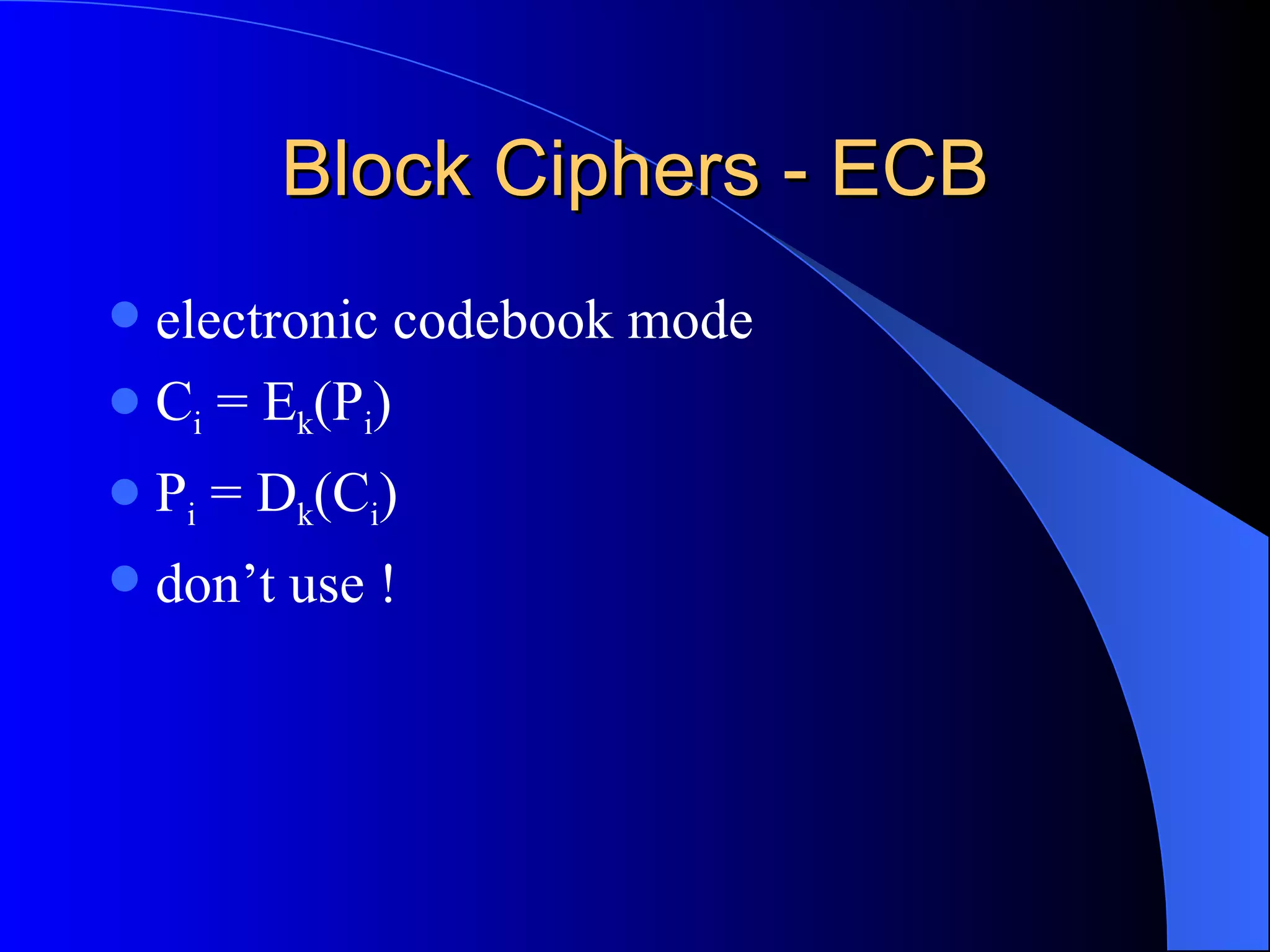
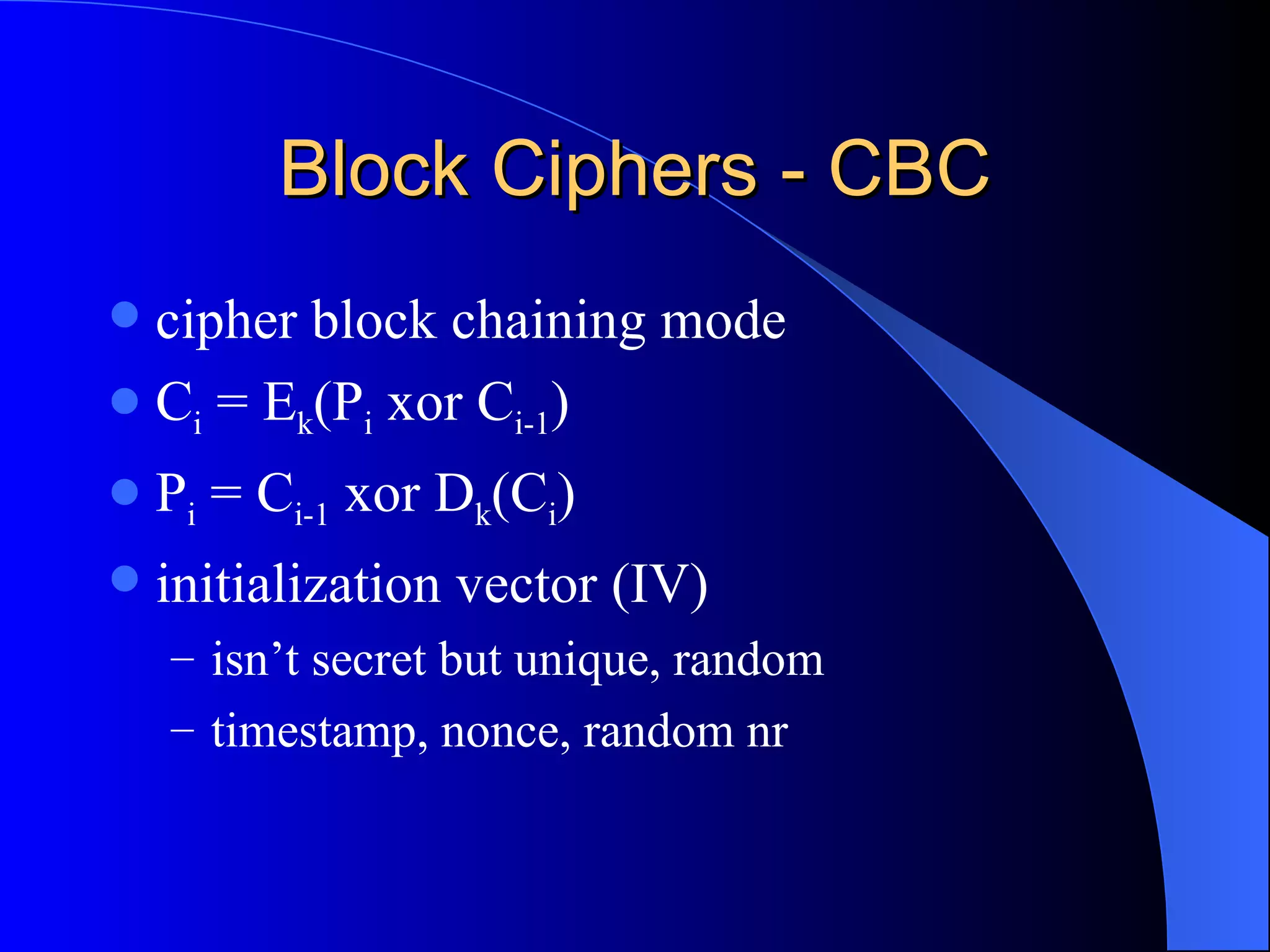
