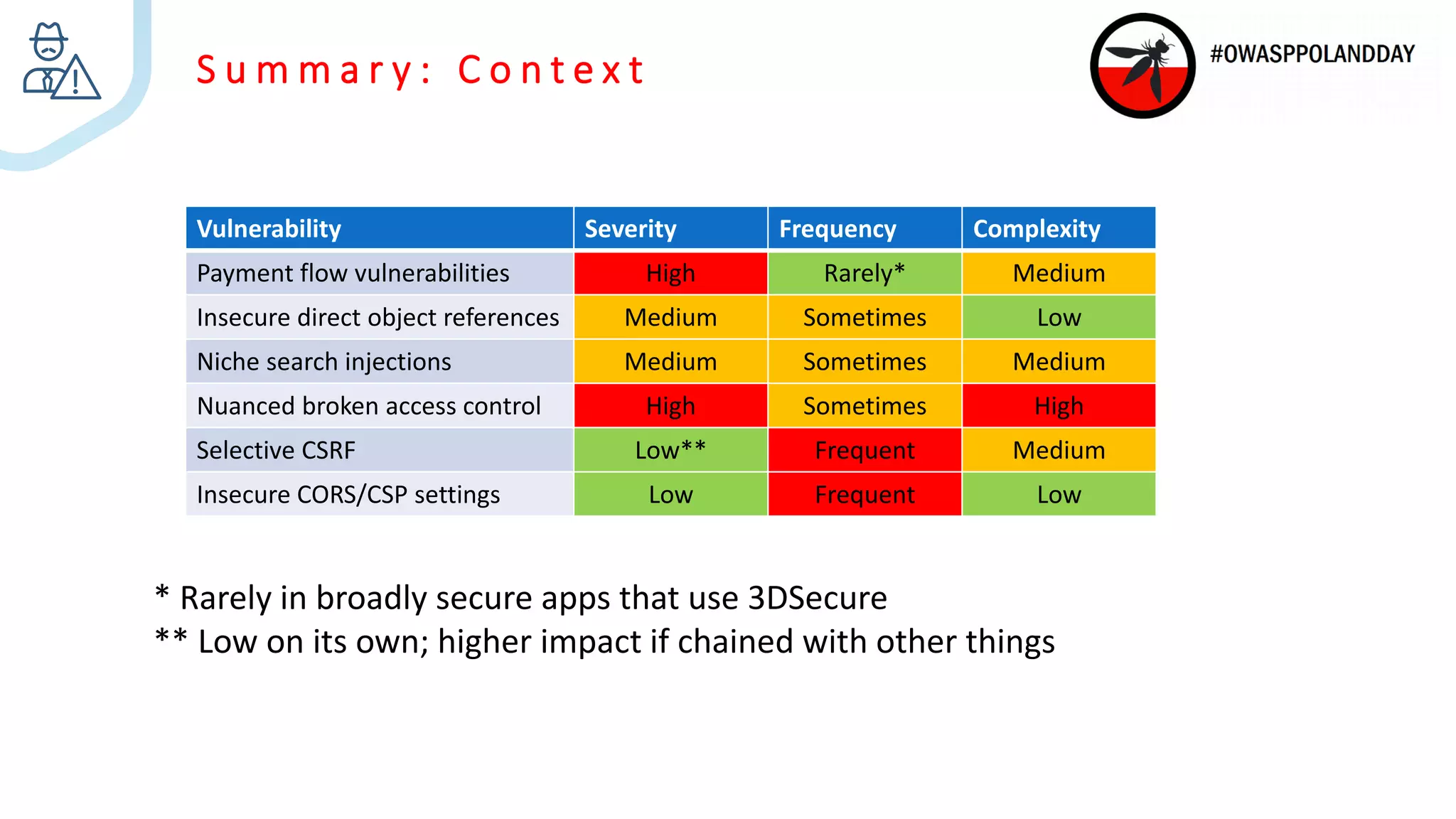
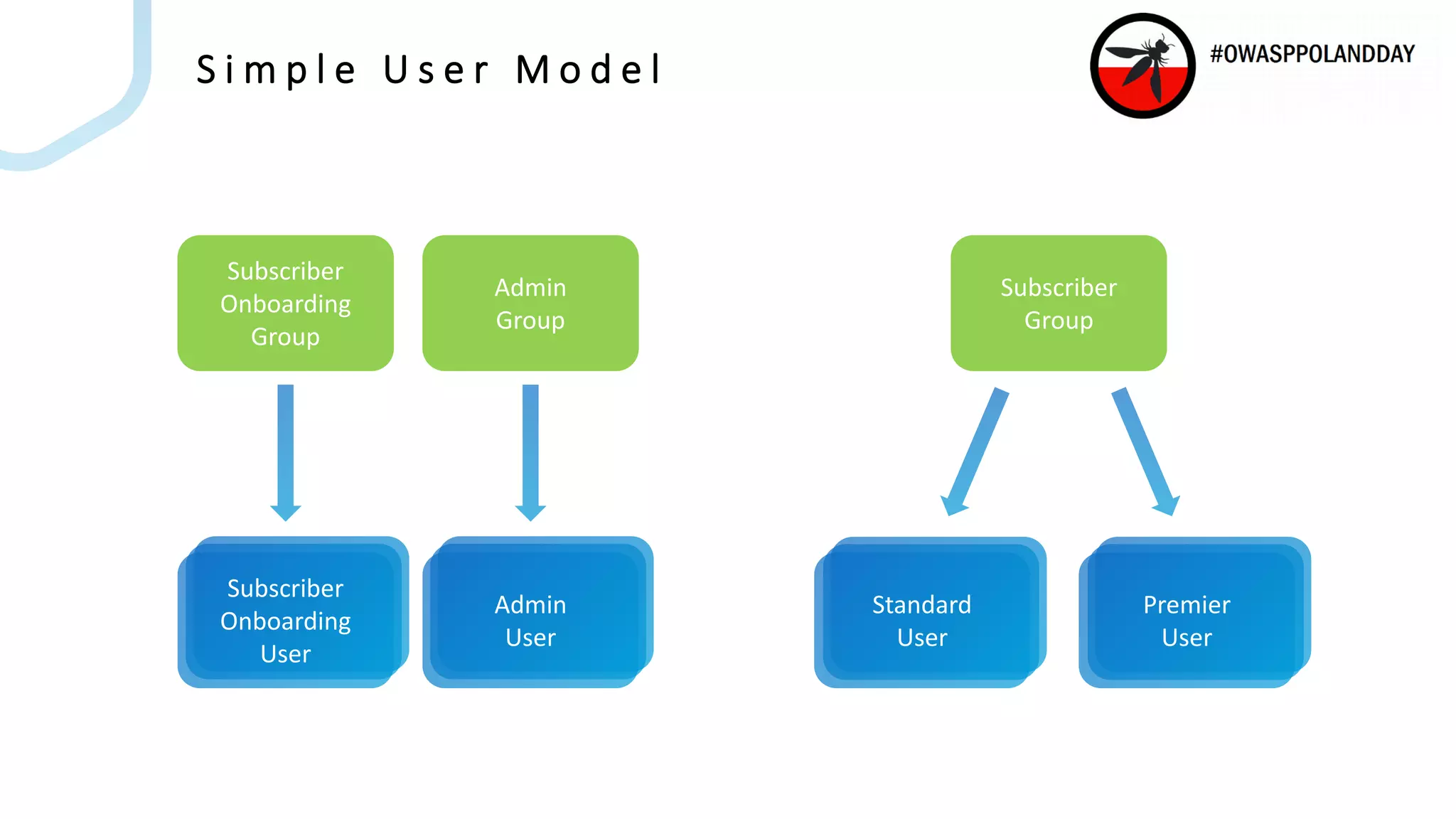
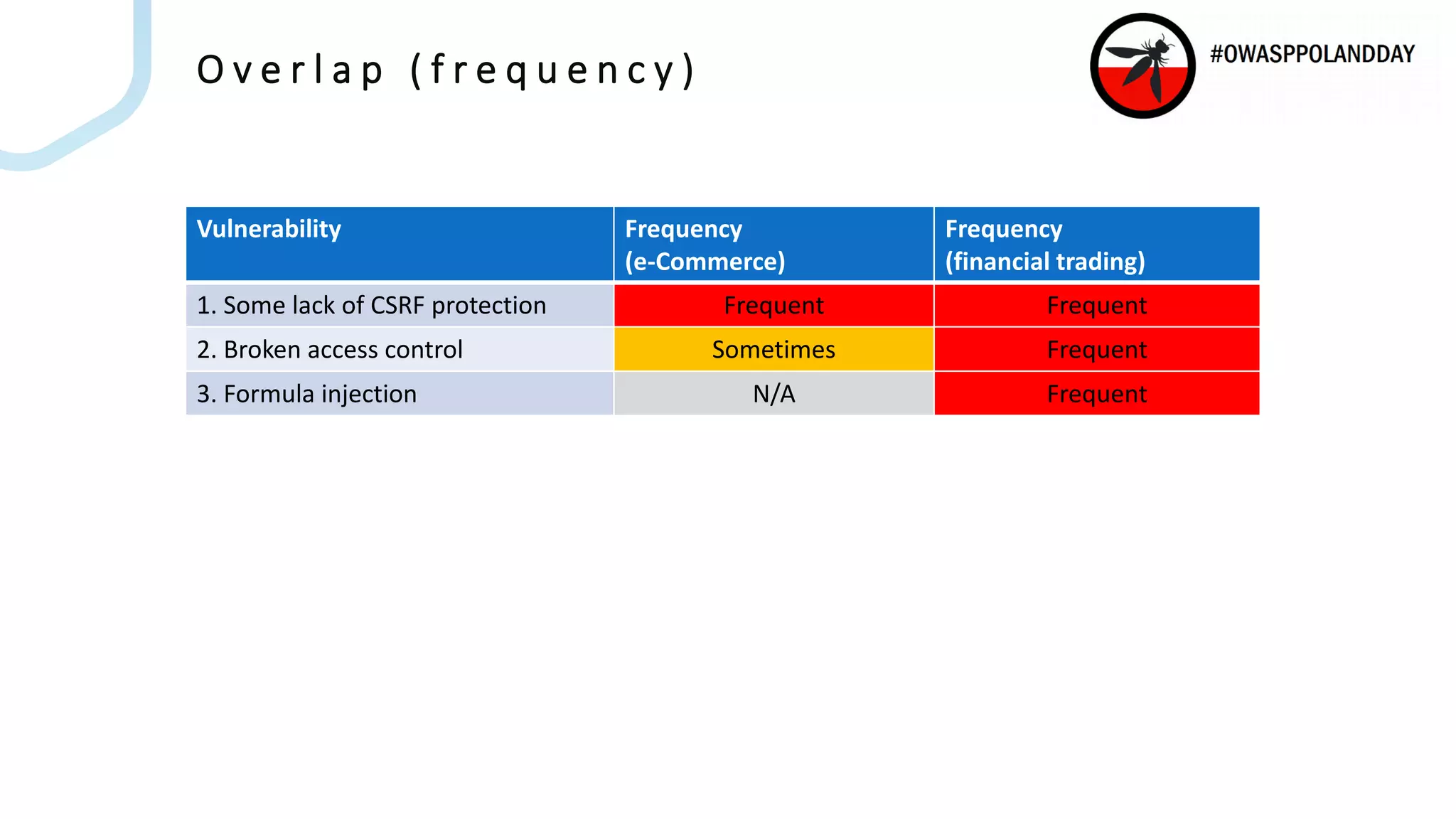
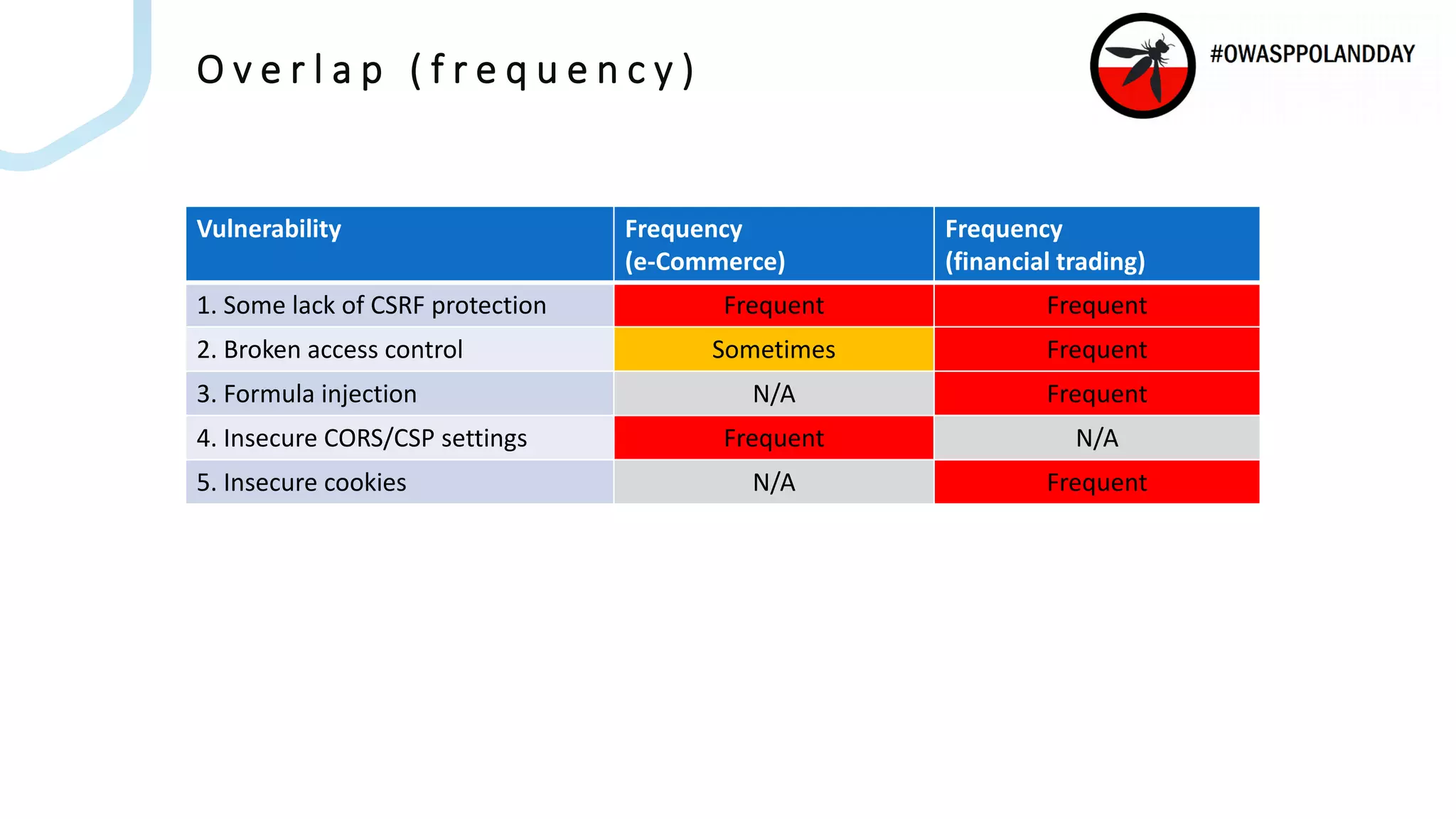
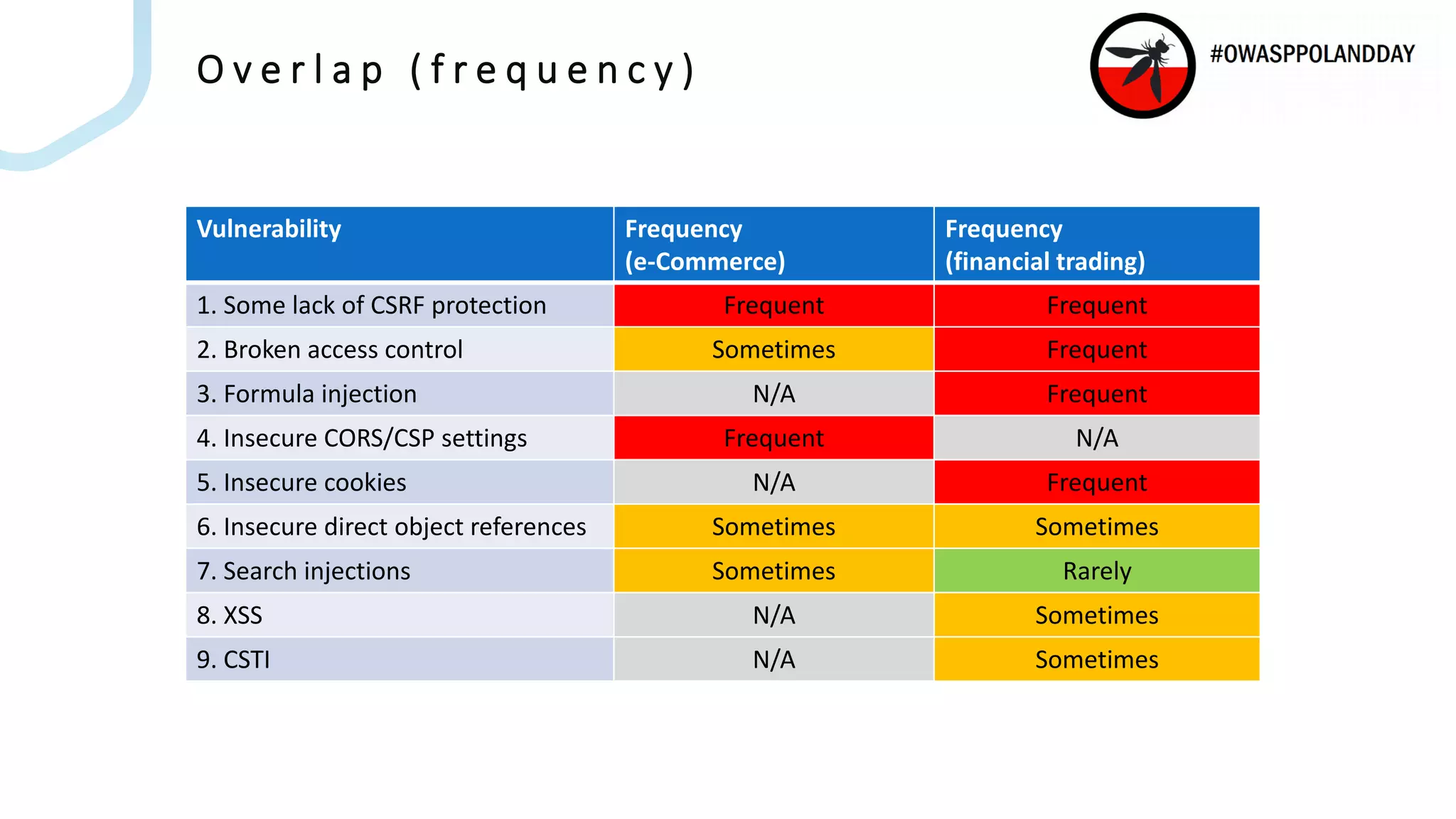
