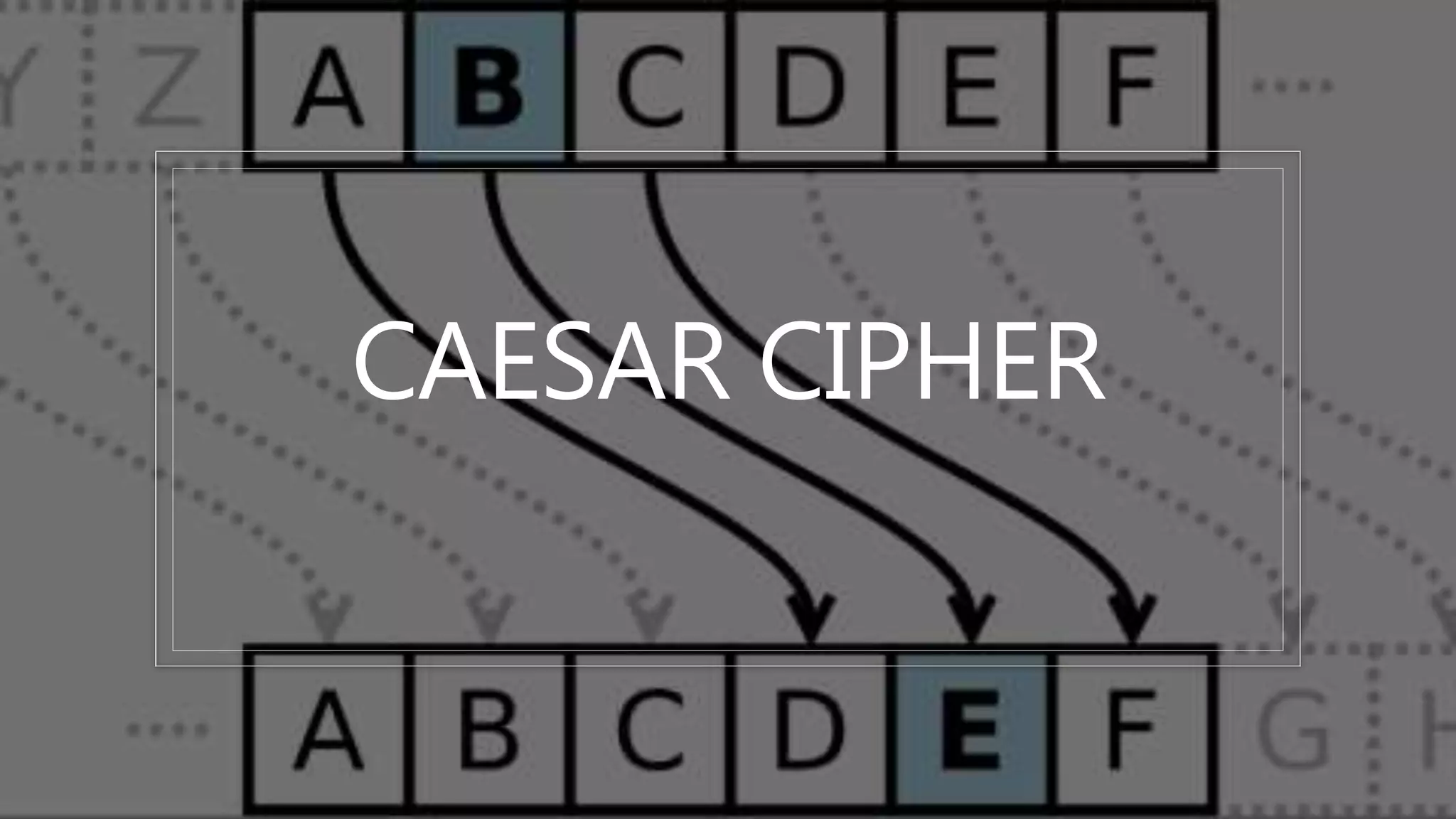
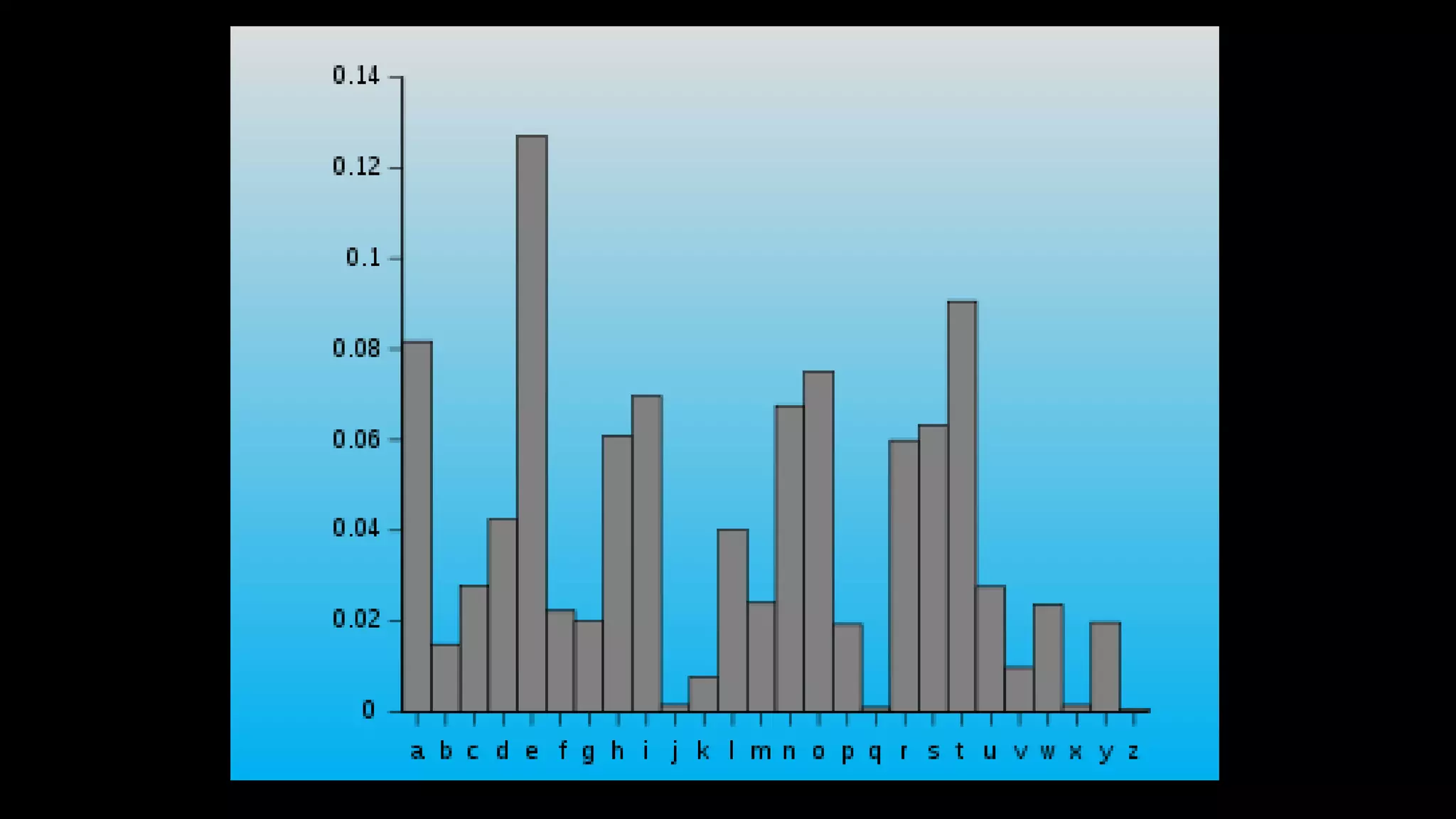
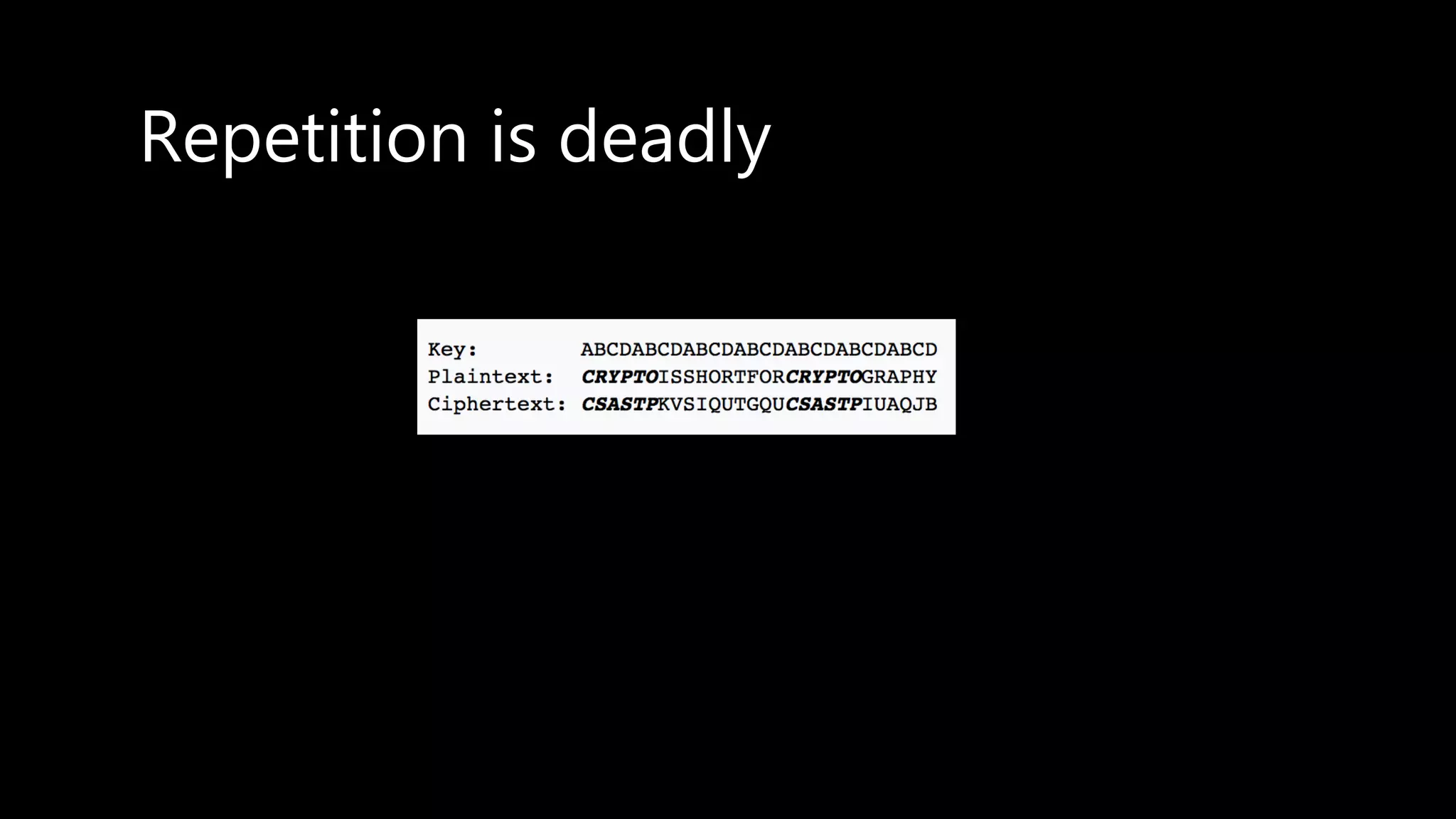
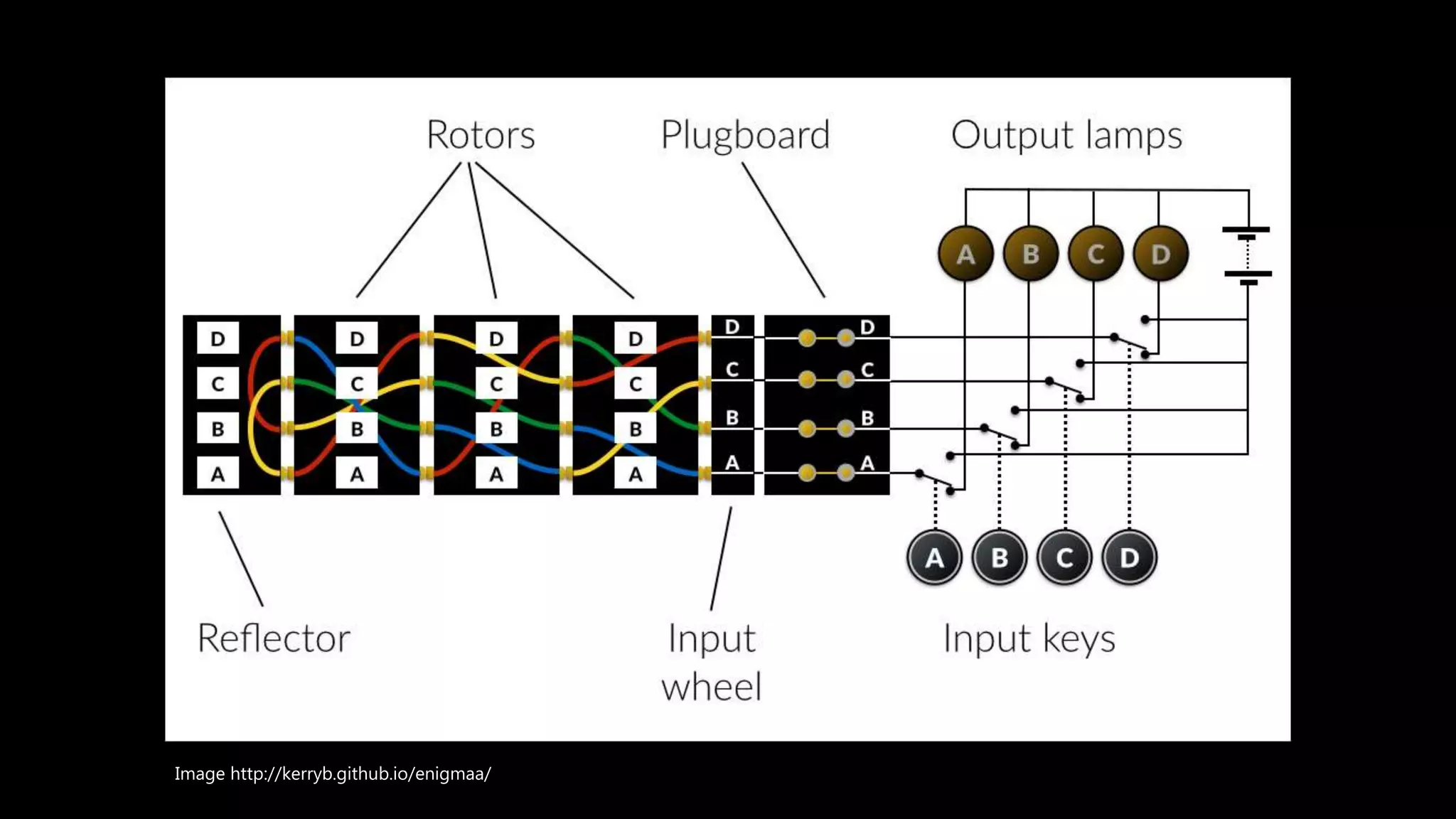
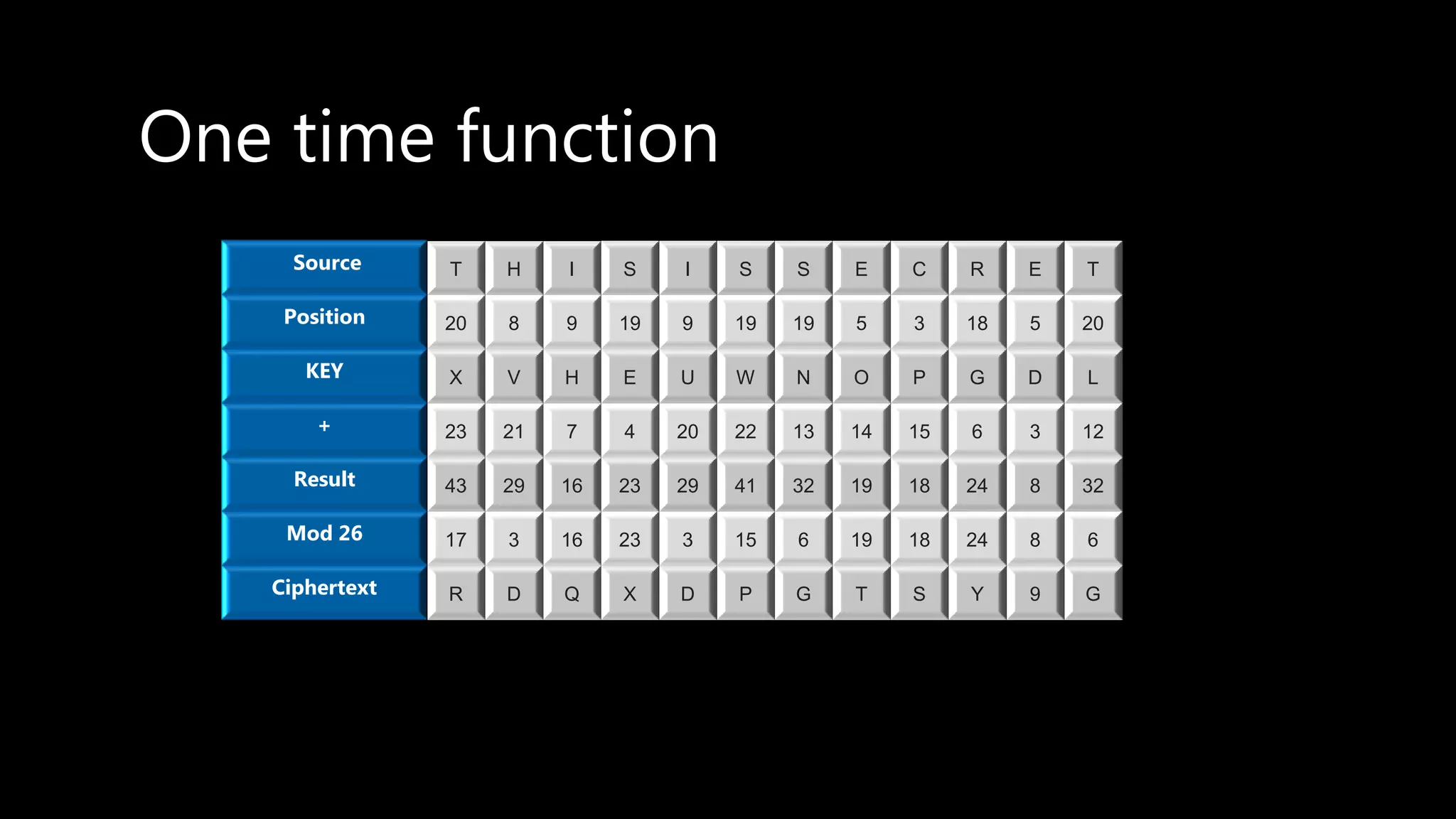
