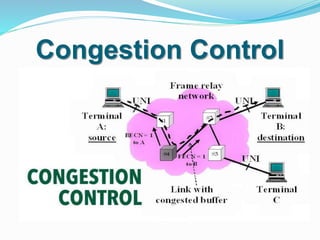
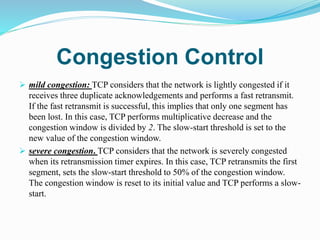
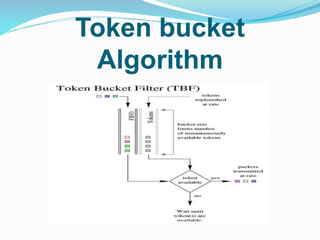
The document outlines the services provided by globalwebtutors.com, focusing on academic assistance such as homework and dissertation editing. It explains network congestion, its effects on performance, and methods to control it, including traffic shaping and algorithms like leaky bucket and token bucket. Additionally, it discusses TCP congestion control, emphasizing how TCP adapts its transmission rate in response to network losses.