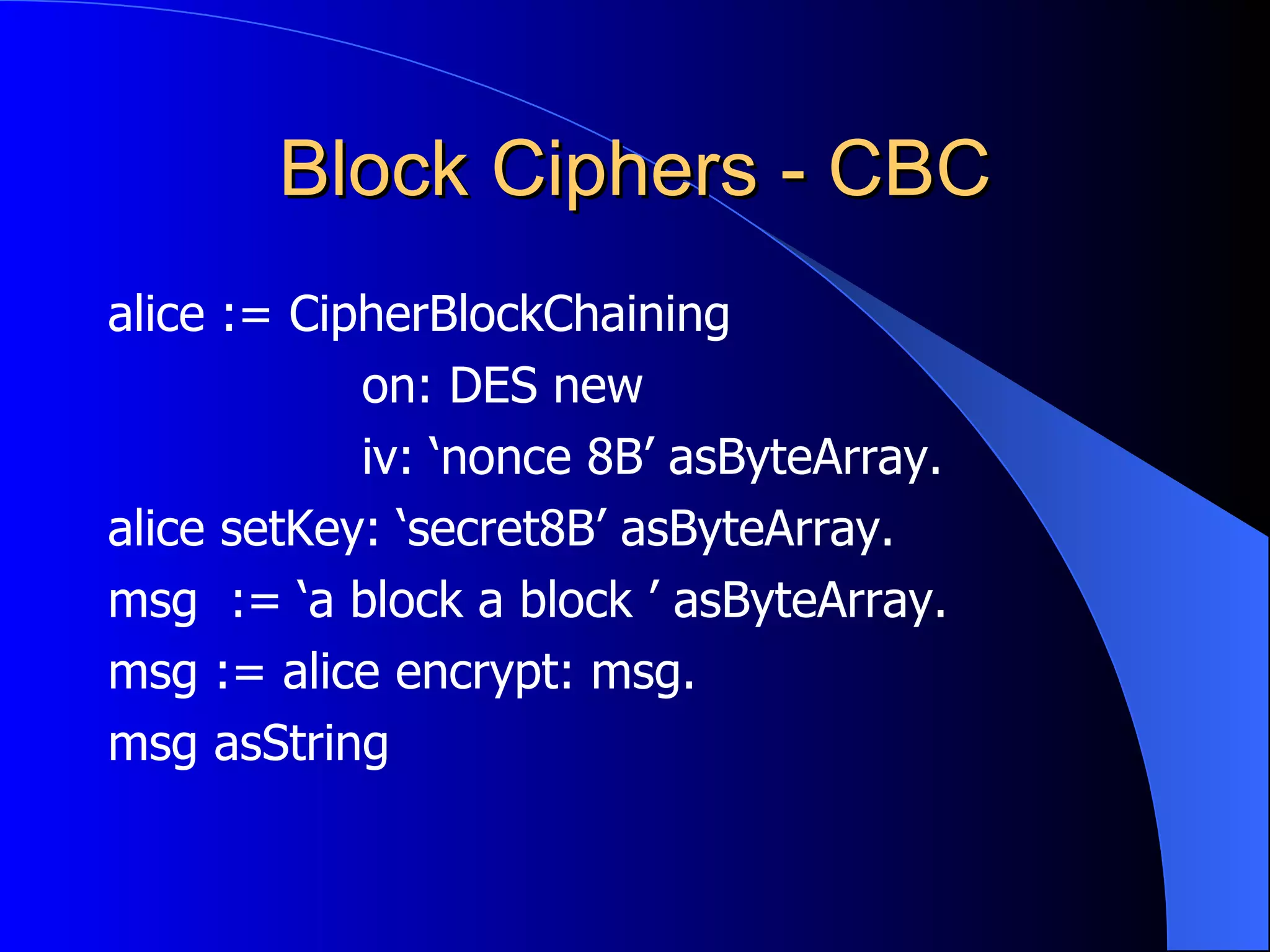
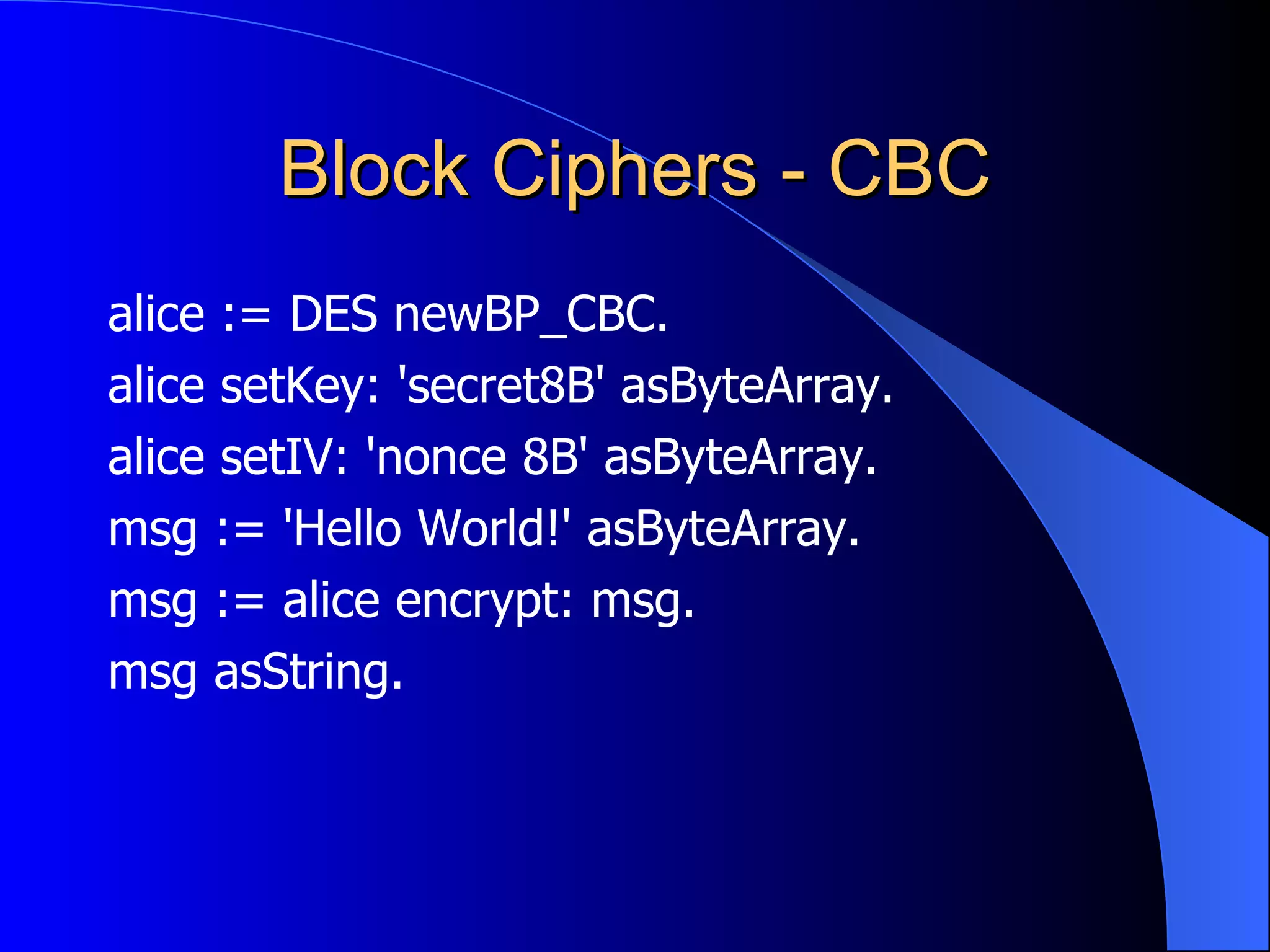
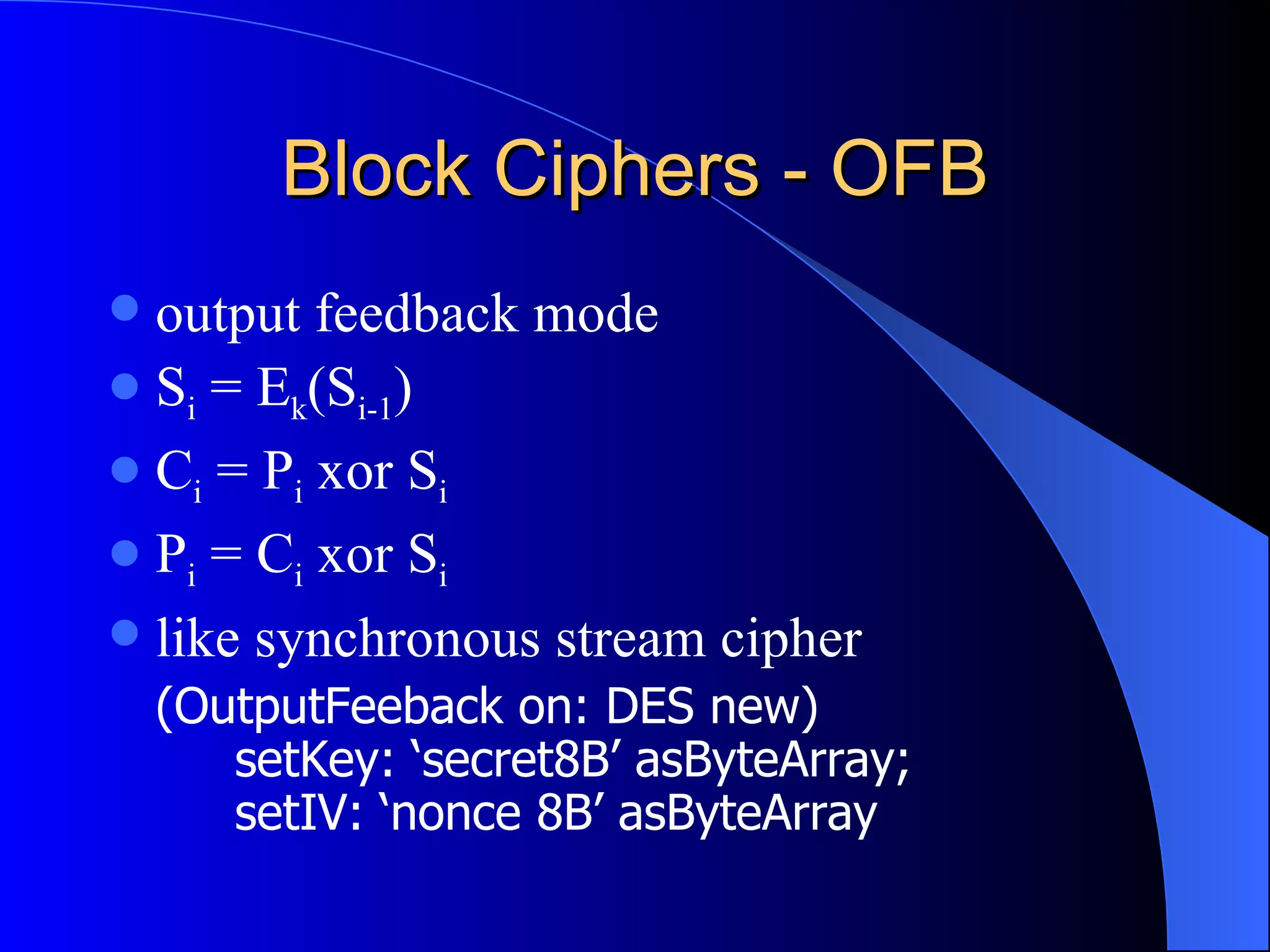