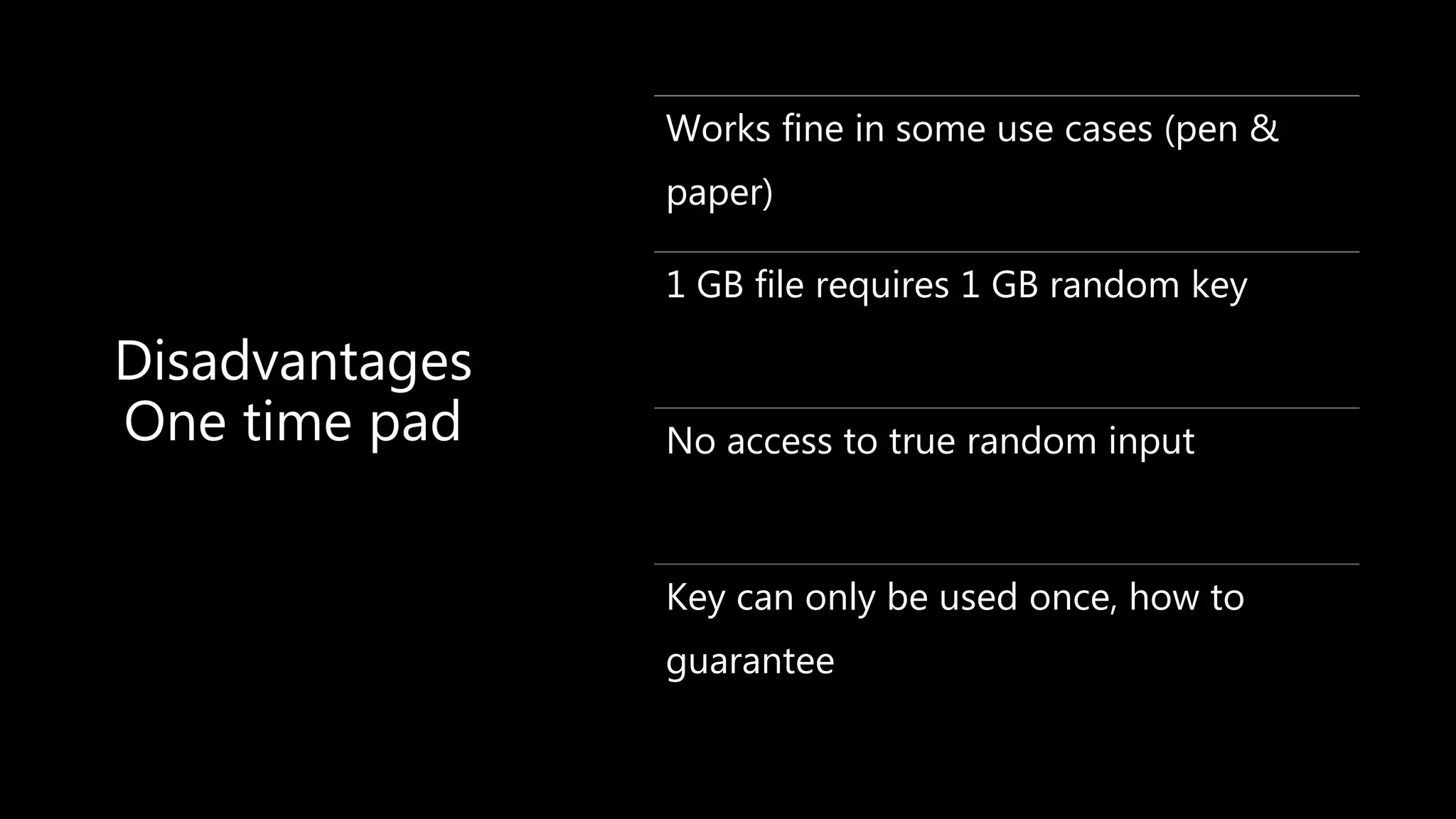
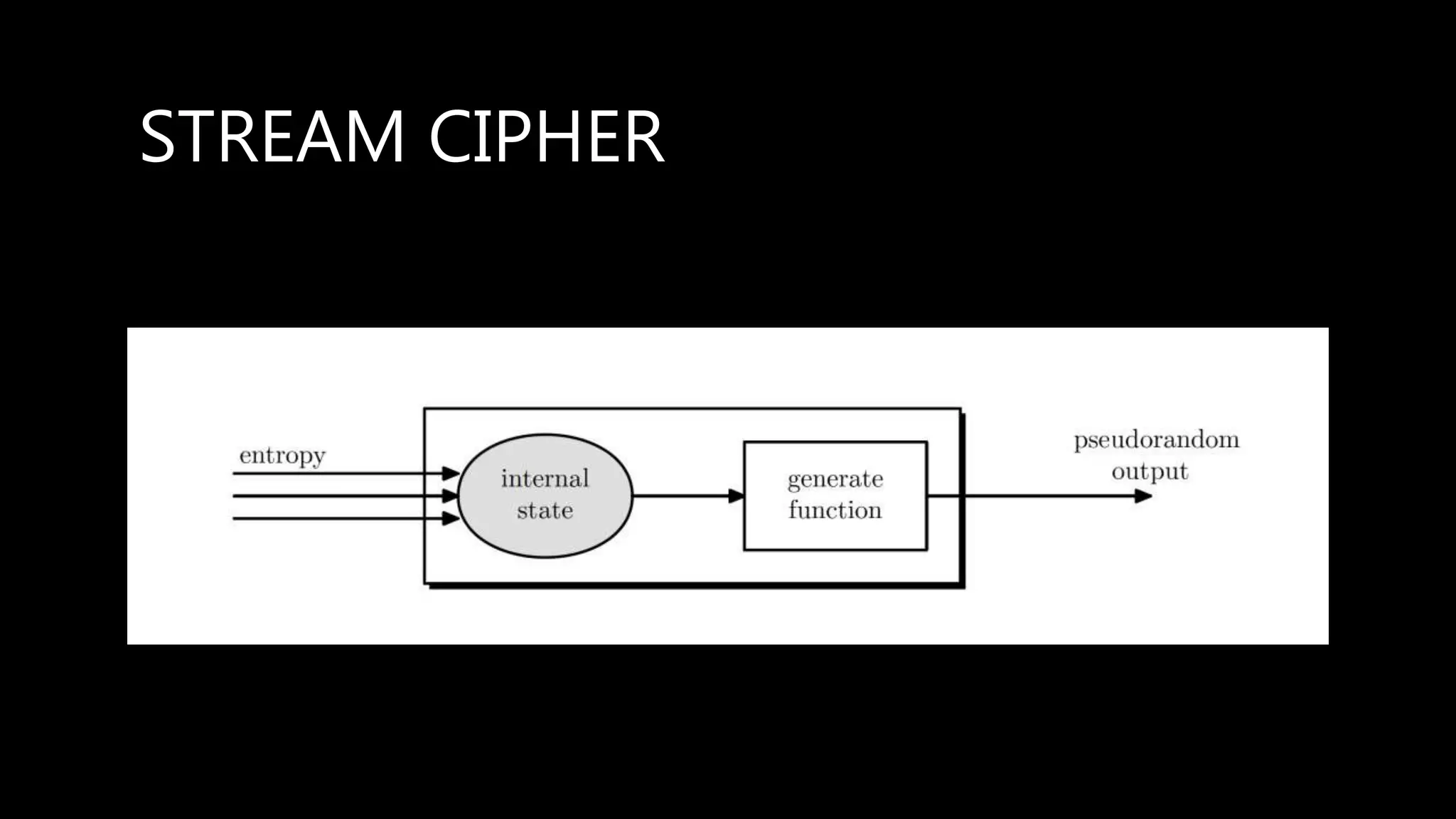
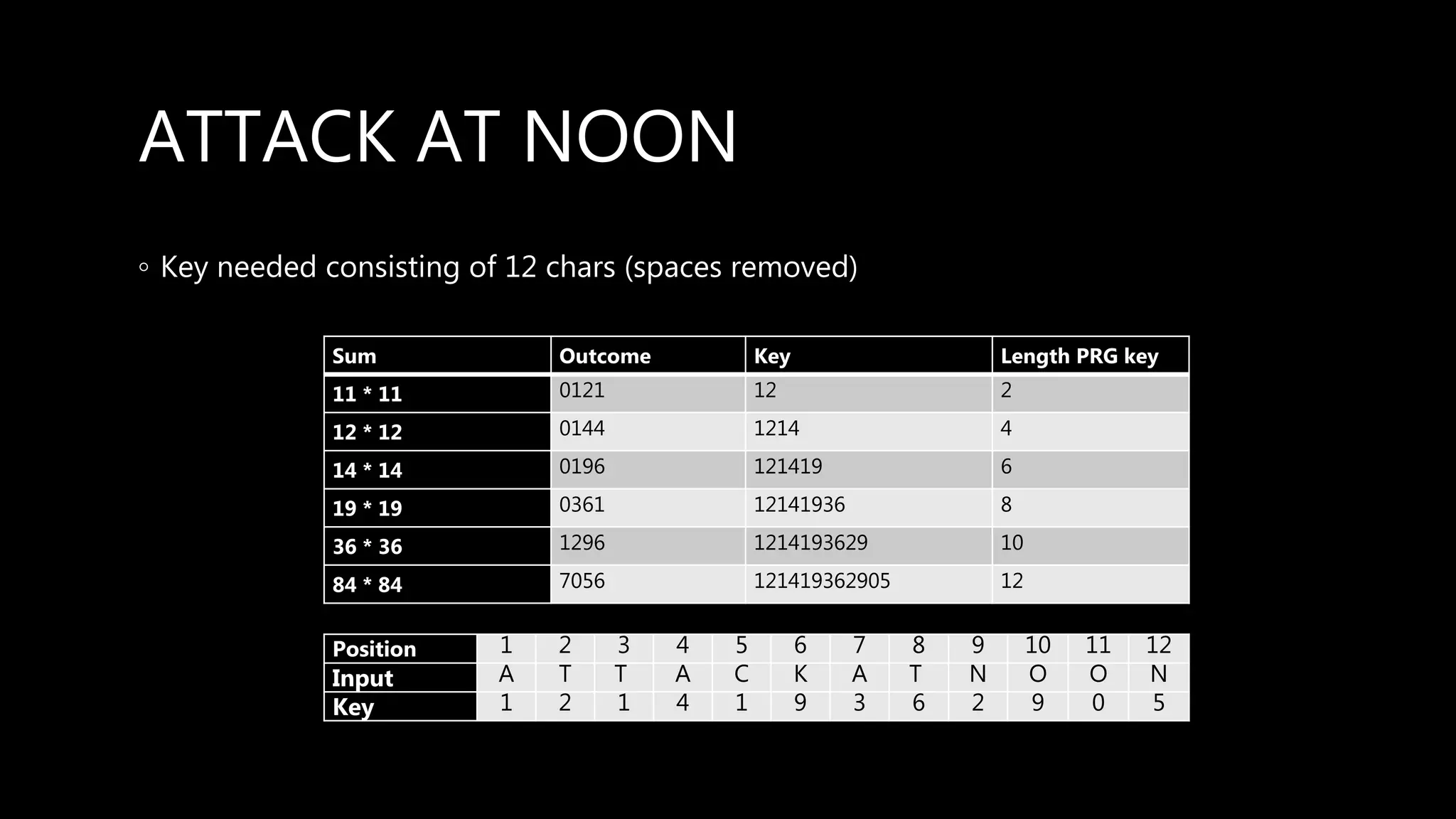
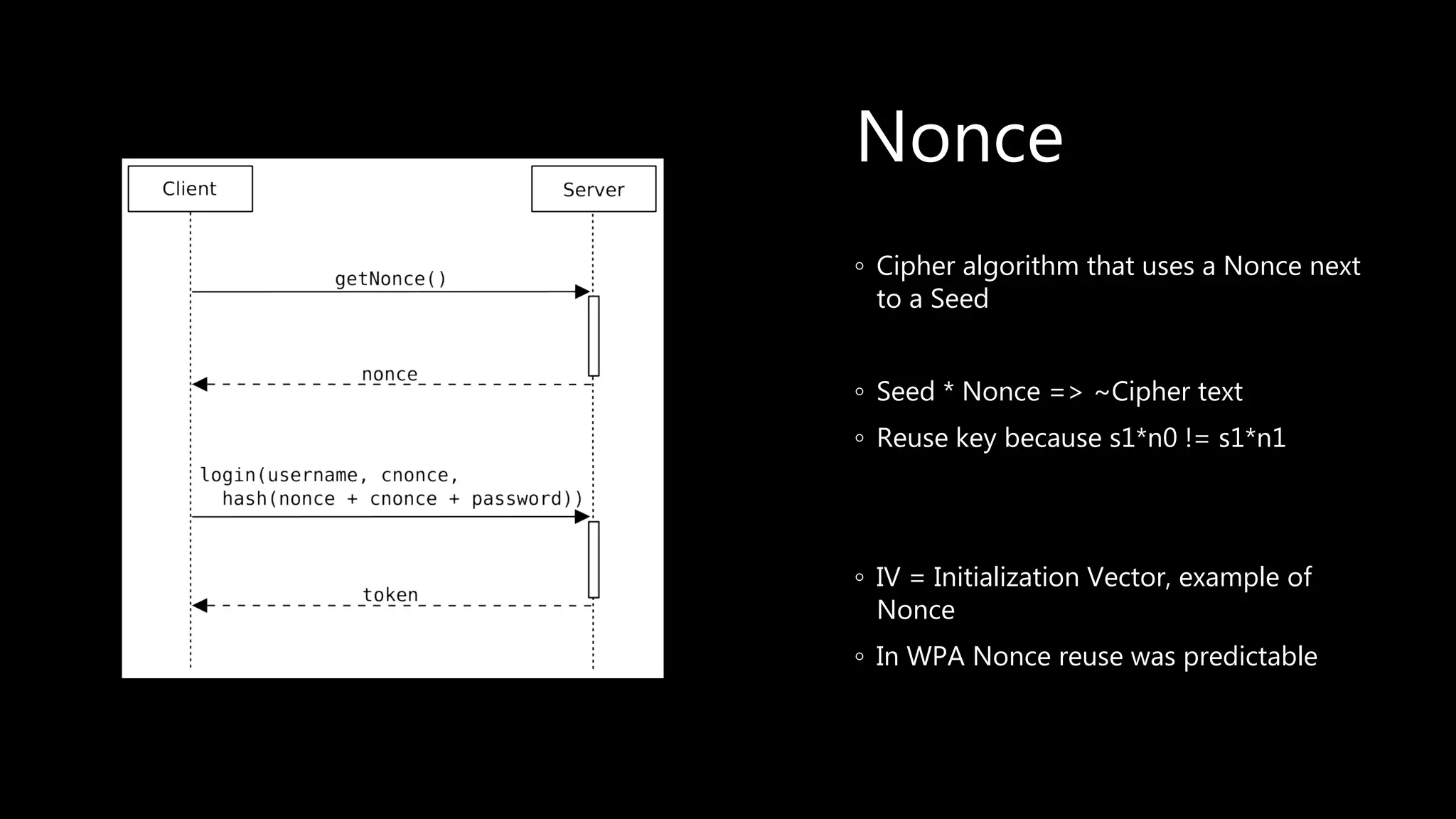
