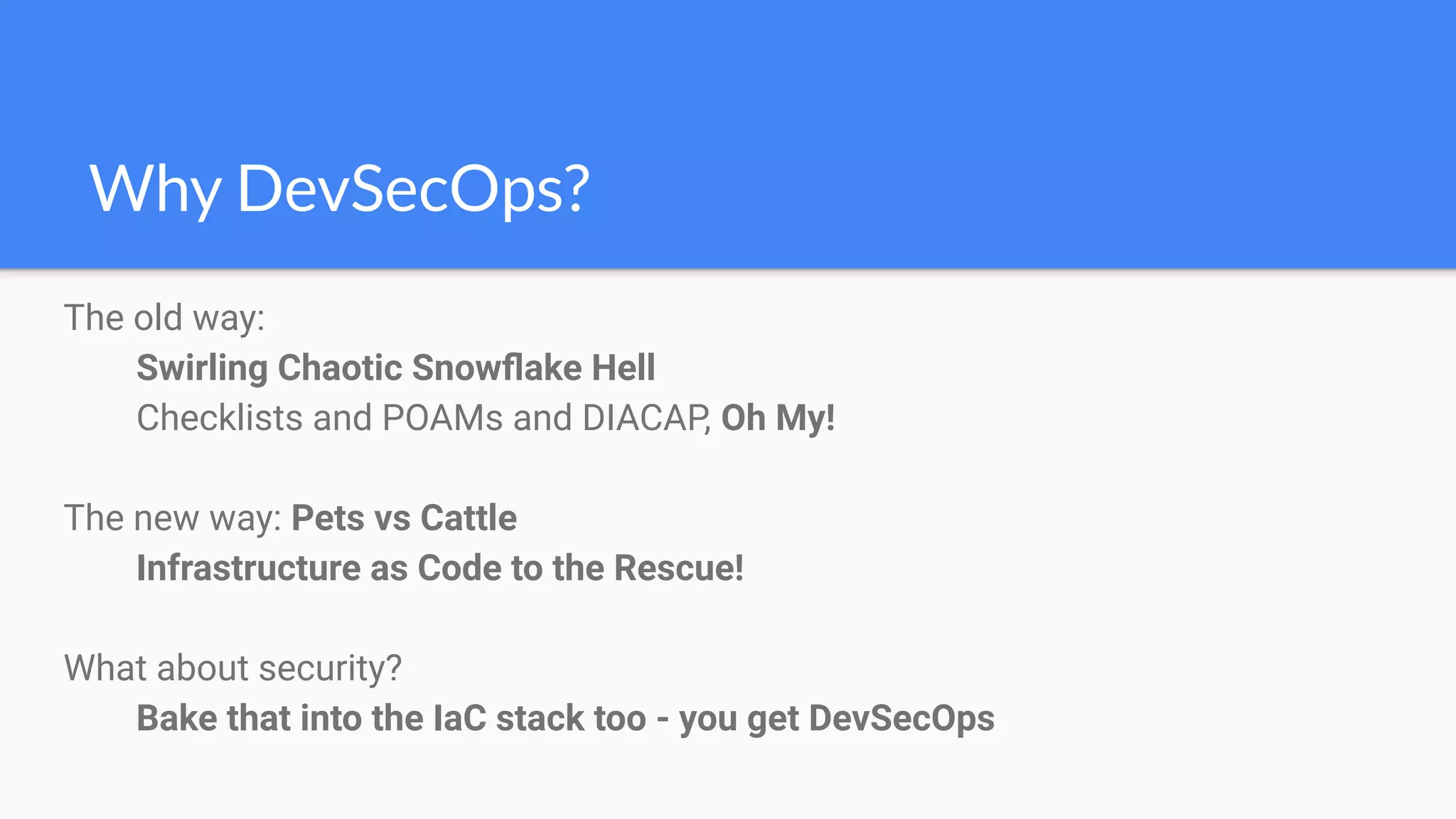
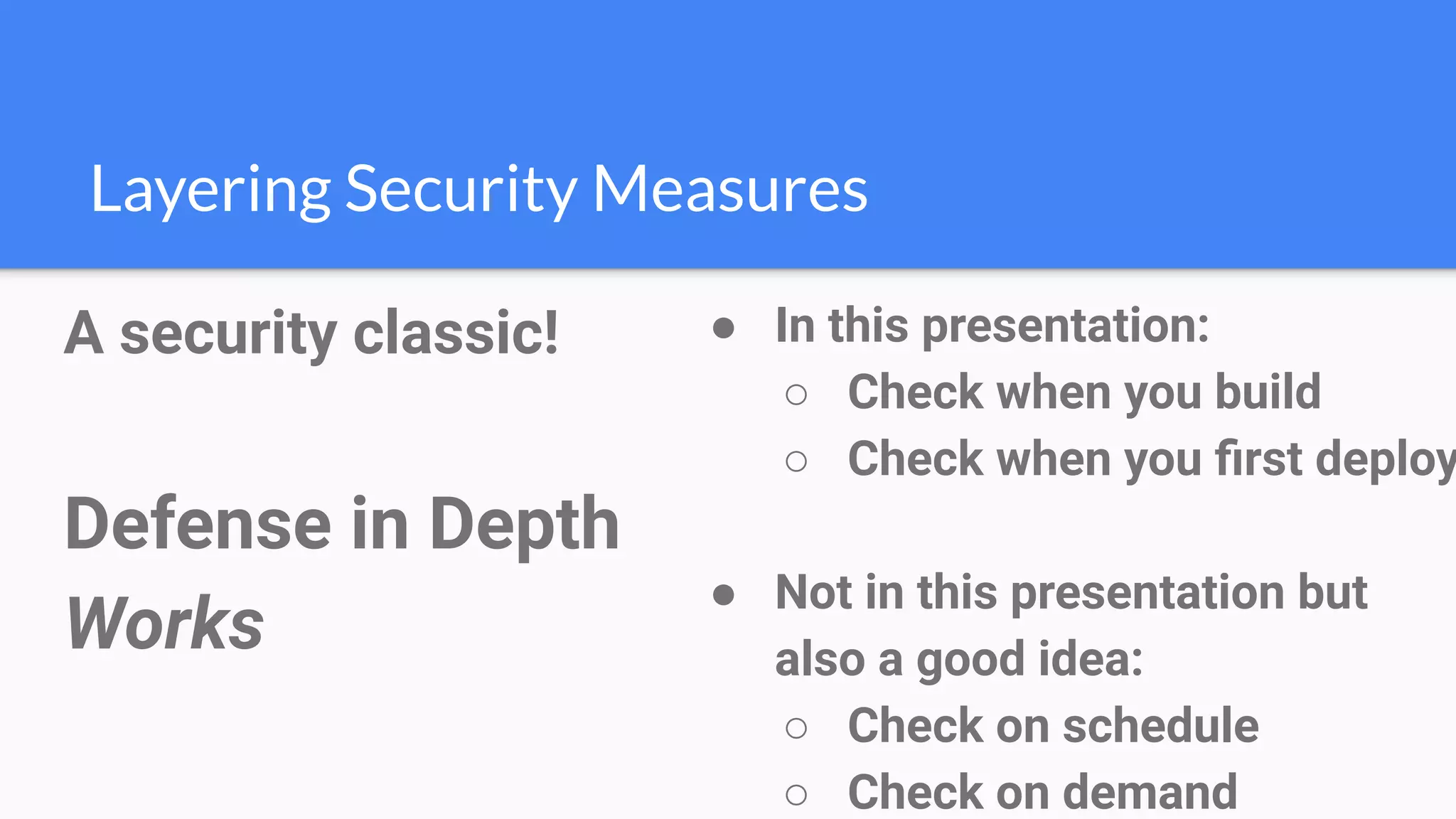
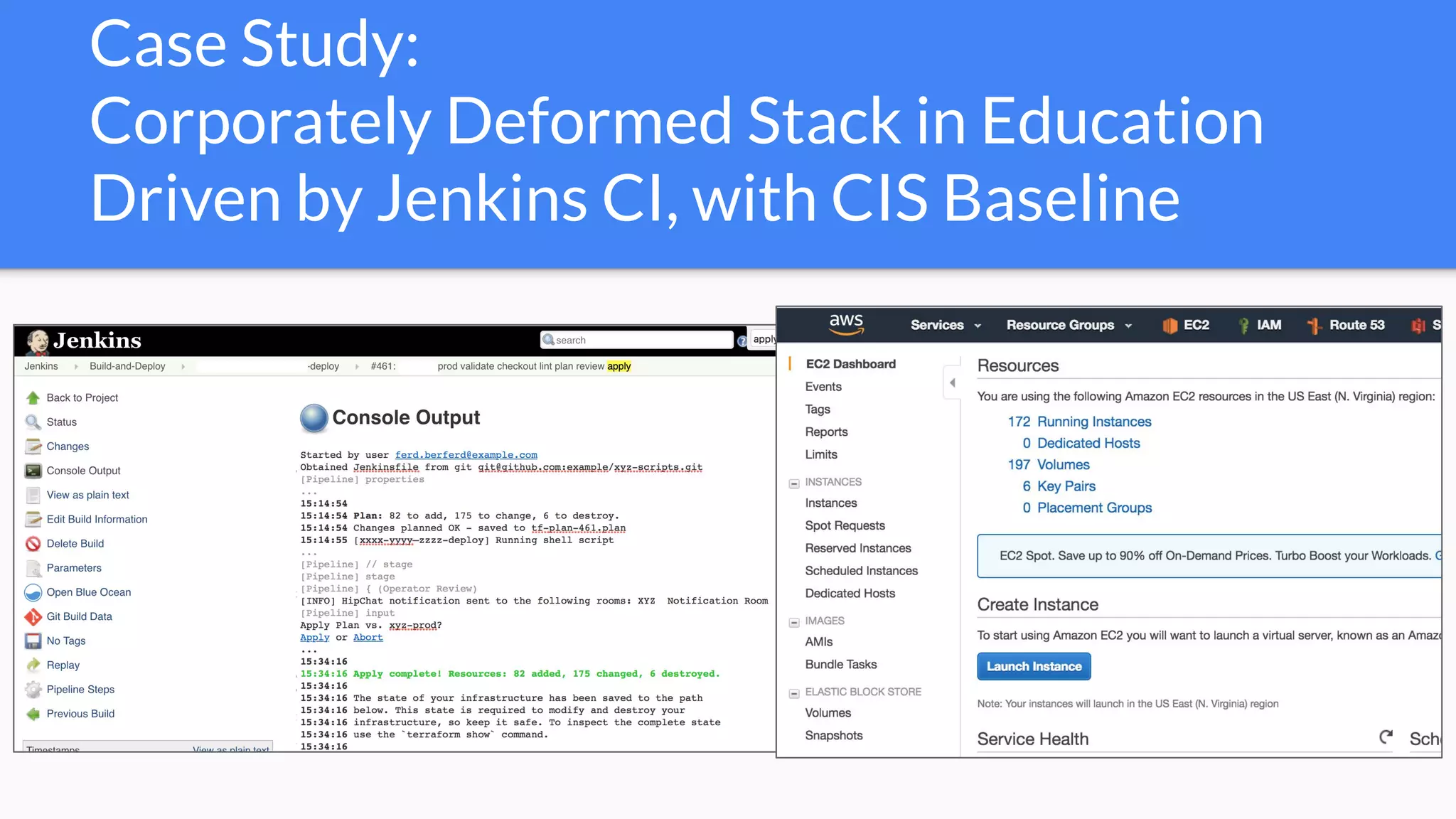
