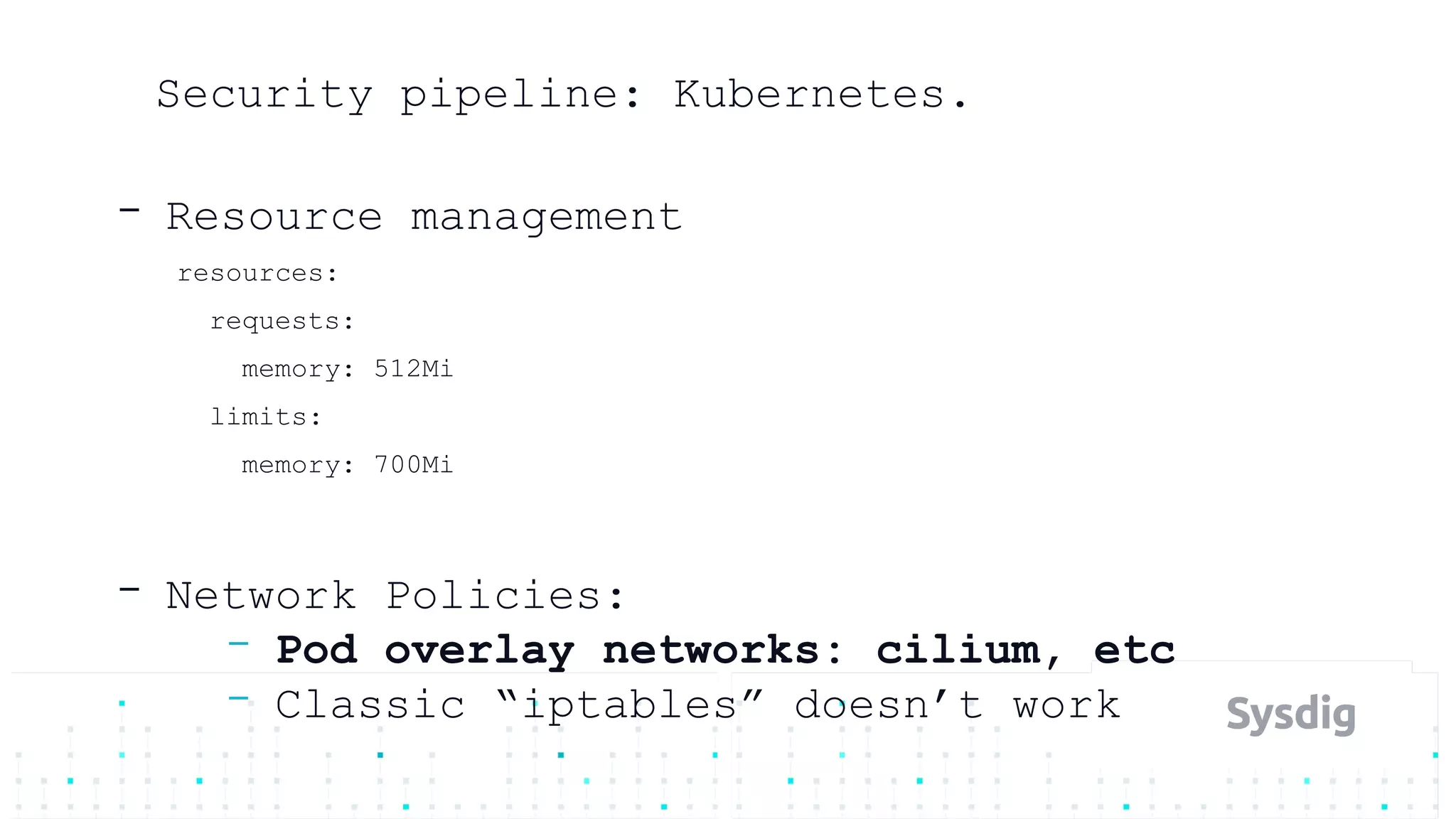
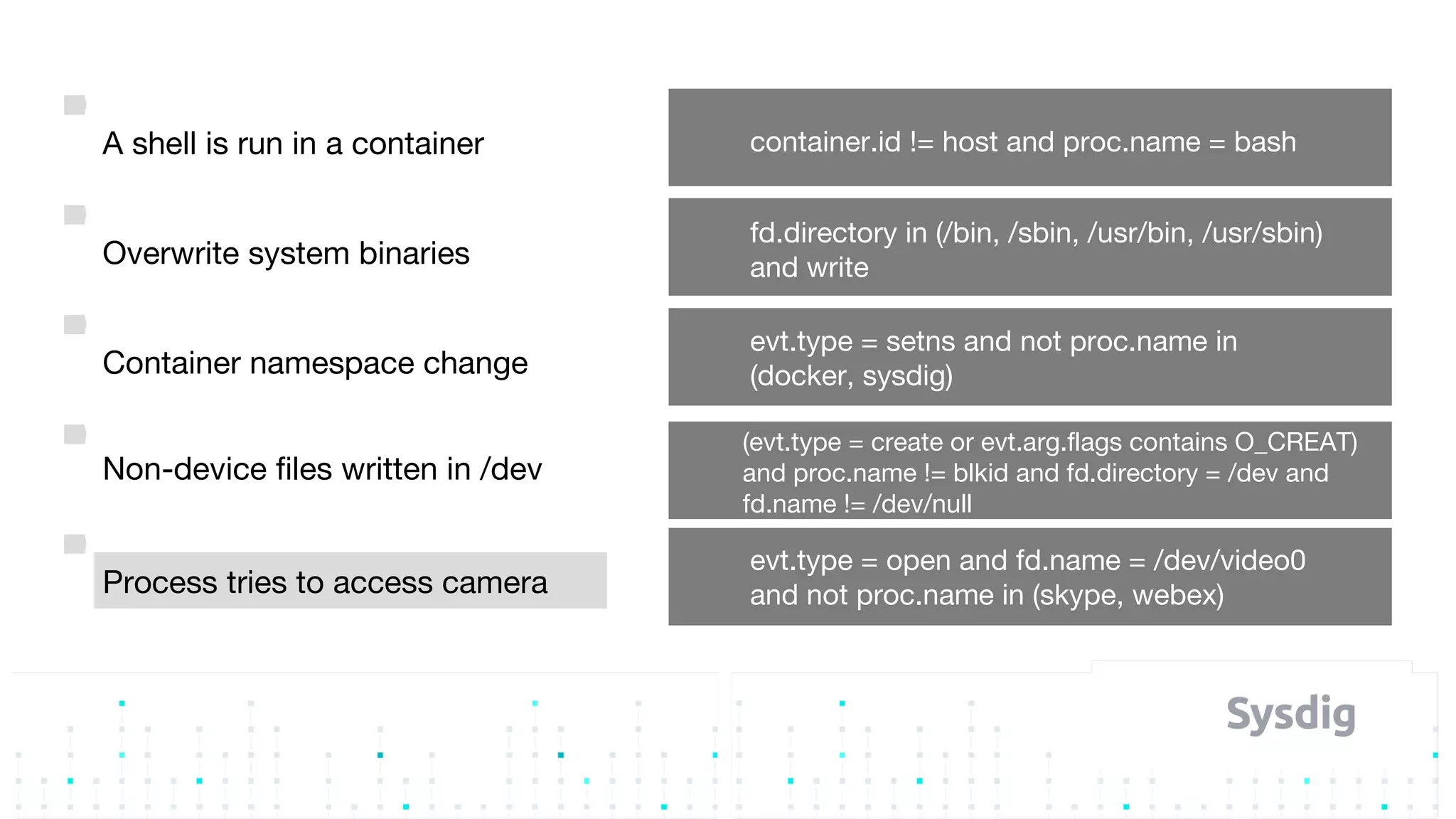
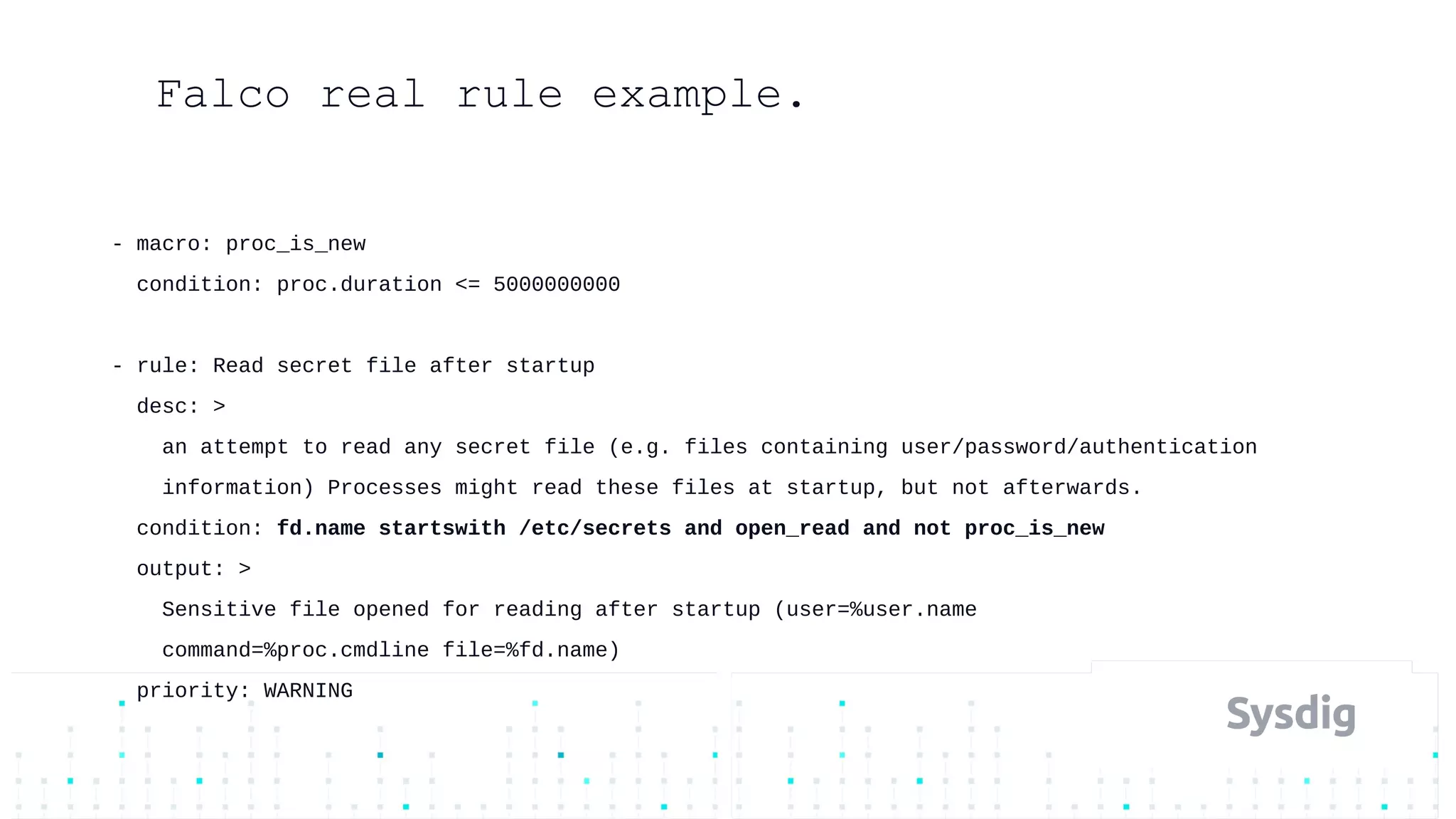
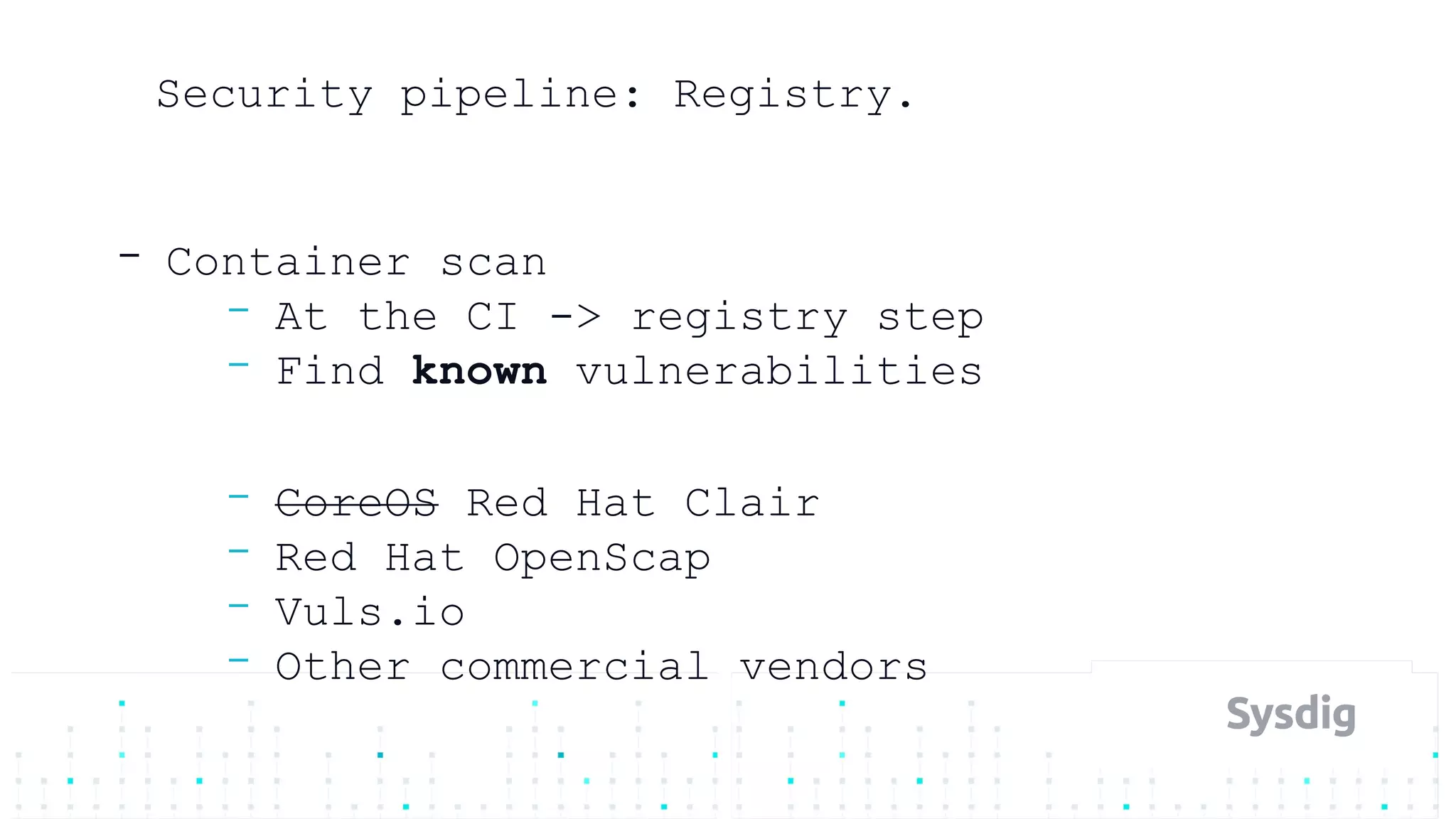
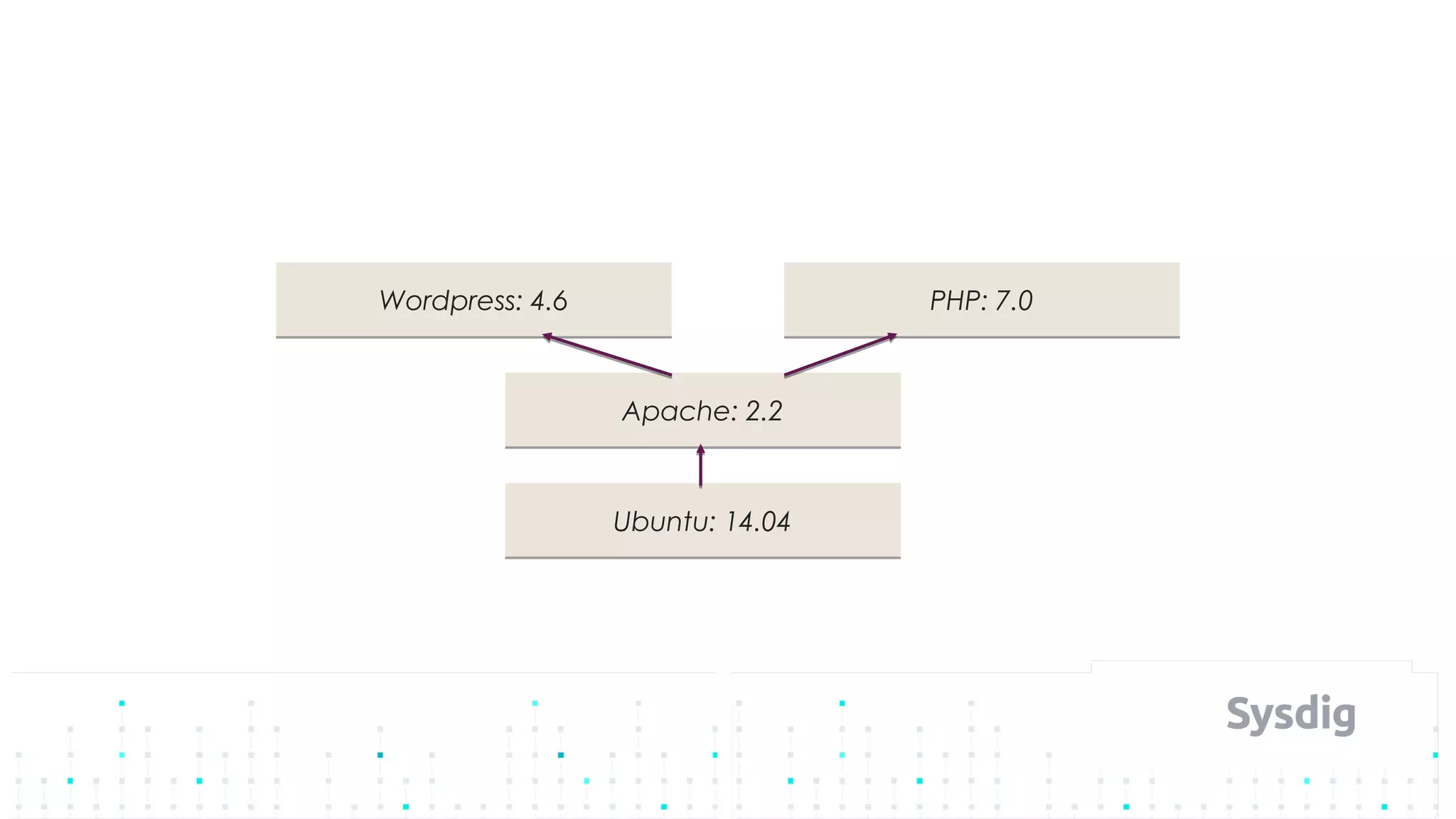
