This document describes a web vulnerability scanner created by students at D.Y.Patil College of Engineering. The scanner focuses on detecting and preventing common web vulnerabilities like SQL injection, cross-site scripting, file inclusions, and OS command injection. It was developed using the waterfall model, with phases for requirements gathering, system design including UML diagrams, and implementation. The motivation was that cyber attacks cost the global economy over $400 billion annually, so an automatic tool is needed to identify vulnerabilities in web applications.
![International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 07 Issue: 03 | Mar 2020 www.irjet.net p-ISSN: 2395-0072
© 2020, IRJET | Impact Factor value: 7.34 | ISO 9001:2008 Certified Journal | Page 2725
Web Vulnerability Scanner
Mr.Kalyan D Bamane1, Vaibhav Gaikwad2, Nikhil Ahire3, Kunal Sambhe4, Chetan Jagtap5
1Professor Kalyan D Bamane, Dept. of Information Technology of D.Y.Patil College of Engineering, Akurdi,
Maharashtra, India
2Vaibhav Gaikwad, Dept. of Information Technology of D.Y.Patil College of Engineering, Akurdi,
Maharashtra, India
3Nikhil Ahire, Dept. of Information Technology of D.Y.Patil College of Engineering, Akurdi,
Maharashtra, India
4Kunal Sambhe, Dept. of Information Technology of D.Y.Patil College of Engineering, Akurdi, Maharashtra, India
5Chetan Jagtap, Dept. of Information Technology of D.Y.Patil College of Engineering, Akurdi, Maharashtra, India
---------------------------------------------------------------------***----------------------------------------------------------------------
Abstract - The code life cycle was in use to develop the
gorgeous smart code. This daysthecodedevelopmentlifecycle
ought to incorporate the protection options. Input Validation
Attacks on input field area unit one in every of the foremost
wide unfold types of vulnerability on the online application.
Our main aim is to focuses on detection of vulnerability and
bar of Input Validation attacks like SQL Injection, Cross site
Scripting ,File Inclusions, OS Command Injection (OSCi) by
incorporating security in code development life cycle.
Key Words: Cross site Scripting, File Inclusions, OS
Command Injection, SQL Injection.
1. INTRODUCTION
OS Command Injection could be an attack techniqueusedfor
unauthorized execution of software system commands over
vulnerable machine. The aim of associate degree (Oscar) OS
Command Injection is that the execution of absolute
commands on the host software system via a vulnerable
applications. (OSCi) OS Command Injection attacksareaunit
potential once associate degree application passes unsafe
user provided knowledge (forms, cookies, HTTP headers,
then on) to a system shell). Cross-site Scripting XSS refers to
client-side code injection attack whereby associate degree
aggressor will execute malicious java scripts (also
unremarkably brought up as a malicious payload) into a
legitimate web site or vulnerable internet application. XSSis
amongst the foremost severe of internet application
vulnerabilities and happens once an internet application
makes use of nullified or unencoded user input at intervals
the output it generates.
Remote File Inclusion (RFI) is associate degree attack
technique that exploits the power of bound web-based
programming frameworks to dynamically execute remote
scripts over a vulnerable machine. The vulnerabilities
manifest once the name or location of the remote script is
built exploitationinputparameters inassociatedegreeHTTP
request and also the internet application fails to validate
these inputs. (SQLi) SQL Injection refers to associate degree
injection attack whereby associate degree aggressor will
execute malicious SQL statements (also unremarkably
brought up as a malicious payload) that management an
internetapplication’sinformationserver(alsounremarkably
brought up as a on-line database Management System
_RDBMS).By investment associate degree SQL Injection
vulnerabilities, given the correct circumstances to associate
degree aggressor will use it to bypass an internet
application’s authentication and authorization mechanisms
and retrieve the contentsof wholeinformation.SQLInjection
is additionally accustomed add, modifyanddelete recordsin
an exceedingly information that affects knowledgeintegrity.
2. LITERATURE SURVEY
There area unit range of researches done on numerous
internet vulnerabilities that comes underneath linguistics
uniform resource locator, XSS, RFI, LFI, SQLi, CMDi etc.