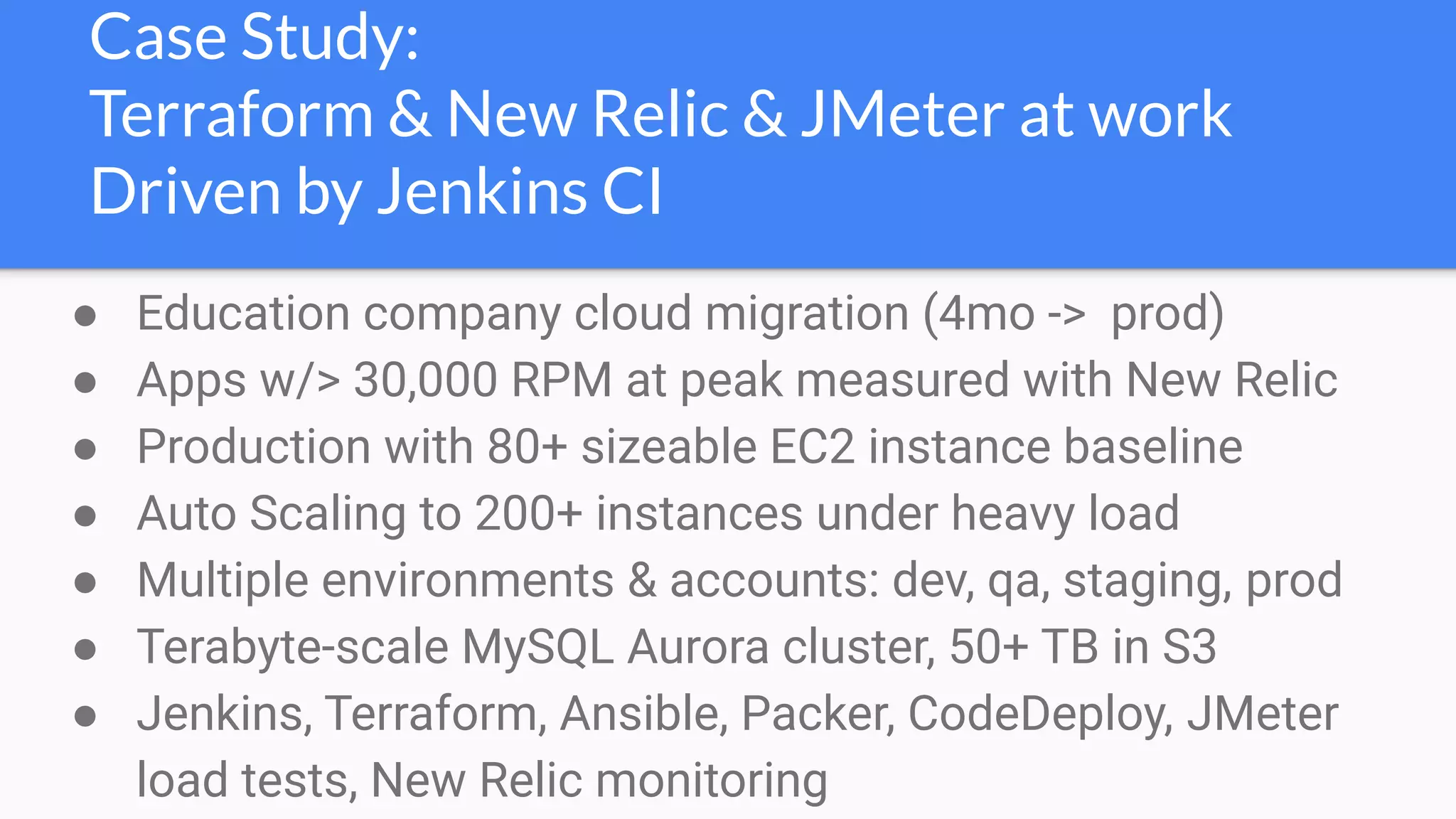
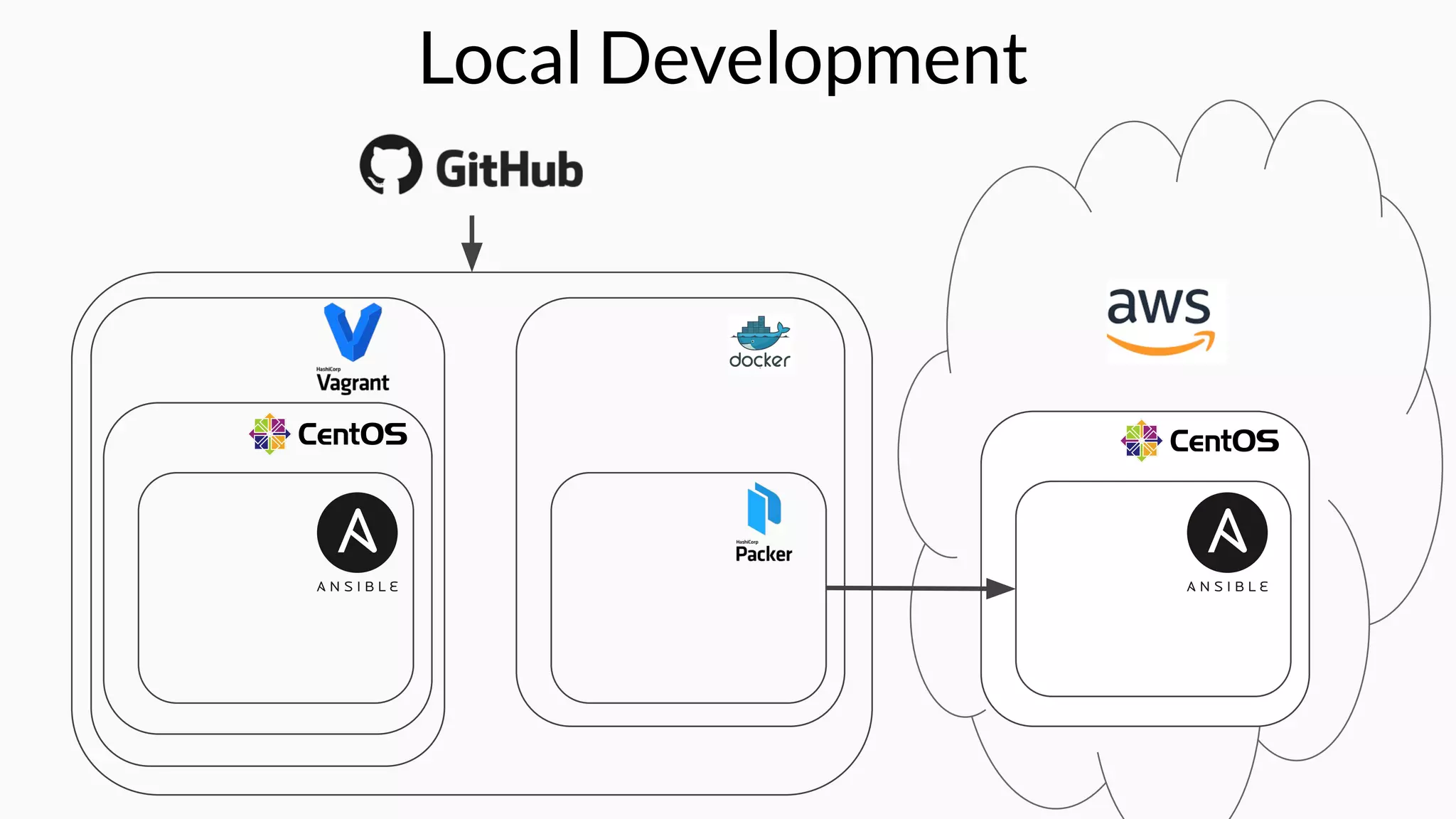
