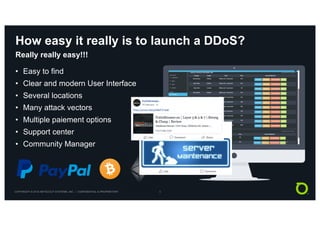
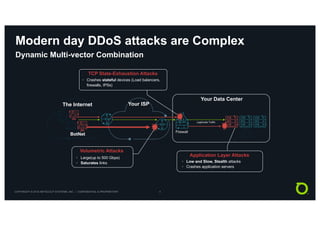
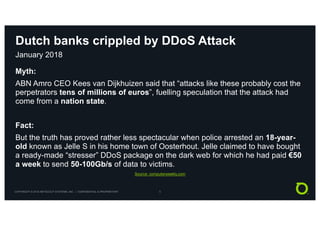
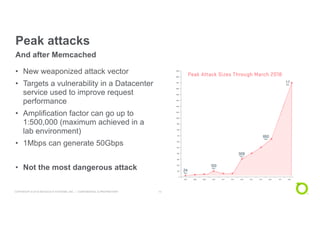
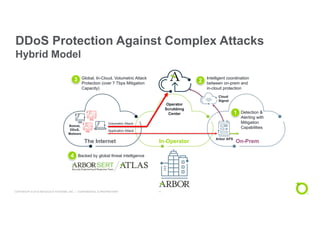
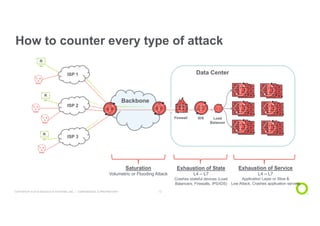
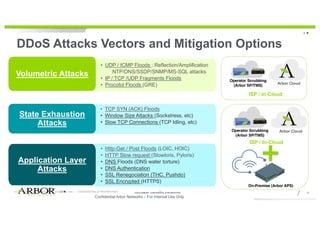
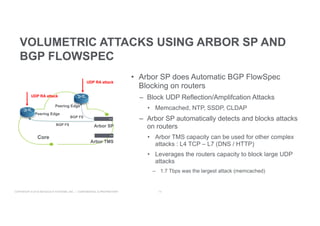
This document discusses techniques for advanced protection against distributed denial-of-service (DDoS) attacks. It begins by asking questions about knowing the latest DDoS attack trends, best mitigation practices, and the real impact of attacks. It then discusses how easy it is to launch DDoS attacks and the complexity of modern multi-vector attacks. Specific examples of DDoS attacks are provided, such as a 2018 attack against Dutch banks, and how every physical or geopolitical event has a corresponding cyber reflection. The document promotes Arbor Networks as the industry leader in DDoS protection and describes their hybrid DDoS mitigation approach using on-premise and in-cloud/operator solutions.