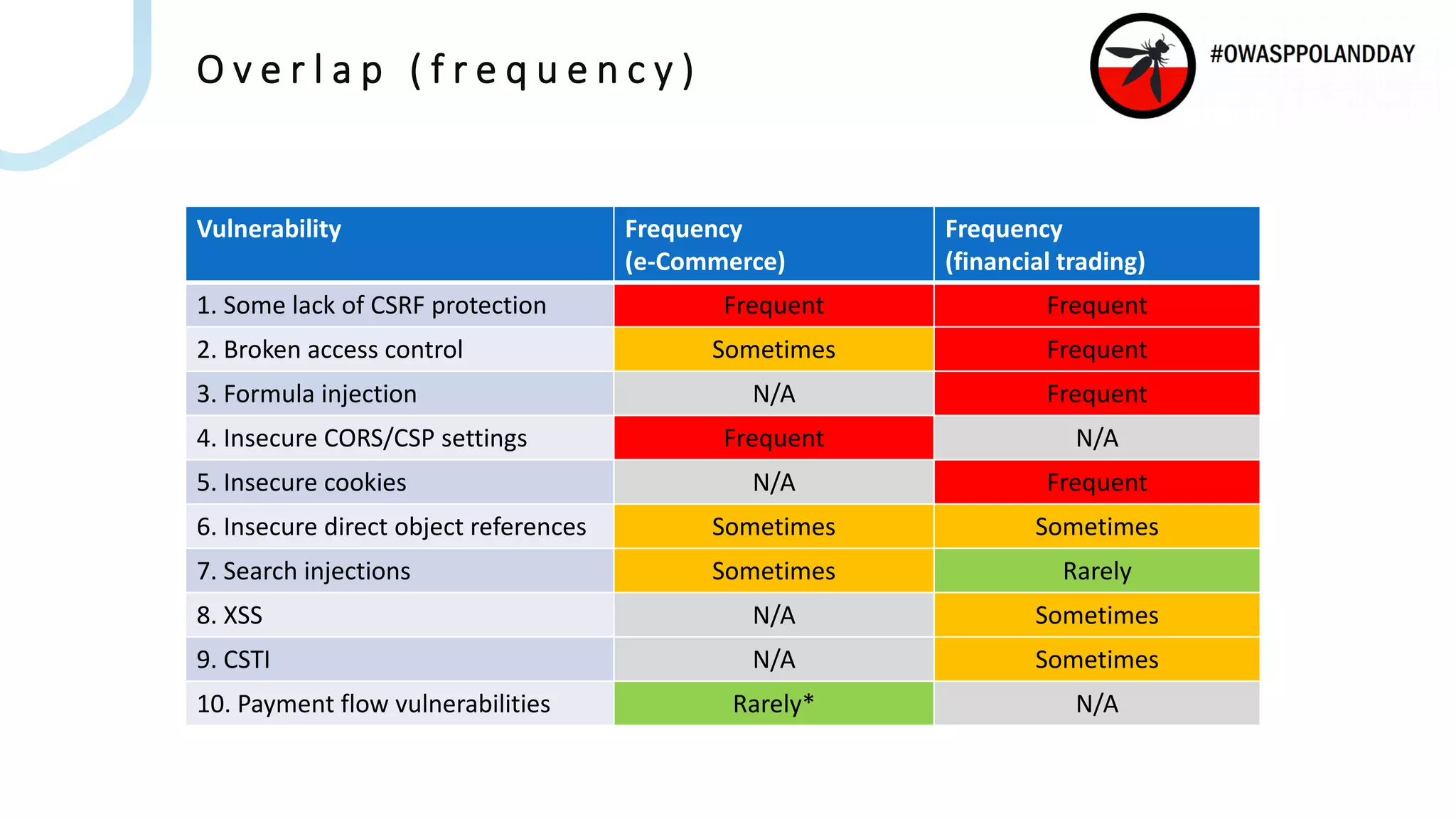
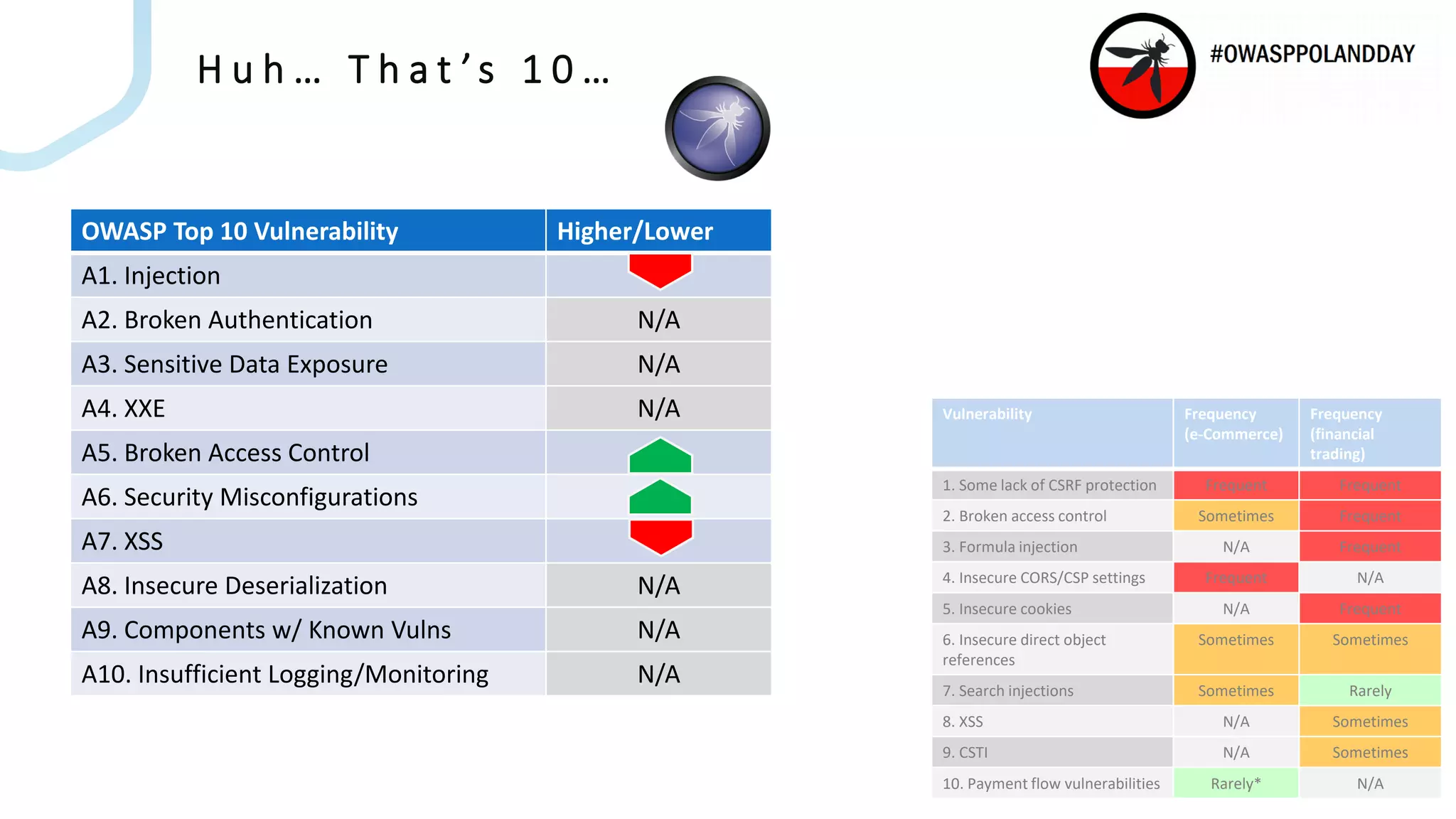
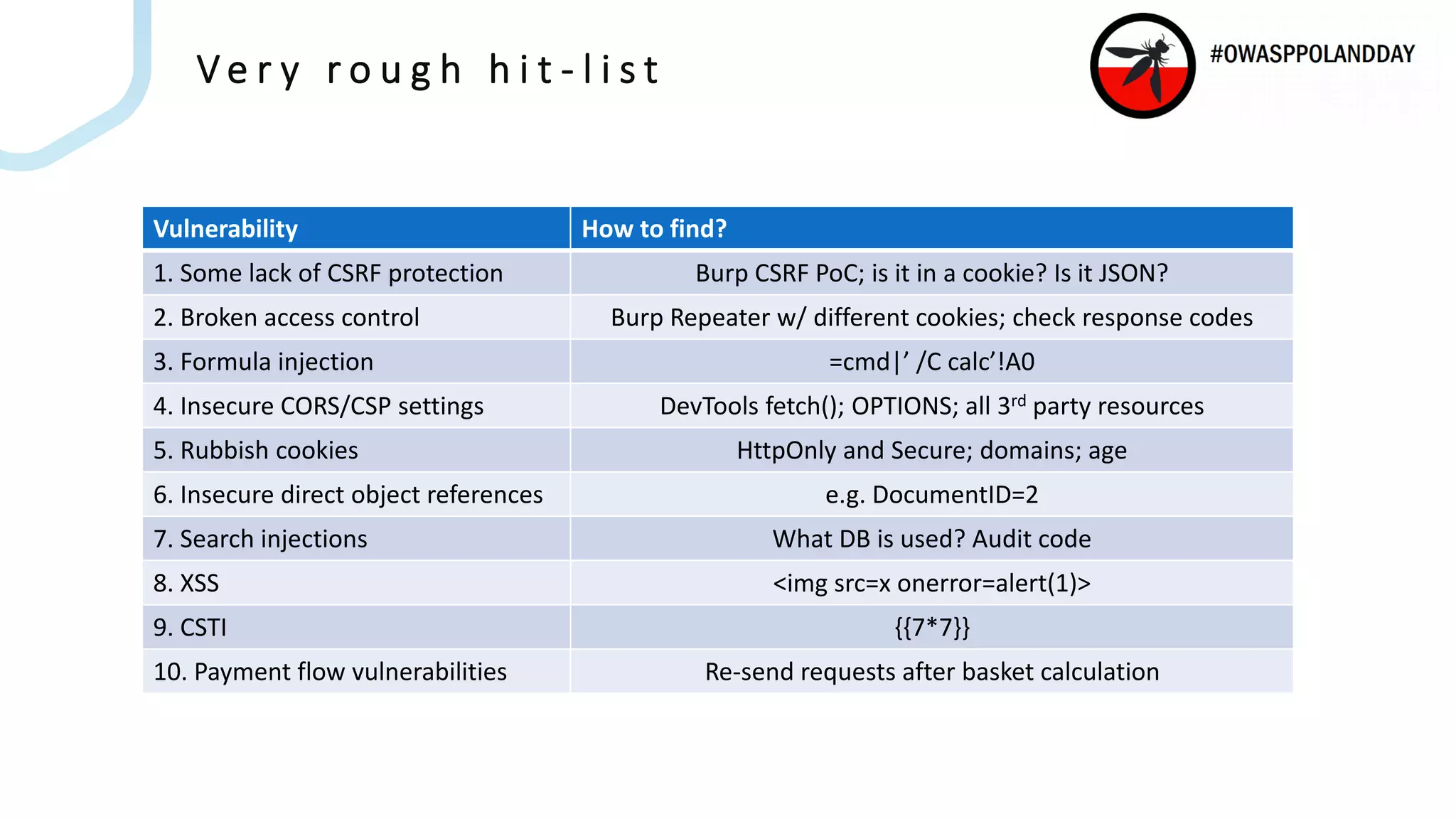
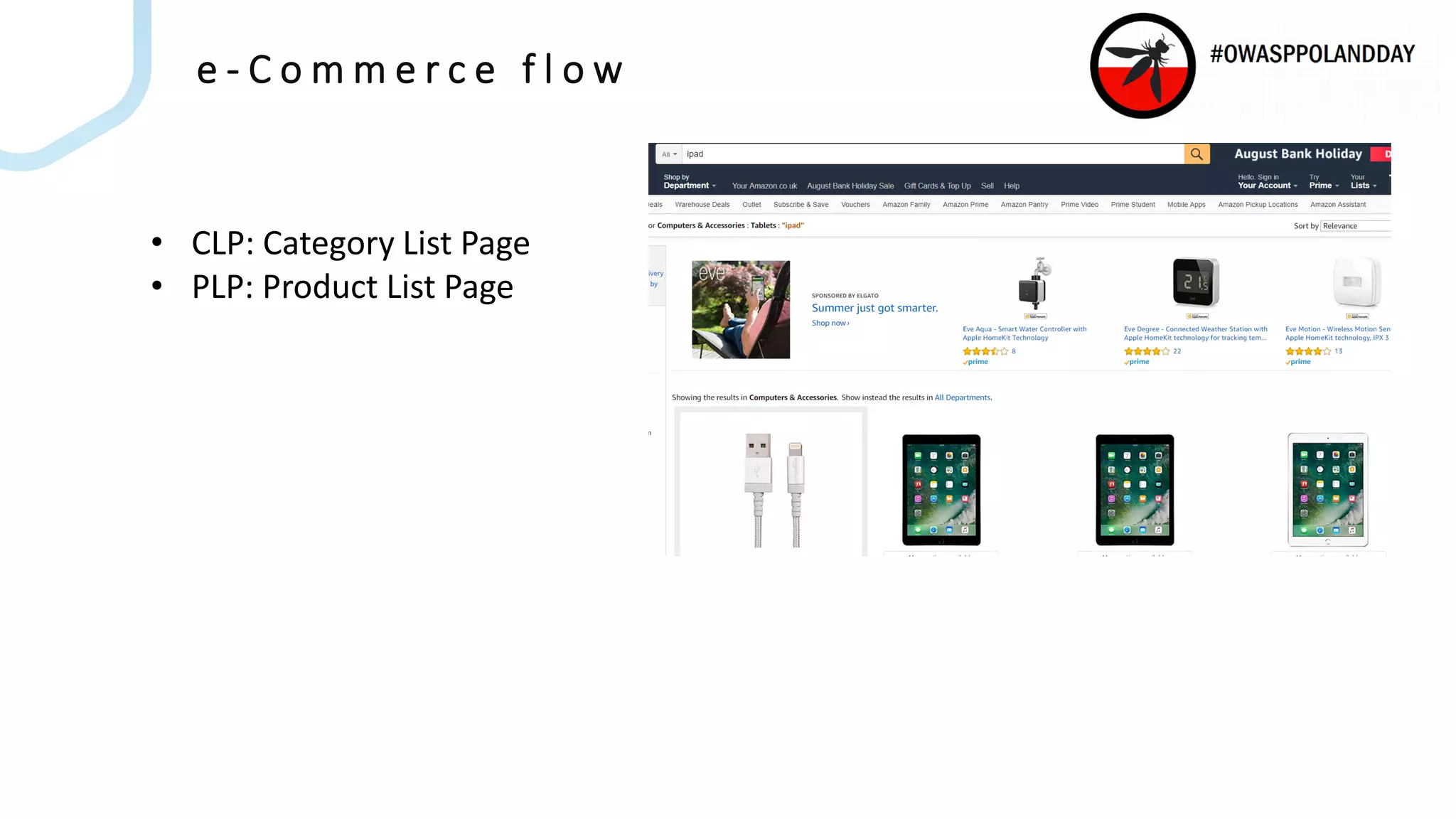
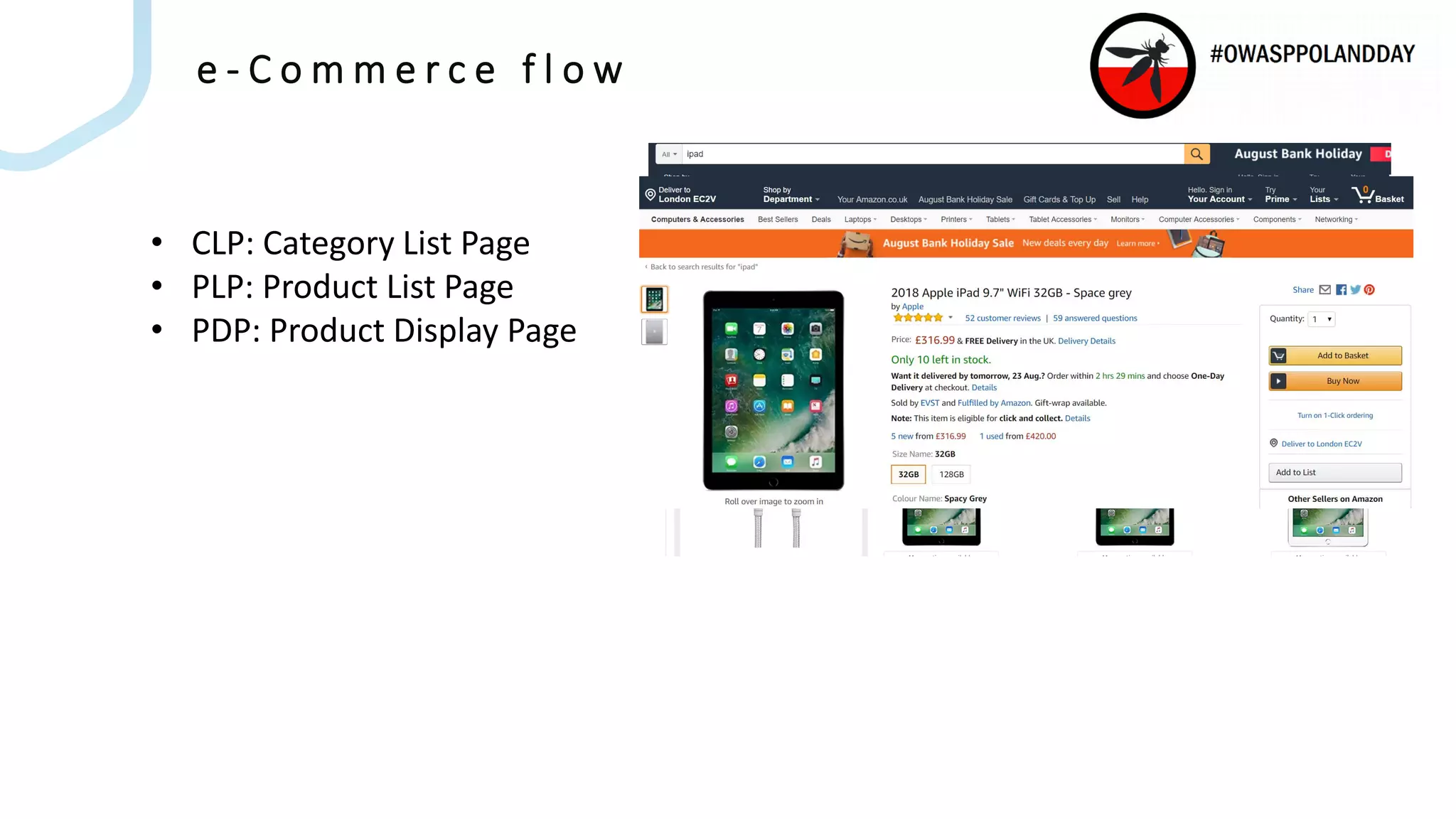
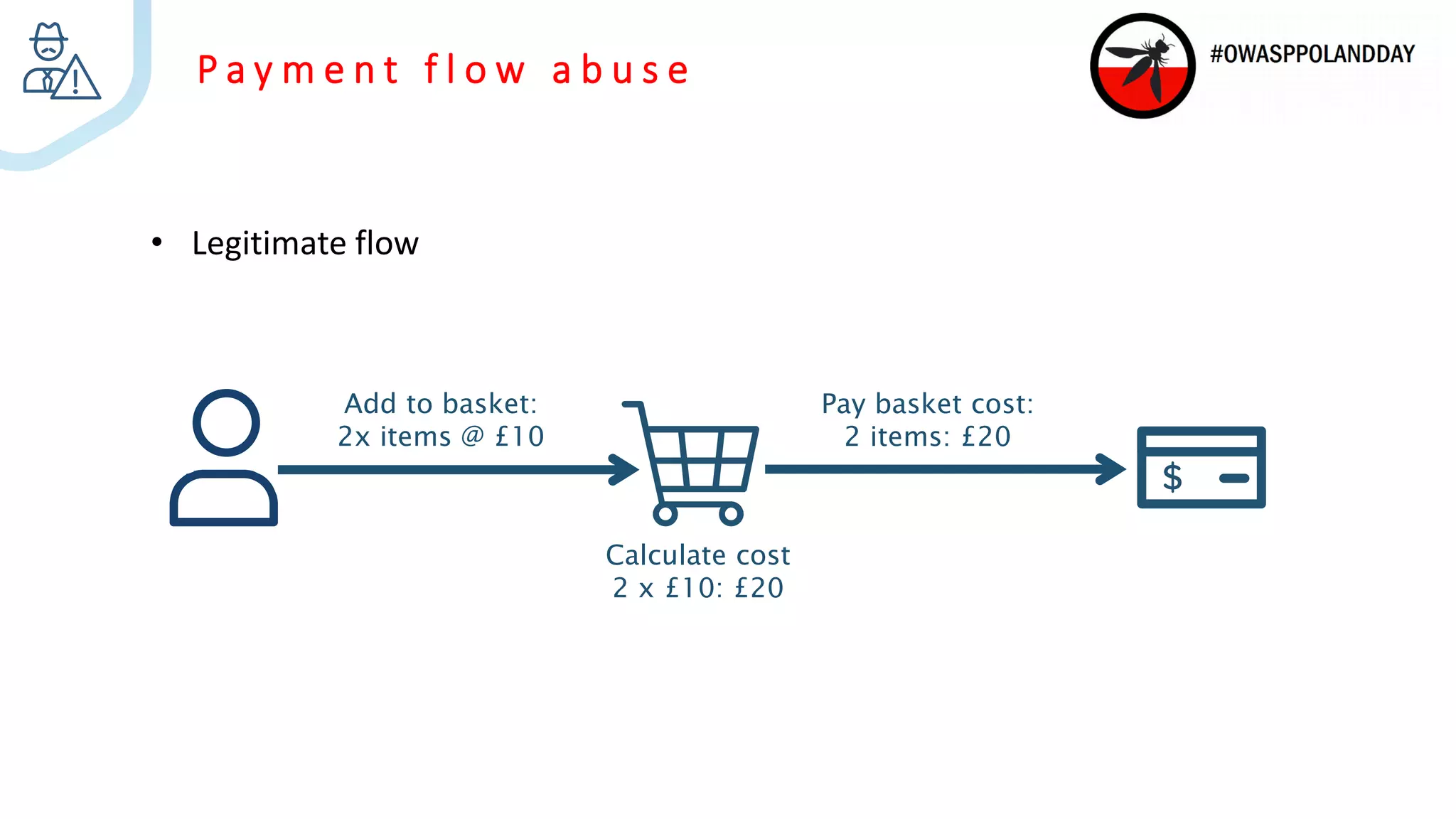
