This document discusses various techniques for securing containers and monitoring container activity, including:
- Static and dynamic scanning of container images to detect vulnerabilities
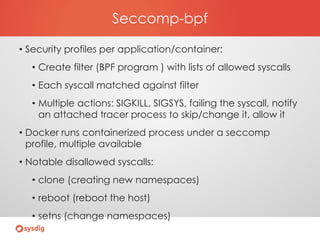
- Using seccomp, seccomp-bpf, SELinux, and Auditd for sandboxing and monitoring system calls
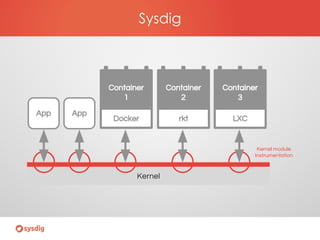
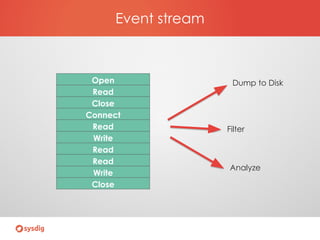
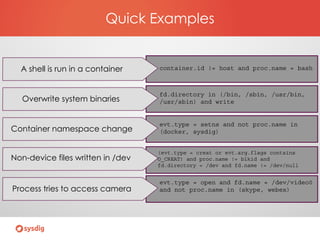
- Sysdig Falco for behavioral monitoring and detecting anomalies based on rules
- Examples of rules to detect things like shells running in containers or overwriting system binaries
The document provides an overview of these various security tools and techniques for containers, with examples of how they can be used to monitor and restrict container behavior to detect security issues or policy violations.



















![Falco Rules
• .yaml file containing Macros, Lists, and Rules
- macro: bin_dir
condition: fd.directory in (/bin, /sbin, /usr/bin, /usr/sbin)
- list: package_mgmt_binaries
items: [dpkg, dpkg-preconfigu, rpm, rpmkey, yum, frontend]
- rule: write_binary_dir
desc: an attempt to write to any file below a set of binary directories
condition: bin_dir and evt.dir = < and open_write and not package_mgmt_procs
output: "File below a known binary directory opened for writing
(user=%user.name command=%proc.cmdline file=%fd.name)"
priority: WARNING](https://image.slidesharecdn.com/wtfmycontainerjustspawnedashell-170208114801/85/WTF-my-container-just-spawned-a-shell-24-320.jpg)



