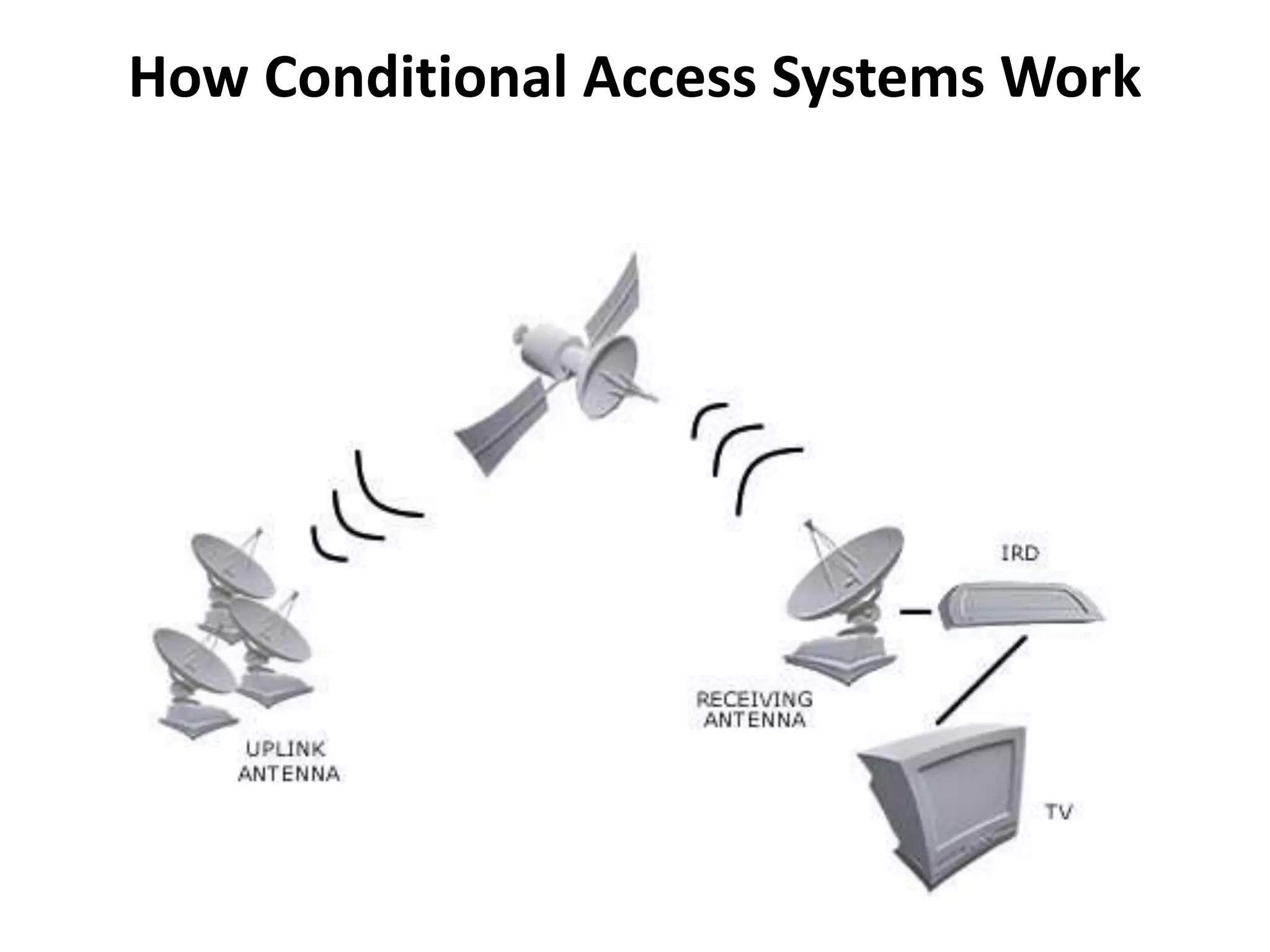
The document discusses Conditional Access (CA) systems, which use scrambling and encryption to prevent unauthorized access to digital content. It outlines their functionality, applications in pay-per-view and service restriction, as well as advantages such as seamless operation and protecting purchased content. Additionally, it provides models to help understand and evaluate CA systems for future digital video broadcasting services.