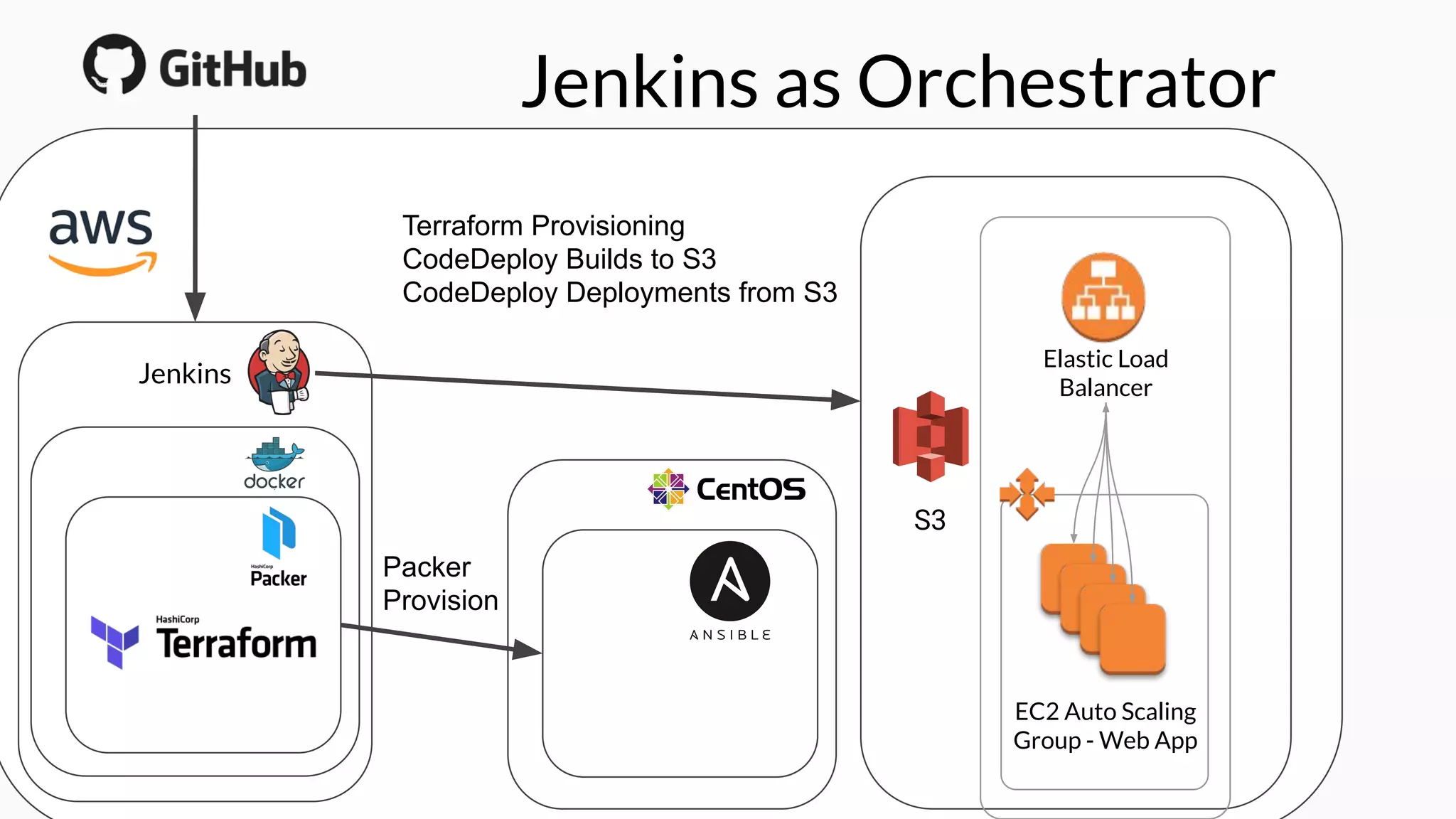
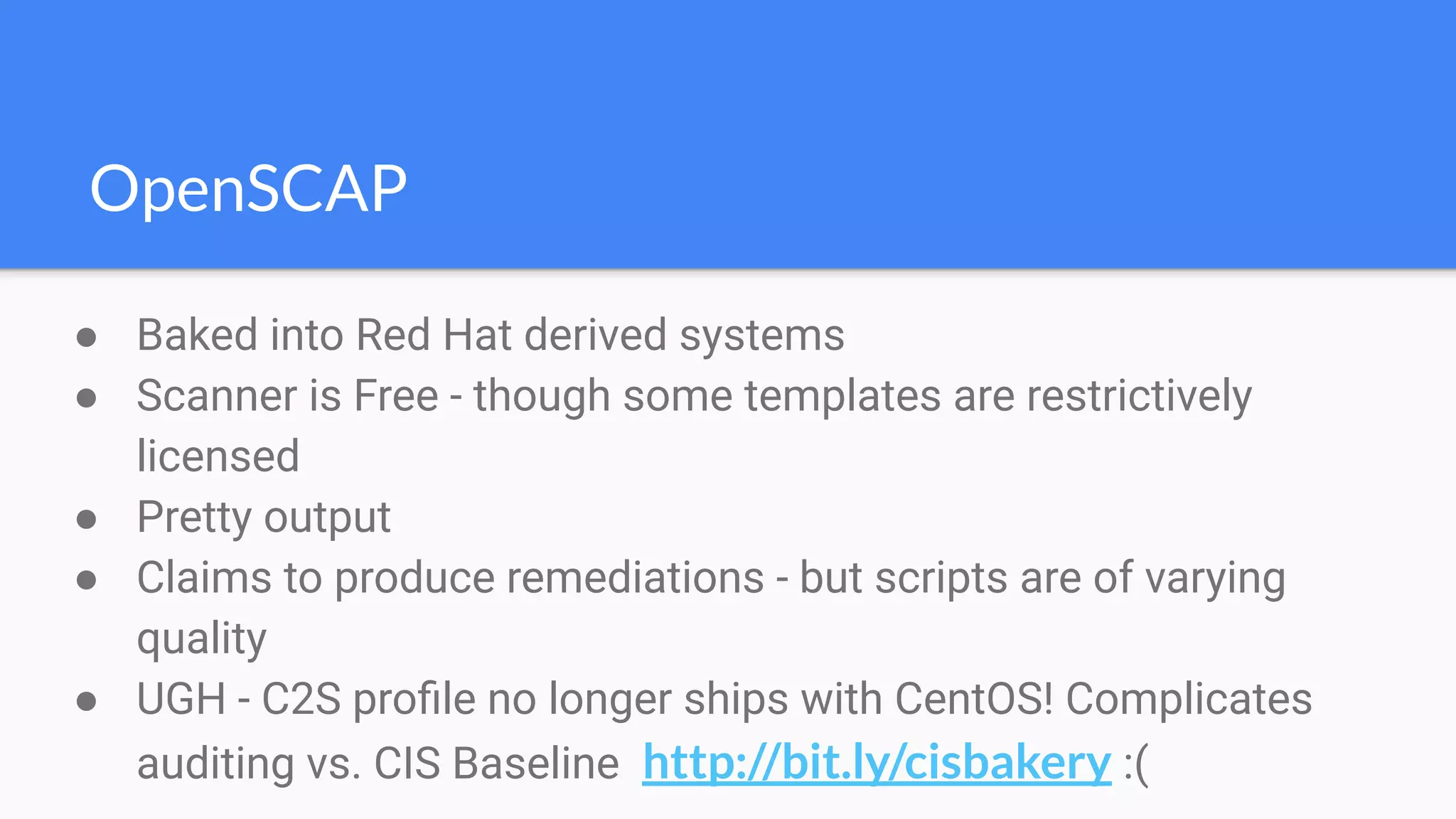
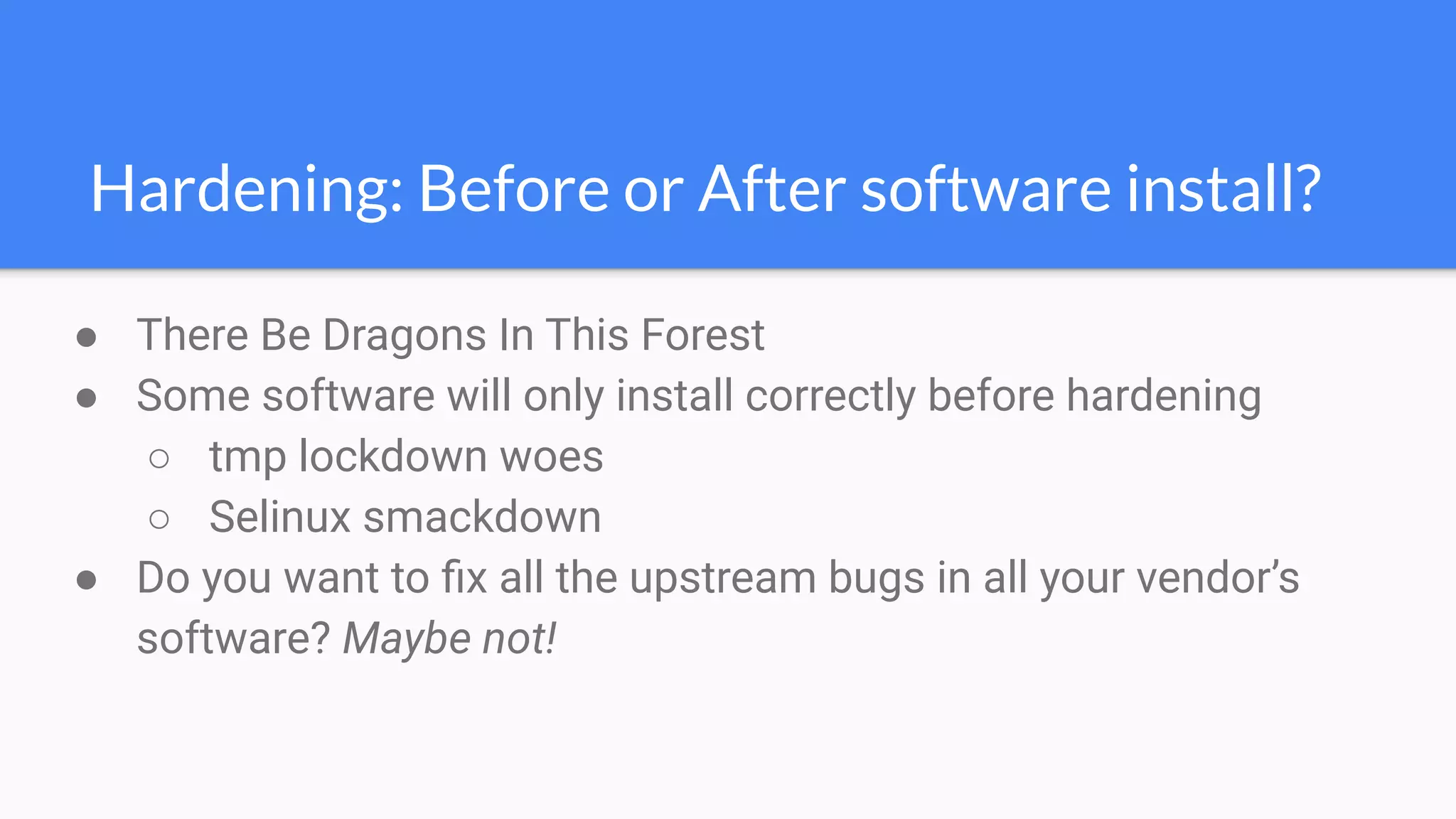
