Embed presentation
Downloaded 60 times








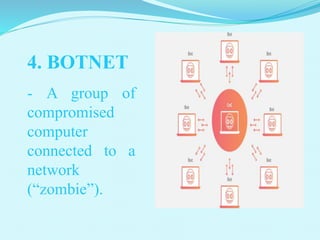
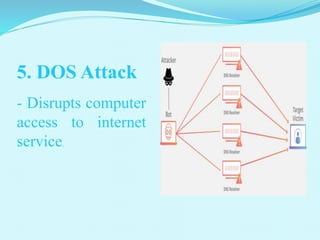

This document discusses five main internet threats: malware, spam, phishing, botnets, and DOS attacks. Malware includes viruses, worms, trojans, spyware, and adware which can replicate and spread between computers through various means to access users' information or monitor their activities without consent. Spam involves unwanted emails, often containing malware, from bots or advertisers. Phishing tricks users into providing private details like passwords or financial information. Botnets are networks of compromised computers controlled remotely. DOS attacks disrupt access to internet services.