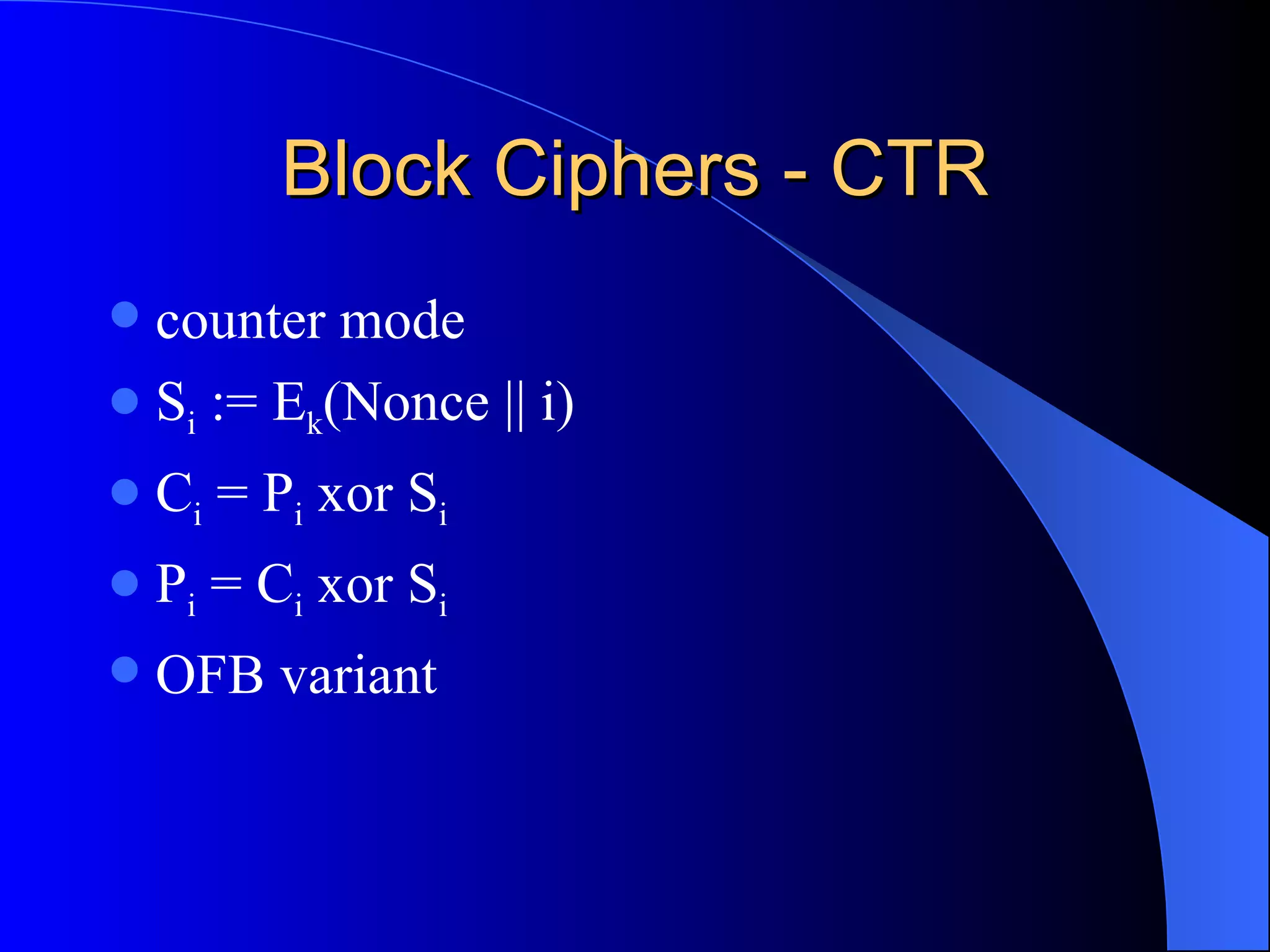
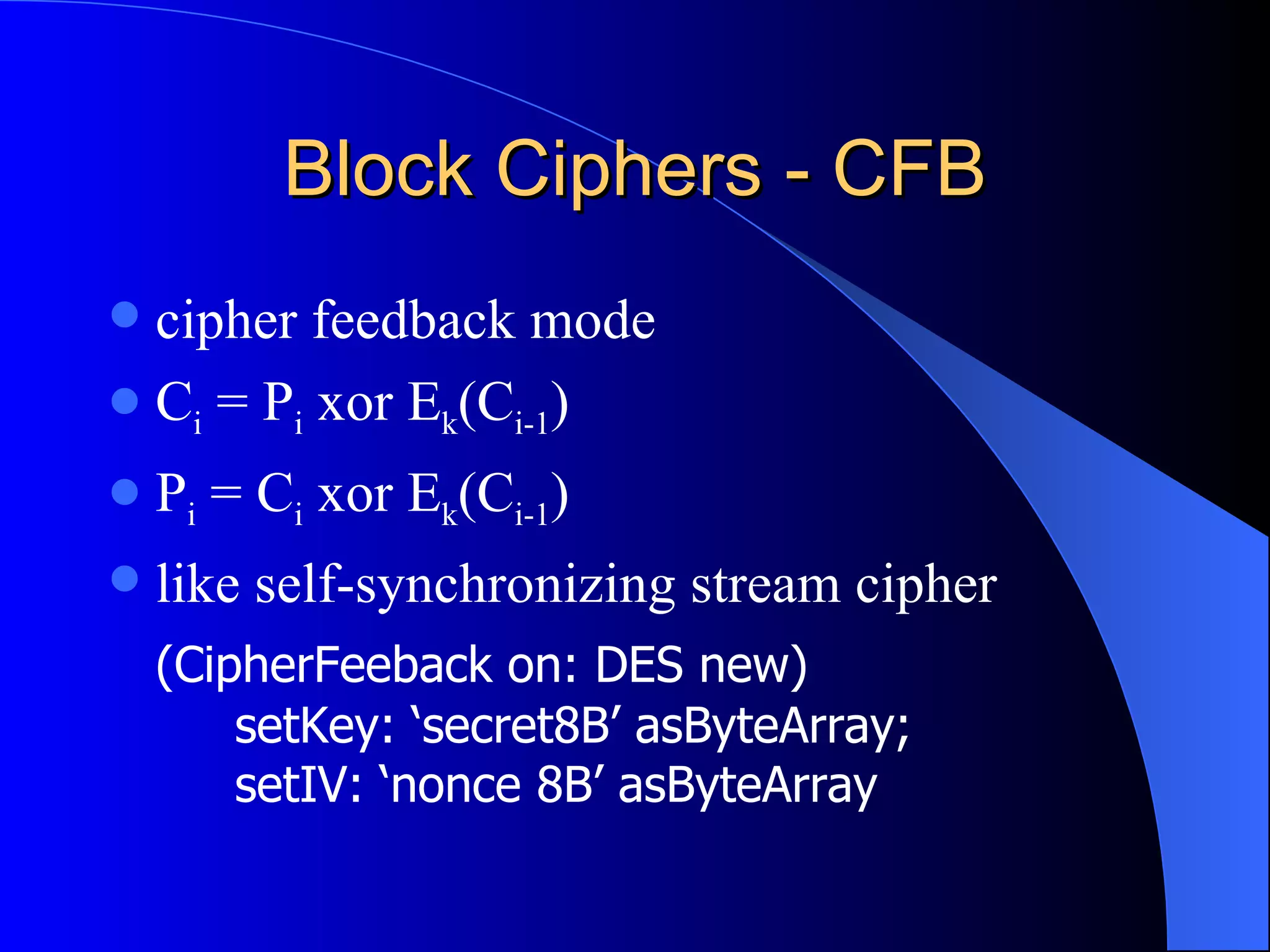
