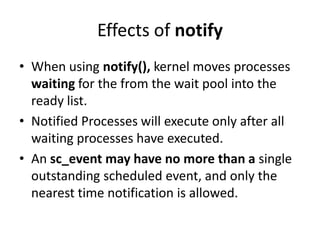
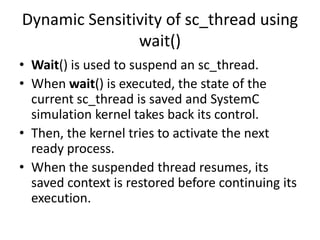
This document discusses concurrency in SystemC simulations. It explains that SystemC uses events and processes to model concurrent systems. There are two main types of processes: threads and methods. Threads can wait for events using wait() and methods use next_trigger() to establish dynamic sensitivity. Events have no duration and are used to trigger processes. Notifying an event using notify() moves waiting processes to the ready queue. The SystemC kernel is event-driven and executes ready processes in non-deterministic order.



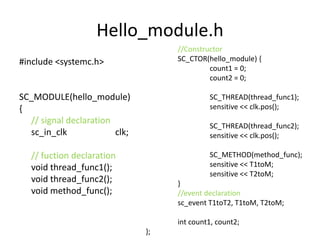
![Simplified Simulation Kernel
[From SystemC From the Groud Up]](https://image.slidesharecdn.com/concurrency2010-131015115322-phpapp01/85/Concurrency-2010-4-320.jpg)

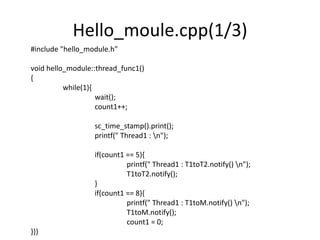
![Process execution and Event Pools
[From SystemC From the Groud Up]](https://image.slidesharecdn.com/concurrency2010-131015115322-phpapp01/85/Concurrency-2010-6-320.jpg)





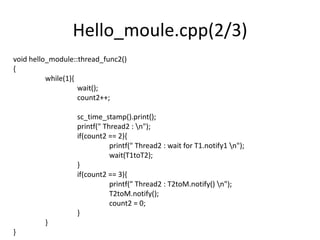
![Simulation Scenarios in Different
Perspects
User Perceives
Actual in SystemC Kernel
[From SystemC From the Groud Up]](https://image.slidesharecdn.com/concurrency2010-131015115322-phpapp01/85/Concurrency-2010-14-320.jpg)




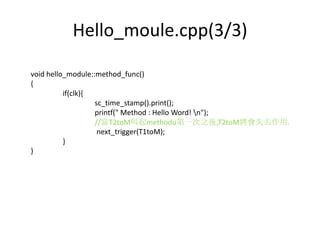
![Static Sensitivity
• Static sensitivity is established during the elaboration
stage and cannot be changed once it is established.
• It applies to the most recent process registration. It is
used when processes are handled for certain fixed
events without implementing the related codes in the
processes bodies.
• Thread: wait();// static sensitivity
• Method: next_trigger();// static sensitivity
• Syntax:
– sensitive << name_of_event1 [<< name_of_event2];
– sensitive (name_of_event, …);](https://image.slidesharecdn.com/concurrency2010-131015115322-phpapp01/85/Concurrency-2010-20-320.jpg)

![Main.cpp
#include <systemc.h>
#include "hello_module.h"
int sc_main(int argc, char* argv[])
{
// signal declaration
sc_clock
clk("clk", 10, SC_NS, 0.5);
// module declaration
hello_module
module0("hello_word");
// signal connection
module0.clk(clk);
// run simulation
sc_start(1000, SC_NS);
return 0;
}](https://image.slidesharecdn.com/concurrency2010-131015115322-phpapp01/85/Concurrency-2010-22-320.jpg)