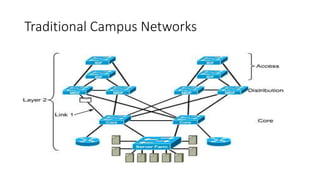
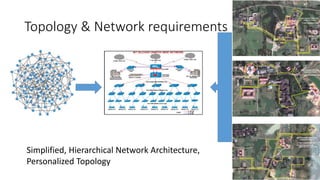
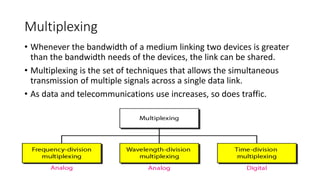
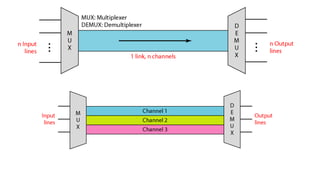
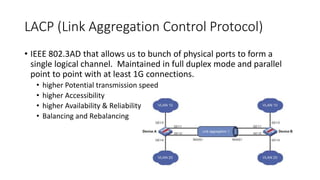
This document discusses enterprise campus networks and presents alternatives to traditional campus network designs. It outlines challenges with complex campus networks including availability, performance, security, and managing bandwidth utilization and prioritized traffic. It proposes a simplified, hierarchical network architecture and discusses supporting techniques like LACP, VLANs, STP, firewalls, and VPNs to improve security, availability, and traffic management. The conclusion advocates for alternative personalized approaches to campus networks that can efficiently meet requirements while maintaining security, performance, and compliance with administrative policies.