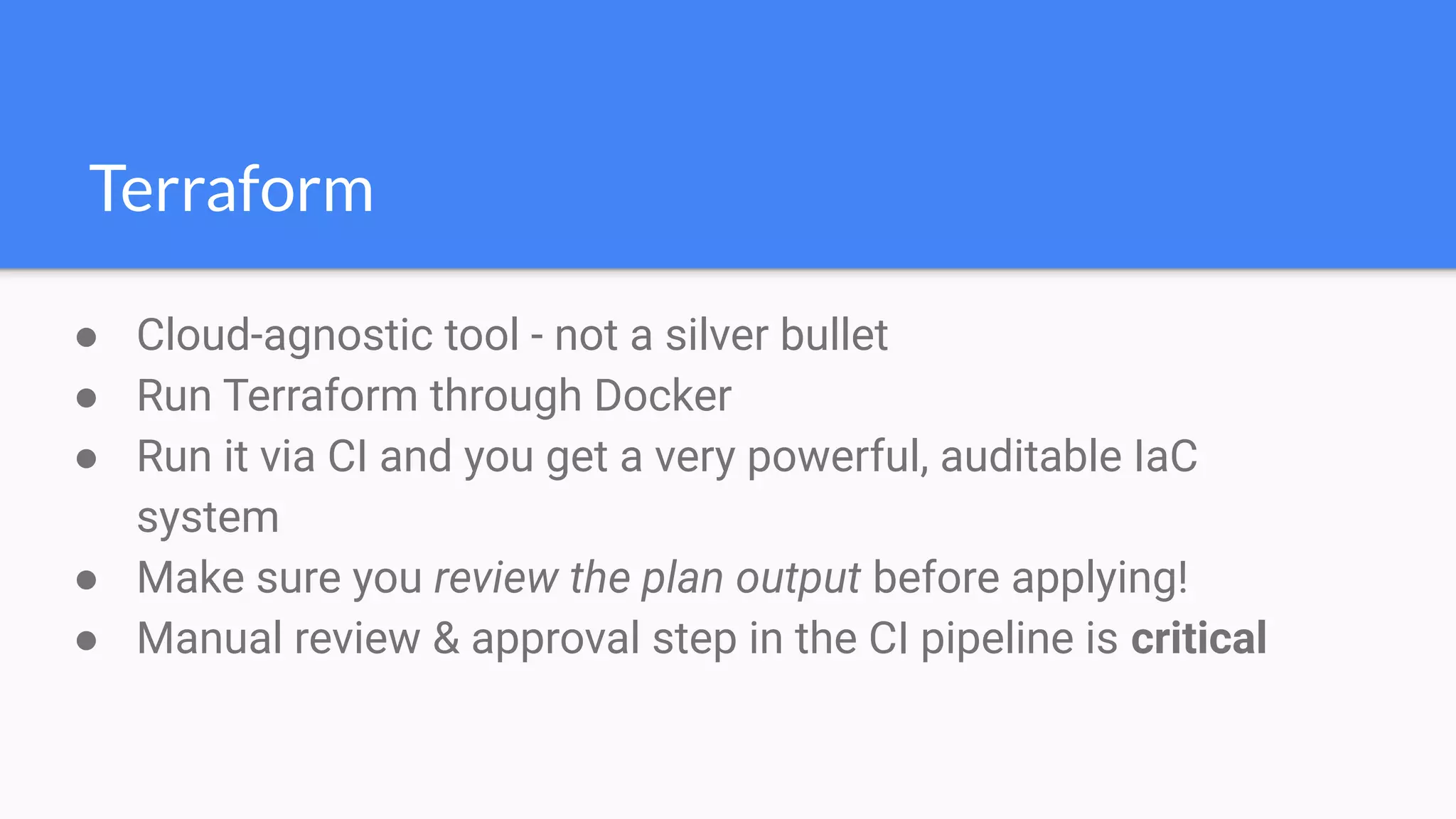
The document discusses the implementation of extensible DevSecOps pipelines using tools like Jenkins, Docker, and Terraform to enhance security in cloud infrastructure. It emphasizes the importance of integrating security checks throughout the deployment process and presents a case study from an education company that successfully migrated critical systems using these practices. Additionally, it covers best practices for system hardening, image creation, and managing containerized microservices amidst inherent complexities.