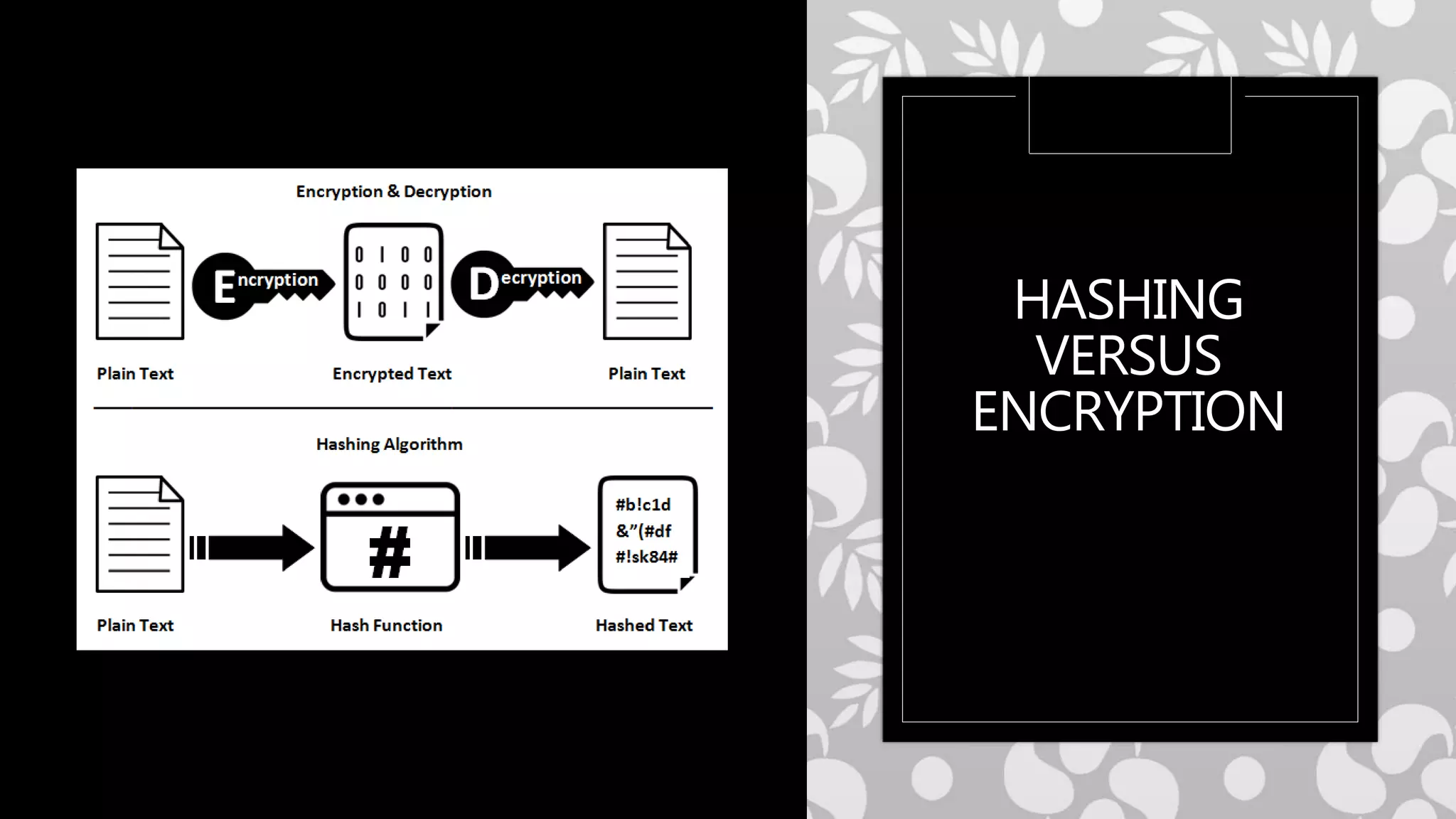
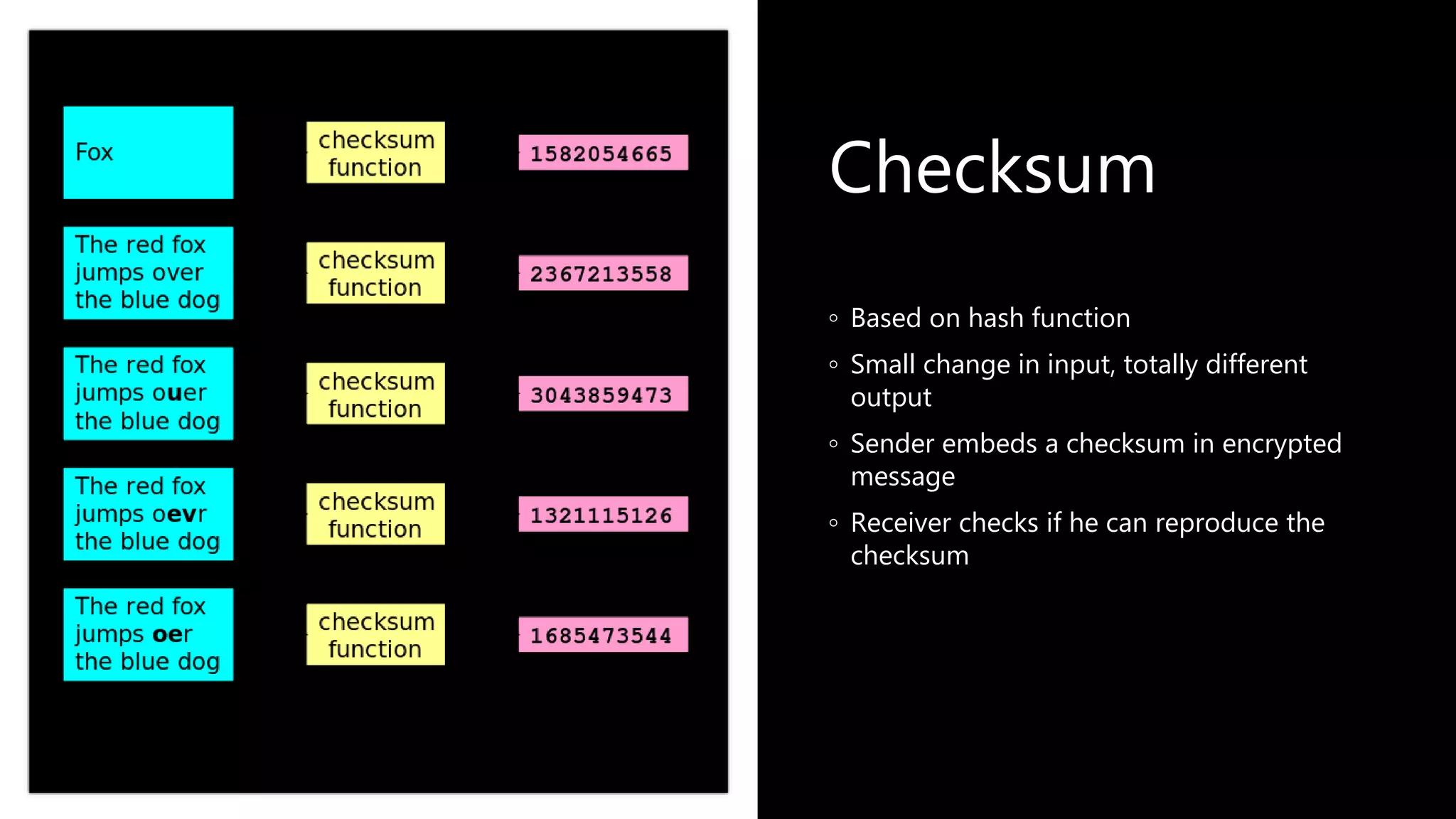
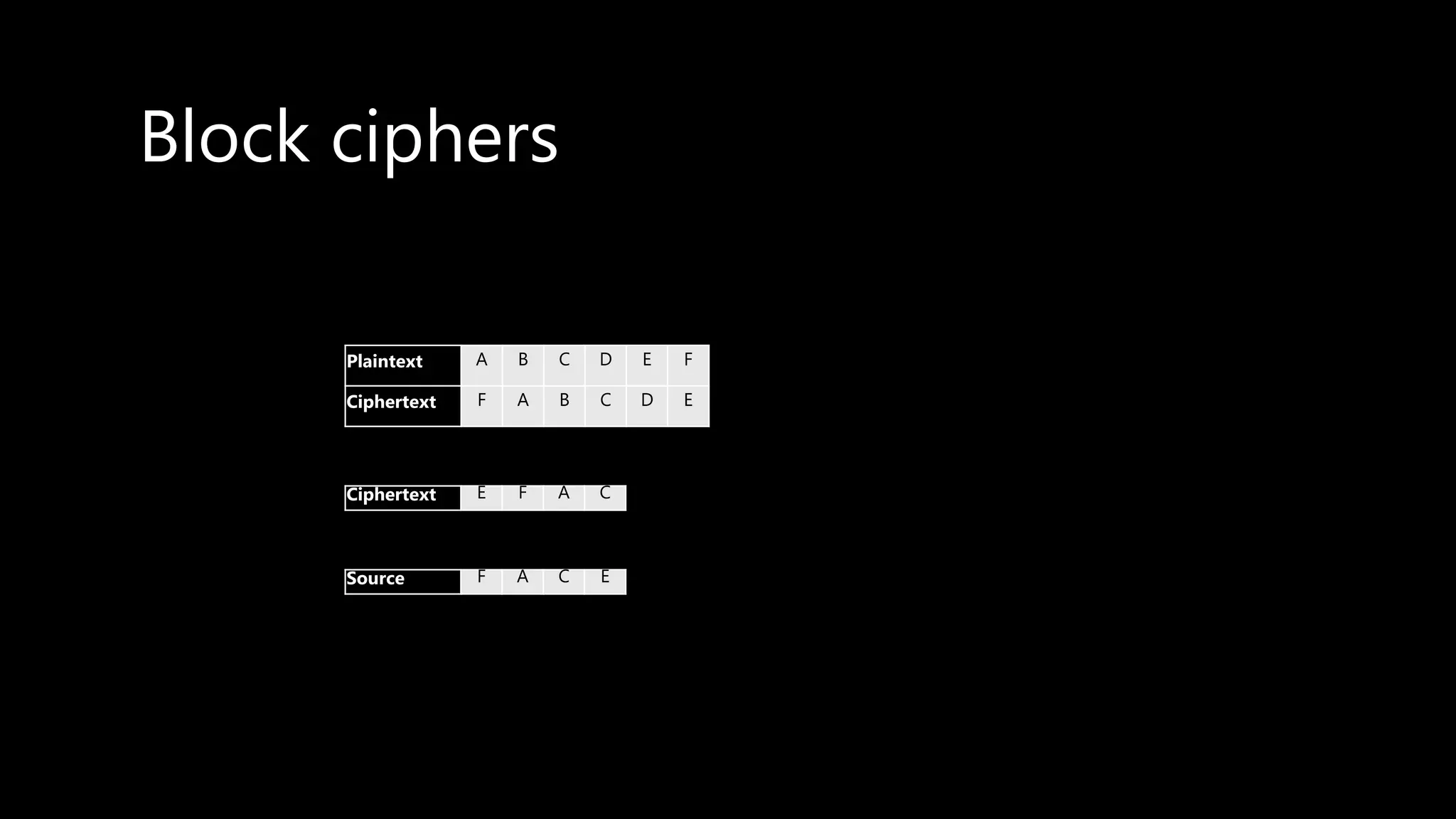
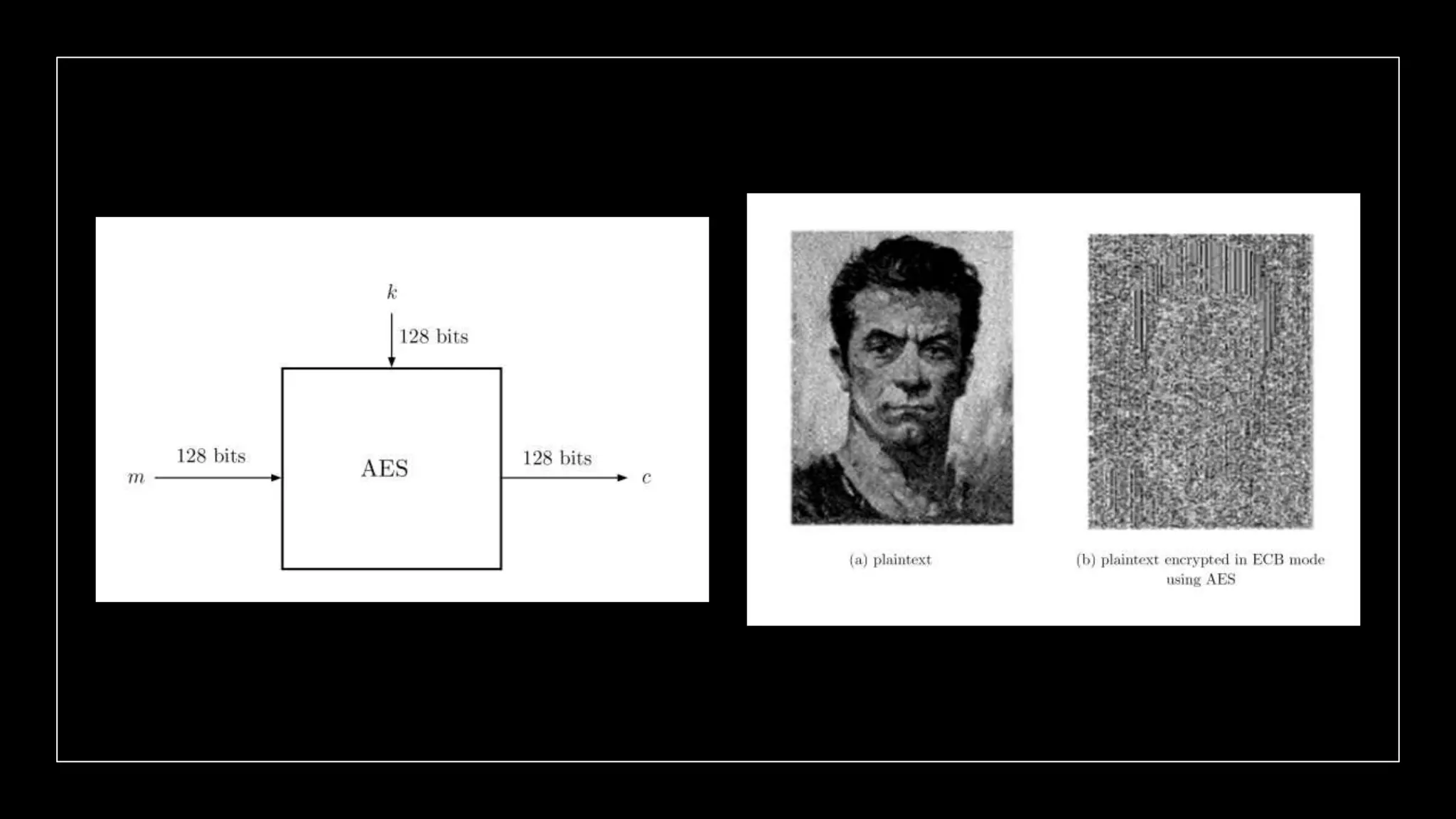
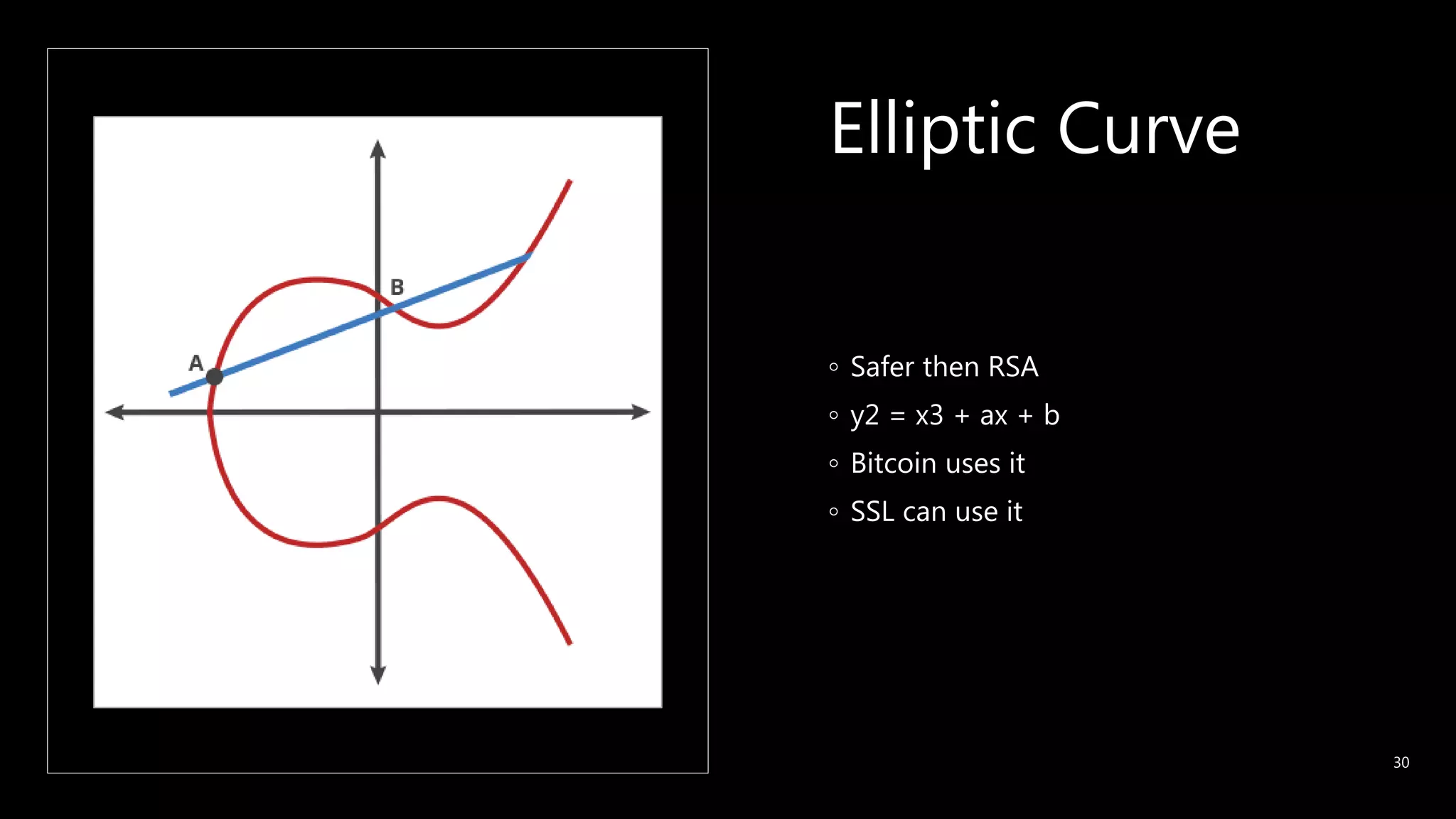