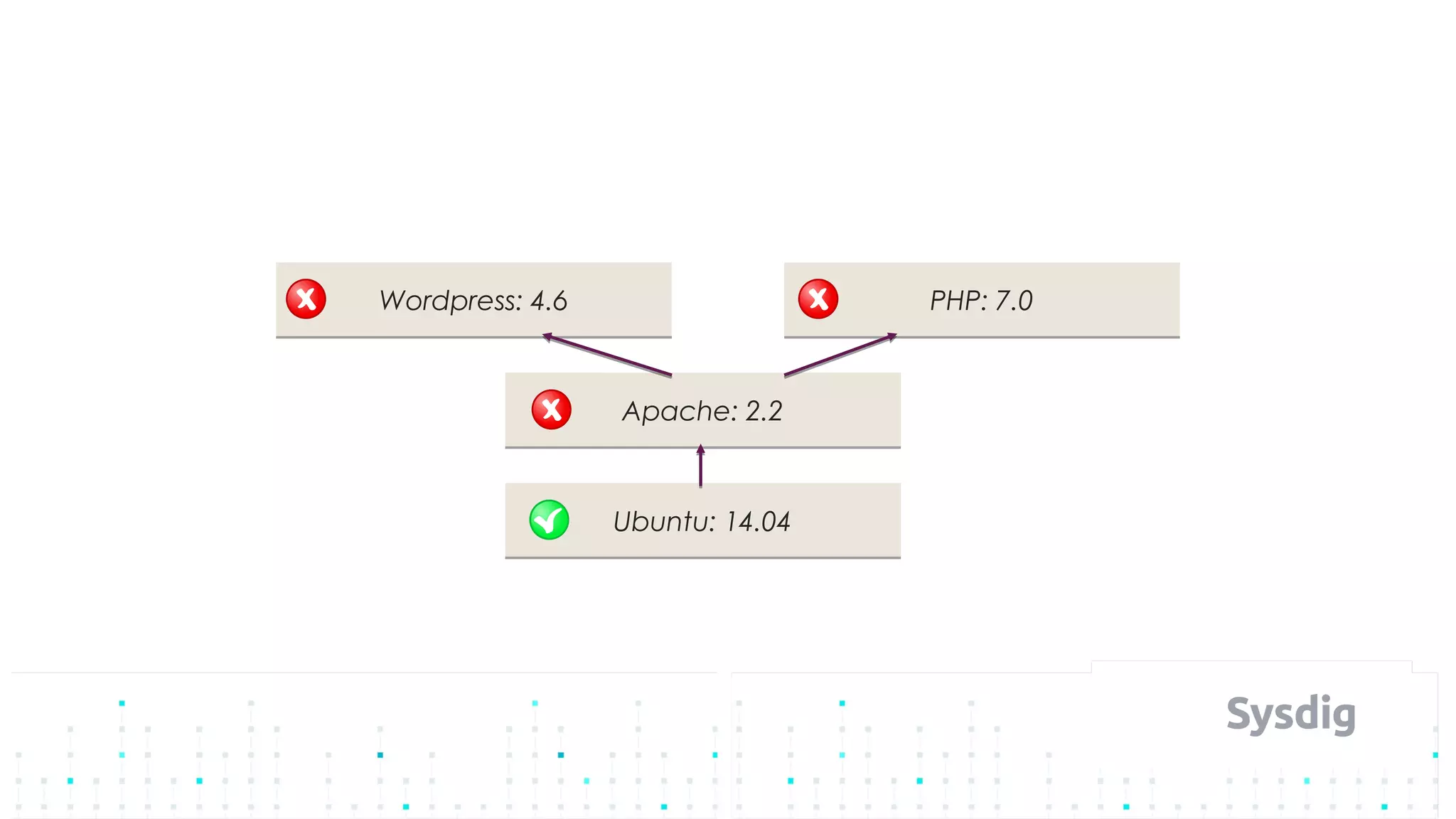
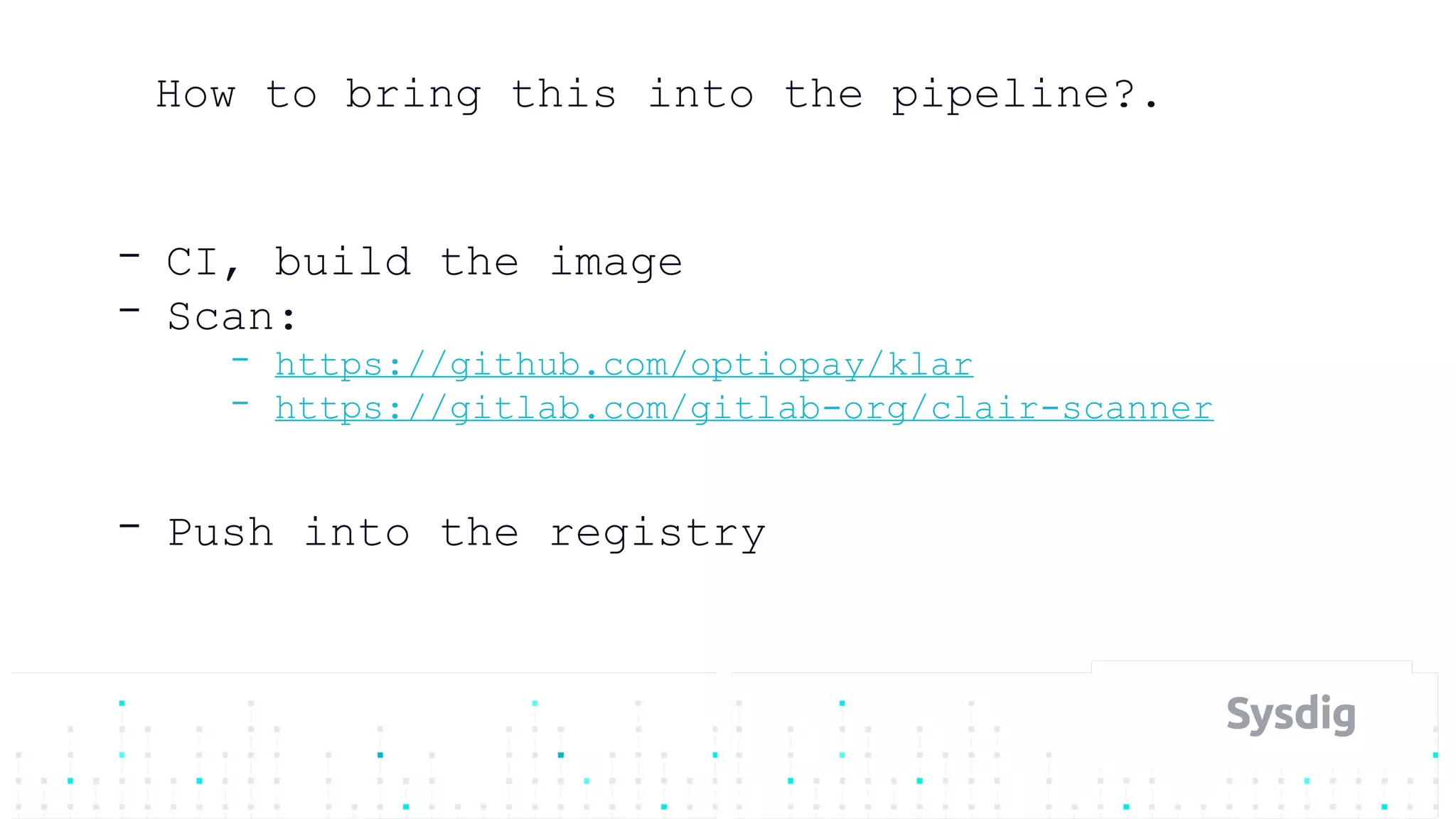
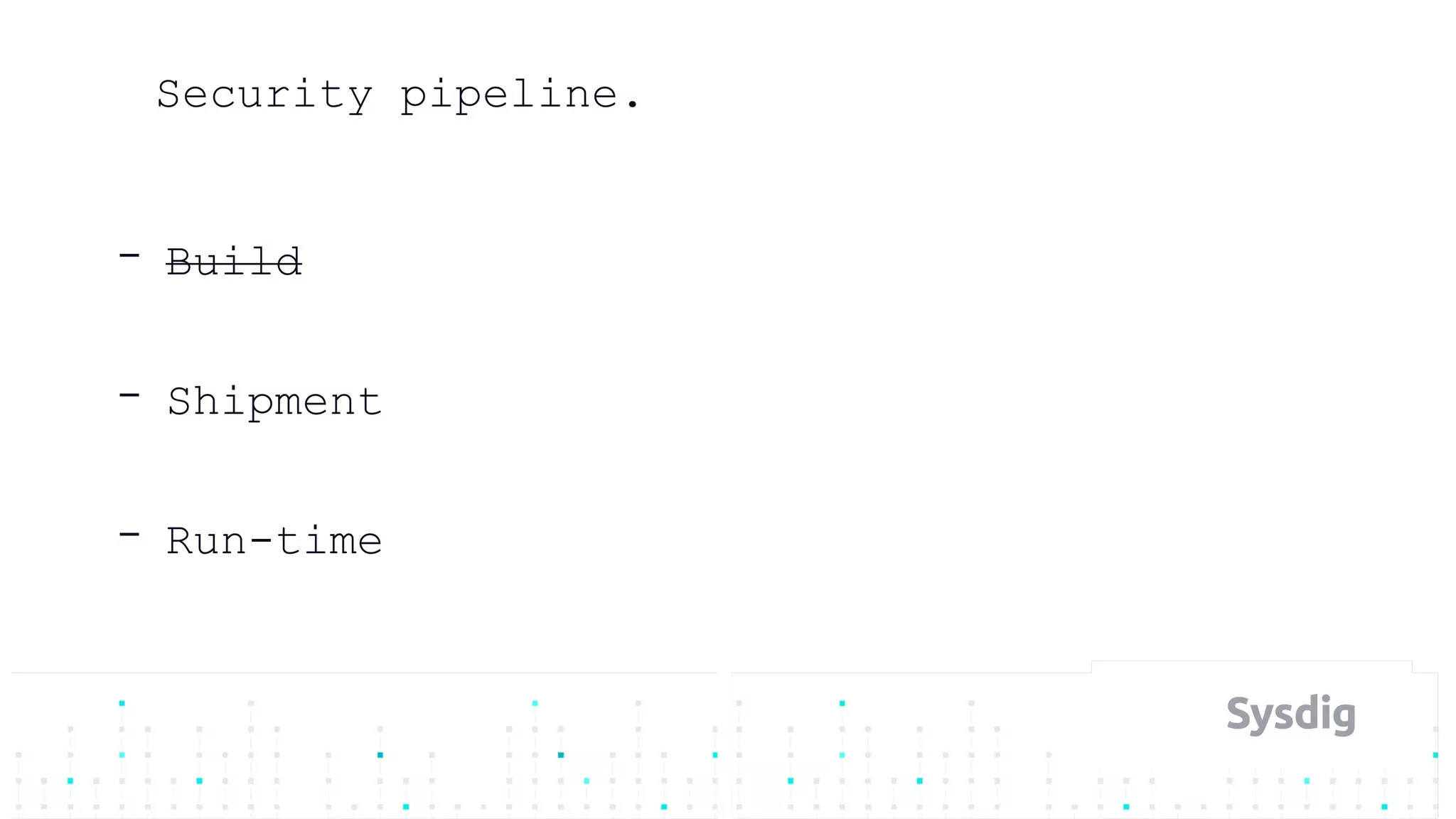
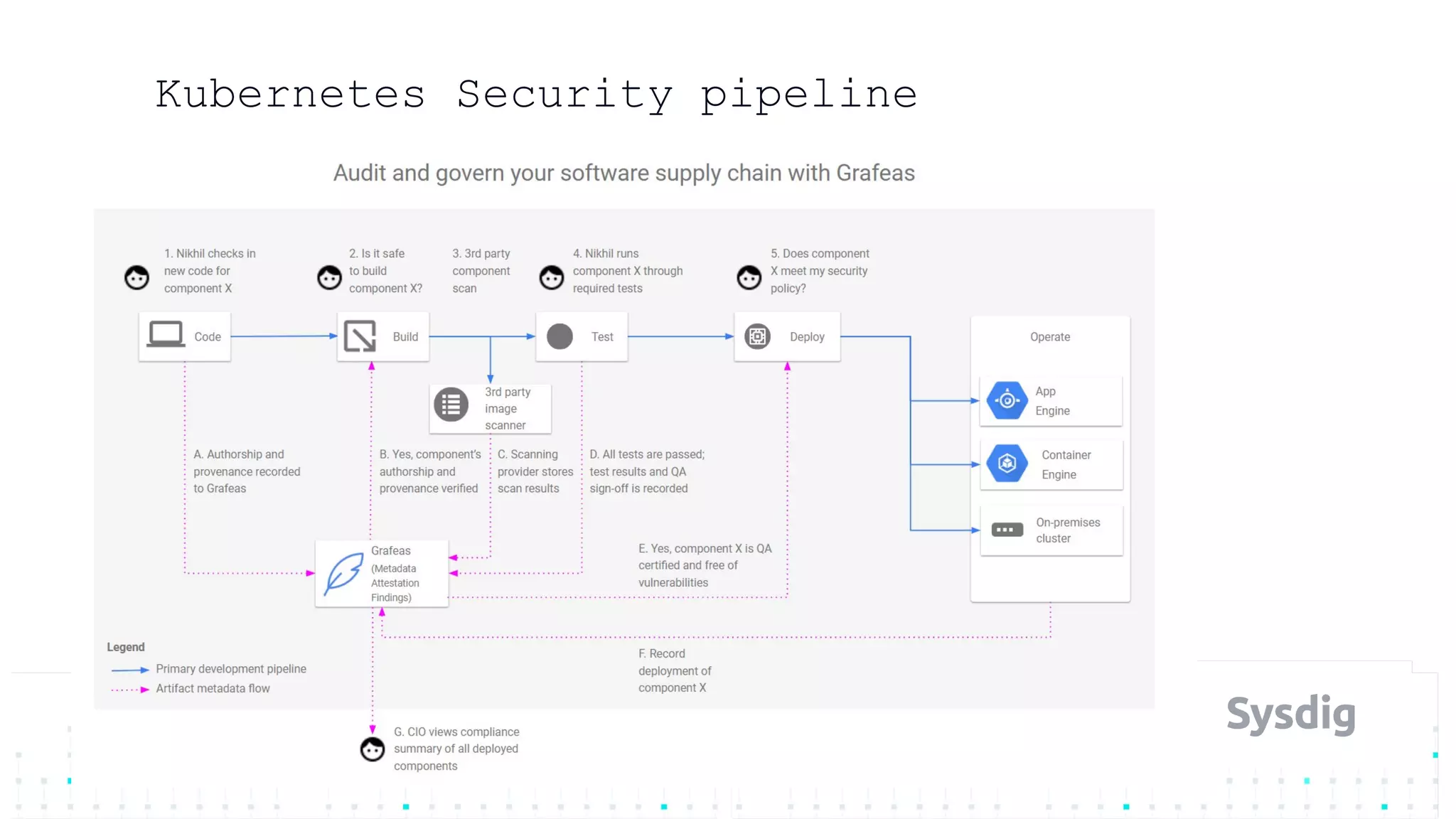
