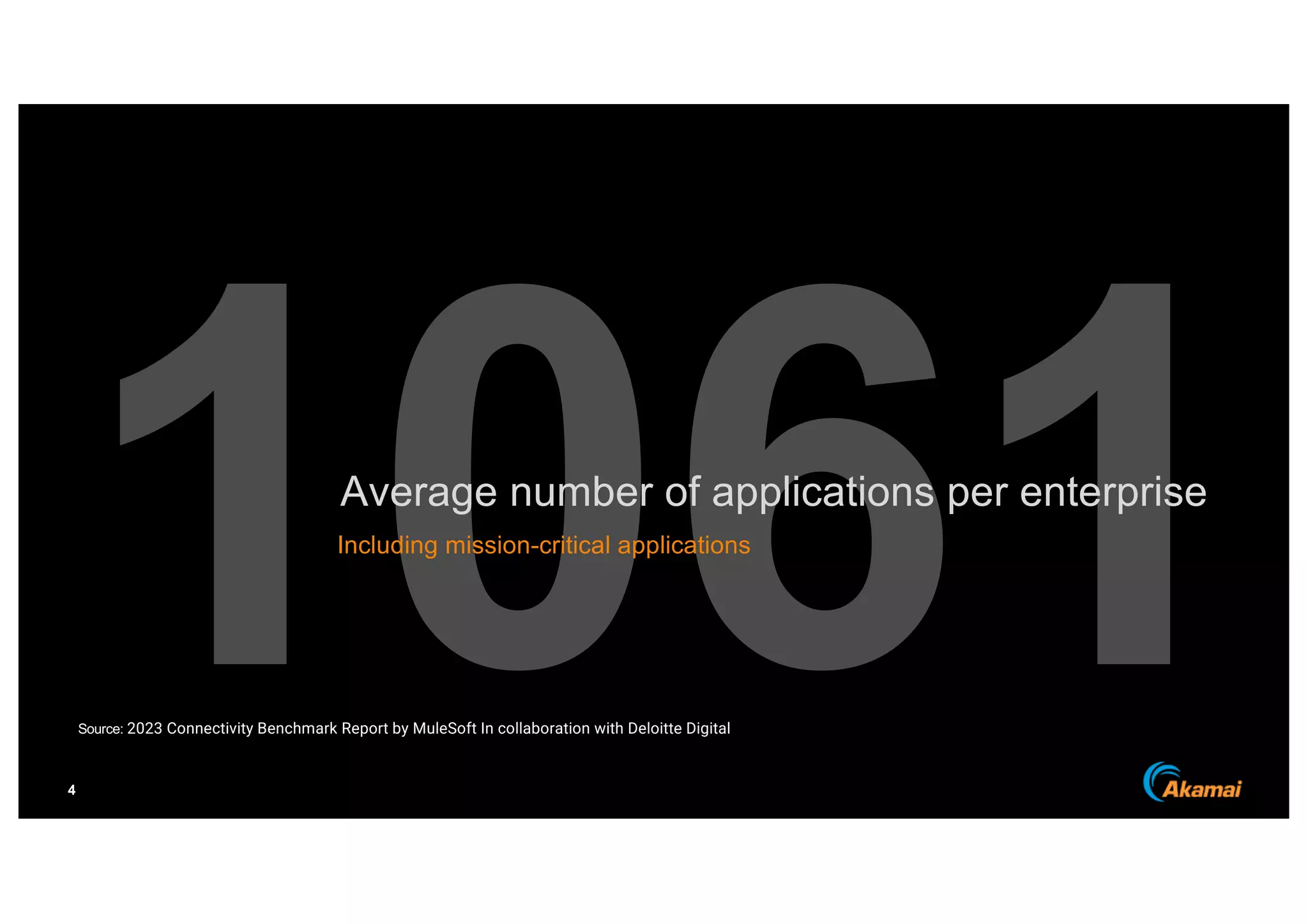
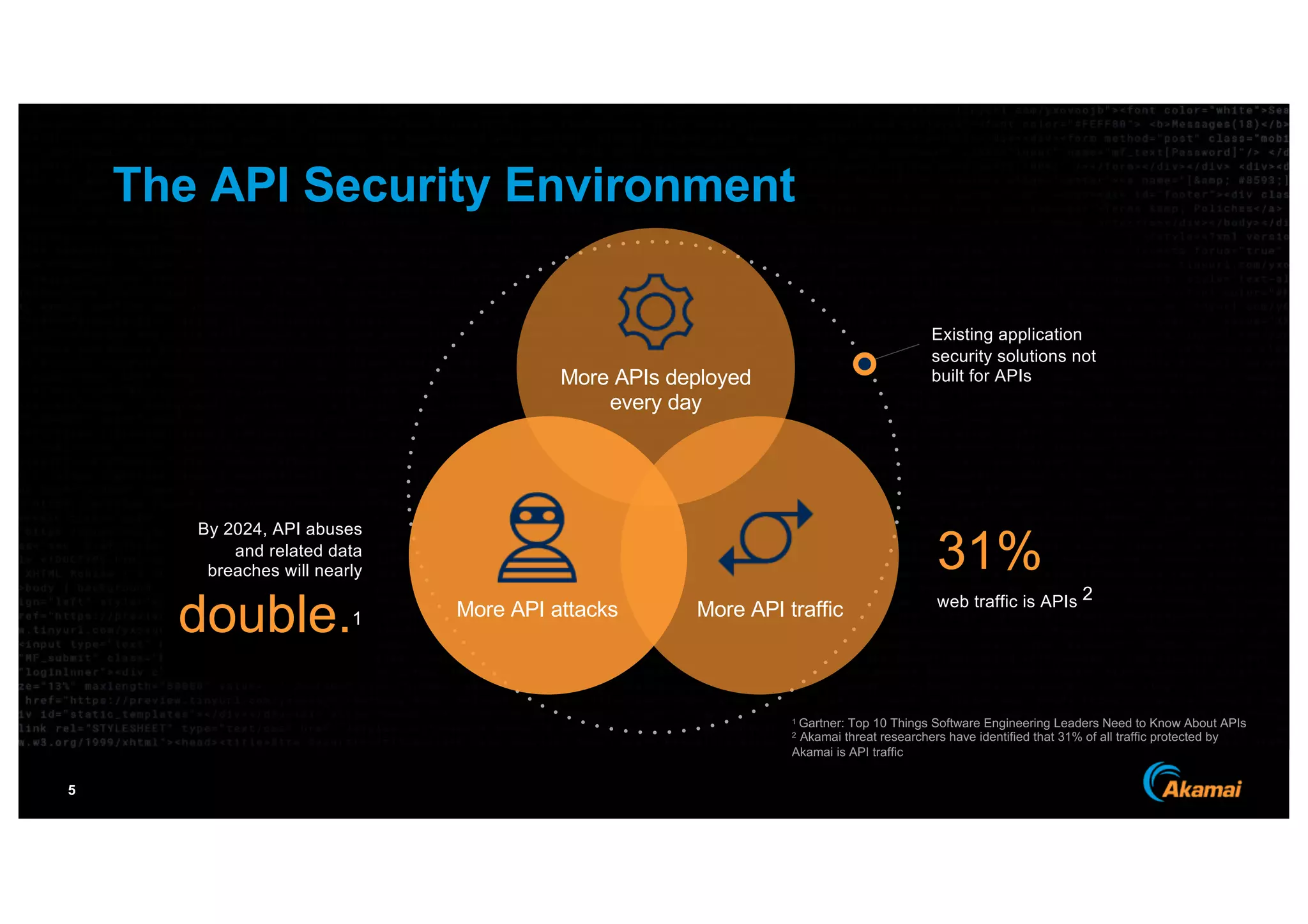
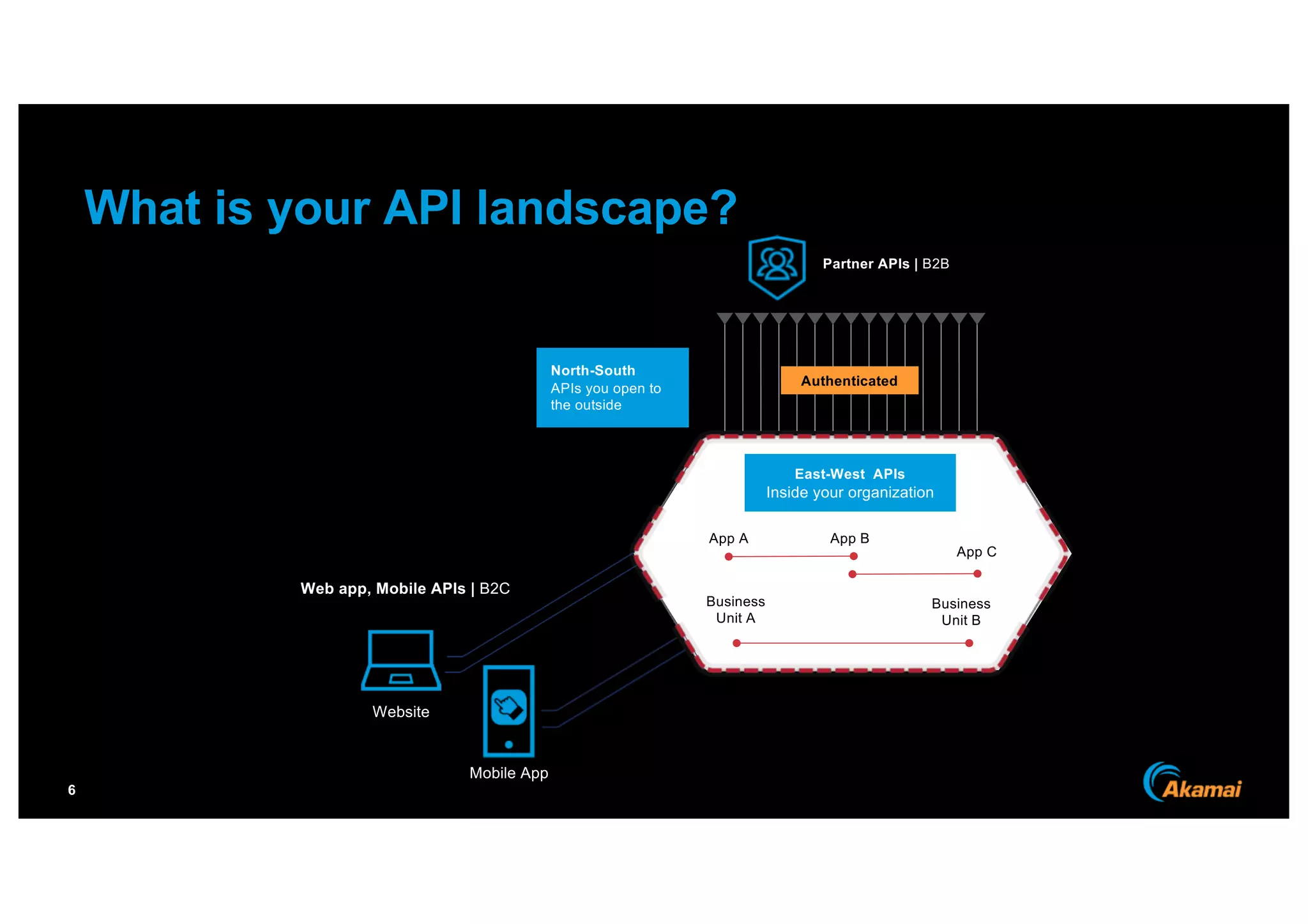