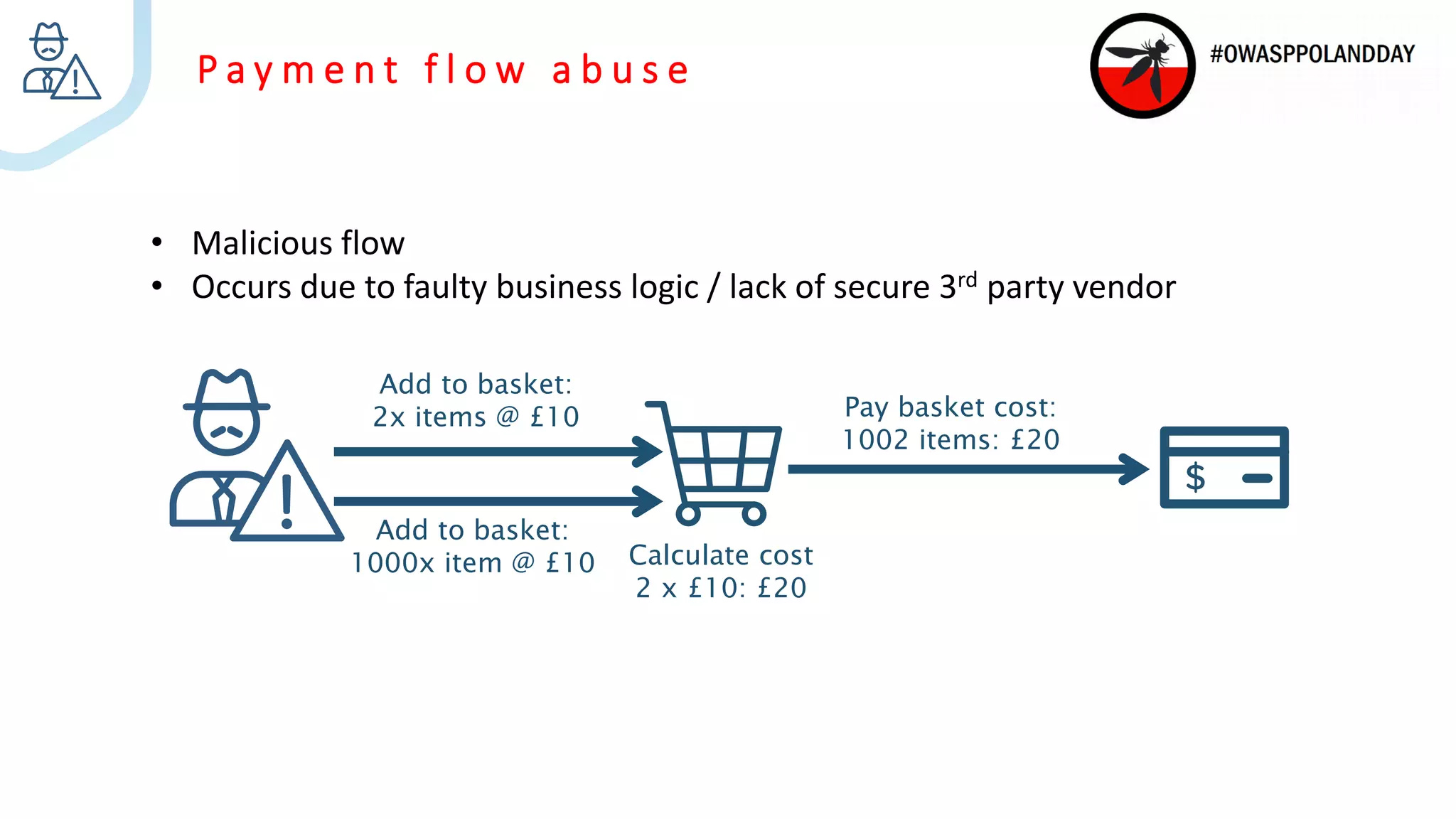
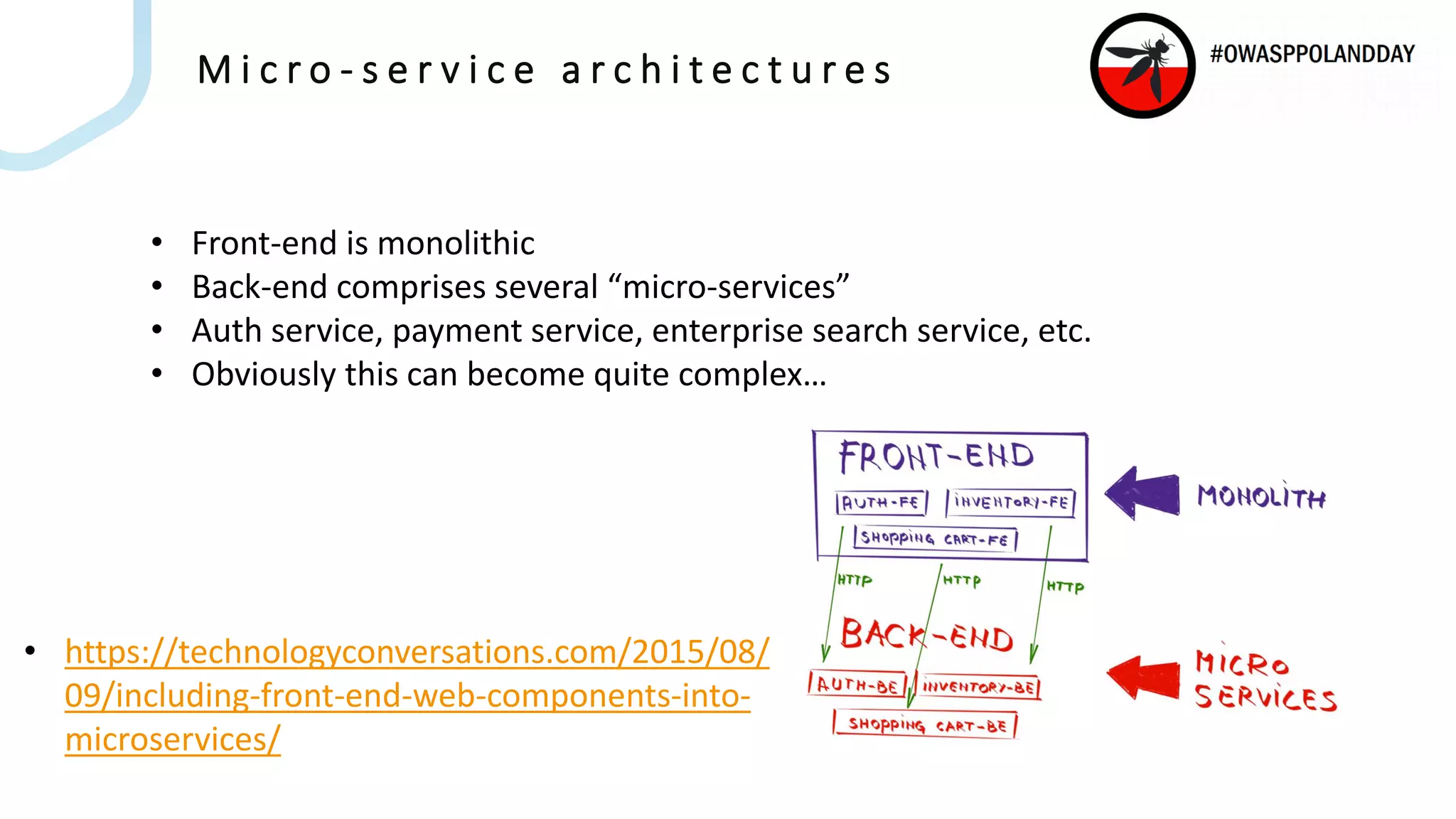
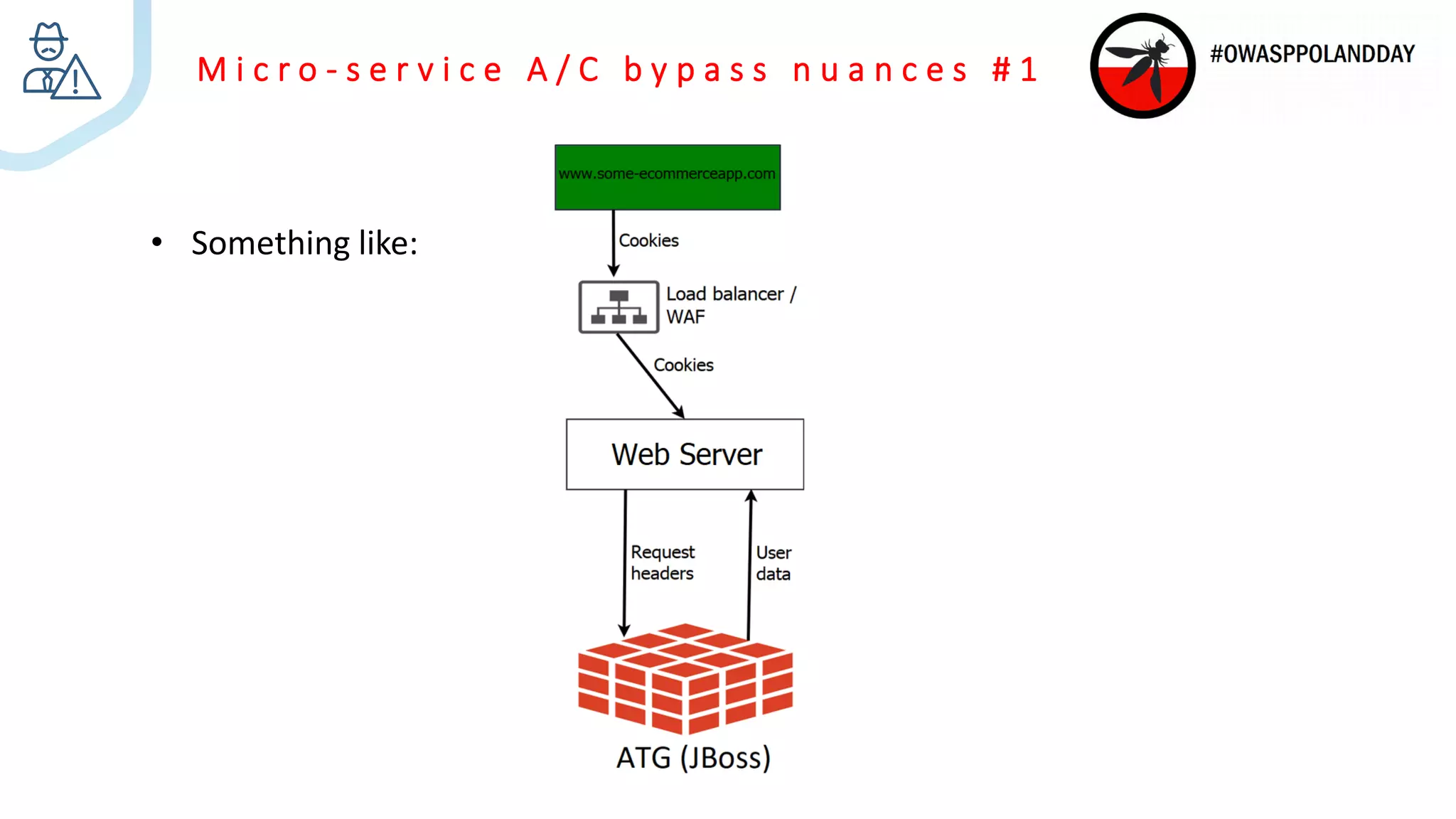
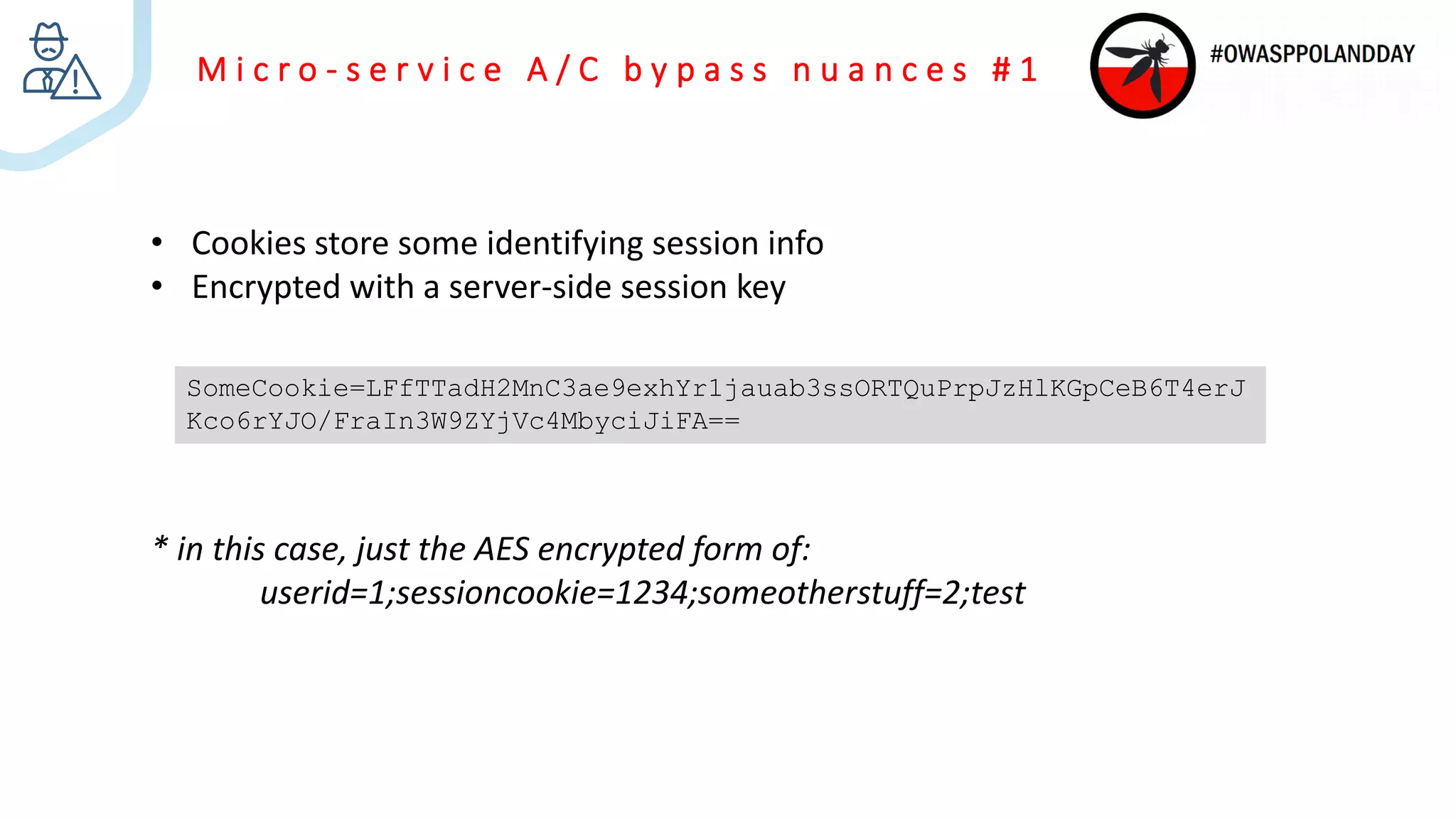
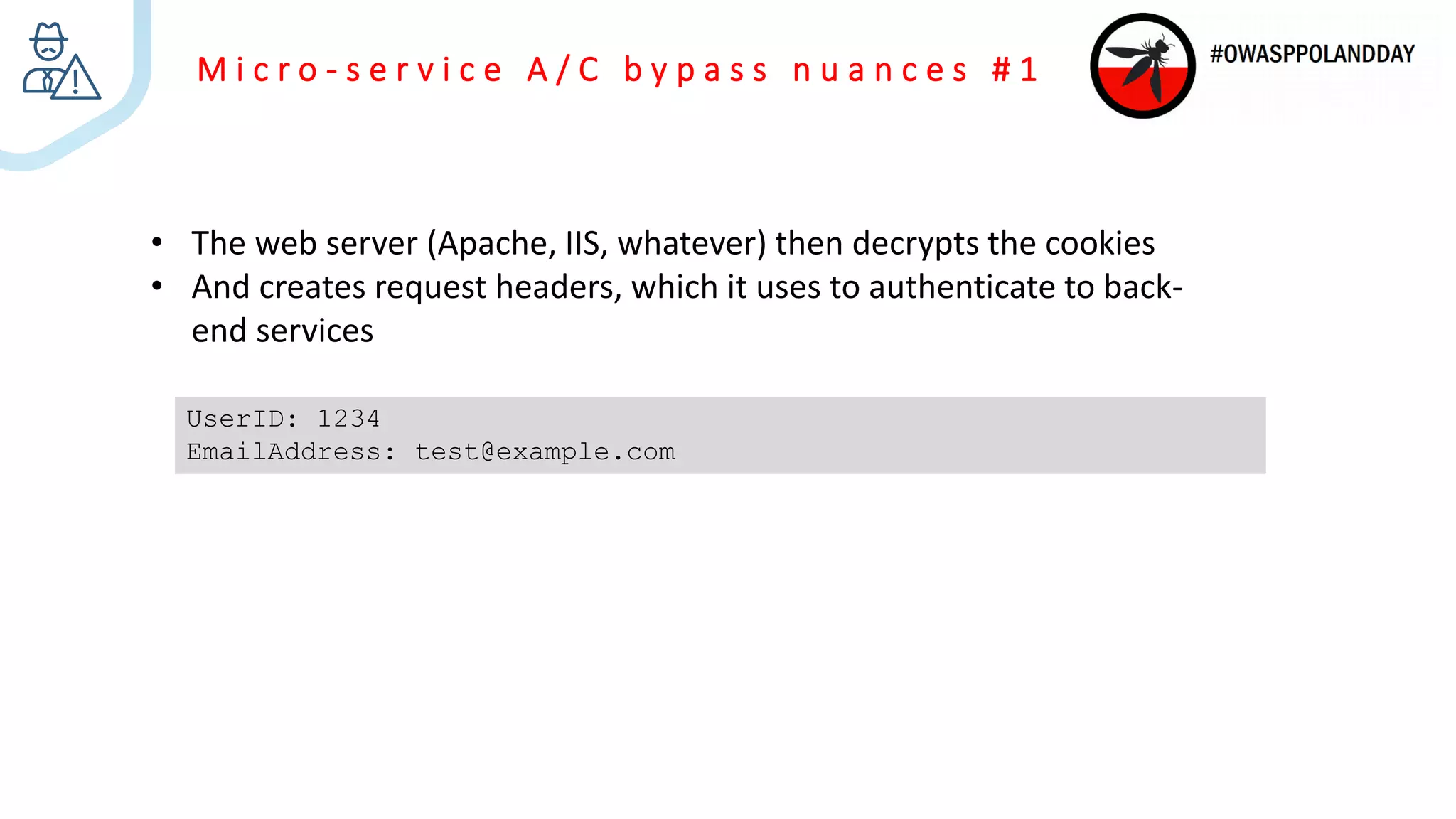