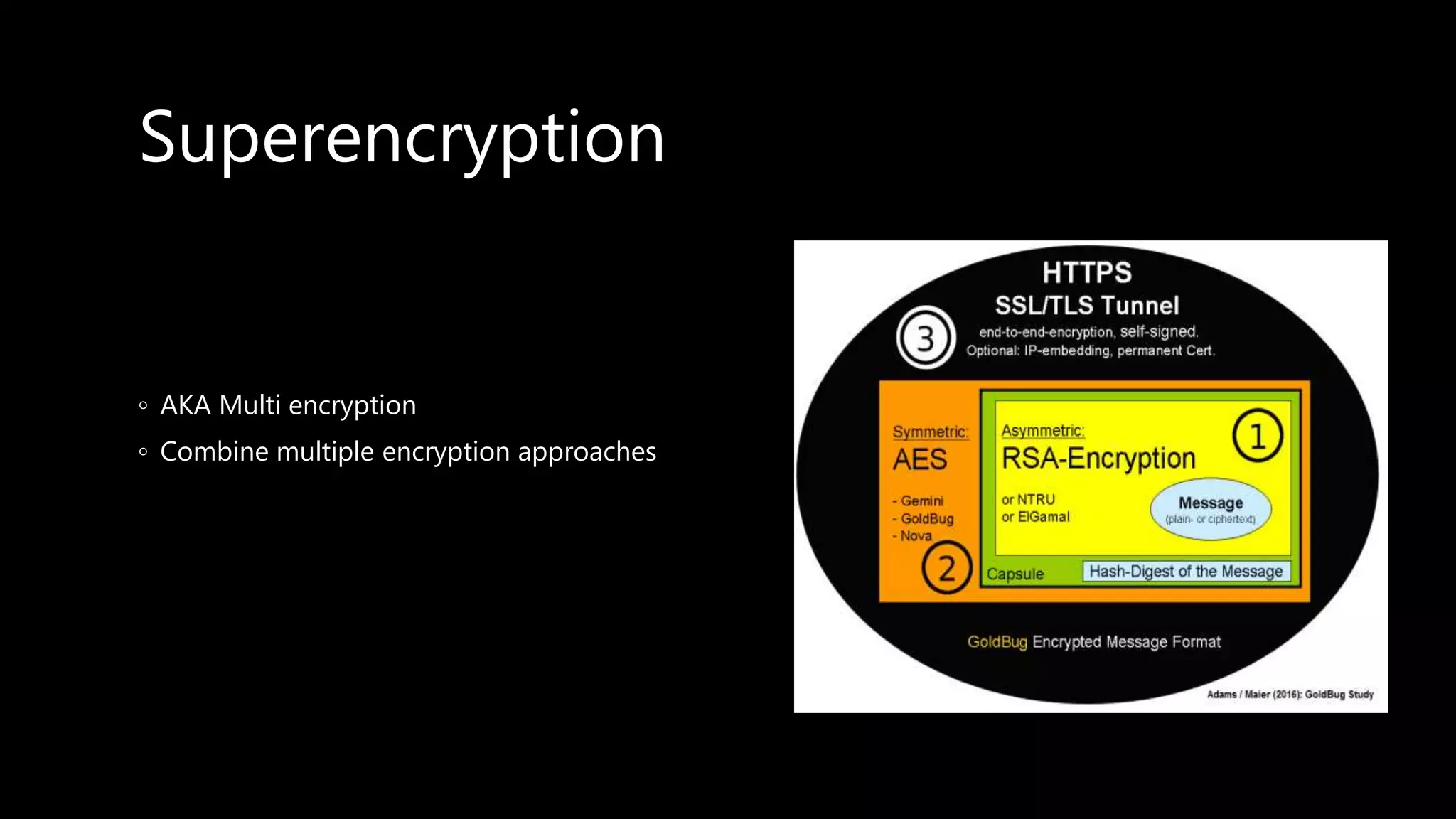
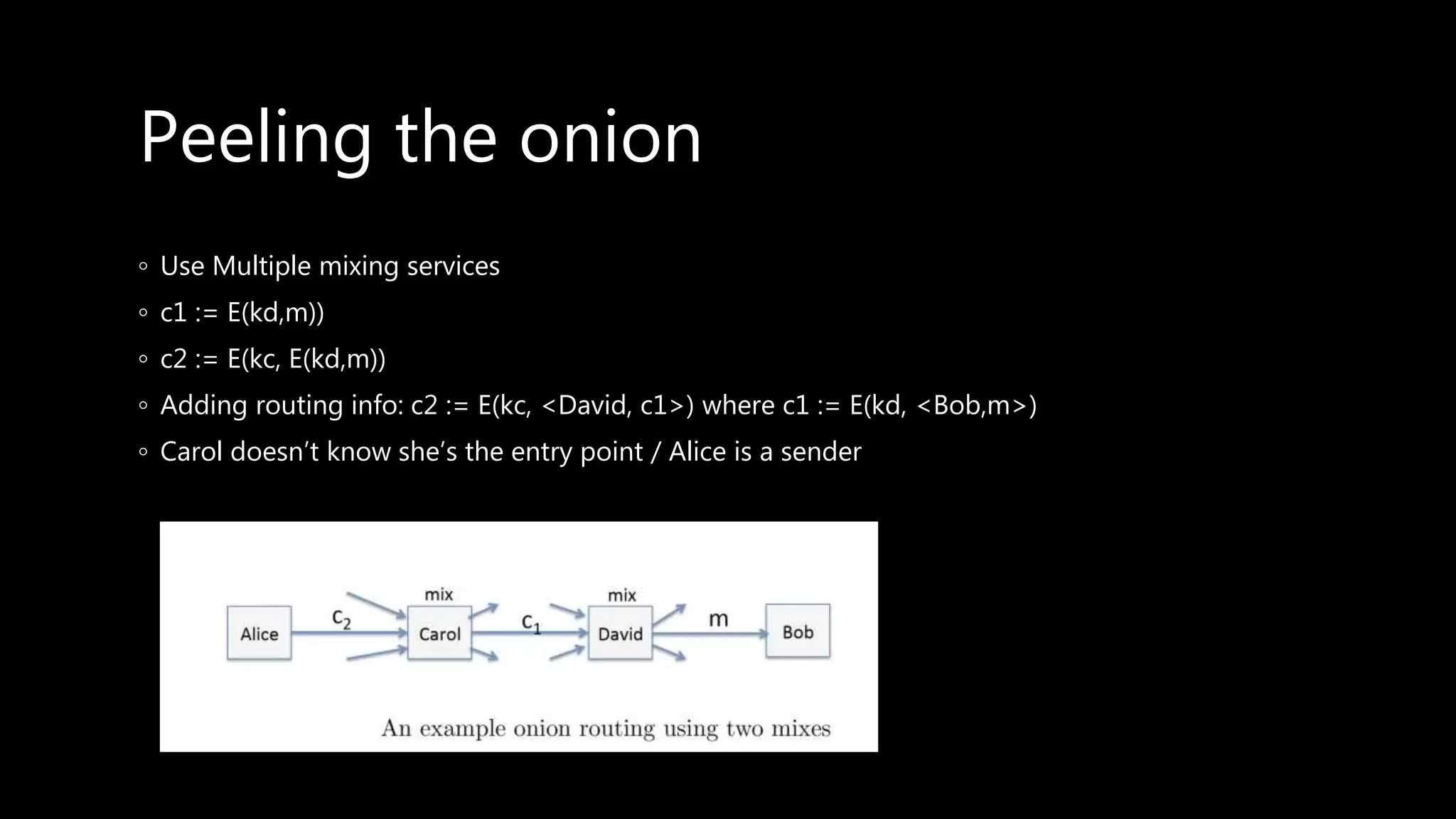
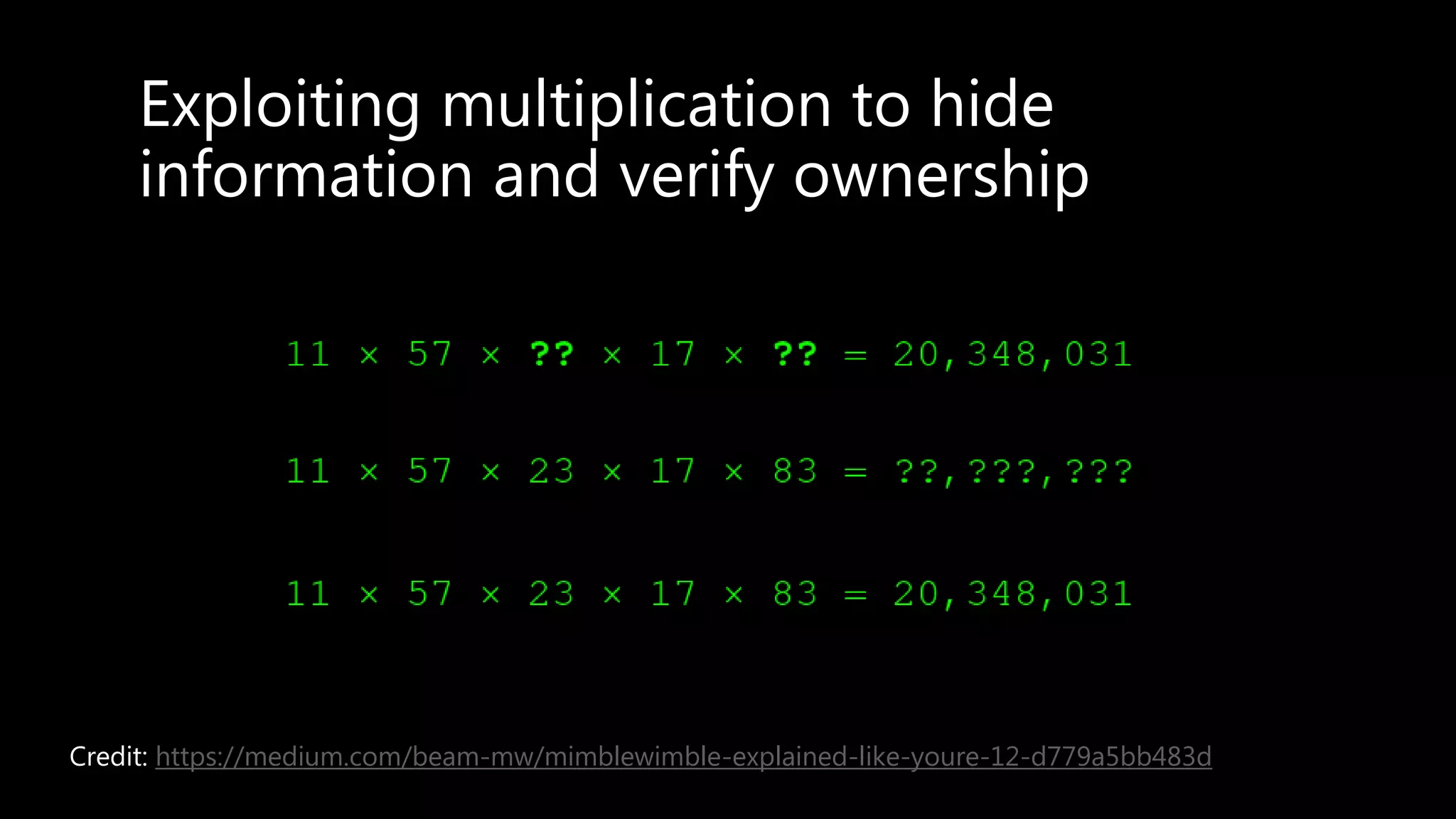
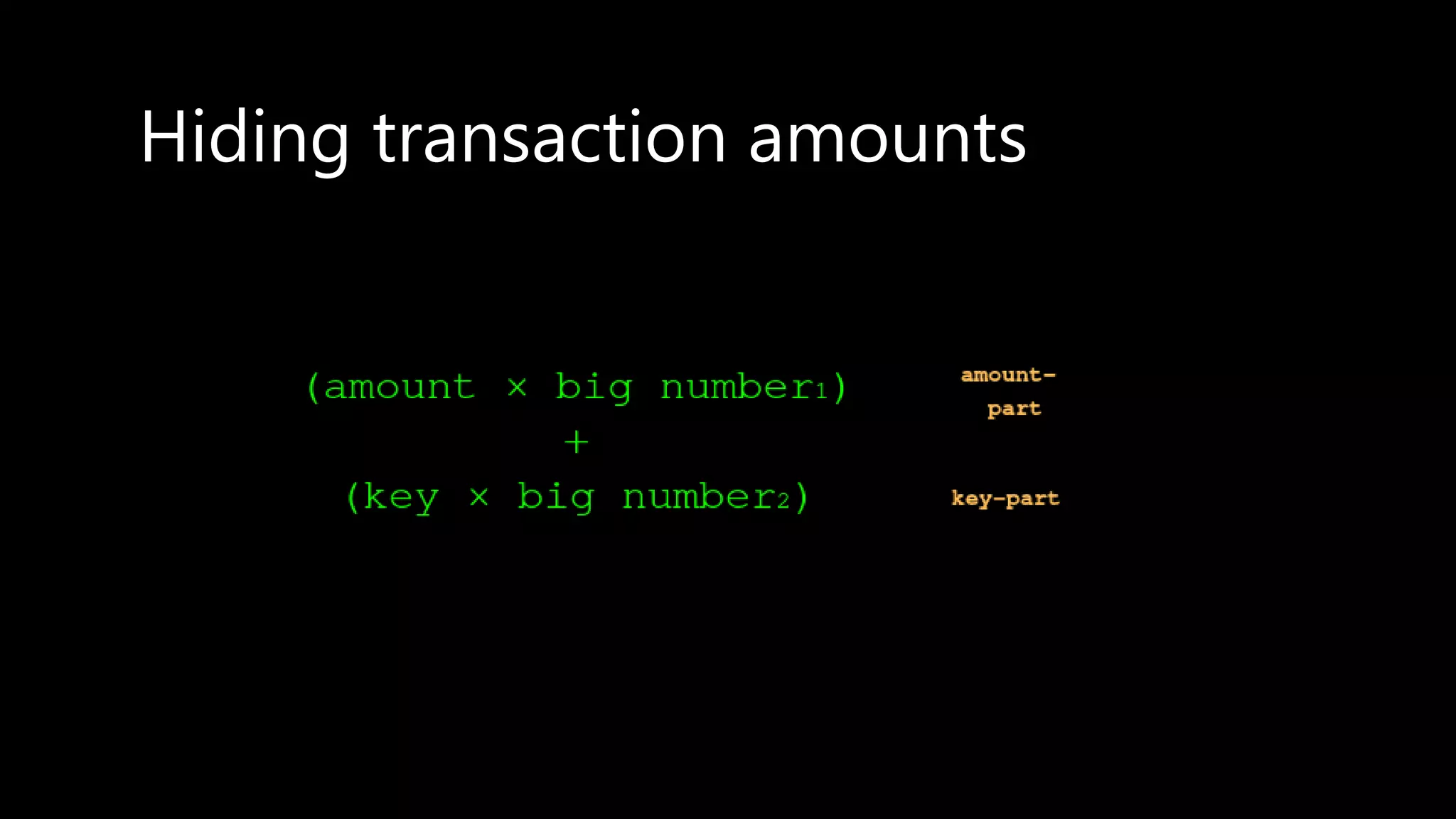
