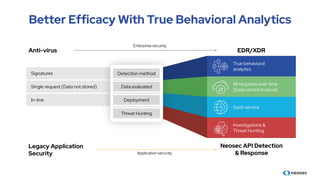
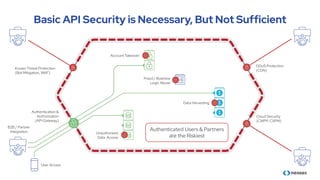
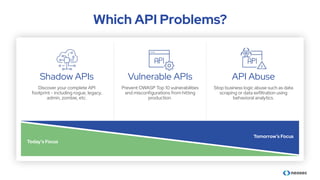
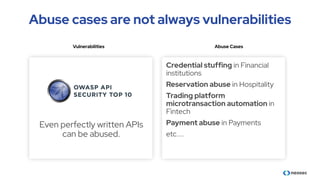
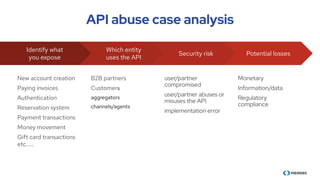
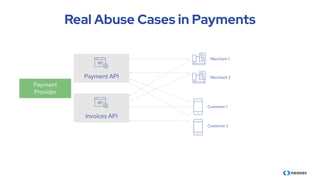
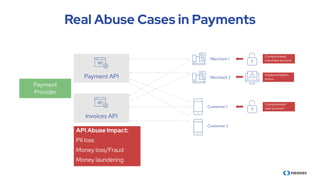
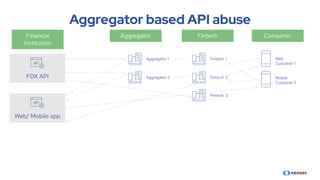
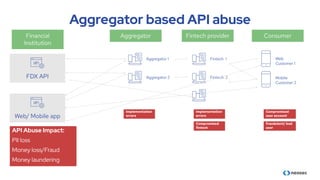
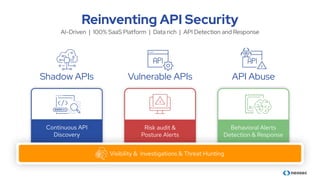
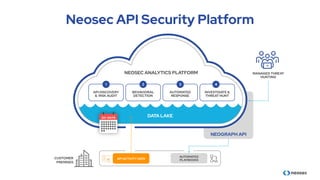
The document discusses the importance of behavioral analytics in understanding and preventing API abuse. It emphasizes the need for comprehensive visibility into API activity and highlights the risks posed by both attacks and vulnerabilities, particularly in B2B environments. Solutions such as automated detection and response systems are proposed to mitigate these risks effectively.