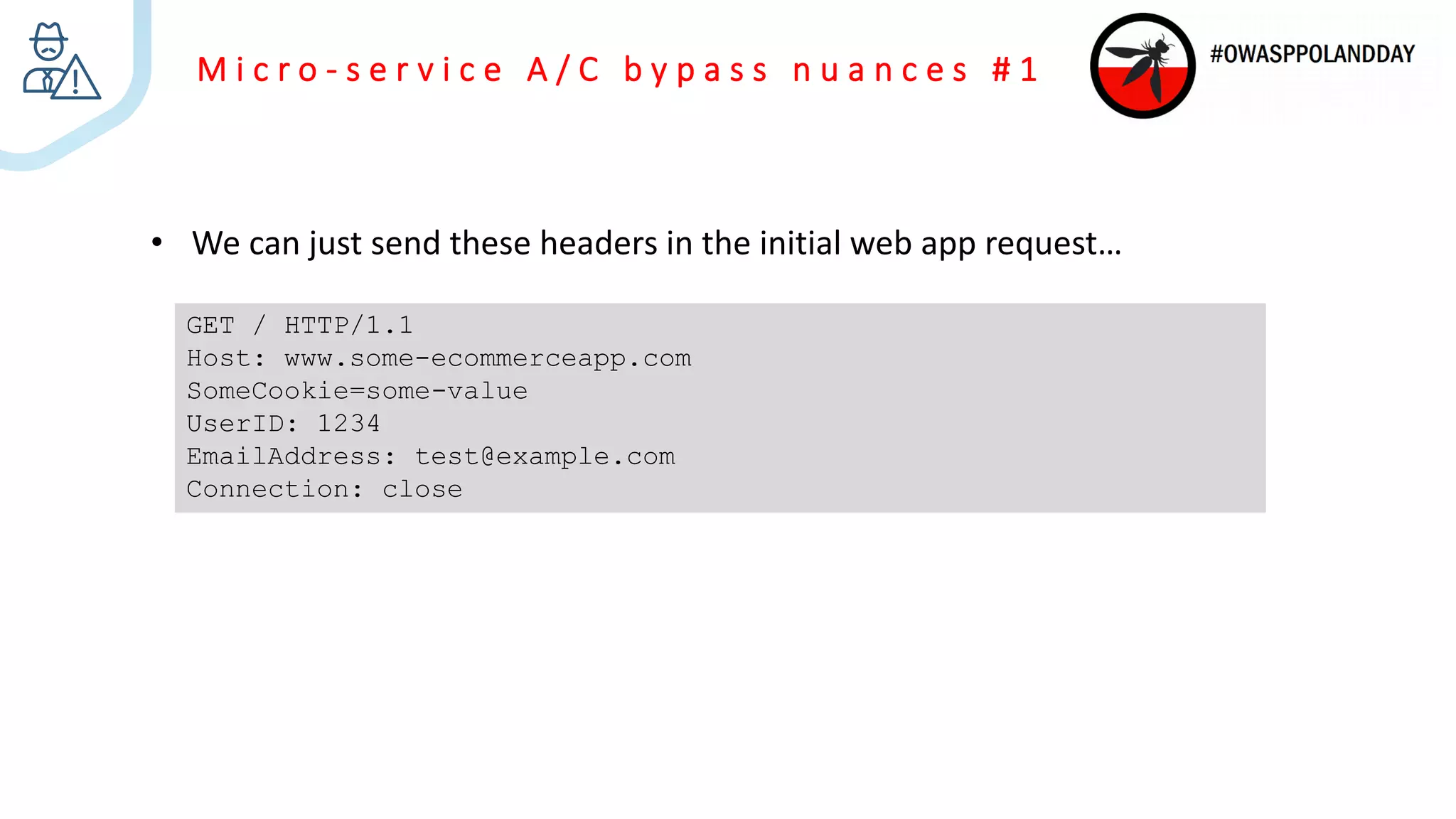
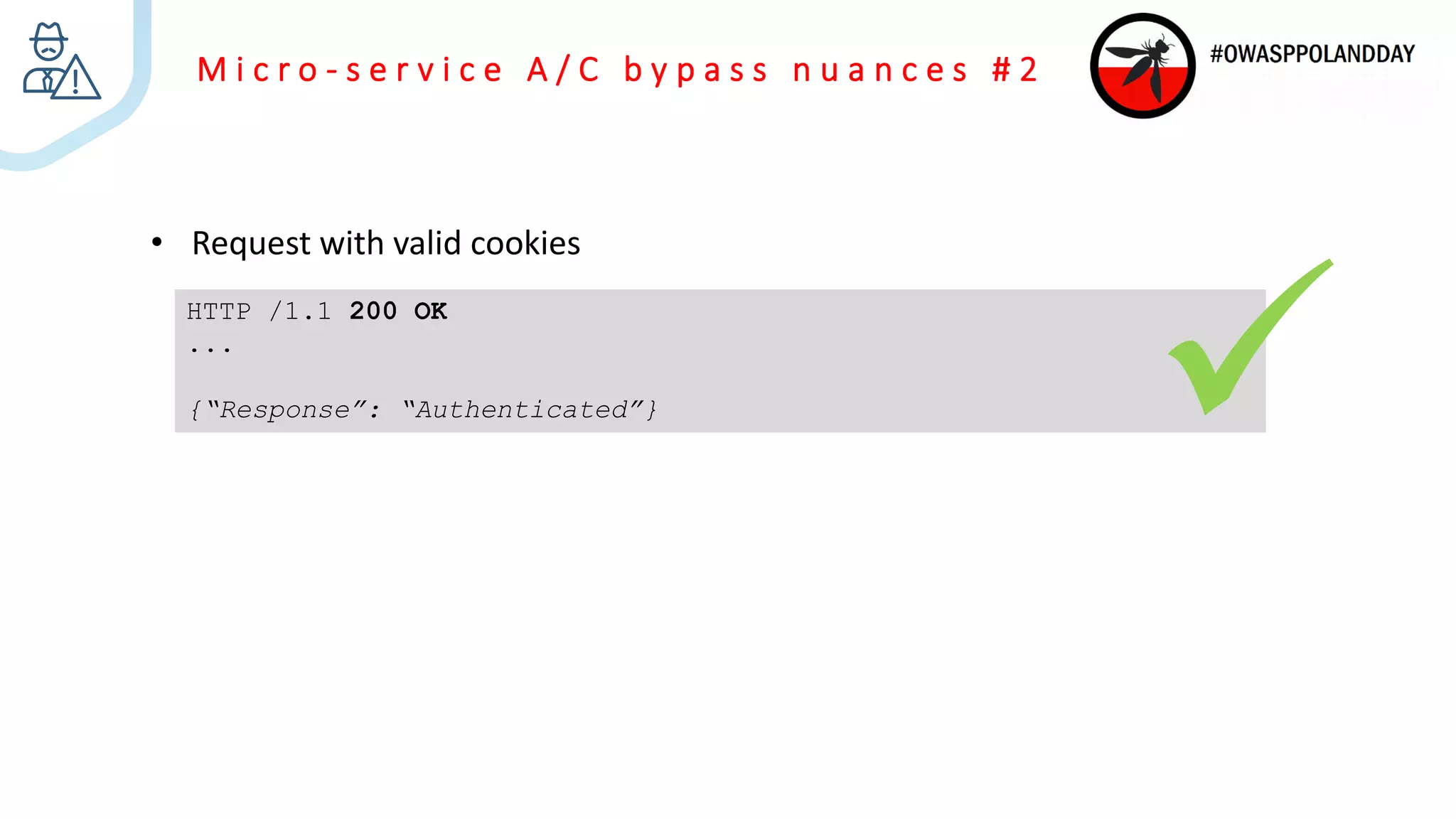
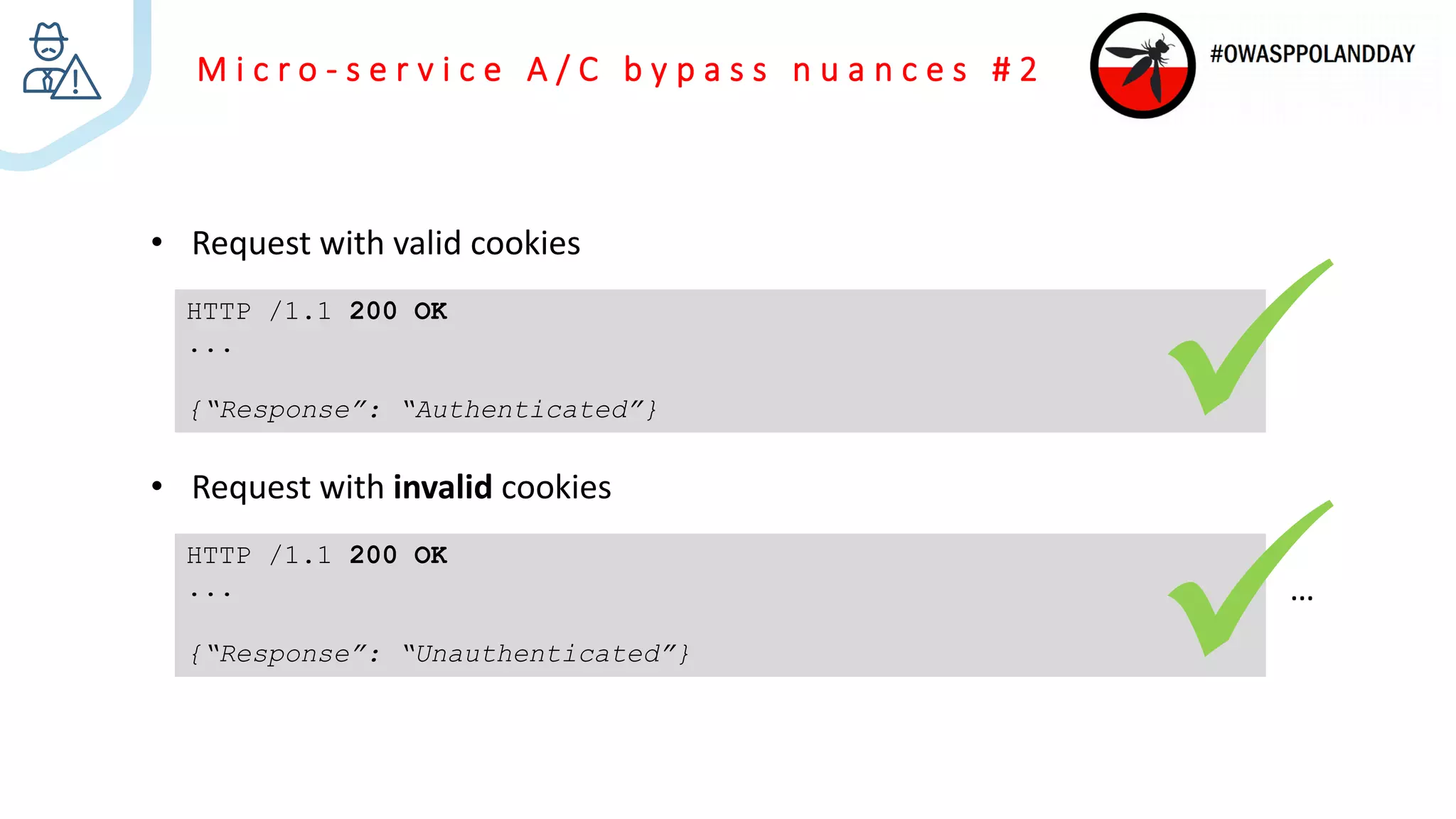
The document presents an overview of current vulnerabilities found in e-commerce and financial trading