In this our project comes underneath linguistics uniform
resource locator means that such attacks involve a user
modifying the uniform resource locator discover mode to
perform numerous actions that aren't originally planned to
be handled by server. We tend to studied numerous
vulnerabilities like RFI, LFI, SQLi, Cross-Site Scripting.
[1] Most of the dealing data or the client data is hold on
within the backend databases fortheseinternetapplications.
One in every of the vulnerabilities of the online applications
is SQL (Structured question Language) injectionattack.Also,
the online application sessions area unit susceptible to
session hijacking attack, if the human will holdofthesession
id. Considering, there area unit numerous tools on the
market to retrieve session/HTTP cookies, this makes
internet applications very susceptible to session hijacking
attacks. There area unit some ways projected to defend the
databases against SQL injection attacks, get there's no
certain shot thanks to stop these SQL injection attacks. This
project proposes an especially economical technique for the
bar of SQL injection attack and session-hijacking. The
hashing technique is employed for implementing the bar of
those attacks.
[2] Second-order SQL injection could be a serious threat to
internet application and it's harder to observe than first-
order SQL injection. The attack payload of second order SQL
injection (SQLi) is from untrusted user input and hold on in](https://image.slidesharecdn.com/irjet-v7i3544-201221025508/75/IRJET-Web-Vulnerability-Scanner-1-2048.jpg)
![International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 07 Issue: 03 | Mar 2020 www.irjet.net p-ISSN: 2395-0072
© 2020, IRJET | Impact Factor value: 7.34 | ISO 9001:2008 Certified Journal | Page 2726
information or filesystem he SQL statement submitted by
internet application is sometimes dynamically assembledby
a trustworthy constant string within the program and
untrusted user provided input, and also the softwaresystem
in unable to differentiate the trustworthy and untrusted a
part of a SQL statement. The paper presents a technique of
finding second order SQL injection attacks supported ISR
Instruction Set randomisation. the tactic randomise the
trustworthy SQL keywords contained in internet
applications to dynamically build new SQL instruction sets,
and add a proxy server before software system, the proxy
detects whether or not the received SQLinstructioncontains
commonplace SQL keywords to seek out attack behaviour .
Experimental results show that this technique will
effectively observe second-order SQL injection attack and
has low process price.
[3] Internet applications take a vital role in remote access
over the net. These applications haveseveralcapabilities like
information access, file read/write, calculations additionally
as desktop applications however run in internet browsers
environments. As desktopapplications,internetapplications
may be exploited however with totally different techniques
one in every of the main famous vulnerabilities of the net
applications is native File Inclusion. Inclusion in internet
applications is comparable to library imports in desktop
applications wherever a developer will embrace former
developed codes. If associate degree assailant includes
his/her libraries, he/she will run his/her malicious code.
Current analysis makes a short survey of static and dynamic
code analysis and suggests a framework for dynamically
preventing malicious file inclusions by attackers. it's
mentioned that this framework prevents native file
inclusions notwithstanding the developer has exploitable
ASCII text file. The language PHP is employed for describing
the vulnerability and interference framework.
[4] A web application is a computer program that utilizes
web browser and web technology to perform tasks over the
internet. In recent years, millions of businesses use the
internet as an effective communication channel which lets
them exchange the information worth their target market
and makes fast,, secure transactions. However, there are
many threats which are arising to gain this valuable
information which is mainly done by various kinds of
attackers who uses different kind of techniques for data
thief. So, the challenge is to provide the security to various
web application and prevent the attacker to gain root shell
access and admin passwords. In survey, observed that the
attacks like RFI(Remote File Inclusion) and LFI(Local File
Inclusion) are truly vulnerable. Though, these kinds of
attacks are rare but the unauthorized access can harm the
whole system. So, system mainly concentrates on detection
and prevention of web application by using various
techniques such as Dynamic Allocation,FileSizeVerification,
Digital Signature and Sanitization of Input. The successful
overcoming of these attacks will increase the securitywhich
will improve the quality of web application.