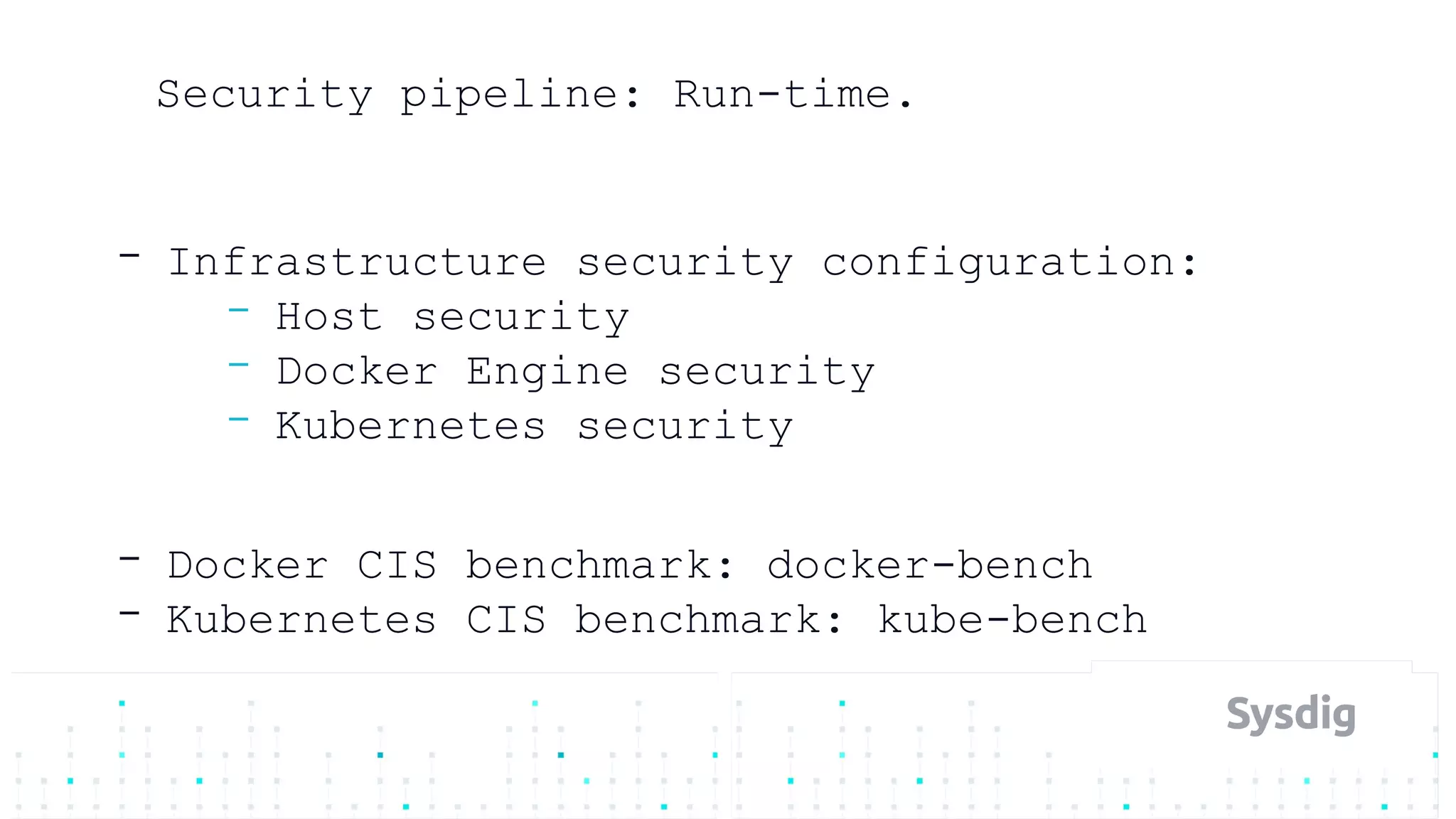
Mateo Burillo discusses the importance of continuous integration, delivery, and security in DevOps, emphasizing the need for a robust security pipeline in container environments. He outlines various security measures, including trust boundaries, attack surface minimization, and the significance of security as code, alongside implementing tools for vulnerability scanning and incident response. The presentation also covers Kubernetes security, monitoring, and the use of behavior-based analysis for threat detection.



















![kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
namespace: default
name: pod-reader
rules:
- apiGroups: [""] # "" indicates the core API group
resources: ["pods"]
verbs: ["get", "watch", "list"]
# This role binding allows "jane" to read pods in the "default" namespace.
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: read-pods
namespace: default
subjects:
- kind: User
name: jane
apiGroup: rbac.authorization.k8s.io
roleRef:
kind: Role
name: pod-reader
apiGroup: rbac.authorization.k8s.io](https://image.slidesharecdn.com/ci2fcd2fcs-180521112810/75/Continuous-Security-28-2048.jpg)