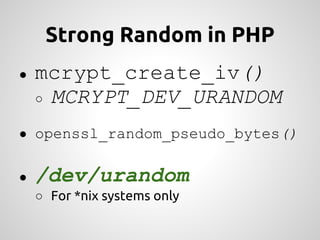
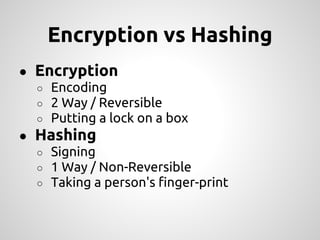
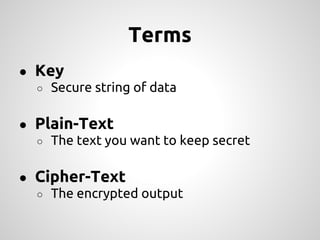
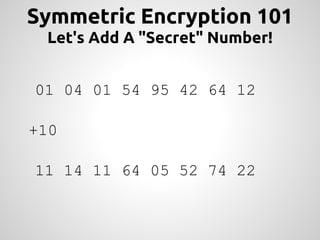
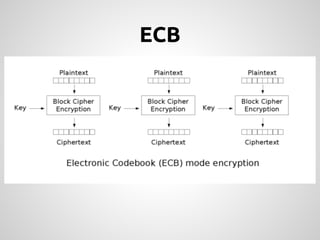
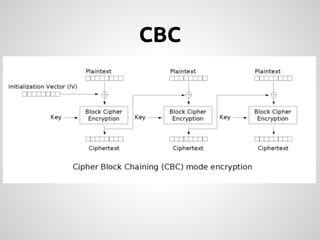
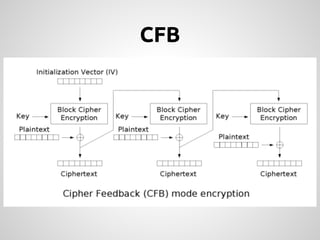
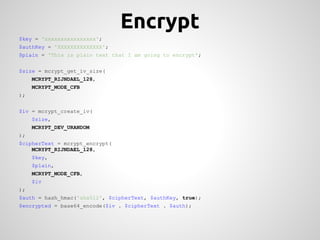
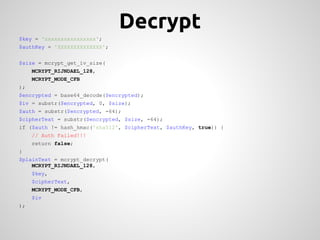
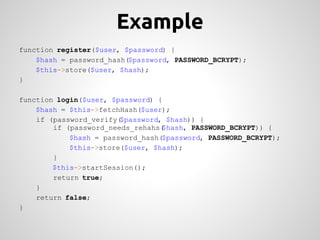
This document provides an overview of cryptography concepts for PHP developers. It discusses keeping data secure from viewing, tampering and forgery through encryption but notes cryptography is not a silver bullet and vulnerabilities still exist. The document covers random number generation, symmetric and asymmetric encryption, hashing, common ciphers and modes, and securely storing passwords through hashing rather than encryption. It strongly recommends using existing libraries rather than implementing cryptography directly due to the complexity and risk of bugs.