applications, emphasizing the need for context and tailored testing techniques. It highlights typical vulnerabilities such as broken access control, payment flow abuse, and XSS, along with strategies for identifying them using tools like Burp Suite. The authors stress the importance of understanding specific domain risks and encourage quick, context-specific testing for effective results.












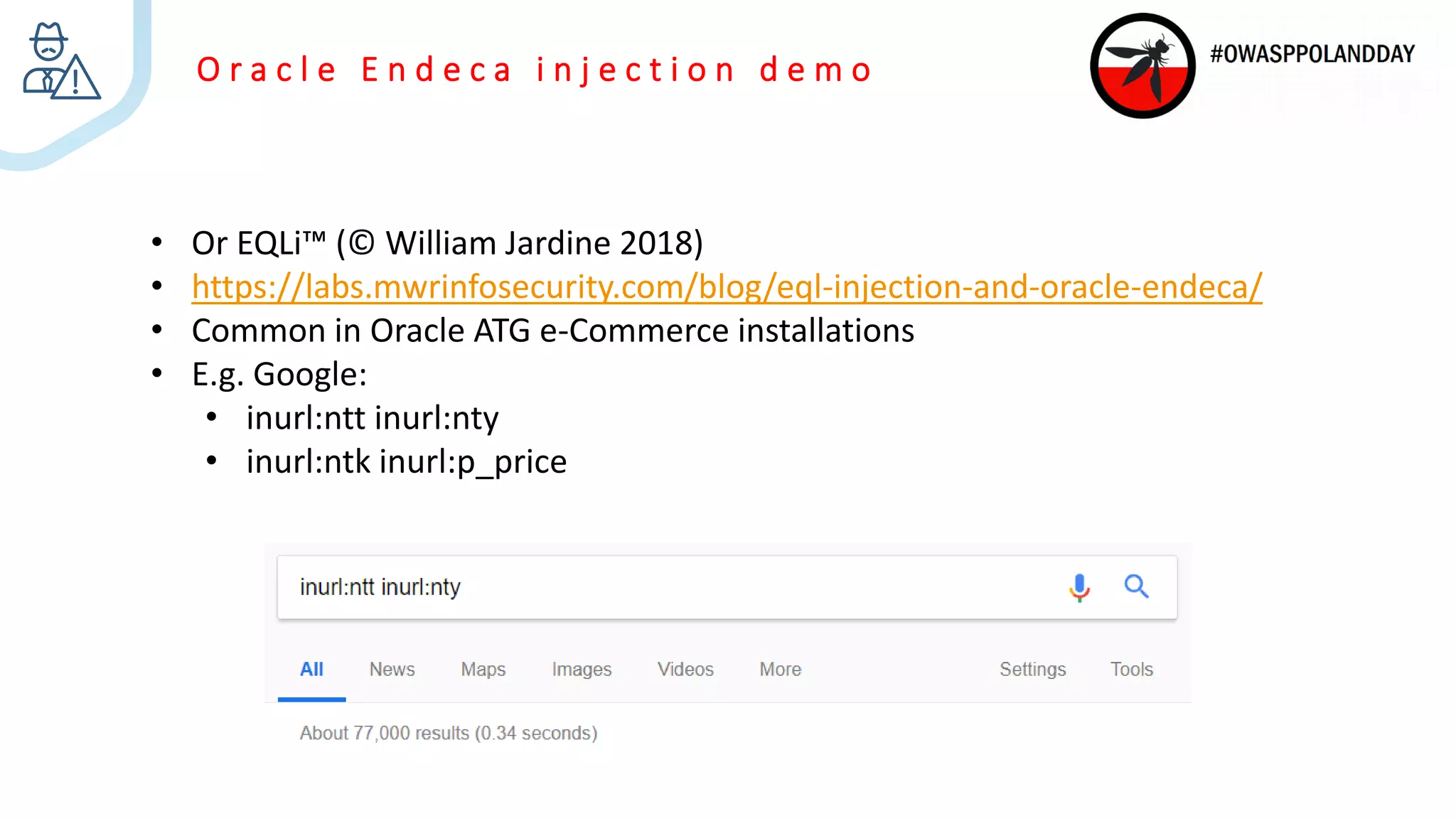
![O r a c l e E n d e c a i n j e c t i o n d e m o
Nrs=collection()/record[LISTING_ID%3D "T123456"]
Nrs=collection()/record[endeca:matches(.,"P_Marked_For_Emergency_
Withdrawal ","Y")]
Ns=P_Stock_Availability|0||P_Best_Seller|0
Ntt=someitem&Ntk=All](https://image.slidesharecdn.com/fieldingjardine-commonvulnsfinanceandecommerce-181012140852/75/OWASP-Poland-Day-2018-Anthony-Fielding-and-William-Jardine-Common-App-Vulns-27-2048.jpg)