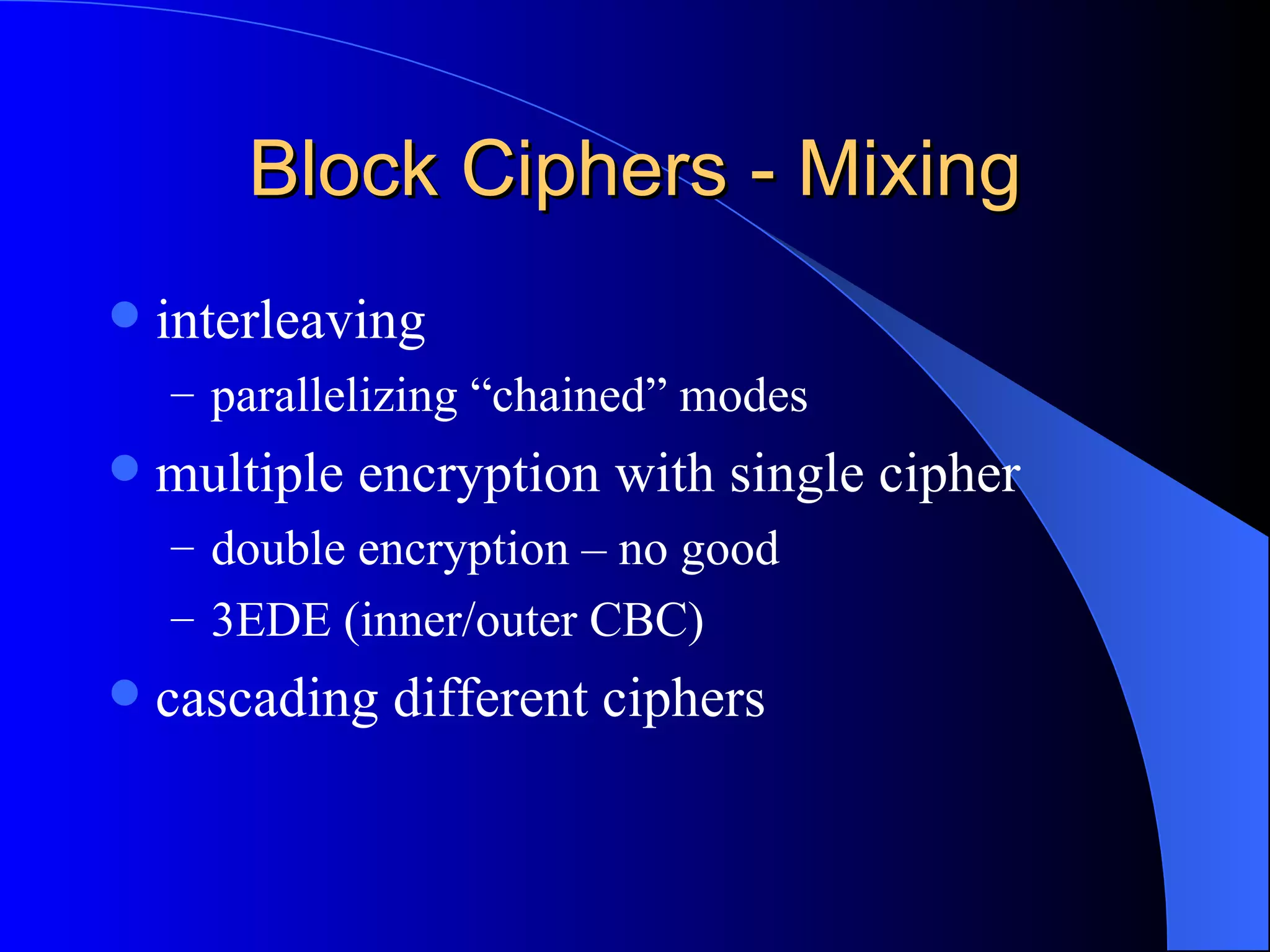
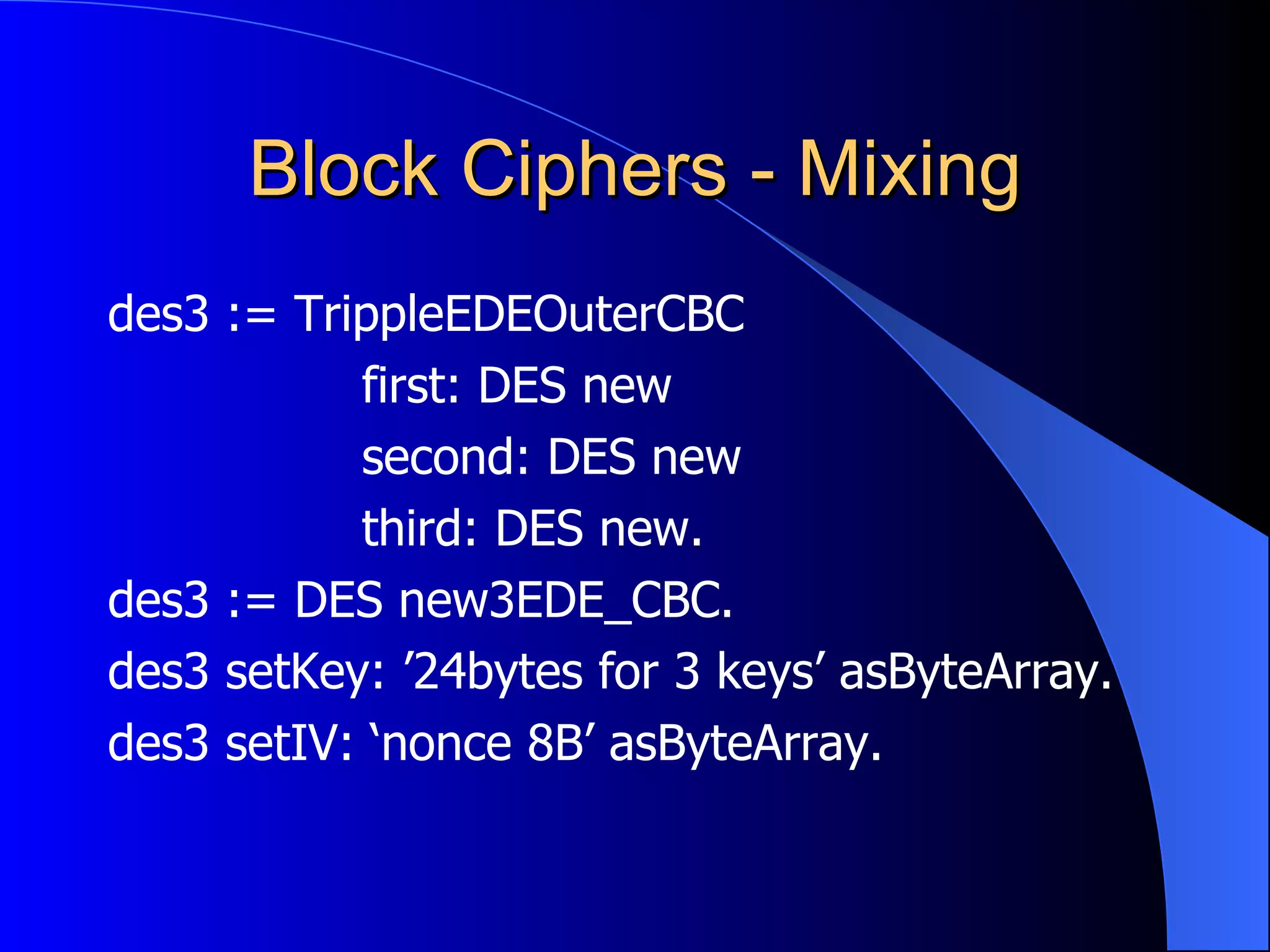
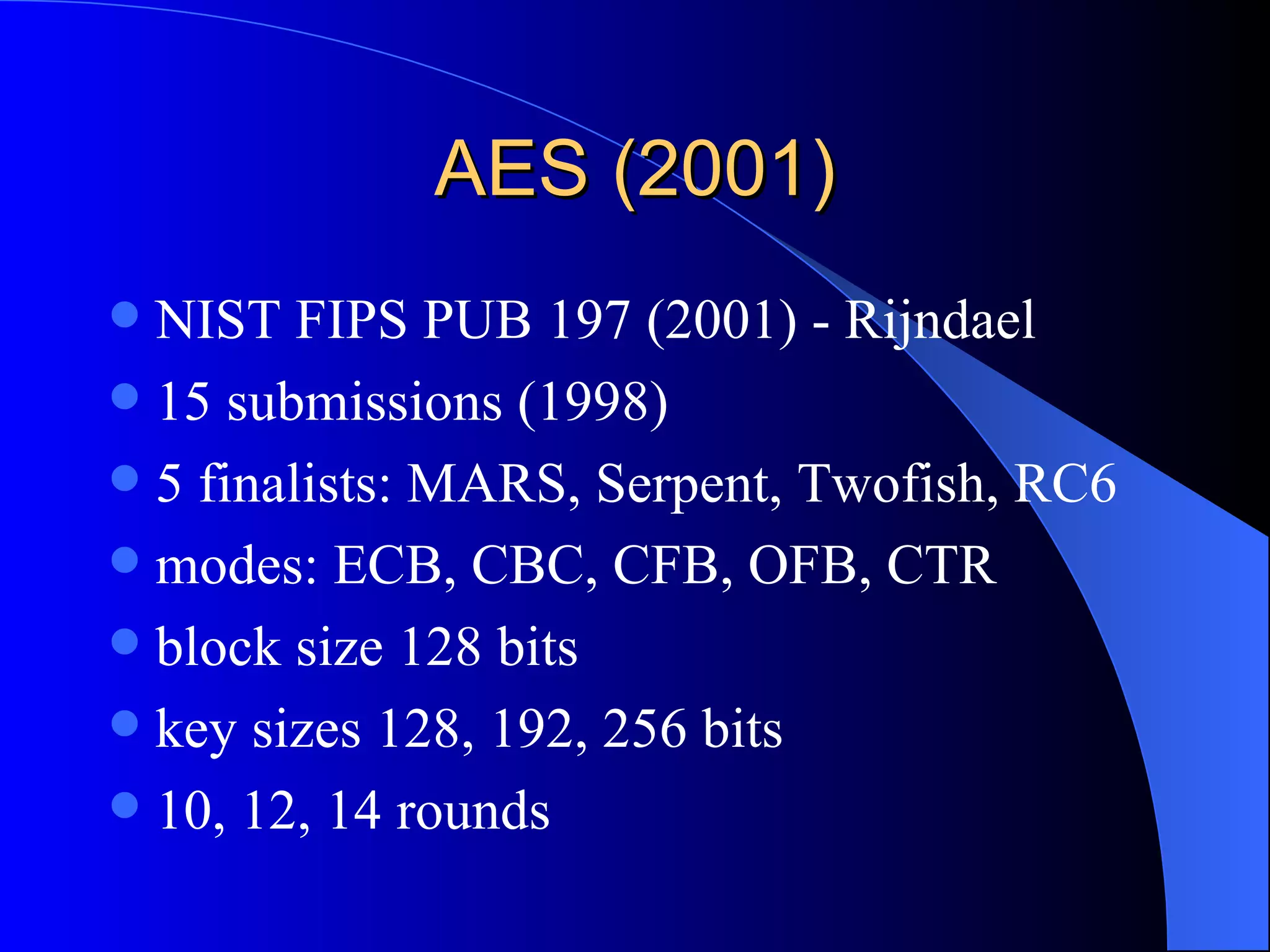
The document discusses various cryptographic techniques including encryption, message authentication codes, and digital signatures. It describes symmetric key ciphers like stream ciphers (RC4) and block ciphers (DES, AES) as well as asymmetric key ciphers. Specific block cipher modes like CBC, CFB, OFB, and CTR are also summarized. Popular algorithms like DES, AES, Blowfish, and RC4 are briefly explained.