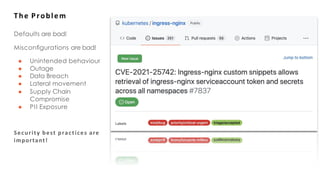
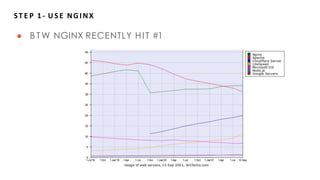
This document summarizes steps for securing an NGINX deployment on Kubernetes. It begins by outlining the challenge of securing a website hosted on NGINX without vulnerabilities. The plan is then described in three steps: 1) Use NGINX and get example code, 2) Wrap the code in a Kubernetes Deployment, and 3) Check for security issues using Checkov. Key aspects of securing the deployment discussed are applying the principle of least privilege through profiles, capabilities, and users, ensuring immutability with read-only filesystems and unmounting service account tokens, and increasing resilience with liveness/readiness probes and resource limits. The importance of using secure defaults, open source scanning tools, and an overall Dev