3. MOTIVATION:
Cyber risk is currently firmly at the highest of the
international agenda ashigh-profilebreachesraisefearsthat
hack attacks and differentsecurityfailuresmayendanger the
worldwide economy law-breaking prices the worldwide
economy over United States $400 billion p.a., per estimates
by the Centre for Strategic and International Studies. In
2017, some 10,000 firms within the US had their systems
compromised by criminals, the Centre reports therefore
there's a necessity for an automatic software package which
can facilitate in recognizing loop holes in internet
applications.
4. ANALYSIS MODEL:
We are using waterfall model for our project.
1. Demand gathering and analysis:
In this step of falls we tend to establish what are numerous
necessities are want for our project such are software
package and hardware needed, database, and interfaces.
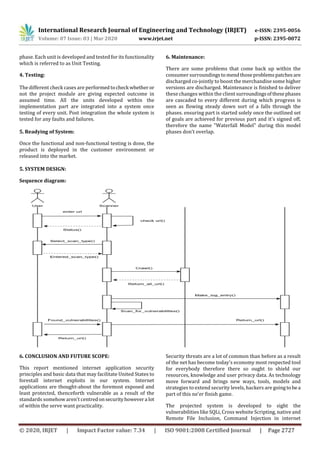
2. System Design:
In this system style part we tend to style the system that is
definitely understood for user i.e. user friendly we tend to
style some UML diagrams and knowledge multidimensional
language to know the system flow and system module and
sequence of execution.
3. Implementation:
In implementation part of our project we've enforced
numerous module needed of with success obtaining
expected outcome at the various module levels.
With inputs from system style, the system is initial
developed in tiny programs referred to as units, that are
integrated within the next part every unit is developed and
tested for its practicality that is spoken as Unit Testing With
inputs from system design, the system is first developed in
small programs called units, which are integratedinthenext](https://image.slidesharecdn.com/irjet-v7i3544-201221025508/85/IRJET-Web-Vulnerability-Scanner-2-320.jpg)
![International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 07 Issue: 03 | Mar 2020 www.irjet.net p-ISSN: 2395-0072
© 2020, IRJET | Impact Factor value: 7.34 | ISO 9001:2008 Certified Journal | Page 2728
applications and it'll conjointly give data concerning remedy
of vulnerable universalresourcelocatoranditsvulnerability.
Our systematization goes at the guts of the matter and
captures apparently differing kinds of on top of mentioned
vulnerabilities. The straightforward and effectivestrategyis
supposed to be value effective and is brazenly targeted
toward massive industrial applications. The results of the
projected systems are satisfactory.
7. ACKNOWLEDGEMENT
We are highly indebted to Prof Mr. K.D.Bamane our project
guide for his guidance and constant supervision as well as
for providing necessary information regarding the project&
also for his support in completing this Research Paper. We
would like to express my gratitude towards Head of I.T.
Department Dr Mrs. Preeti Patil for her kind co-operation
and encouragement which helped us in completion of this
Research Paper
REFERENCES
[1] KarisD’silva,J.Vanajakshi,KNManjunath,SrikanthPrabhu"
An Effective Method for Preventing SQLInjectionAttack
and Session Hijacking"Electronic ISBN: 9781-5090-
3704-9 .
[2] Chen Ping"A second-order SQL injection detection
method"Electronic ISBN: 9781-5090-6414-4.
[3] Mir Saman Tajbakhsh; Jamshid Bagherzadeh“A sound
framework for dynamic prevention of Local File
Inclusion” ISNB: 978-1-4673-7485-9.
[4] P.S.Sadaphule, Priyanka Kamble,Sanika Mehre,Utkarsha
Dhande,Rashmi Savant” Prevention of Website Attack
Based on Remote File Inclusion-A survey” International
Journal of Advance Engineering and Research
Development” e-ISSN : 2348-4470](https://image.slidesharecdn.com/irjet-v7i3544-201221025508/85/IRJET-Web-Vulnerability-Scanner-4-320.jpg)