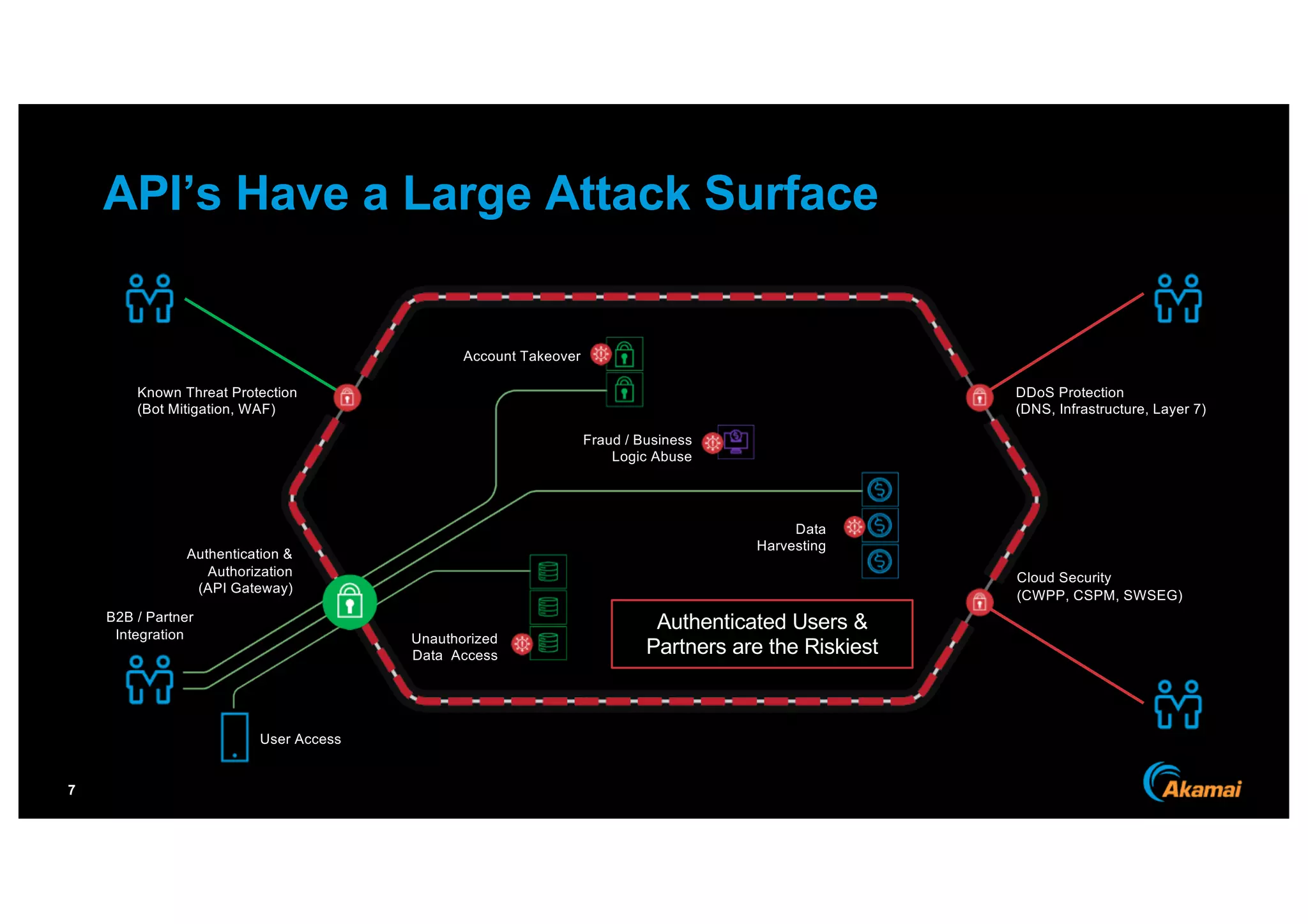
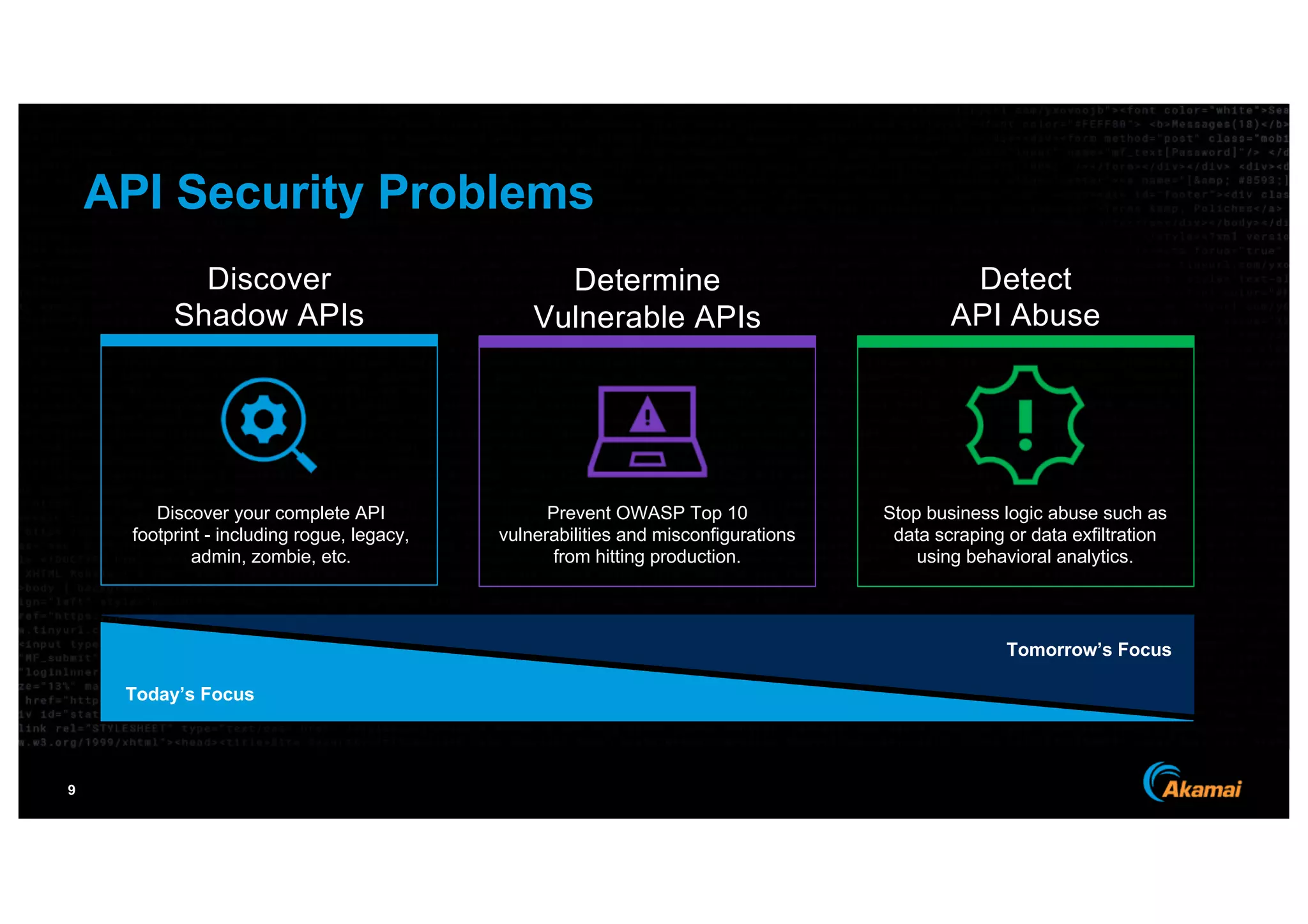
