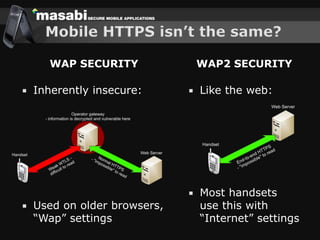
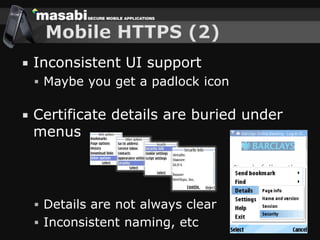
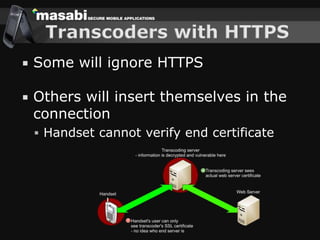
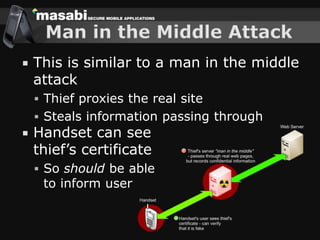
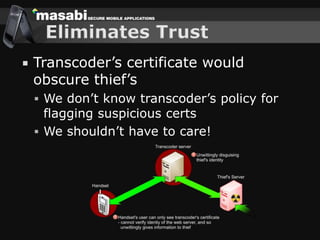
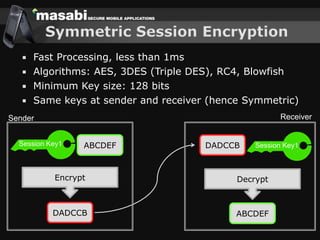
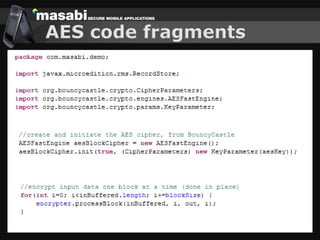
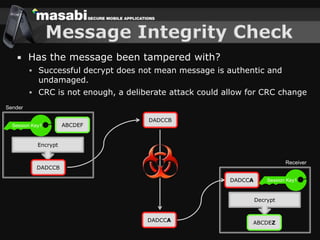
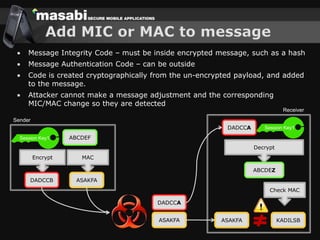
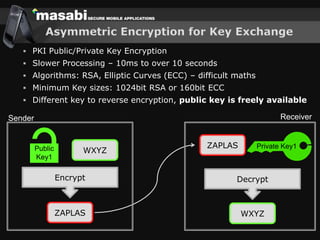
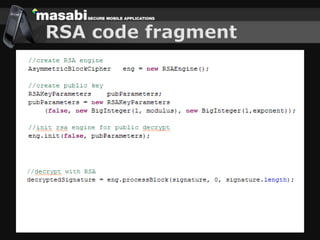
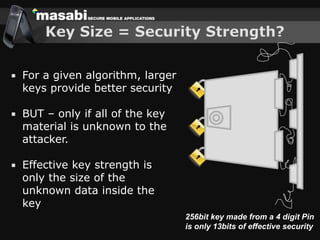
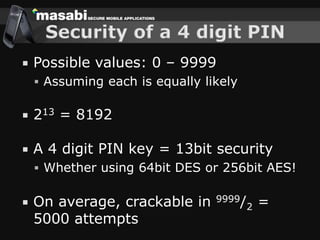
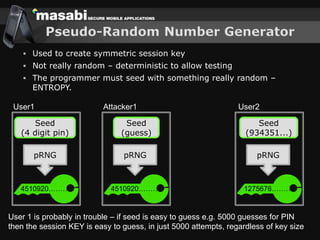
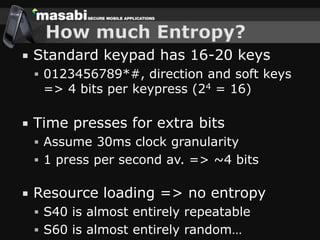
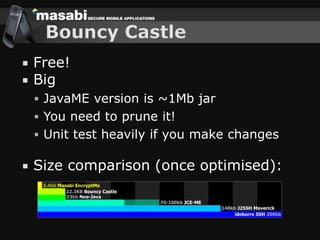
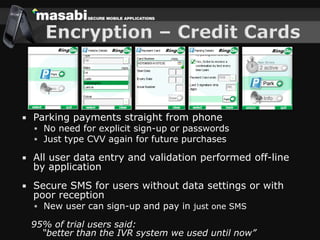
This document discusses the challenges of building secure mobile applications. It covers why security is important for mobile, how to secure applications in an insecure mobile environment, and case studies of mobile security implementations. Some key points discussed include using HTTPS for end-to-end security, securing the key exchange process, ensuring strong entropy for keys, implementing message integrity checks, and supporting a wide range of mobile devices and networks.