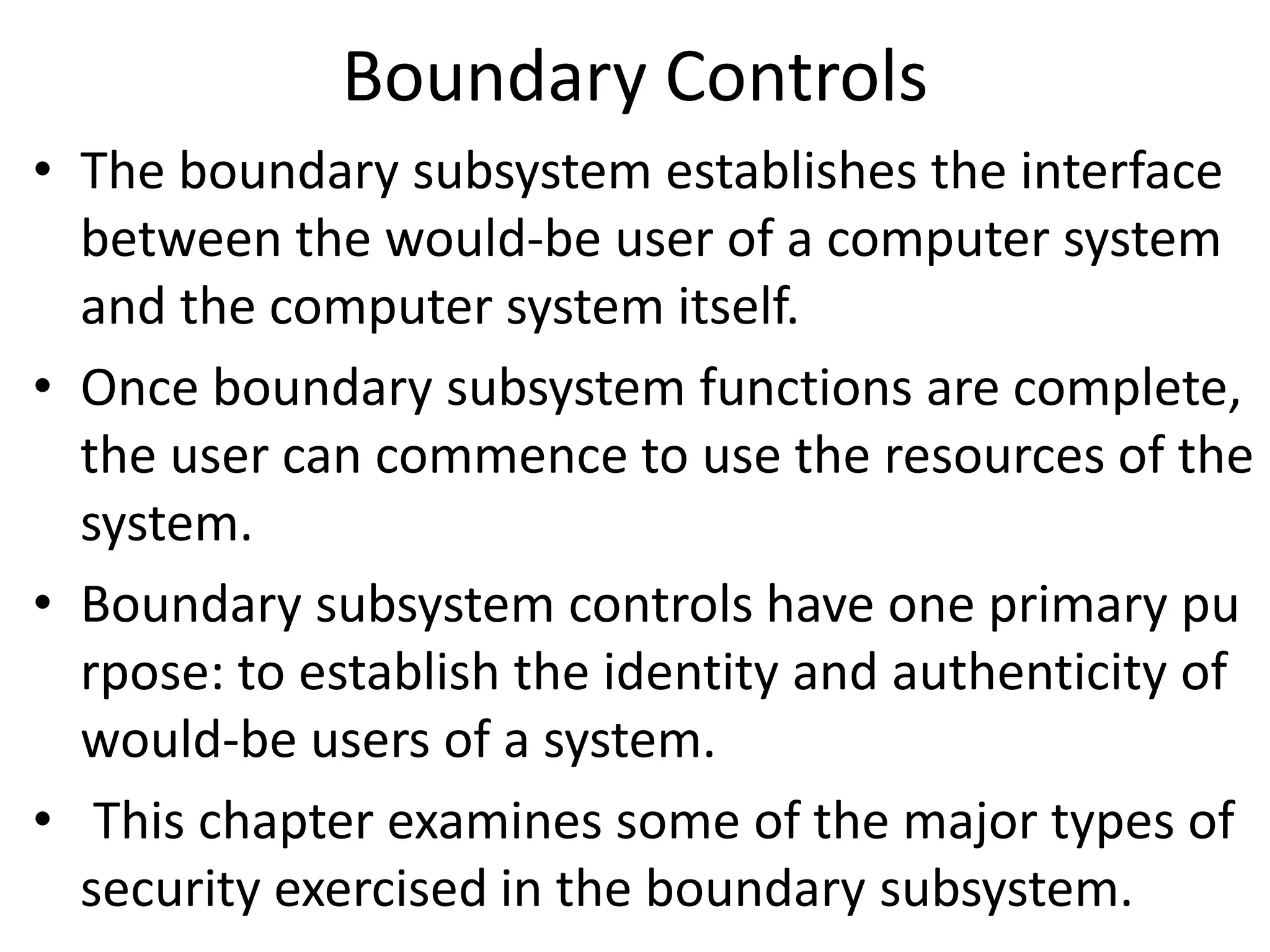
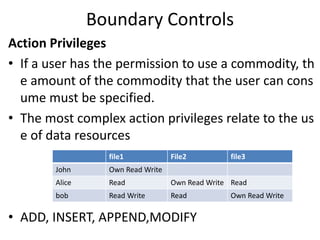
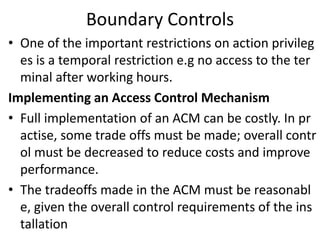
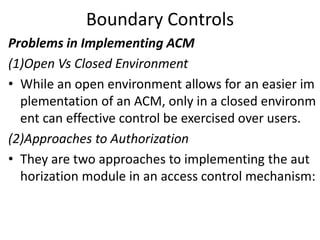
The document discusses boundary controls and access control mechanisms. It describes how boundary controls establish the interface between users and computer systems by authenticating users' identities. It then examines different types of access controls, including identification, authentication, authorization of users and resources. It discusses implementing access control mechanisms and challenges around open vs closed environments, authorization approaches, and dynamics of authorization. It also covers cryptographic controls like encryption techniques, choosing cipher systems, key distribution, and digital signatures.









![Boundary Controls
Secret Message
• S Pur(m)
• R Prr[Pur(m)]
Signed Secret Message
• S Pur(m)
• S Prs[Pur(m)]
• R Pus (Prs[Pur(m)])
• R Prr[Pur(m)]](https://image.slidesharecdn.com/boundarysecurity-230607120013-a3254632/85/boundary_security-pptx-18-320.jpg)