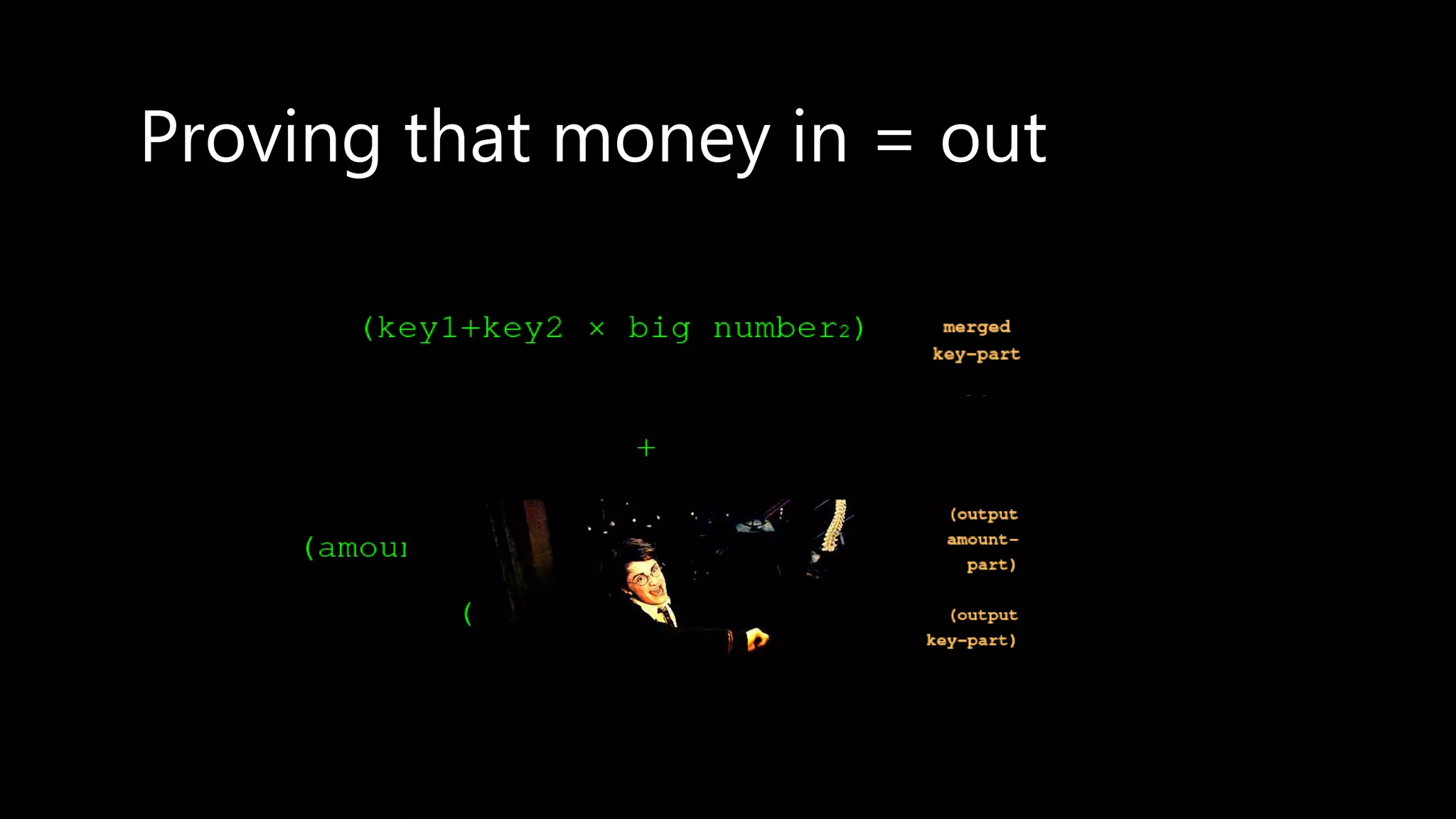
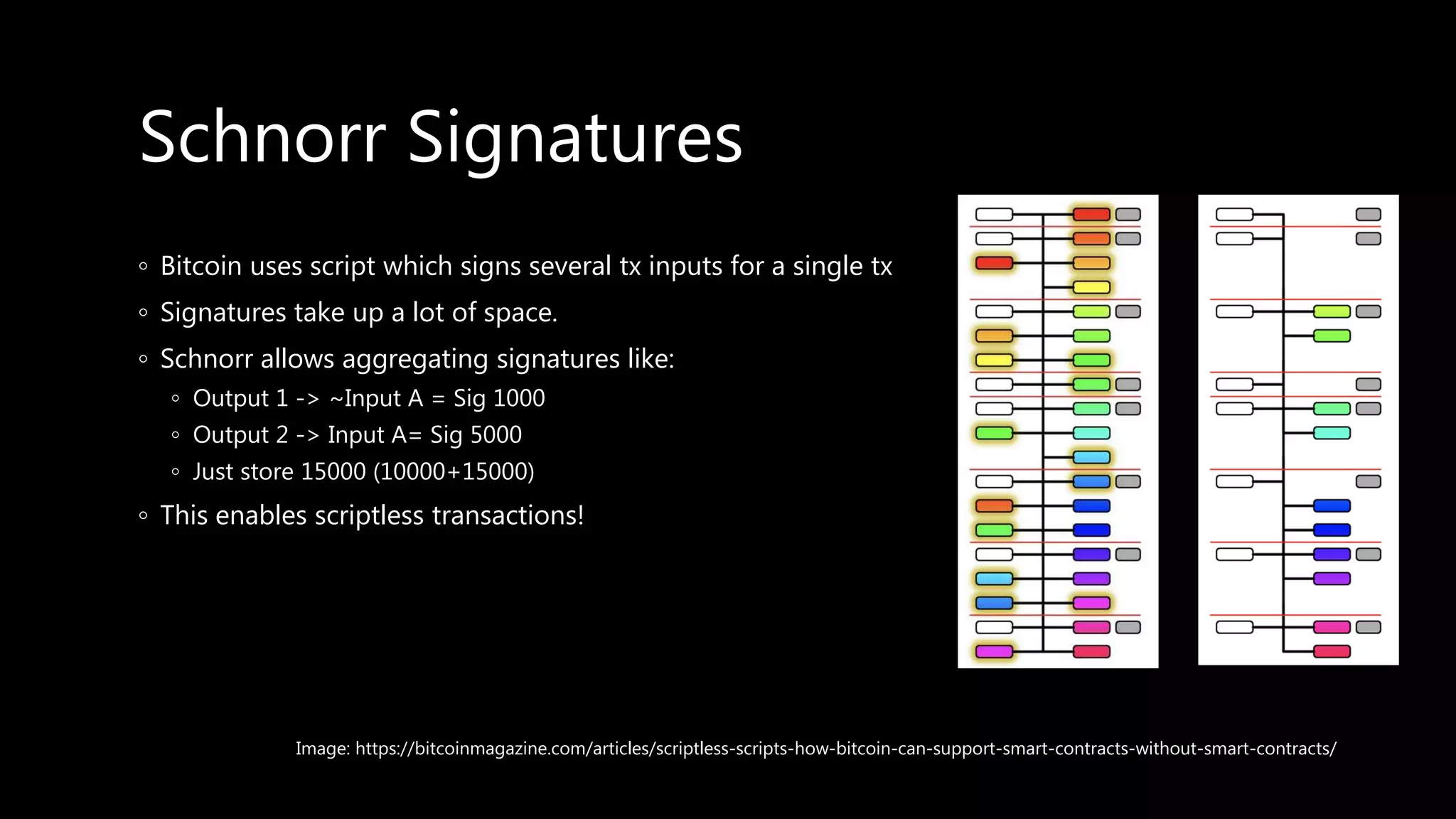
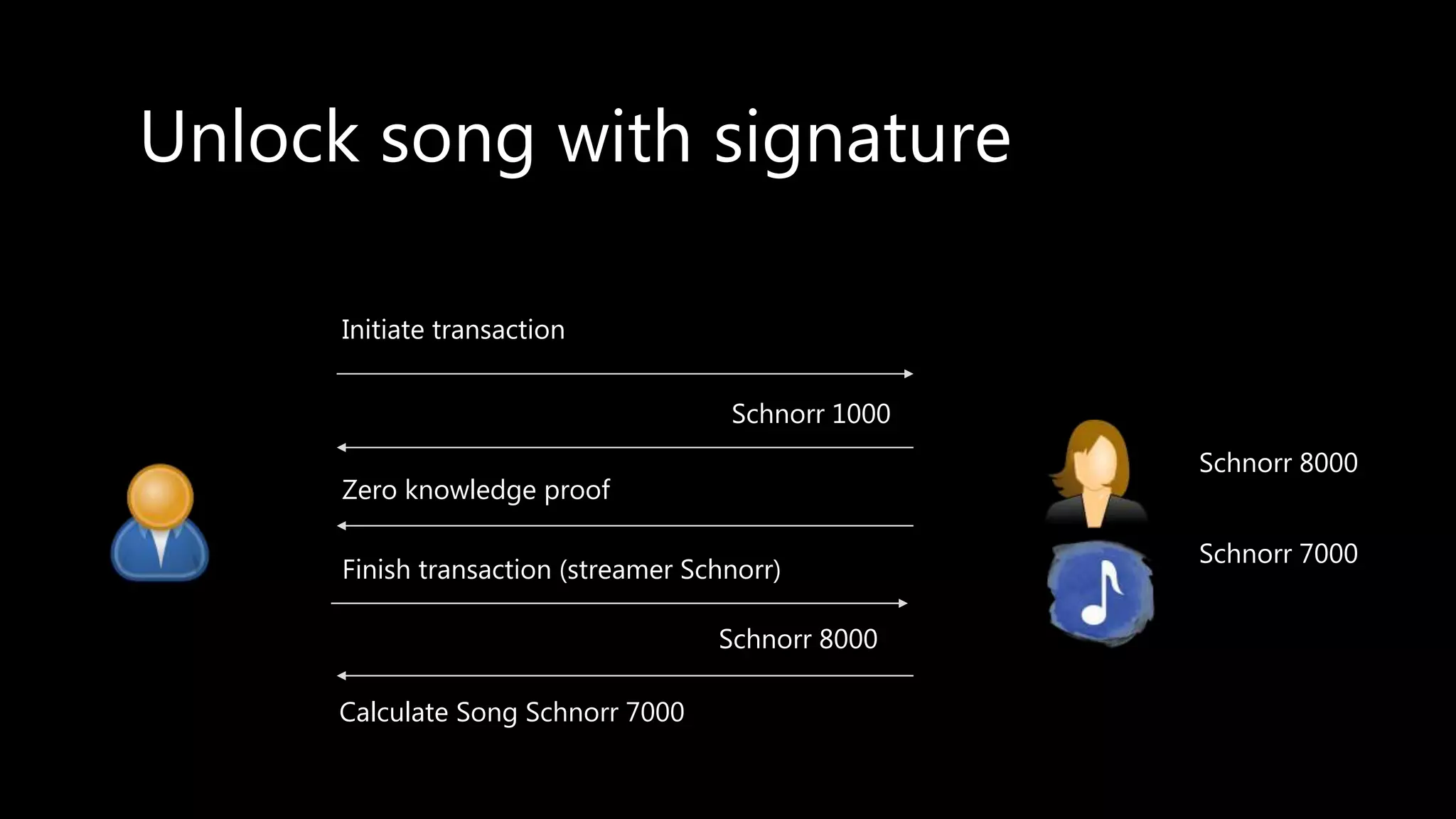
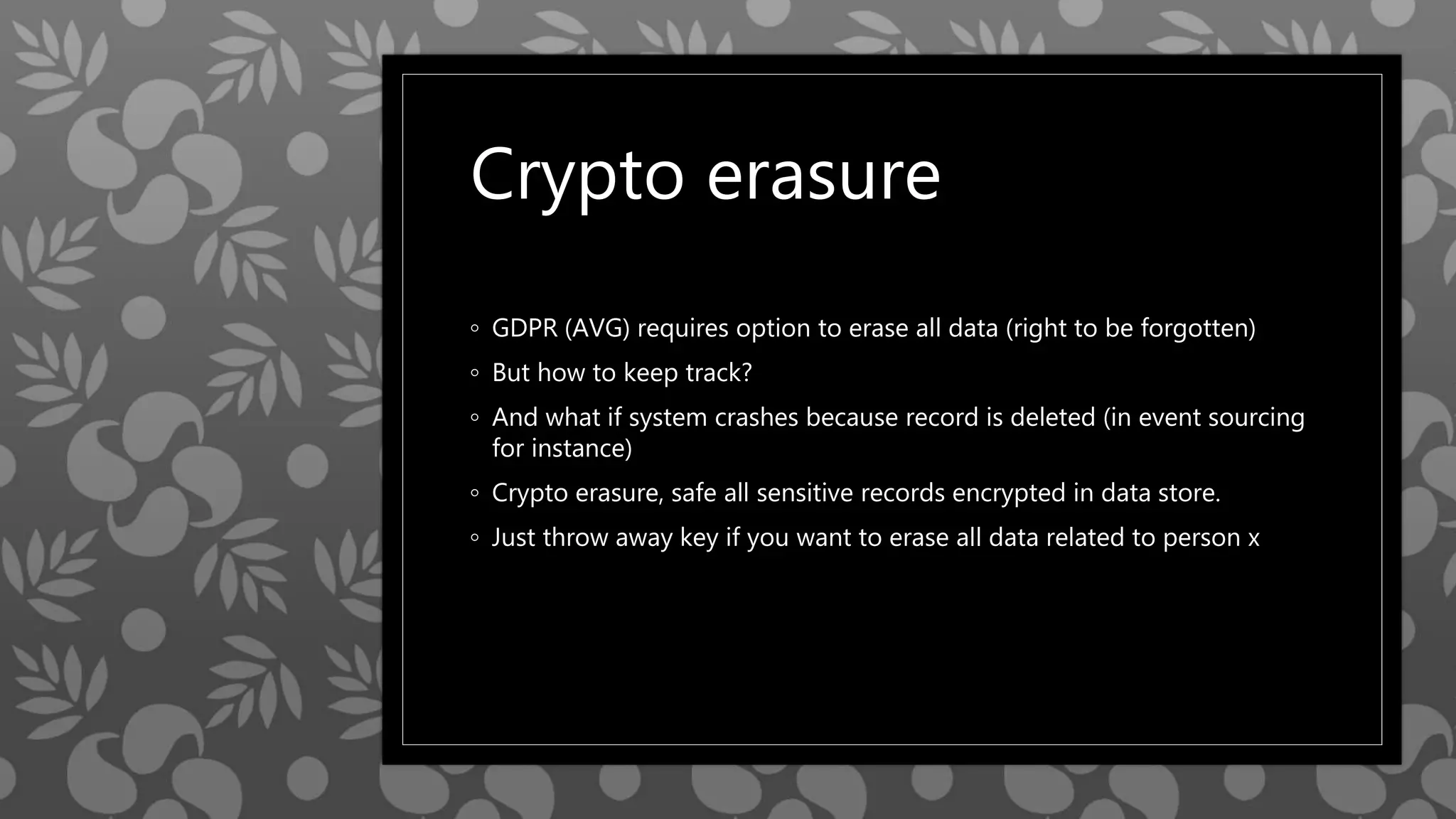
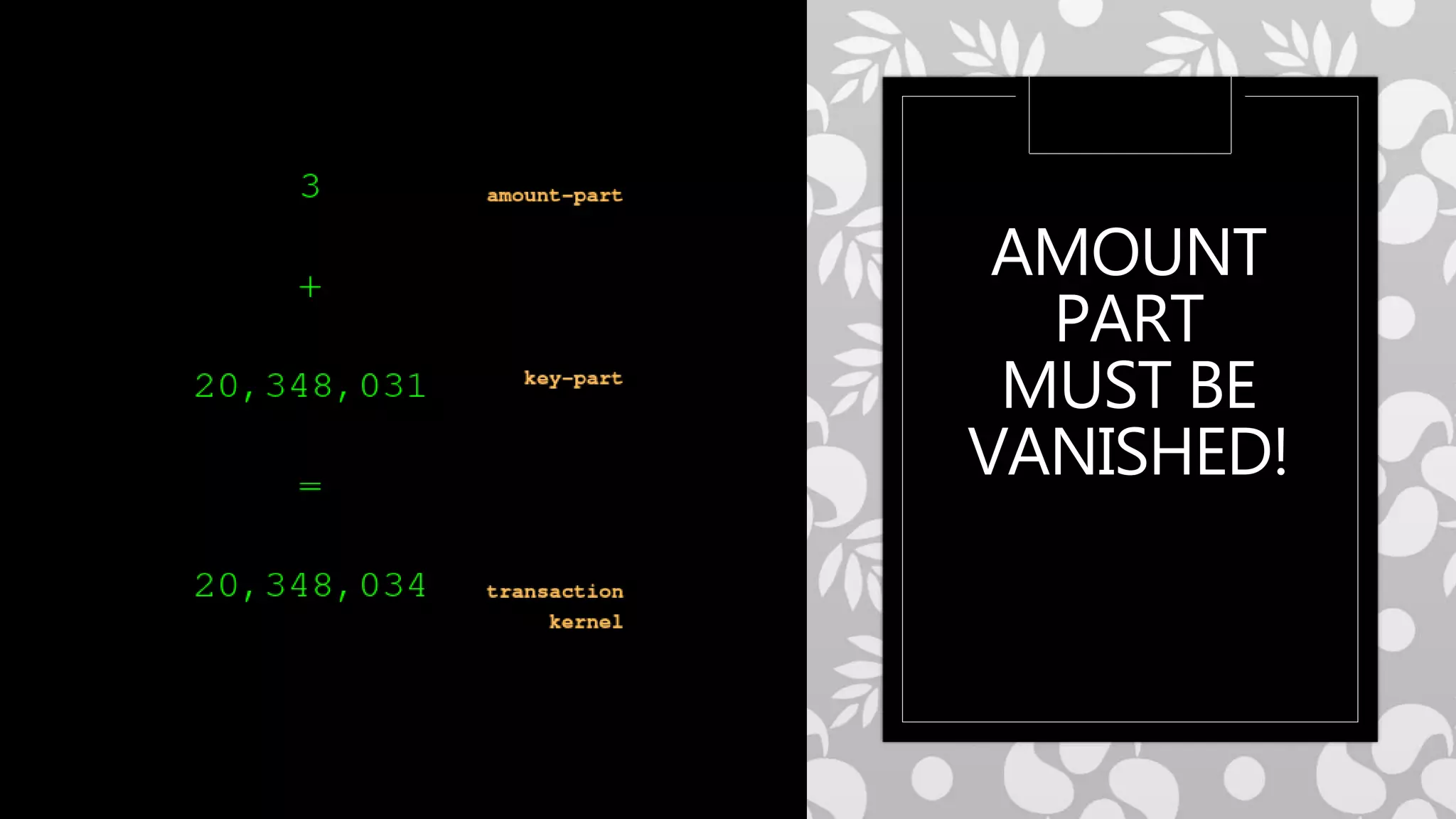
This document provides an overview of cryptography concepts including various ciphers like the Caesar cipher, Vigenère cipher, Playfair cipher, and the one-time pad. It discusses stream ciphers using techniques like the middle squares method. Asymmetric encryption techniques like elliptic curve cryptography are covered as well as the impact of quantum computing. Additional topics include hashing, block ciphers, mixing services/onion routing, zero-knowledge proofs, and scriptless scripts. Recommended further reading on applied cryptography is also provided.