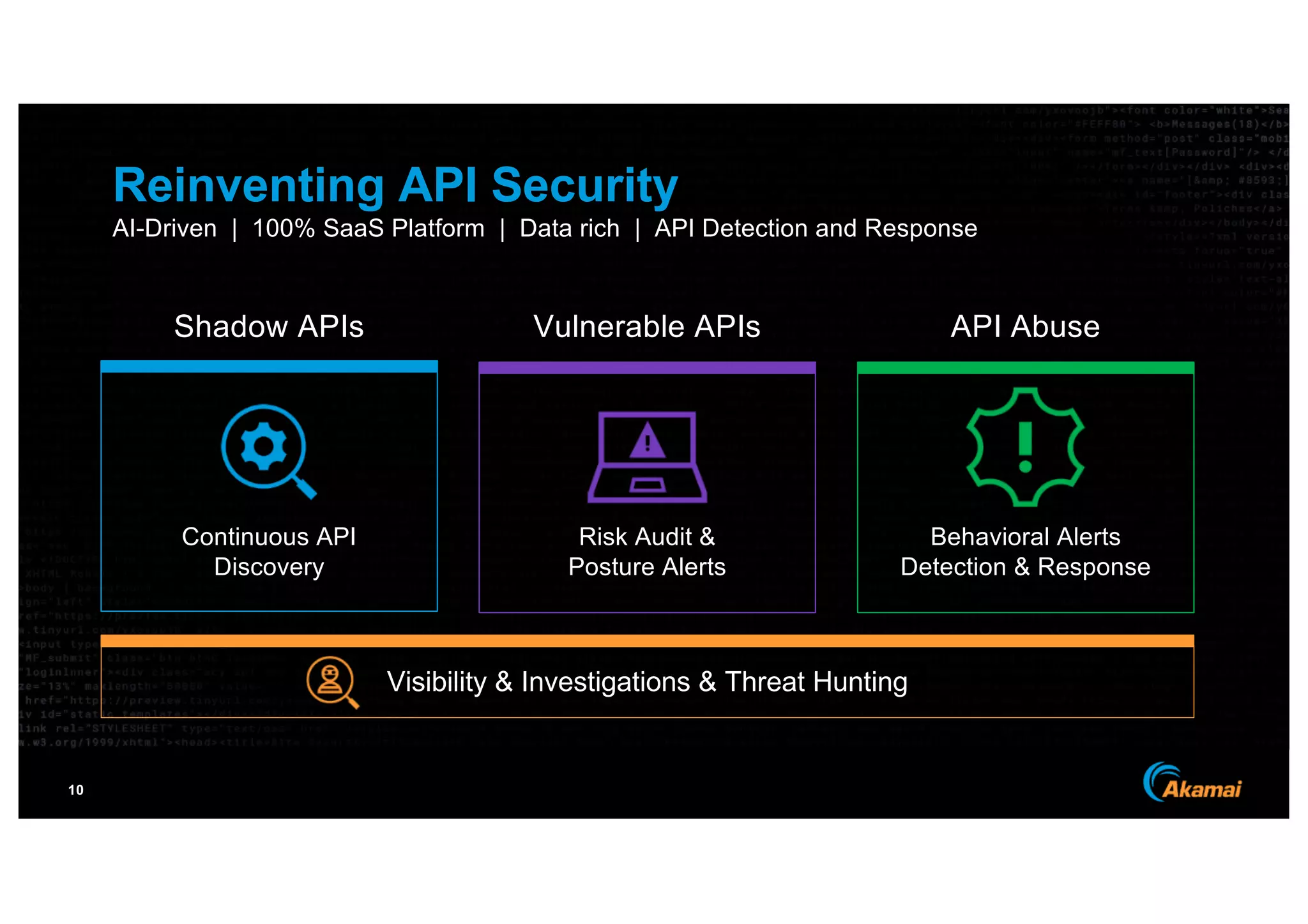
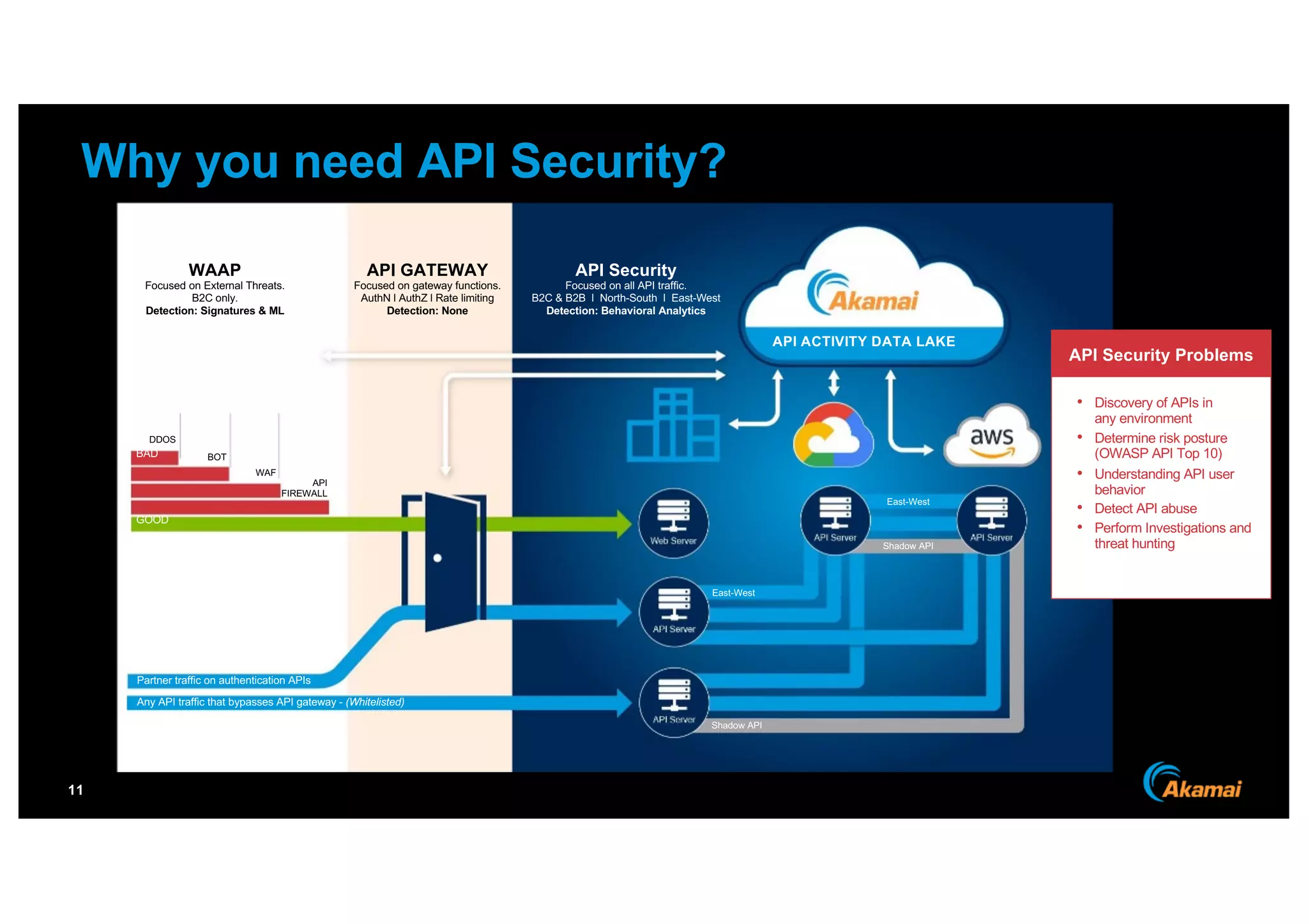
The document discusses the growing prevalence of APIs in enterprises, highlighting security concerns as API traffic increases and vulnerabilities are expected to double by 2024. It outlines the attack surface of APIs, mentioning existing security solutions are inadequate for the unique challenges posed by APIs. Key recommendations include employing behavioral analytics for threat detection and improving API security frameworks to address vulnerabilities effectively.